当前位置:网站首页>Hash tables, sets, maps, trees, heaps, and graphs
Hash tables, sets, maps, trees, heaps, and graphs
2022-06-12 13:41:00 【You stole my name】
One 、 Hashtable 、 mapping 、 aggregate
hash Definition
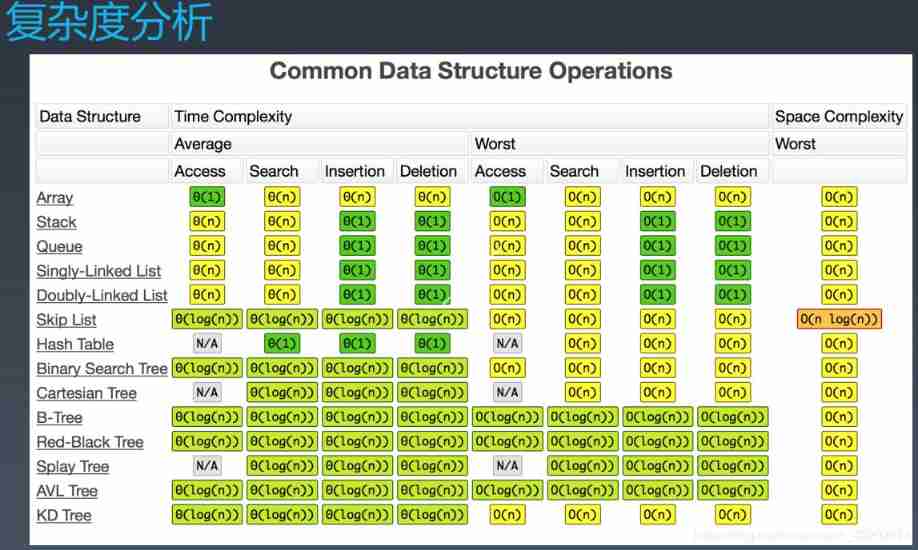
Hashtable (Hash table), Also called a hash table , According to the key code value (Key value) Data structures that are accessed directly . It accesses records by mapping key values to a location in a table , To speed up the search . This mapping function is called the hash function (Hash Function), The array of records is called a hash table ( Or hash table ).The engineering practice
Telephone directory 、 User information sheet 、 cache (LRU Cache) And key value pair storage (Redis) etc. .hash function

hash Collision

set、map
map yes key-value Yes ,key No repetition ;set: A collection of non repeating elements .
Two 、 Trees 、 Binary tree 、 Binary search tree
Trees and pictures


The list is a special tree , Trees are special graphs
Traversal of binary tree :
1. Before the order (Pre-order): root - Left - Right
2. Middle preface (In-order): Left - root - Right
3. In the following order (Post-order): Left - Right - root
Common traversal algorithms :1. recursive ;2. iteration + Stack .Binary search tree
Binary search tree , Also known as binary sort tree 、 Ordered binary tree (Ordered Binary Tree)、 Sort binary trees (Sorted Binary Tree), An empty tree or a binary tree with the following properties :
1. The value of all nodes in the left subtree is less than the value of its root node ;
2. The value of all nodes in the right subtree is greater than the value of its root node ;
3. And so on : Left 、 Right subtrees are also binary search trees .
In the sequence traversal : Ascending order
3、 ... and 、 Pile and binary pile
- The top of the heap is the maximum or minimum , The biggest one is called the big top pile , The smallest one is called small top pile . The time complexity of finding the best value is O(1).
- Binary heap is realized by complete binary tree , Actually do it with an array . The index for i The left child's index is 2i+1; The index for i The right child's index is 2i+2; The index of the parent node with index is floor((i-1)/2);
边栏推荐
- Web3.0,「激发创造」的时代
- How to solve the problem of data table query error when SQLite writes the registration function?
- Qualcomm platform development series (Protocol) QMI brief introduction and usage
- Wechat web developer tools tutorial, web development issues
- 2068: [example 2.6] chicken and rabbit in the same cage
- 看完这一篇就够了,web中文开发
- jupyternotebook有汉字数据库吗。在深度学习中可以识别手写中文吗
- xcode 调试openGLES
- 1005: estimation of the earth's population carrying capacity
- Formal analysis of Woo Lam protocol with scyther tool
猜你喜欢

leetcode 47. Permutations II full permutations II (medium)

A method of quickly creating test window

618 entered the second half of the period, apple occupied the high-end market, and the domestic mobile phones finally undercut the price competition
![2061: [example 1.2] trapezoidal area](/img/83/79b73ca10615c852768aba8d2a5049.jpg)
2061: [example 1.2] trapezoidal area

Pre research of image scanning tool

Qualcomm platform development series (Protocol) QMI brief introduction and usage

Paw 高级使用指南

Successfully rated Tencent t3-2, 10000 word parsing

IC chip scheme fs4062b for lithium battery charging with 5V boost to 12.6V

创新实训(十)高级界面美化
随机推荐
GPUImage链式纹理的简单实现
static 和 extern 关键字详解
2065: [example 2.2] sum of integers
MySQL 查询 limit 1000,10 和 limit 10 速度一样快吗? 深度分页如何破解
Overview of embedded system 2- composition and application of embedded system
将字符串转为16进制字符串并显示出来
leetcode 47. Permutations II 全排列 II(中等)
Real time software source code of COVID-19
Codeforces 1637 E. best pair - Thinking
【刷题篇】超级洗衣机
1001:Hello,World
go-zero 微服务实战系列(二、服务拆分)
Application of short circuit expression (||) in C language
Script import CDN link prompt net:: err_ FILE_ NOT_ Found problem
Codeforces 1637 A. sorting parts - simple thinking
1002: output the second integer
Resume NFT platform trustrecruit joined Octopus network as a candidate application chain
开发中使用的语言技巧
Simple implementation of gpuimage chain texture
Xcode debugging OpenGLES