当前位置:网站首页>[Floyd] post disaster reconstruction
[Floyd] post disaster reconstruction
2022-07-02 01:27:00 【Code chess】
1️⃣ Title Description
Topic link :
https://www.luogu.com.cn/problem/P1119

The conscience of this problem is that the reconstruction time is sorted from small to large , And the reconstruction time of inquiry is also sorted from small to large , So we can operate forward , There is no need to sort .
2️⃣ Simple ideas
The main problem is Floyd An understanding and practice of the essence of Algorithm .
Floyd In the algorithm k It means Intermediate nodes , Taking this as the intermediate node can update the shortest distance between two points .
f [ i ] [ j ] f[i][j] f[i][j]: It stands for i To j The shortest distance
Whenever an inquiry is made , If a village is rebuilt before the time point asked , Take this village as the transit node , Update the shortest distance of all points .
Updated code :
while(a[k] <= t && k < n)
{
for(int i = 0; i < n; i++)
for(int j = 0; j < n; j++)
{
if(f[i][k] + f[k][j] < f[i][j])
f[j][i] = f[i][j] = f[i][k] + f[k][j];
}
k ++;
}
#include<bits/stdc++.h>
using namespace std;
using ll = long long;
int main()
{
ios::sync_with_stdio(false);
cin.tie(nullptr);
int n, m;
cin >> n >> m;
vector<int> a(n);
for(int i = 0; i < n; i++) cin >> a[i];
vector f(n, vector(n, 1e9));
for(int i = 0; i < n; i++) f[i][i] = 0;
for(int i = 1; i <= m; i++)
{
int a, b, c;
cin >> a >> b >> c;
f[a][b] = f[b][a] = c;
}
int q;
int k = 0;
cin >> q;
while(q--)
{
int x, y, t;
cin >> x >> y >> t;
while(a[k] <= t && k < n)
{
for(int i = 0; i < n; i++)
for(int j = 0; j < n; j++)
{
if(f[i][k] + f[k][j] < f[i][j])
f[j][i] = f[i][j] = f[i][k] + f[k][j];
}
k ++;
}
if(a[x] > t || a[y] > t) cout << -1 << "\n";
else
{
if(f[x][y] == 1e9) cout << -1 << "\n";
else cout << f[x][y] << "\n";
}
}
return 0;
}
边栏推荐
- Datawhale 社区黑板报(第1期)
- 教你白嫖Amazon rds一年并搭建MySQL云数据库(只需10分钟,真香)
- Variables and constants of go language foundation
- MySQL application day02
- I'll teach you to visit Amazon RDS for a year and build a MySQL cloud database (only 10 minutes, really fragrant)
- Based on Simulink and FlightGear, the dynamic control of multi rotor UAV in equilibrium is modeled and simulated
- ACM教程 - 快速排序(常规 + 尾递归 + 随机基准数)
- No converter found for return value of type: class
- [Obsidian] wechat is sent to Obsidian using remotely save S3 compatibility
- Edge extraction edges based on Halcon learning_ image. Hdev routine
猜你喜欢

The technology boss is ready, and the topic of position C is up to you
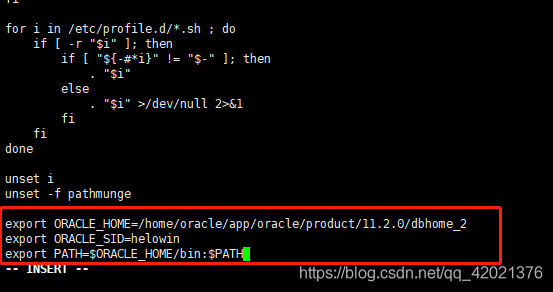
Docker installing Oracle_ 11g
![[disease detection] realize lung cancer detection system based on BP neural network, including GUI interface](/img/c9/3fe8693629a8452dcfdb4349ddee0d.png)
[disease detection] realize lung cancer detection system based on BP neural network, including GUI interface

【图像增强】基于Frangi滤波器实现血管图像增强附matlab代码

Infiltration records of CFS shooting range in the fourth phase of the western regions' Dadu Mansion

【疾病检测】基于BP神经网络实现肺癌检测系统含GUI界面
Finally got byte offer, 25-year-old inexperienced experience in software testing, to share with you

6-3 vulnerability exploitation SSH environment construction

教你白嫖Amazon rds一年并搭建MySQL云数据库(只需10分钟,真香)
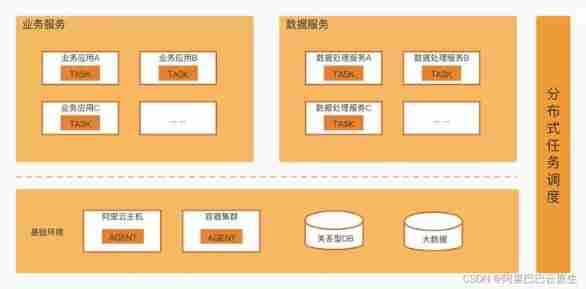
How does schedulerx help users solve the problem of distributed task scheduling?
随机推荐
[IVX junior engineer training course 10 papers to get certificates] 0708 news page production
笔者更加愿意将产业互联网看成是一个比消费互联网要丰富得多的概念
技术大佬准备就绪,话题C位由你决定
Datawhale community blackboard newspaper (issue 1)
关于ASP.NET CORE使用DateTime日期类型参数的一个小细节
[IVX junior engineer training course 10 papers] 06 database and services
8.8.4-PointersOnC-20220215
Part 29 supplement (XXIX) basis of ECMAScript
Shell Function
Learning notes 25 - multi sensor front fusion technology
Altium designer measure distance (ctrl+m)
Global and Chinese market of picture archiving and communication system (PACS) 2022-2028: Research Report on technology, participants, trends, market size and share
Basic usage of shell script
Learn C language from scratch day 025 (maze)
Private project practice sharing [Yugong series] February 2022 U3D full stack class 009 unity object creation
Develop a simple login logic based on SSM
No converter found for return value of type: class
学习笔记3--高精度地图关键技术(上)
Leetcode, 3 repeatless longest subsequence
Load and domcontentloaded in JS