当前位置:网站首页>SQL injection vulnerability (x) secondary injection
SQL injection vulnerability (x) secondary injection
2022-06-22 06:26:00 【A τθ】
One 、 The secondary injection
The second injection loophole is a kind of Web Forms of security vulnerabilities that exist widely in applications . Compared to a single injection vulnerability , Second injection vulnerabilities are more difficult to detect , But it has
The same attack power as an injection attack vulnerability .
1、 The principle of secondary injection
When inserting data into database for the first time , Just used addslashes Or with the help of get_magic_quotes_gpc The special characters are escaped ,
however addslashes One feature is that although parameters will be added after filtering “\” Transference , however “\” It's not inserted into the database , When writing to the database, it is still
Keep the original data .
After storing the data into the database , Developers think the data is credible . The next time you need to query , The dirty data is directly extracted from the database , no
The next step of inspection and treatment , This will cause SQL The second injection of .
For example, when inserting data for the first time , Data with single quotation marks , Directly inserted into the database ; Then in the next use, in the process of patching , A secondary injection is formed .
The principle of secondary injection , It is mainly divided into two steps :
First step : Insert malicious database
When inserting data into the database for the first time , Escape only special characters in it , When writing to the database, the original data is retained , however , The data itself contains malicious
Content .
The second step : Quoting malicious data
After storing the data in the database , Developers think the data is credible . When the next query is needed , Took malicious data directly from the database , There is no further
Step checksum processing .
This results in sql The secondary injection .

Two 、 Conduct secondary injection in black box environment
First determine whether the tested website is filtered , Generally, the website will filter the input parameters , Then look for places where malicious data may be brought into secondary use .
For example, user registration -> Change Password 、 Email registration -> Change Password 、 Article addition -> Article editor . Find all function points that have secondary use . Secondary injection test SQL Inject , The secondary injection
Most of them are character injection , So pay attention to the closure problem .
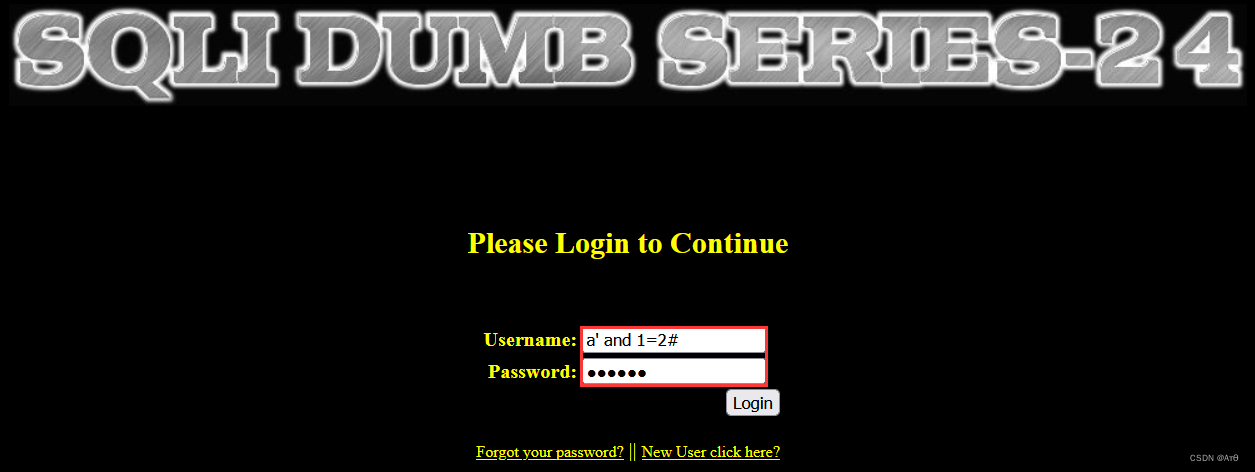
Register users now a’, Then register users separately a' and 1=1# 、a' and 1=2# And where it might trigger .
1、 View the account number in the database 、 password
mysql> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| challenges |
| cms |
| mysql |
| performance_schema |
| security |
+--------------------+
6 rows in set (0.00 sec)
mysql> use security;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
mysql> show tables;
+--------------------+
| Tables_in_security |
+--------------------+
| emails |
| referers |
| uagents |
| users |
+--------------------+
4 rows in set (0.00 sec)

2、 Secondary injection experiment
2.1、 Registered account a


2.2、 Registered account a’ and 1=1#


2.3、 By modifying the a’ and 1=1# Password , To modify the a Password




2.4、a’ and 1=2# Can't modify




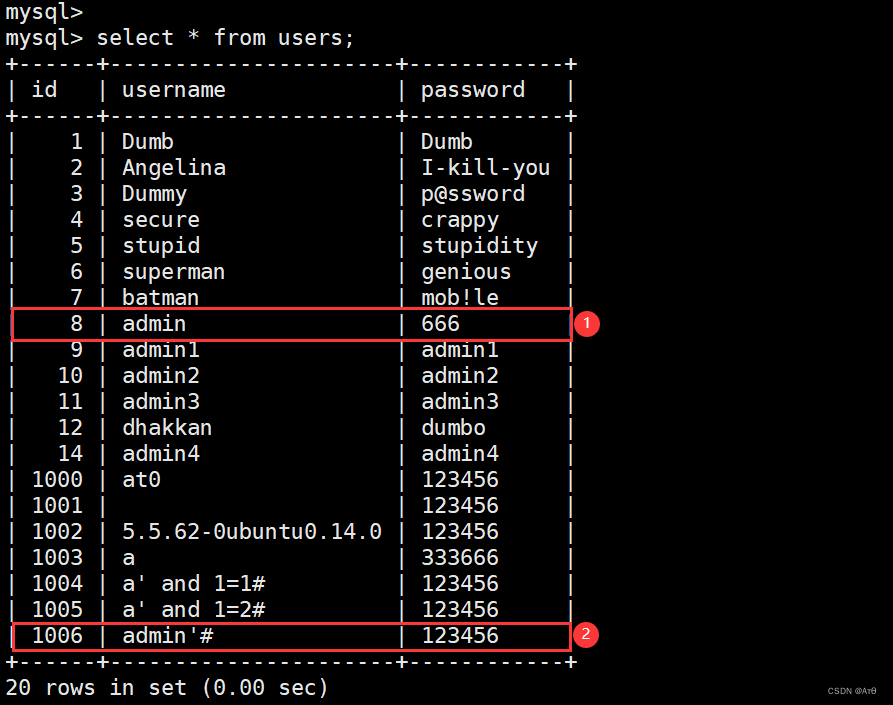
3、 modify admin Password
3.1、 Registered account admin’#



3.2、 modify admin’# password



边栏推荐
猜你喜欢
随机推荐
Expert PID control in Simulink
Using Monte Carlo method to calculate pi
SQL 注入漏洞(十二)Cookie注入
CMake 入门级别语法
[technical notes]
What is JUC
八锁问题详解
Producer and consumer issues
Configuration files required for SSM integration and error reports caused by common configuration errors
仙人掌之歌——上线运营(5)
Detailed explanation of eight locks
Cmake entry level syntax
[5g NR] UE registration management status
CGIC file upload - rookie notes
Machine learning concept sorting (no formula)
[openairinterface5g] project directory structure
5G-GUTI详解
Detailed interpretation of tab[i = (n - 1) & hash]
Information system project management - scope management (focus)
Install boost





![[5g NR] ng interface](/img/28/98e545104e4530d0e8f65e9ac993ca.png)