当前位置:网站首页>A Security Analysis Of Browser Extensions
A Security Analysis Of Browser Extensions
2022-06-11 04:05:00 【Sword-heart】
0x00 Preface
Browser extended security doesn't seem to be much discussed ,drops There are no relevant articles on , I only found a sample article on extension on Zhihu , Link please click me . therefore , I searched some research reports on extended security , The following is one of them , From Cornell University Library ( The same school as Berkeley ), It provides us with a very good idea for mass analysis of extended security and bypassing silent installation , I think it is worth learning , So translate it and share it with you . original text :http://arxiv.org/abs/1403.3235
0x01 Abstract
Browser extension ( It is often called a plug-in or add-on ) In essence, it is a small piece of code that allows developers to add functions to the browser . However , Extension also comes at a security cost : Users must trust the plug-in developer . Let's see how this trust relationship is broken , This will cause malicious extensions to be installed in the user's browser . Again , We also look at the silent installation method extended in various browsers and how the browser itself prevents silent installation .
We compare the extension mechanisms of various browsers , Trying to create a rule to minimize the permissions of the plug-in in the browser , Then based on this, various plug-ins are analyzed , In order to observe whether the minimize permission rule meets the requirements of the plug-in for permission .
alike , We have also investigated many plug-ins on a variety of browsers , Find out the root cause of possible attack . for instance , If the developer's account is hacked , Then the extension developed by the developer may be embedded with malicious code . We also found abuse of authority , It is found that many extensions will apply for more permissions than they use .
Finally, a solution is provided to let users check the reliability of the extension before downloading it .
0x02 Introduce
Browser extensions are now extremely popular , exceed 33% Of Chrome Browser users have more than one extension installed . On a normal website , Expand ( Also known as plug-ins ) Is a short piece of code that allows users to modify browser behavior . Most plug-ins use javascript To write , Of course, there are other scripts . When extensions are so widely used in desktop operating systems , In a mobile browser , Still in its infancy , Only a small number of mobile browsers will support third-party extensions , such as Mozilla’s Firefox for Android and Dolphin Because of time , In this article , We just use Google Chrome and Firefox For example , Other browsers will not be considered for the time being .
Most browsers have their own security model in their extended platforms . In this article , We analyzed a variety of vulnerabilities caused or possibly caused by extensions . meanwhile , Based on the test results, the effectiveness of these security models is verified .
0x03 Safety overview
1、Google Chrome There are three ways to ensure the security of the extension .
1 2 3 4 |
|

chart 1:Google Chrome Extended architecture diagram of
2、 threat .
There are two possible attacks in the extension :
1 2 3 4 |
|
We didn't study Firefox An extension of , because Firefox No rights management for extensions . therefore , All extensions can read and write the user's home directory . This leads to Firefox The extension permission of is too large , It also creates more loopholes .
0x04 The way
We use the following operation :
1 2 3 4 |
|
0x05 Statistics
We have a total of Chrome Web The store downloaded 10047 Extensions . They are ranked by popularity , Therefore, the frequency of use that can represent the extension is the highest .
1) Content security policy (Content-Security Policy)
Content security policy is introduced as a new feature to Chrome Of the 18 A version , Through its strict strategy , Most of the vulnerabilities discussed above are blocked . We found that there was 4079 Extensions have upgraded its manifest To the second edition , So as to force the content security policy to be applied . Although these extensions still have permissions abuse and their own vulnerabilities , But it is also more secure than other extensions that do not apply this policy .
stay 10047 Of the extensions , We have successfully scanned 9558 individual , Others are wrong manifest The file and some files are missing and could not be successfully analyzed .
2) Abuse of authority
Through analysis manifest.json file , We scanned the permissions of these extension requests . The method comes from Google Chrome Developer Web page :“ All the extensions , Both browser applications and themes have a json Format manifest file , With manifest.l name , perhaps missing.json, Important information to provide extensions .”
Then match the permissions actually used by the extension .Chrome The security policy of only allows ‘backgroud-scripts’ Direct access to the core API. By parsing all the files in the source code ‘backgroud-scripts’ paragraph , Analyze the actual permissions required for extension .
We found that among these extensions , More than half of them have applied for permission that is more than necessary for actual use . Most of them applied for one or two additional permissions , This can be attributed to the level and lack of rigor of developers . In addition, there are 192 Multiple applications for extensions 4 Or more permissions , It shows a serious safety problem .
In Statistics , We do not include permissions that cannot be abused . such as , The authority of the notification function , Can be allowed to use HTML5 Notification interface for , But it cannot be abused . There are more than 300 Extensions have applied for this permission , But did not use , We have not included these extensions in the statistical results . Although they do not pose a security problem , But in the application for permission , It's also a bad habit .
Here are our statistics :

The following is a tree view of the comparison between the extended number of permission abuse and the number of additional permissions applied ,Y The coordinates are 10 Is the value of the base logarithm .
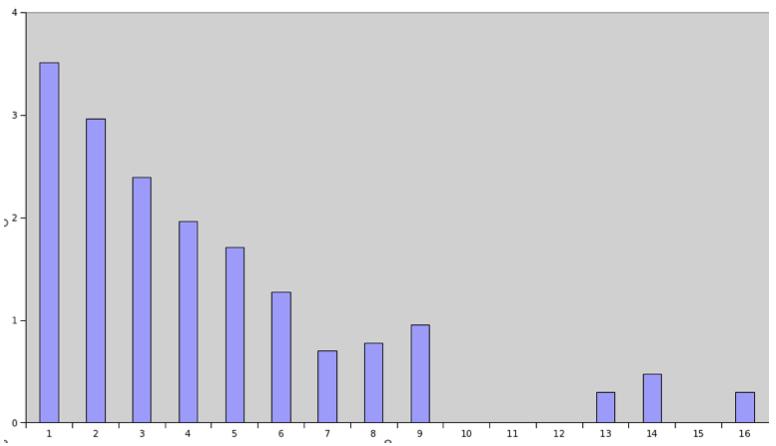
Many unqualified extensions will apply for extremely sensitive permissions , In this way, hackers and malicious developers can easily use these permissions to obtain the user's account information , Like the browser's cookie.
3) Network level attacks
We found some extensions in HTTP There are also loopholes at the network level , They will pass through HTTP Protocol load remote script . For technical reasons , It is impossible to count all the HTTP request , But I still found 146 Extensions have been initiated externally HTTP request . We only count the direct inclusion <script> Request for tag , If you add include XHR Request ( Many extensions use ), This number will be much higher .
We can not use the program to count the contents XHR Request , If statistics are made manually , It will be a hard job . This is because many requests are used directly javascript launch , Or use <img> Tag initiation , Such as JQuery、MooTools Others, such as javacript frame . We intend to analyze all URL character string , Assume it is the requested address , It turns out that it leads to a lot of errors , Thus negating this practice .
Network level attacks include man in the middle attacks (MitM), If you use this method , Will allow remote code execution , And when the problem lies in the core extension , This means that all permissions can be abused . for instance , Man in the middle attack can replicate the user's browser cookie value , Then send it to the attacker himself . This will result in something like “ grail ” attack , Thus endangering all user accounts .
0x06 A working model
1、 Silent installation
Firefox and Chrome There are silent installation methods . Under normal circumstances , This involves registry editing . When the browser starts , The corresponding key value in the registry will be checked , When installing extensions , A warning window will pop up . Only the user has allowed , Extensions will be installed .
We created a mechanism that does not require a warning window to pop up , Test both browsers in different ways .
1 2 3 |
|
The research on the silent installation mechanism shows that , The way browsers are now is not perfect , It's easy to get around . Of course , In the browser corresponding to bypass Silent installation , This is always a cat and mouse game .
2、 Extension check
We check the database by setting up an online extension , Let users use our research results . Users can easily find the corresponding extended permission abuse and external HTTP Request analysis . We also intend to publish it on the website as soon as possible .
Website by reading manifest.json File to compare the actual permissions required for extension with the permissions applied , After analysis, it is stored in the database , And provide HTTP Method of interface access .
0x07 Conclusion
We have successfully developed the script , Realized Chrome and Firefox Extended silent installation without warning , Proved that the current prevention mechanism is not perfect .
In the extension of analysis , There are about 50% There is abuse of authority . Although it is difficult to give accurate figures , But it can be concluded that , A considerable number of extensions will be attacked due to permission abuse . We also realize that , Content security policy (Content-Security Policy) It is indeed an efficient solution to ensure extended security .Google Chrome Web Stores will also be safer because of the implementation of this strategy .
Last , Attach a copy of this project github The source code address on :https://github.com/captn3m0/nullcon2014
1 2 3 4 5 |
|
This article comes from the dark cloud knowledge base , This image is for the convenience of your study and research , The copyright of this article belongs to Wuyun knowledge base !
边栏推荐
- Vulkan-官方示例解读-Shadows(光栅化)
- Go failing - expected ‘package‘, found ‘EOF‘
- Market prospect analysis and Research Report of nitrogen liquefier in 2022
- Market prospect analysis and Research Report of digital line scan camera in 2022
- 什么样的人才是幸福的?
- Linq. pdf
- Google 有哪些牛逼的开源项目?
- 雷达辐射源调制信号仿真
- 6. form label
- GPS Beidou time service, NTP makes network clock synchronization more accurate
猜你喜欢

ESP series module burning firmware

MAUI 迁移指南

WPF of open source project hero alliance

2022-06-10:薯队长从北向南穿过一片红薯地(南北长M,东西宽N),红薯地被划分为1x1的方格, 他可以从北边的任何一个格子出发,到达南边的任何一个格子, 但每一步只能走到东南、正南、西南方向的
![[network] socket programming](/img/df/2afc300bfc2dd319247a4b75ef7e2c.png)
[network] socket programming

Detailed explanation of network time synchronization (NTP network timing) of video monitoring system

Sentence s, paragraph P in VIM text object

让人感到心灵平静,阳光温暖的图片

Shell script binary encryption

给孩子的国学经典
随机推荐
华生·K的秘密日记
Quartz:老而弥坚的开源任务调度框架,用起来够丝滑
如何做编程知识投资及减少知识失效的影响
MAUI 迁移指南
Chinese classics for children
Detailed explanation of network time synchronization (NTP network timing) of video monitoring system
从功能测试进阶自动化测试,熬夜7天整理出这一份3000字超全学习指南【附网盘资源】
Notes on redisson distributed lock usage
Simulation of radar emitter modulated signal
雷达辐射源调制信号仿真(代码)
Source Insight 4.0设置注释与反注释的快捷键
pmm监控oracle
[cnn]| translation invariance
PMM monitoring Oracle
B - 刷墙 (C语言)
手工测试转不了自动化测试,缺的是什么?
Docker swarm installs redis cluster (bitnami/redis cluster:latest)
Large factory outsourcing or self research company? How to choose a job for a tester?
Shell script binary encryption
Market prospect analysis and Research Report of programmable digital temperature regulator in 2022