Text
A penetration of an authorized unit , Because of the php frame , some cms Upload , From realization webshell Start .
details
Add listening , Generate Trojan file and change the application name to hide online .


Change the sleep time to 10 second

View host name whoami

Grab the plaintext password

Sure enough, the authority is not enough , Raise the right

Try all kinds of potatoes , According to the patch, I didn't find ,winserver2012 Right to mention here ms16-075 Yes. , But the strange thing is CS Not online , Upload script to go online CS

However, it did not go online , The cost of trial and error is high
【---- Help network security learn , All the following learning materials are free ! Add vx:yj009991, remarks “ Blog Garden ” obtain !】
① Thinking map of the growth path of Network Security Learning
② 60+ Network security classic common toolkit
③ 100+SRC Vulnerability analysis report
④ 150+ Network security attack and defense technology ebook
⑤ The most authoritative CISSP Certification test guide + Question bank
⑥ super 1800 page CTF Practical skills manual
⑦ A collection of the latest interview questions from Wangan factory ( With answers )
⑧ APP Client security detection guide ( Android +IOS)
Check it out. winserver 2012 Right to the version of , Uploading multiple scripts does not work ,CS Your plug-in just hit , In fact, I don't know why I failed the first time I tried , It's strange
Restart a monitor

Continue to raise rights ,ms-058 It is possible to raise the right

It was only the second time that the right was successfully raised

Modify sleep time , Neither too long nor too short is recommended , Grab the plaintext password
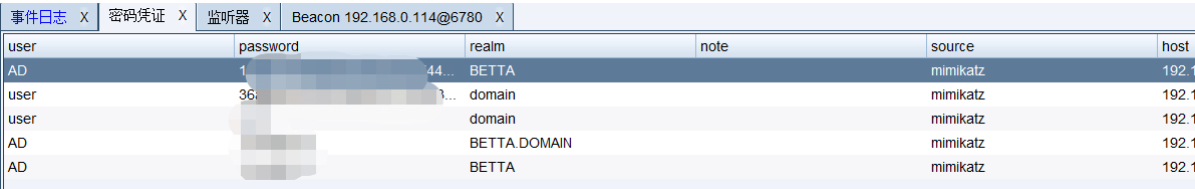
The plaintext password was successfully retrieved , Try to login remotely , Because in the early stage of information collection 3389 It's open .
Successfully logged in

Try to write scheduled task input permission maintenance , Here, you can choose to plan a task or dll Hijacking is OK , Here I choose to plan the task , After all, authorization projects don't worry about other problems , According to the preceding systeminfo Information at this time, we have obtained the permission of domain control , You can continue to perform intranet horizontal and domain penetration
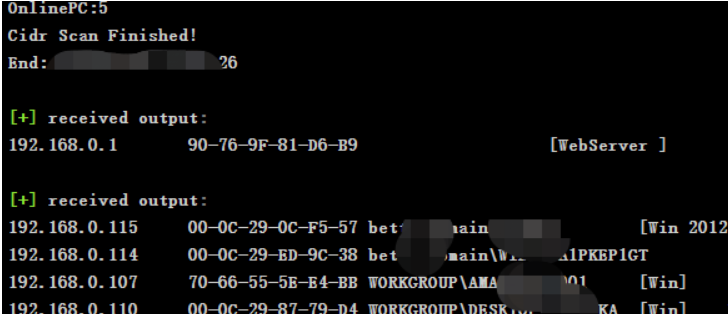
Of this network segment pc less , Intranet usually has other ip, Direct scan B paragraph

Get a lot of Intranet terminal information , however win10 Mostly ,win10 Of 445 Port utilization is generally blocked , Directly scan whether there are service classes , Such as ftp
The virtual terminal can execute , But no echo , You can only go up remotely
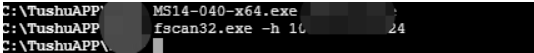
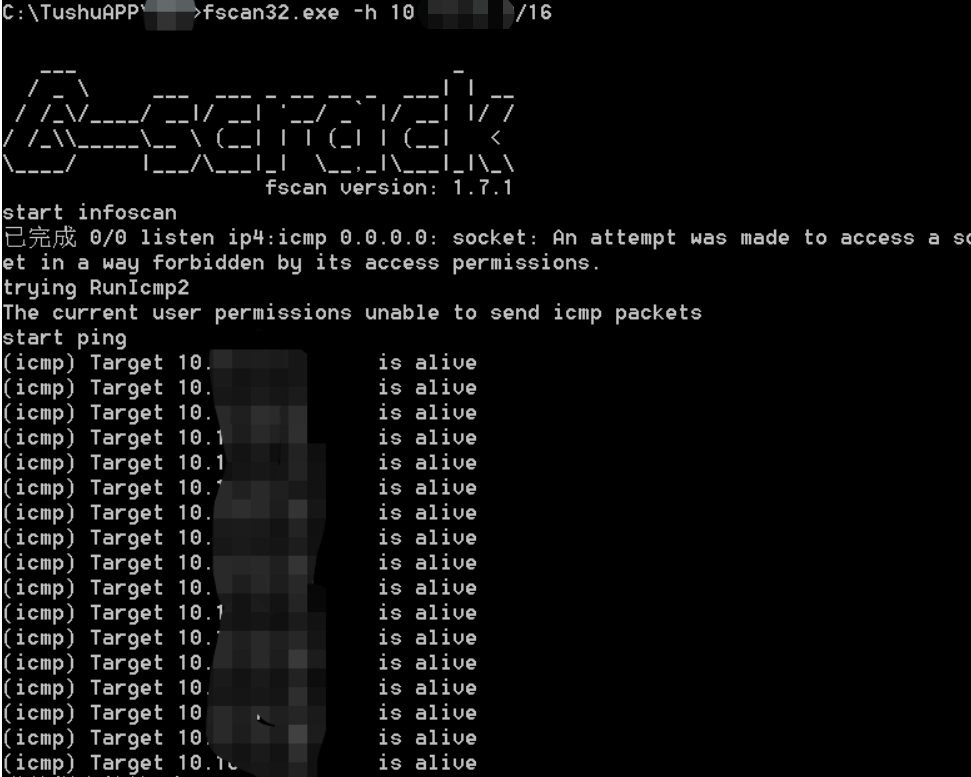
There are a large number of terminals in the intranet , But there's no server , This is the only server , Small domain , At this time, the network topology of the intranet is roughly ,445 There are a large number of hosts open in the intranet

But I tried to use it for several times without success , Basically winserver If you use the server, you can get shell The probability is probably high ,win10 Your host has never been successful before , This time, I didn't get it shell
According to the obtained plaintext password , Password spraying for blasting

Get passwords for some accounts .
Query the currently logged in domain user

Determine the host according to the host name queried above ip The address is 192.168.0.119,pth After the launch .
Summary
I don't know if it's a honeypot , But there are basically no servers in the intranet , The number of domain users is also small , Anyway, writing the report and handing it in will be over .
More range experiments 、 Network security learning materials , Please click here >>