当前位置:网站首页>Error reporting injection of SQL injection
Error reporting injection of SQL injection
2022-06-11 06:01:00 【visionkiwi】
An error injection
There are two common error reporting injections :extractvalue , updatexml
When to use error injection ?
When there is no suitable data return point, error injection is required . When injecting, the back end is injected , But the front end doesn't get a better display .
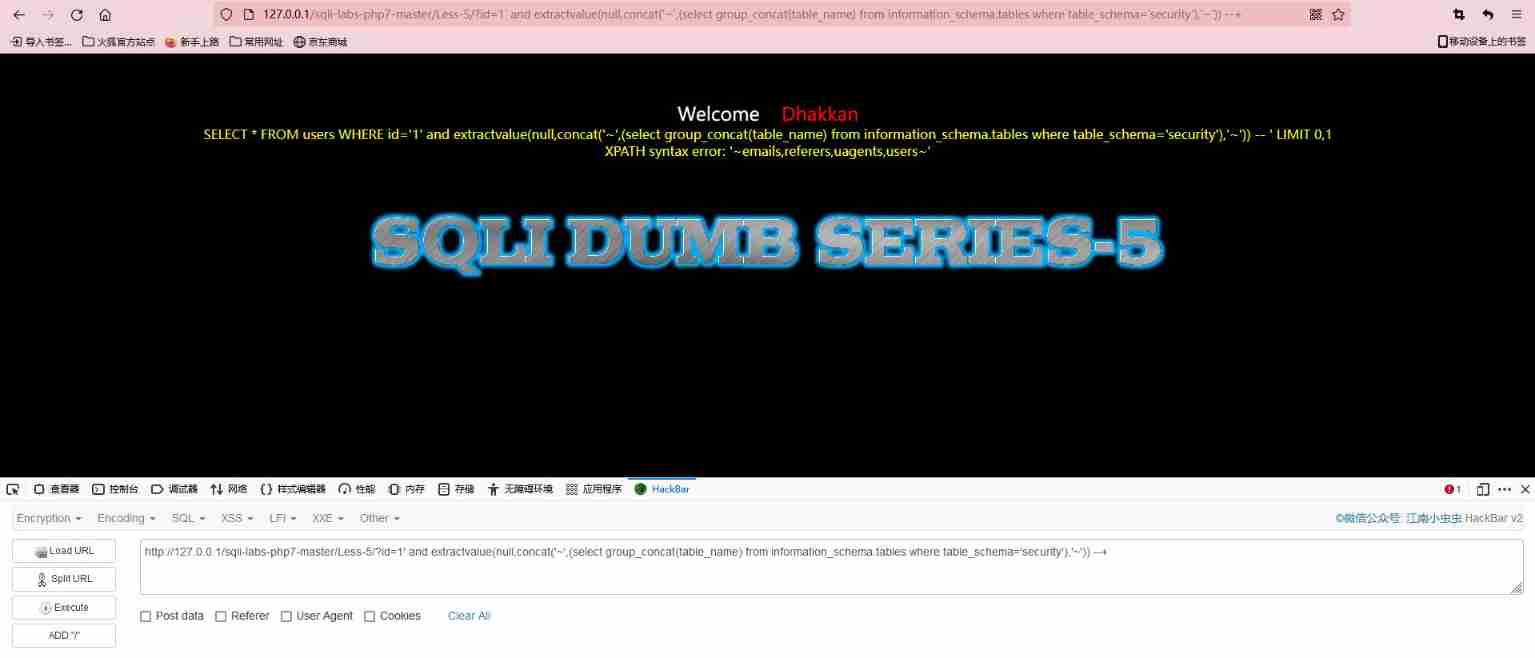
extractvalue
payload: and extractvalue(null,concat(0x7e,(payload),0x7e))
The database is xml Intentional error reporting of documents
utilize concat Splicing in the background
Specify that the first parameter is null , Let him deliberately report mistakes , The second parameter statement is brought into the database for execution , Finally, an error is reported and the execution result is displayed

We can see that it returns a XPATH syntax error: '~security~'
This XPATH It means : stay XPATH There is an error in the implementation of , Is the first parameter we wrote null The error of , So the statement of the second parameter is executed , So you can go to the next step to get the table name , Name , data ....
Be careful : In case of error injection , We can only use it select Rather than union select

How to solve the above situation : stay payload When it's time to add limit, As shown in the figure below

Another way is to build payload When you use group_concat() Here's the picture
updatexml
payload: and 1=(updatexml(1,concat(0x7e,(payload)),1))
payload: and 1=(updatexml(1,concat(0x7e,(payload)),1))
updatexml This function is used to update xml Data . By default, the updated content is passed in , But the illegal communication made him deliberately report a mistake , And then execute sql sentence
边栏推荐
- 修复Yum依赖冲突
- 使用Batch枚举文件
- OJDBC在Linux系统下Connection速度慢解决方案
- Sign for this "plug-in" before returning home for the new year
- Sword finger offer 50: the first character that appears only once
- DISM命令使用小结
- Completabilefuture asynchronous task choreography usage and explanation
- Free get | full function version of version control software
- URL in flask_ for
- NDK learning notes (x) POSIX socket for connectionless communication
猜你喜欢

Do we really need conference headphones?
Implementation of data access platform scheme (Youzu network)

NDK learning notes (12) native graphics API, using avilib to create an avi video player

Thymeleafengine template engine

Summarize the five most common BlockingQueue features

NDK learning notes (VI) Basics: memory management, standard file i/o

Write a list with kotlin

安装Oracle数据库
![Experimental report on information management and information system [information security and confidentiality] of Huazhong Agricultural University](/img/f6/e58196aeac85178f6603cea1962a6e.jpg)
Experimental report on information management and information system [information security and confidentiality] of Huazhong Agricultural University

Compliance management 101: processes, planning and challenges
随机推荐
What is a thread pool?
那个酷爱写代码的少年后来怎么样了——走近华为云“瑶光少年”
配置Rust编译环境
How to deal with message blackout and message sending failure of Aurora im
Sword finger offer 32: print binary tree from top to bottom
ThymeleafEngine模板引擎
[must see for game development] 3-step configuration p4ignore + wonderful Q & A analysis (reprinted from user articles)
Compliance management 101: processes, planning and challenges
View controller and navigation mode
Cenos7 builds redis-3.2.9 and integrates jedis
Servlet
Super (subclass)__ init__ And parent class__ init__ ()
Getting started with kotlin
Informatica:数据质量管理六步法
Using batch enumeration files
做亚马逊测评要了解的知识点有哪些?
Twitter data collection (content, fans, keywords, etc.)
Distributed framework ray - detailed introduction to starting ray and connecting clusters
Linux Installation redis
Sword finger offer 50: the first character that appears only once