当前位置:网站首页>Laravel permission control
Laravel permission control
2022-07-29 00:18:00 【Ningmujun】
Add roles to the user table id, According to the character id Get user role , If it is a role, there is no need to create an intermediate table , Otherwise, you need to create an intermediate table .
According to the character id Get the role owned by the user , Get the permissions of the role according to the Chinese table of roles and permissions id, According to authority id Get the permission range of the user ,
$node_id = role_node::where('role_id', $role['id'])->get()->toArray(); $res = [];
foreach ($node_id as $v) {
$res[] = node::where('id', $v['node_id'])->first()->toArray();
}What we got here $res It is the user permissions queried , Deposit in session in , Then read the current permissions of the user in the middleware ,

This is the user permission obtained
Read the user's permission in the display homepage , Use recursion or three-level linkage , What you read is before you get it and then put it in session Authority
$res = Cache::get('auths');
$rbac = rbac::data($res);
return view('index', ['list' => $rbac]);recursive :
public static function data($data,$pid=0)
{
$res=[];
foreach ($data as $v){
if ($v['pid']==$pid){
$res[$v['id']]=$v;
$res[$v['id']]['son']=self::data($data,$v['id']);
}
}
return $res;
}Then display the obtained permissions on the home page .
边栏推荐
- 【C】 Introduction and Simulation Implementation of ATOI and offsetof
- CV instance segmentation model sketch (1)
- Centos7 install mysql8
- 1-7 解决类中方法的this指向问题
- PHP语言基础知识(超详细)
- Idea error running 'application' command line is too long solution
- 跳表的原理
- Please briefly describe the respective characteristics of list, set and map type sets (briefly describe three different inheritance methods)
- Leetcode 763. partition labels divide alphabetic intervals (medium)
- Web系统常见安全漏洞介绍及解决方案-CSRF攻击
猜你喜欢

Build SSM project with JSP as view parser

ES6 operation tutorial

Have passed hcip and joined the company of your choice, and share the learning experience and experience of Huawei certification

AutoCAD -- import excel tables into CAD and merge CAD
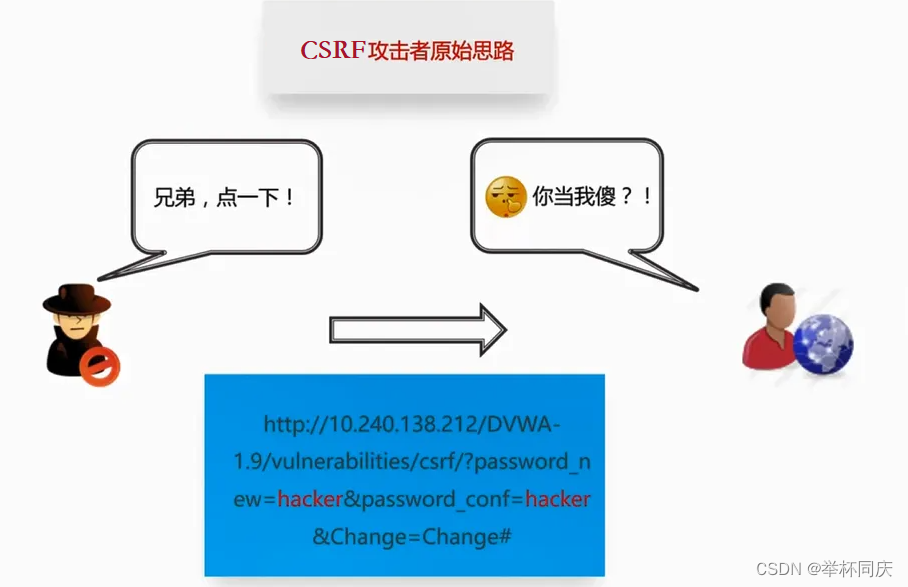
Web系统常见安全漏洞介绍及解决方案-CSRF攻击

动态规划问题(八)
Servlet运行原理_API详解_请求响应构造进阶之路(Servlet_2)

JS高级 之 ES6~ES13 新特性

IDEA报错Error running ‘Application‘ Command line is too long解决方案

EN 1873 assembly accessories for roofing - plastic single roof lamps - CE certification
随机推荐
Es6操作教程
“Method Not Allowed“,405问题分析及解决
CV semantic segmentation model sketch (2)
Opencv macro definition
Feign call fails. JSON parse error illegal character ((ctrl-char, code 31)) only regular white space (R
curl (7) Failed connect to localhost8080; Connection refused
递归/回溯刷题(下)
Application of Devops in Internet of things solutions
IDEA报错Error running ‘Application‘ Command line is too long解决方案
Servlet运行原理_API详解_请求响应构造进阶之路(Servlet_2)
Data warehouse: Doris' application practice in meituan
动态规划问题(二)
110道 MySQL面试题及答案 (持续更新)
【C】 Replace spaces and realize binary parity bit exchange of integers by macros
Leetcode62. Different paths
Sword finger offer 41. median in data flow
The difference between {} and ${}
1-7 解决类中方法的this指向问题
动态规划问题(四)
#{}和${}的区别