当前位置:网站首页>Force buckle 272 Closest binary search tree value II recursion
Force buckle 272 Closest binary search tree value II recursion
2022-06-25 08:00:00 【Empress Yu】
Power button 272. The closest binary search tree value II
Given the root of a binary search tree
root、 A target valuetargetAnd an integerk, return BST Closest to target inkIt's worth . You can press In any order Return to the answer .subject Guarantee In this binary search tree, there is only one kind of k Sets of values are the closest
targetExample 1:
Input : root = [4,2,5,1,3], The target = 3.714286, And k = 2 Output : [4,3]Example 2:
Input : root = [1], target = 0.000000, k = 1 Output : [1]Tips :
- The total number of nodes in the binary tree is
n1 <= k <= n <= 10^40 <= Node.val <= 10^9-109 <= target <= 10^9source : Power button (LeetCode)
link :https://leetcode.cn/problems/closest-binary-search-tree-value-ii
Copyright belongs to the network . For commercial reprint, please contact the official authority , Non-commercial reprint please indicate the source .
The result of doing the question
adopt , Just pure tree recursion
Method 1-1: Merging recursion
Because both of them are recursive, let's divide them into small points
Merge type means to push directly from the child result to the father , Merge the results of parent-child merging
1. Before calculating the left subtree n individual , Before calculating the right subtree n individual , Add in the middle 2n+1 individual , The part beyond , By deleting the far left and right nodes
class Solution {
public List<Integer> closestKValues(TreeNode root, double target, int k) {
Deque<Integer> ans = new LinkedList<>();
if(root == null) return new ArrayList<>();
List<Integer> left = closestKValues(root.left,target,k);
List<Integer> right = closestKValues(root.right,target,k);
ans.addAll(left);
ans.add(root.val);
ans.addAll(right);
if(ans.size()<=k){
return new ArrayList<>(ans);
}
while (ans.size()>k){
double d1 = Math.abs(ans.getFirst()-target);
double d2 = Math.abs(ans.getLast()-target);
if(d1>d2){
ans.removeFirst();
}else{
ans.removeLast();
}
}
return new ArrayList<>(ans);
}
}Method 1-2: Sliding window recursion
Keep... In the window k There is a feasible solution
1. The order in a binary search tree is equivalent to traversing an ordered array
2. front k Direct access
3. If exceeded k individual , Check if the larger value is closer to , If not, just quit , If yes, remove the first one and add a current value
class Solution {
List<Integer> result = new LinkedList<>();
public List<Integer> closestKValues(TreeNode root, double target, int k) {
dfs(root,target,k);
return result;
}
public void dfs(TreeNode root, double target, int k) {
if (root == null) return ;
dfs(root.left,target,k);
if (result.size() < k || Math.abs(result.get(0) - target) > Math.abs(root.val - target)) {
if(result.size()==k) result.remove(0);
result.add(root.val);
dfs(root.right,target,k);
}
}
}边栏推荐
猜你喜欢

Electronics: Lesson 010 - Experiment 8: relay oscillator

socket问题记录

Opencv minimum filtering (not limited to images)

Tips on how to design soft and hard composite boards ~ 22021/11/22

Vscode is good, but I won't use it again
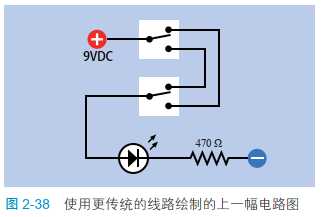
电子学:第008课——实验 6:非常简单的开关

How to resize an image in C #
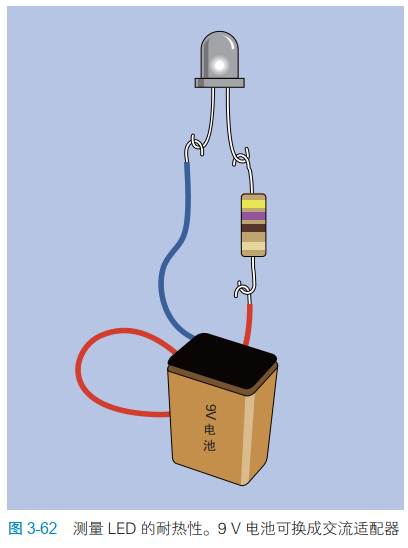
电子学:第012课——实验 13:烧烤 LED

PCB board design - automatic layout 2021-10-15

Pcb|about FPC reinforcement type
随机推荐
Analysis and utilization of Microsoft Office Word remote command execution vulnerability (cve-2022-30190)
WebSocket的理解以及应用场景
417-二叉树的层序遍历1(102. 二叉树的层序遍历、107.二叉树的层次遍历 II、199.二叉树的右视图、637.二叉树的层平均值)
【补题】2021牛客暑期多校训练营6-n
新版USBCAN卡CAN分析仪的CAN&CANFD综合测试分析软件LKMaster主要功能介绍
50. pow (x, n) - fast power
DNS协议及其DNS完整的查询过程
时钟刻度盘的绘制
Do you know why the PCB produces tin beads? 2021-09-30
VSCode很好,但我以后不会再用了
PCB board design - automatic layout 2021-10-15
电子学:第010课——实验 9:时间与电容器
力扣76题,最小覆盖字串
取消word文档中某些页面的页眉
Solving some interesting problems with recurrence of function
使用Adobe Acrobat Pro调整PDF页面为统一大小
年后求职找B端产品经理?差点把自己坑惨了......
TCP的那点玩意儿
FM信号、调制信号和载波
Importer des données dans MATLAB
