当前位置:网站首页>Redis cache avalanche, penetration, breakdown
Redis cache avalanche, penetration, breakdown
2022-07-03 18:08:00 【popofzk】
Cache request process
Redis The avalanche of cache 、 through 、 Breakdown is a classic problem often encountered in daily work , Let's find out , Their solution is mainly : The bloon filter 、 Distributed lock ( Write next time. )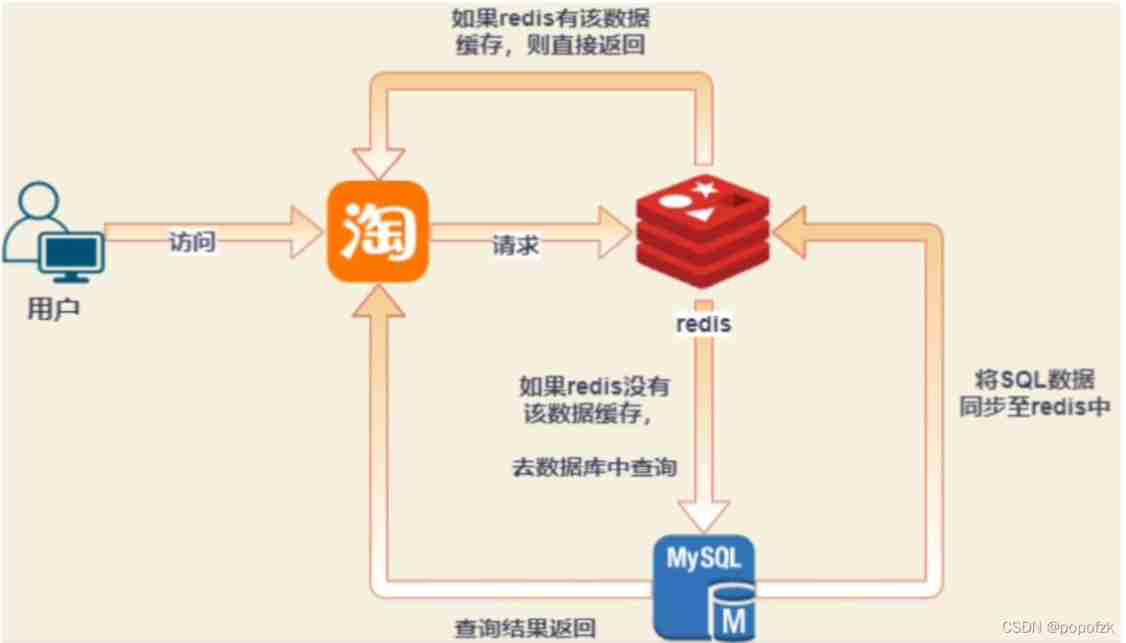
This is a simple client 、 Server request Redis Flow chart of , Simply put, when the user accesses the server , If the server needs to request data from the database , Go to the cache first to see if there is any , Go straight back to , If you don't have it, you will go to the database to query and return , This is a normal caching process .
Cache avalanche
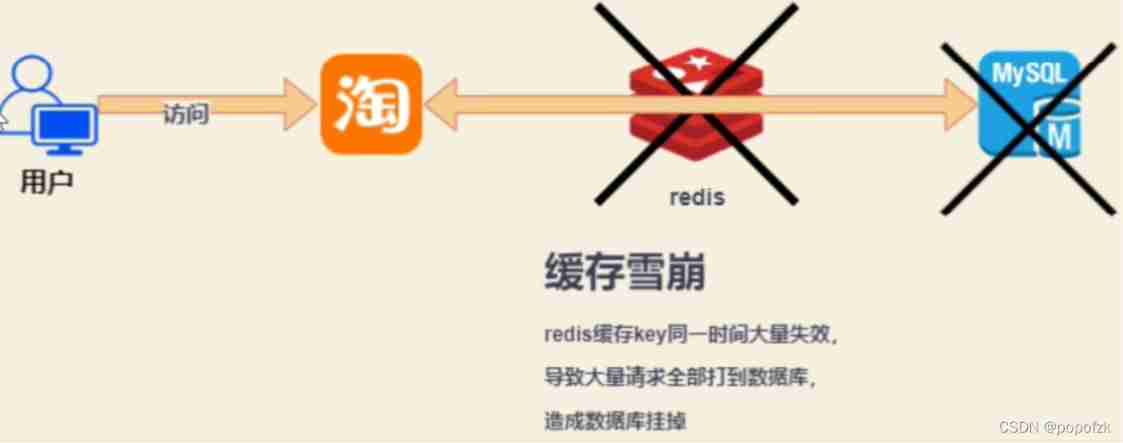
For example, the scene of a treasure , When the double 11 comes , The number of user visits is very large , So a lot of data is put into Redis In the cache , Corresponding Redis Of key, And set the cache expiration time to three hours , During the double 11 , After shopping for more than three hours , At the same time, all caches are invalidated in an instant , As a result, all requests are made to the database , The database fails to respond in time , At this time, there is no way to provide this service .
Simply speaking : Users visit a treasure ,Redis Medium key Large area failure , It leads to direct communication with the database , This phenomenon is called cache avalanche .
Solution :
- Set the expiration time , Let him not fail at the same time , When setting the cache , Random initialization expiration time , In this way, all caches will not be invalidated at the same time , Distribute as widely as possible .
- Redis It's usually cluster deployment , We will focus on key Put it on different nodes , Let these hotspot caches be evenly distributed on different nodes .
- Do not set cache expiration time
- Run timed tasks , Constantly refresh the cache , When the cache is about to expire, let it extend for three hours
Cache penetration

Here is a scene , For example, a hacker wants to attack our website :
The primary keys of databases are from 0 Began to increase , There is no negative number , This hacker has been using id<0 Make a request to our server ,redis Naturally, there is no such id, Will go to MySQL For the request , In this way, requests are constantly hitting the database , because Redis No interception id<0 The data of , Directly penetrated by such illegal requests .
Simply speaking : Cache penetration is Redis And there's no such data in the database , Generally, this is not a normal user , Are malicious users .
Solution :
- When data penetrates Redis When calling the database , The null value returned by the database should also be synchronized to Redis In the middle , At least make sure it's illegal id The next request is directly from Redis In the back
- ( Hackers will change different illegal parameters ), Pull black directly ip
- ( Hackers will also change different ip), Verify the validity of the input parameters
- The bloon filter
Cache breakdown

For example, this scene : On double eleven , Take father Ma's shoes out for auction , The programmer put the data of shoes into Redis In cache , Corresponding to one key, At auction , As one can imagine , Everyone's enthusiasm is very high , It's been going on 4 Hours , The shoe cache is invalid , As a result, a large number of requests cannot query the data of this shoe , And then hit all the data in the database , The database fails to respond in time .
Simply speaking : Is to puncture a very hot spot key
Solution :
- Let the cache never expire ( Not so good )
- The best way : Distributed lock ( Lock the database at the request step , At this time, only one thread can grab the lock , That is, only one thread can operate the database , At this time, the pressure on the database is very small , When you find this hotspot key Later, I will write again Redis in , Other threads that didn't get locks , Let him sleep for a few milliseconds , Go again redis Query data in )
reflection :
A project can be divided into three stages , Get ready to go online 、 Preparation during project operation 、 Treatment measures after project downtime .
For example, before the project goes online , It can be built into a cluster :Redis colony 、MySQL colony 、 Its own distributed cluster , This can form a highly available cluster , Enhance the robustness of the system .
Some problems occurred during the operation of the project , The treatment measures of current limiting and degradation can be adopted , Prevent a large number of requests from hitting the database , Make the system unavailable .
If the system really hangs , Some alarm systems can be integrated , Even if we inform our developers , At the same time, quickly restart the project , utilize Redis Of aof、rdb Persistence mechanism , To quickly recover cached data , Minimize the time when the system is unavailable
边栏推荐
- [combinatorics] generating function (use generating function to solve the number of solutions of indefinite equation)
- Prototype inheritance..
- Should I be laid off at the age of 40? IBM is suspected of age discrimination, calling its old employees "dinosaurs" and planning to dismiss, but the employees can't refute it
- Keepalived 设置不抢占资源
- How to install PHP on Ubuntu 20.04
- [combinatorics] generating function (property summary | important generating function)*
- MySQL has been stopped in the configuration interface during installation
- PHP returns 500 errors but no error log - PHP return 500 error but no error log
- Golang string (string) and byte array ([]byte) are converted to each other
- TCP拥塞控制详解 | 3. 设计空间
猜你喜欢
随机推荐
The third day of writing C language by Yabo people
Five problems of database operation in commodity supermarket system
Research on Swift
图像24位深度转8位深度
c# . Net tool ecosystem
模块九作业
Research Report on investment trends and development planning of China's thermal insulation material industry, 2022-2028
ArrayList analysis 3: delete elements
[combinatorics] generating function (shift property)
STM32 realizes 74HC595 control
Global and Chinese health care OEM and ODM market status survey and investment planning recommendations report 2022-2028
[untitled]
远程办公工具分享|社区征文
OpenSSL的SSL/BIO_get_fd
Implementation of Tetris in C language
基于人脸识别的课堂考勤系统 tkinter+openpyxl+face_recognition
Fedora 21 安装 LAMP 主机服务器
Introduction to PHP MySQL
Computer graduation design PHP campus address book telephone number inquiry system
Postfix tips and troubleshooting commands