当前位置:网站首页>BUUCTF--reverse2
BUUCTF--reverse2
2022-06-29 09:26:00 【X.IO】
reverse2
1预处理 获得信息
获得信息
64位文件
2.拖进IDA64,shift+F12 可以直接看到flag,可是这不是最终的flag,双击跟进
可以直接看到flag,可是这不是最终的flag,双击跟进 然后F5找到伪代码
然后F5找到伪代码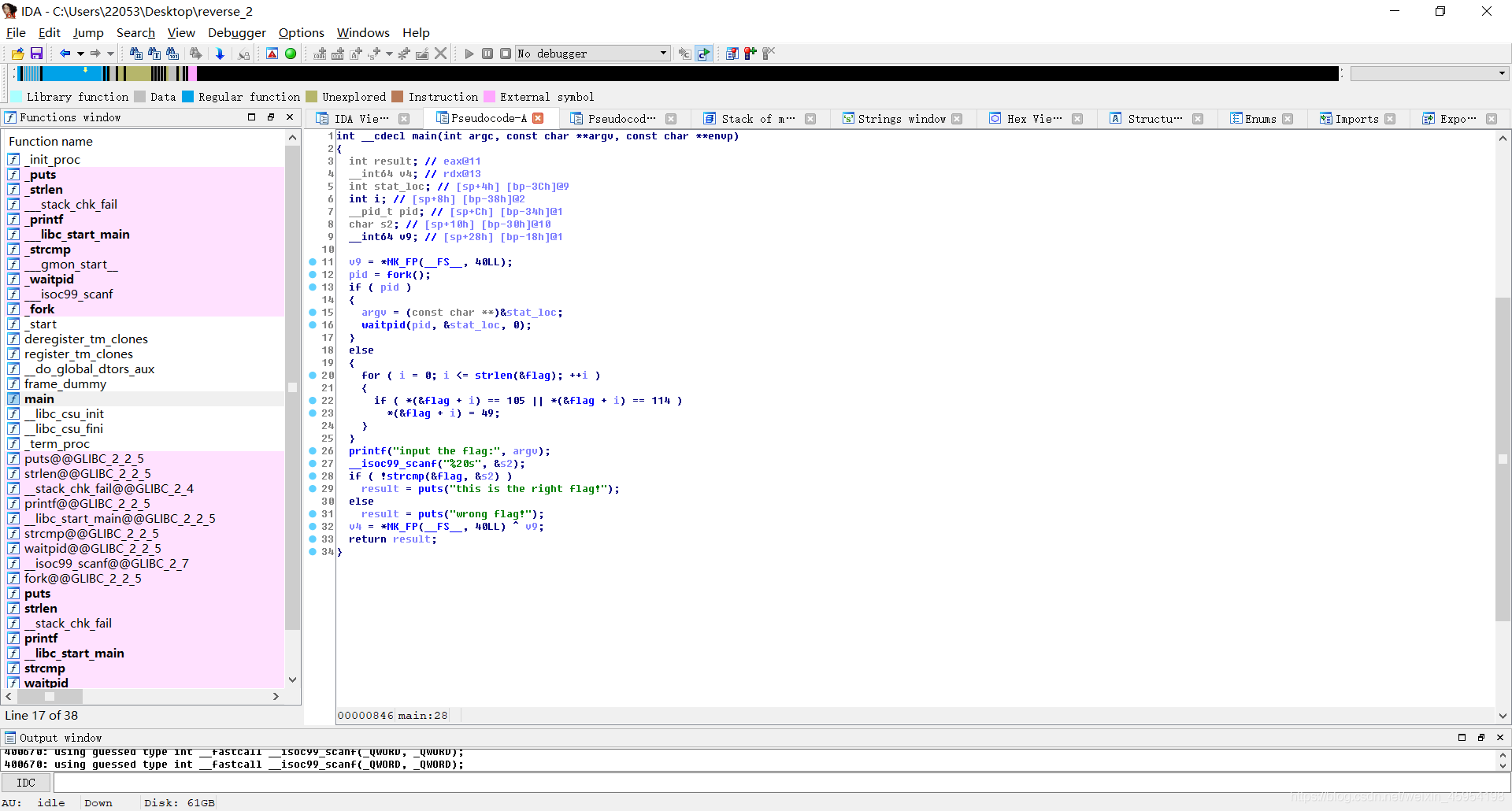 分析伪代码,找到关键的函数
分析伪代码,找到关键的函数
for ( i = 0; i <= strlen(&flag); ++i )
{
if ( *(&flag + i) == 105 || *(&flag + i) == 114 )
*(&flag + i) = 49;
}
注意:这里的105、114、49都是ASCII码,参考ASCII码表可知
105表示i 114表示r 49表示1
所以最终的flag是把flag中的i和r替换成1.
 flag{hack1ng_fo1_fun}
flag{hack1ng_fo1_fun}
边栏推荐
- Time varying and non time varying
- BUUCTF--内涵的软件
- 51nod1277 maximum value in string [KMP]
- If [not] exists in MySQL
- Recurrence of vulnerability analysis for Cisco ASA, FTD and hyperflex HX
- L2-031 go deep into the tiger's den (25 points)
- JNI. H description
- Picture verification code control
- September 29, 2020 non commodity templating code level rapidjson Library
- C#窗体向另一个窗体实时传值
猜你喜欢

這個開源項目超哇塞,手寫照片在線生成
Win32Exception (0x80004005): 组策略阻止了这个程序。要获取详细信息,请与系统管理员联系。

QGIS mapping

September 29, 2020 non commodity templating code level rapidjson Library
Recyclerview sticky (suspended) head

This open source project is super wow, and handwritten photos are generated Online
2020-10-17:刷题1
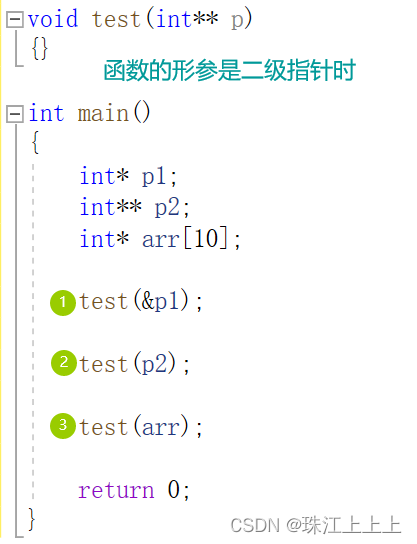
指针数组、数组指针和传参的相关问题

Time varying and non time varying

IIS服务器相关错误
随机推荐
基辅周边的凄美废墟——切尔诺贝利的安全前往指南!
Virtual machine port scanning
2019.10.30 learning summary
2019.10.20 training summary
MySQL InnoDB data length limit per row
Use of Azkaban in task scheduler
C#使用WinExec调用exe程序
2019.10.27 training summary
September 25, 2020 noncopyable of boost library for singleton mode
Sixteen system counter and flow lamp
The stones game
MySQL中innodb_page_cleaners详解
IIS服务器相关错误
完全二叉树的权值 递归做法 ——最后的编程挑战
HDU 6778 car (group enumeration -- > shape pressure DP)
Recurrence of vulnerability analysis for Cisco ASA, FTD and hyperflex HX
Common usage of LINQ in C #
在VMware workstation中安装WMware ESXi 6.5.0并进行配置
Recyclerview universal adapter package
2020-09-21 visual studio header file and Library Directory configuration