当前位置:网站首页>Database knowledge: SQLServer creates non-sa user notes
Database knowledge: SQLServer creates non-sa user notes
2022-08-04 07:02:00 【IT technology sharing community】

Database security is a very important part of database operation and maintenance. Today, I will share with you how to create a non-sa user in SQL Server and set the access rights corresponding to the database. I hope it can be helpful to you.!
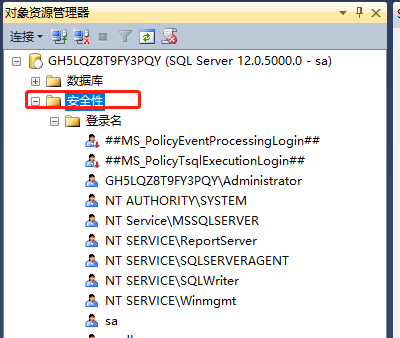
1. Create a login
1.1. Create a login Security→Login→New login (right mouse button)
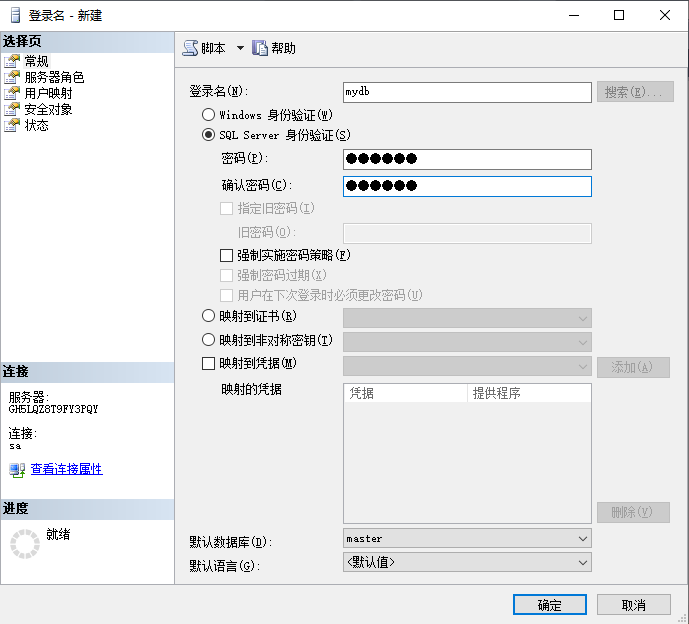
2.2. Create a database and log in to mydb with a password of 123456.
Note: Tick off Enforce password expiration policy (F)
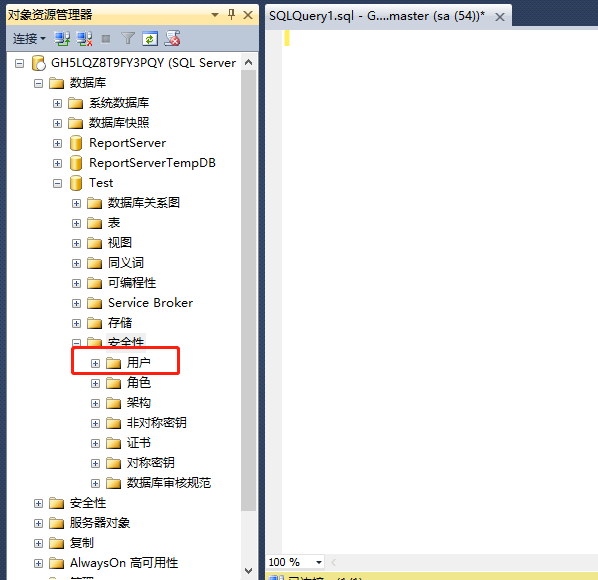
3. New database user
3.1 Test Database→Security→Users→New User (right mouse button)
3.2 New User Dialog
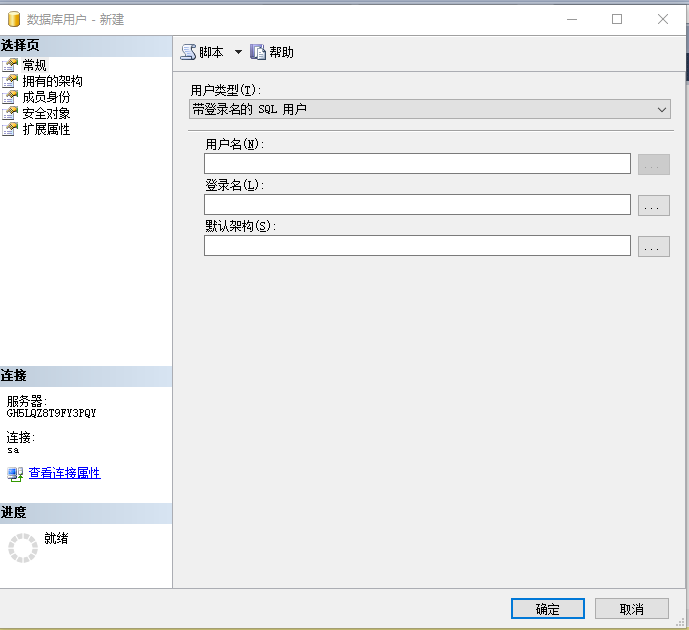
For example, the user name is mydb, the login name is mydb, and selecting the login name is actually selecting the previous step to create a login name
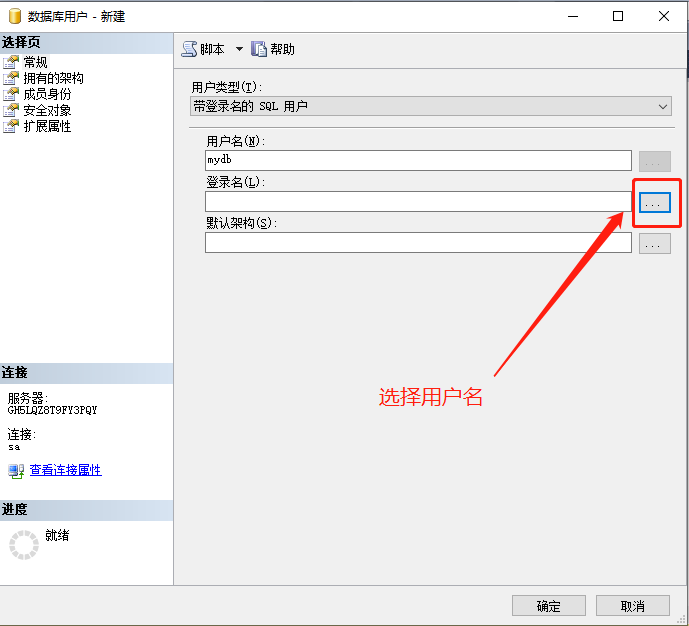
Click the browse button, find mydb, and click the OK button.
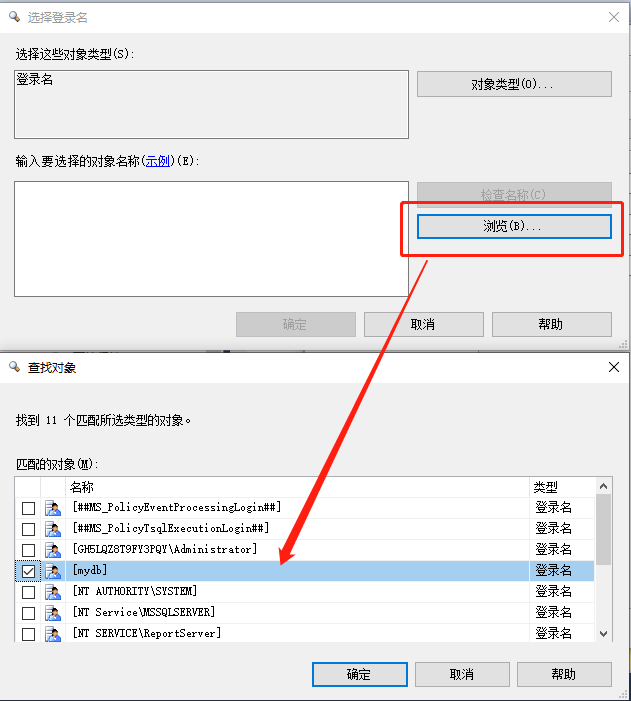
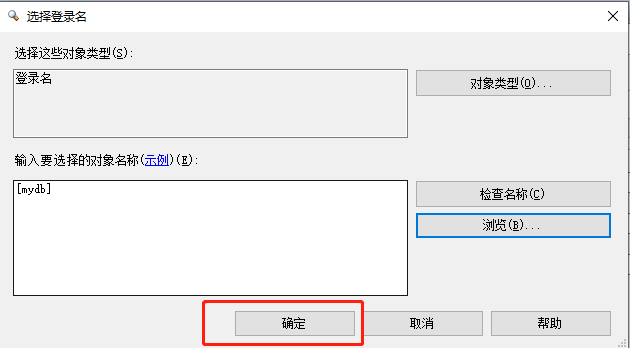
Click the OK button
4. Configure permissions to create users
Then switch the sa account to log in, and set the permissions of the mydb login name. Generally, users of self-built databases only need database query and write operations. The specific selection is as shown below.
Note: If you check db_owner, you will have the ability to create and delete tables, stored procedures, views, functions, and even delete databases. You can also set permissions for other users. It is not recommended to check forcustom user.
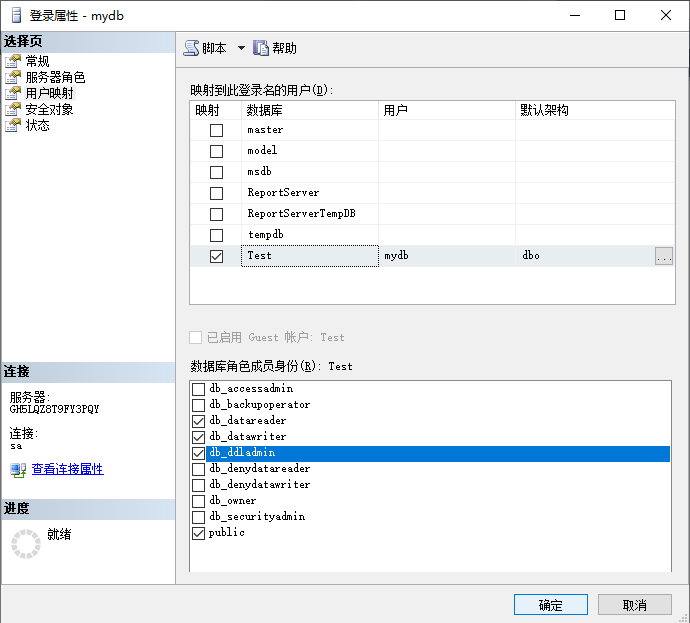
The user mapping page can adjust the non-system built-in databases that the current user can access or own, and can set the user's permissions separately.
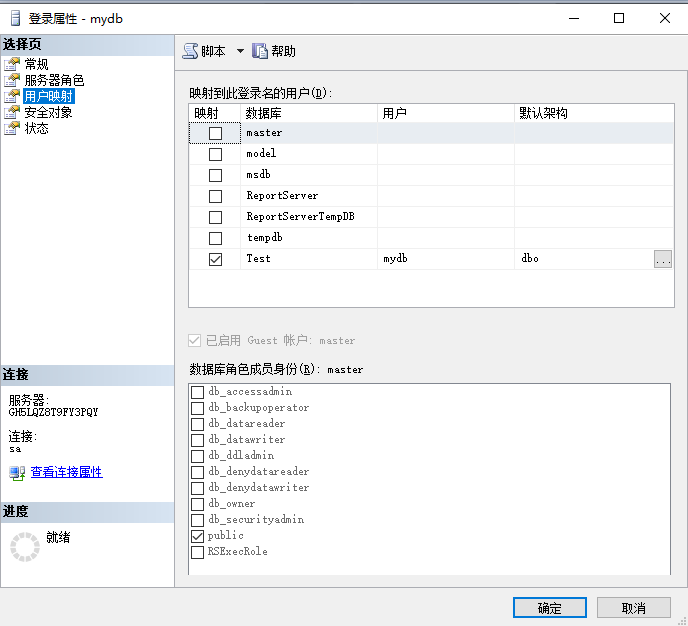
5. Introduction to SQLServer fixed database roles
db_owner: Users in this role can perform any operation in the database.
db_accessadmin: Members of this role can add or delete users from the database.
db_backupopperator: Members of this role allow database backups.
db_datareader: Members of this role are allowed to read any data from any table.
db_datawriter: Members of this role are allowed to write data to any table.
db_ddladmin: Members of this role are allowed to add, modify or delete any object in the database (that is, execute any DDL statement).
db_denydatareader: Members of this role are denied viewing any data in the database, but they can still view it through stored procedures.
db_denydatawriter::: Like the db_denydatareader role, members of this role are denied modifying any data in the database, but they can still modify it through stored procedures.
db_securityadmin: Members of this role can change permissions and roles in the database.
public: In SQL Server 2008 every database user belongs to the public database role.When a user has not been granted or denied specific permissions on a securable object, the user will purportedly grant permissions to the securable object's public role, a database role that cannot be deleted.
边栏推荐
猜你喜欢
随机推荐
Unity Day02
用chrome dev tools 强制js注入
20170729
以太网 ARP
Memory limit should be smaller than already set memoryswap limit, update the memoryswap at the same
【HIT-SC-MEMO5】哈工大2022软件构造 复习笔记5
webrtc技术名词和关键技术要点:SVC,REMB,SVC...
U-Net详解:为什么它适合做医学图像分割?(基于tf-Kersa复现代码)
电脑软件:推荐一款磁盘空间分析工具——WizTree
软件:给大家推荐一款国产非常好用的效率软件uTools
网络技巧:教你给路由器装上电池,断电照样可以上网!
Multi-threaded sequential output
数据库知识:SQLServer创建非sa用户笔记
怎样才能转行成功?
Uos统信系统控制台欢迎登陆后消息及所处区域配置
基于时序模式注意力机制(TPA)的长短时记忆(LSTM)网络TPA-LSTM的多变量输入风电功率预测
让src文件夹能读取xml文件
Operating System Kernel
目标检测中的先验框(Anchor)
Flask request 返回网页中 checkbox 是否选中