当前位置:网站首页>Application Security Series 37: log injection
Application Security Series 37: log injection
2022-07-06 05:32:00 【jimmyleeee】
The parameters entered by the user are directly written to the log file without any verification , Cause attackers to pass special characters (\r \n) Inject new log entries into the log , Destroy the integrity of the system log . for example :test failed to log in. If test It's controllable , You can input (admin login successfully.\r\n test) Modify the log to :admin login successfully.\r\n Info:test failed to log in. Just inject a log . once The integrity of the log cannot be guaranteed , that , Will affect its validity as evidence .
The sample code of log injection is as follows :
logger.info("Test for Log injection for special char CRLF \r\n End");
logger.info("Test for Log injection for special char CR \r End");
logger.info("Test for Log injection for special char LF \n End");stay windows Under the system , Run this code , The results are as follows :
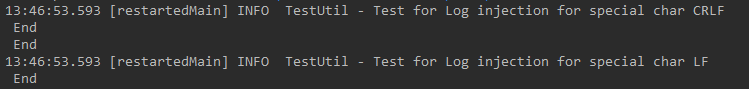
It can be seen from the displayed results , It was originally a line of logs , But it shows two lines in the log , That is, a line of log is injected . What's strange here is , When using \r when , all \r All previous logs are not displayed . in other words , Whether the attacker can hide his traces through this method ???
Line breaks vary from system to system , therefore , You can also filter according to different systems .
| operating system | File newline |
| Windows | \r\n |
| Linux | \n |
| Mac | \r\n |
One of the ways to prevent Namely , escape , take \r Replace the character with \\r,\n Replace with \\n, This can make \r perhaps \n Handle as characters that are not newlines , The sample code is as follows :
logger.info("Test for Log injection for special char CRLF \\r\\n End");
logger.info("Test for Log injection for special char CR \\r End");
logger.info("Test for Log injection for special char LF \\n End");The result is :

You can see here , take \r and \n Print out as specific characters .
The second method of prevention Is the use Log4j The configuration of automatically handles the processing of the characters that cause the injection , Although the principle will \r Replace with \\r,\n Replace with \\n, however , It's easier to use , For details, please refer to : Log4j – Log4j 2 Layouts
have access to %enc{%m}{CRLF} Replace line breaks . The specific configuration is as follows :
<Appenders>
<Console name="console" target="SYSTEM_OUT" follow="true">
<PatternLayout pattern="[%d{yyyy-MM-dd HH:mm:ss.SSS}][%-5p] [%t] [%c{10}#%M:%L] %enc{%m}{CRLF} %n "/>
</Console>
</Appenders>It can also be used log4j The security measures provided by the framework realize automatic replacement .
Another attack against log injection , When the system maintenance personnel check the log , The log may be displayed in web On the page , If the log contains html label , May lead to XSS attack . This point , stay Log4j 2 Layouts It is also described in , have access to HTML Code to achieve , for example :%enc{%m}{HTML}.
边栏推荐
- Closure, decorator
- [effective Objective-C] - memory management
- 算法-- 爬楼梯(Kotlin)
- 【云原生】3.1 Kubernetes平台安装KubeSpher
- LeetCode_字符串反转_简单_557. 反转字符串中的单词 III
- ByteDance program yuan teaches you how to brush algorithm questions: I'm not afraid of the interviewer tearing the code
- 01. 开发博客项目之项目介绍
- Improve jpopup to realize dynamic control disable
- 无代码六月大事件|2022无代码探索者大会即将召开;AI增强型无代码工具推出...
- nacos-高可用seata之TC搭建(02)
猜你喜欢
指針經典筆試題
Implementing fuzzy query with dataframe
![[leetcode16] the sum of the nearest three numbers (double pointer)](/img/99/a167b0fe2962dd0b5fccd2d9280052.jpg)
[leetcode16] the sum of the nearest three numbers (double pointer)

CUDA11.1在线安装
Codeforces Round #804 (Div. 2) Editorial(A-B)
毕业设计游戏商城
How to download GB files from Google cloud hard disk

The ECU of 21 Audi q5l 45tfsi brushes is upgraded to master special adjustment, and the horsepower is safely and stably increased to 305 horsepower
![[untitled]](/img/7e/d0724193f2f2c8681a68bda9e08289.jpg)
[untitled]

无代码六月大事件|2022无代码探索者大会即将召开;AI增强型无代码工具推出...
随机推荐
js Array 列表 实战使用总结
Unity Vector3. Use and calculation principle of reflect
The ECU of 21 Audi q5l 45tfsi brushes is upgraded to master special adjustment, and the horsepower is safely and stably increased to 305 horsepower
The ECU of 21 Audi q5l 45tfsi brushes is upgraded to master special adjustment, and the horsepower is safely and stably increased to 305 horsepower
[leetcode daily question] number of enclaves
Vulhub vulnerability recurrence 69_ Tiki Wiki
Qt TCP 分包粘包的解决方法
pix2pix:使用条件对抗网络的图像到图像转换
C Advanced - data storage (Part 1)
JS array list actual use summary
Excel转换为Lua的配置文件
Detailed summary of SQL injection
Check the useful photo lossless magnification software on Apple computer
[cloud native] 3.1 kubernetes platform installation kubespher
Algorithm -- climbing stairs (kotlin)
[mask requirements of OSPF and Isis in multi access network]
Summary of deep learning tuning tricks
2022半年总结
移植InfoNES到STM32
Three methods of Oracle two table Association update