当前位置:网站首页>01 basic introduction - concept nouns
01 basic introduction - concept nouns
2022-07-06 20:16:00 【Richo Banno】
One 、 domain name
1. What is domain name ?
domain name ( English :Domain Name), Also known as domain , It's a string of names separated by dots Internet The name of a computer or computer unit , Used to locate and identify the computer during data transmission ( Sometimes it also refers to geographical location ).
because IP The address is not easy to remember and can not display the name and nature of the address organization , People designed domain names , And through the domain name system (DNS,Domain Name System) To combine the domain name with IP Addresses map to each other , Make it easier for people to access the Internet , Instead of remembering what can be read directly by the machine IP Address number string .
such as www.baidu.com, This is a domain name , In a nutshell ip Not easy to remember , So there are domain names to facilitate memory . You can think of the relationship between address and longitude and latitude ( Shanghai : longitude 121.48 latitude 31.22)
2. Where is the domain name registered ?
Find a website of domain name registrar ( For example, Ali. 、 Wanwang ), Search the domain name you want ( Not all domain names in China support filing , At present, the mainstream recordable domain names are :
.com, .cn, .com.cn, .net, .top, .wang, .vip, .company, .org.cn,.ac.cn, .site, .online, .ren .store, .tech, .xyz, .club, .link, .pro, .red, .info, .biz, .ltd, .gov.cn, .mobi, .city etc.
Fill in the domain name information . If you register your domain name in the name of the company , You need to fill in the enterprise information 、 Contact information ; If you are registered in your own name , Please switch to the personal column , Fill in personal information . The English information of the domain name will be automatically translated according to the Chinese you fill in , Please check whether there is any error , If there is any error, please correct it in time .
Confirm the domain name bill . Confirm the domain name registrant information 、 After the bill is correct , You can complete the registration by using Alipay or wechat scanning code to pay .
Domain name real name verification . Due to domestic laws and regulations , Real name authentication is required after domain name registration , After passing the certification, it will take effect . If the audit is wrong , Please revise it in time , Resubmit for review .
Domain name filing and binding website . If you need to go online in China , Website filing is required .
3. What is a subdomain 、 Two level domain name 、 Multilevel domain name ?
for example www.dns0755.net yes dns0755.net Subdomain , and dns0755.net again net Subdomain . The sub domain of international top-level domain name is called secondary domain name .
Such as A.com It's a domain name ,A.B.com Is a secondary domain name . The first level domain name is higher than the second level domain name , The secondary domain name is the subdomain name attached to the primary domain name , That is, the secondary domain name is the subdivision level of the primary domain name .
Through the website 【.】 Number to judge the domain name level , How many? 【.】 Just a few levels of domain names , Such as A.com It's a domain name ,A.B.com Is a secondary domain name .
Such as :baidu.com It's Baidu's top-level domain name ,zhidao.baidu.com It's a secondary domain name ,zhidao.zhidao.baidu.com It's three. ( many ) Level domain name ,*.baidu.com It's a pan domain name .
4. Domain name discovery is of great significance for security testing ?
When conducting penetration tests , When the vulnerability cannot be found in its primary domain name , You can try to test the collected sub domain names , It is possible that there will be unintended effects when testing subdomain websites , Then you can go horizontally to the main website .
Two 、DNS And CDN
1. What is? DNS?
The domain name system ( english :Domain Name System, abbreviation :DNS) Is a service of the Internet . It is used to IP A distributed database with address mapping , Make it easier for people to access the Internet .DNS Use TCP and UDP port 53. At present , The limit for the length of each level of domain name is 63 Characters , The total length of the domain name cannot exceed 253 Characters .
2. Local HOSTS And DNS The relationship between ?
Hosts Is a system file without an extension , You can use Notepad and other tools to open , Its function is to match the domain names of some commonly used websites with IP The address establishes an association “ database ”, When the user enters a web address to log in in the browser , The system will automatically start from Hosts Look for the corresponding IP Address , Once found , The system will immediately open the corresponding web page , If not found , Then the system will submit the website again DNS Domain name resolution server IP Address resolution .
It should be noted that ,Hosts The mapping of the file configuration is static , If the computer on the network changes, please update in time IP Address , Otherwise you will not be able to access .
example : To open the first cmd terminal , Enter the command ping www.baidu.com, The results are as follows :

stay hosts file ( The yellow box in the figure shows hosts File absolute path ) Finally, add the contents in the red box in the figure below , and ctrl+s preservation

Again ping www.baidu.com You will find parsing ip Become you hosts In the file ( Yes, of course , I can't visit ).

3. CDN What is it? ? And DNS The relationship between ?
CDN The full name is Content Delivery Network, The content distribution network .CDN The basic idea is to avoid the bottlenecks and links on the Internet that may affect the speed and stability of data transmission , Make content transfer faster 、 A more stable . A layer of intelligent virtual network based on the existing Internet, which is composed of node servers placed everywhere in the network ,CDN The system can connect each node according to the network traffic in real time 、 Comprehensive information such as load status, distance to the user and response time redirect the user's request to the nearest service node ( Just use DNS analysis , direct PING Will show their true IP, If you use CDN,PING Coming out IP It's not the user's reality IP It is CDN Server's IP node . Need to bypass CDN Find the truth later IP Address : expand : Judge whether it exists CDN And bypass , Finding truth IP). Its purpose is to enable users to get the required content nearby , solve Internet The state of network congestion , Improve the response speed of users to visit the website .
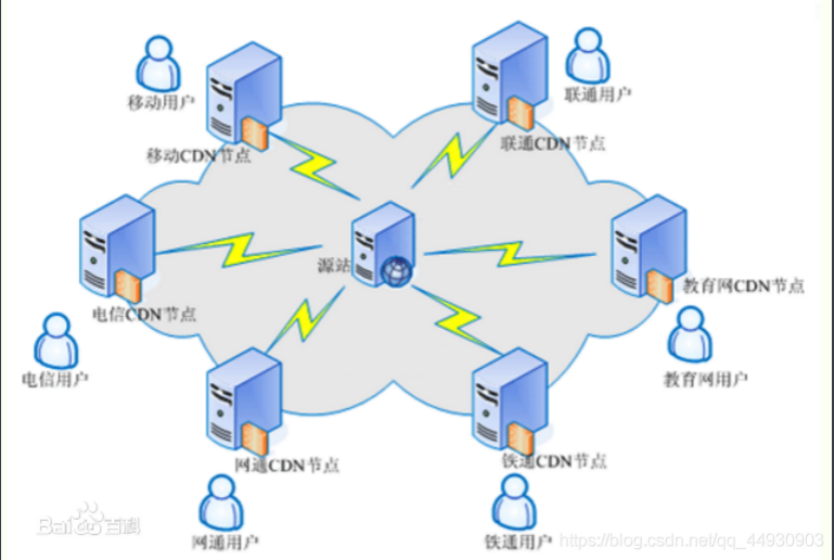
Expand :DNS and CDN The difference and connection DNS and CDN The difference and connection _ Help center - DNS.COM, domain name DNS Resolution service provider
4. common DNS What are the security attacks ?
Cache poisoning
It is also commonly known as domain name system poisoning or DNS Cache poisoning . It is the use of false Internet Replace the address in the domain name system table with the address , And then create damage . When the network user searches the page with the false address , To access a link , The web browser has opened different web links due to the influence of the false entry . under these circumstances , worm 、 Trojan horse 、 Malicious software such as browser hijacking may be downloaded to local users' computers .
DNS hijacked
DNS Hijacking is also called domain hijacking , It refers to blocking domain name resolution requests within the scope of hijacked network , Analyze the requested domain name , Release requests outside the scope of review , Otherwise return to fake IP Address or do nothing to make the request unresponsive , The effect is that you can't visit a specific network or visit a fake website . Such attacks typically change end users through malware TCP/IP Set up , Point users at malicious DNS The server , The DNS The server will resolve the domain name , And finally point to phishing websites and other servers manipulated by attackers .
Domain name hijacking
Domain name hijacking is to intercept domain name resolution requests within the hijacked network , Analyze the requested domain name , Release requests outside the scope of review , Otherwise, it directly returns false IP Address or do nothing to make the request unresponsive , The effect is that you can't visit a specific website or visit a fake website . Once your domain name is hijacked , Users are led to fake websites and can't browse the web normally , Users may be lured to fake websites for login and other operations, resulting in the disclosure of privacy data .
DNS DDoS attack
in the light of DNS Of DDoS The attack takes advantage of the real world by controlling a large number of botnets DNS The protocol stack initiates a large number of domain name query requests , Using tool software to forge the source IP Send massive DNS Inquire about , Send massive DNS The query message causes the network bandwidth to be exhausted and cannot be transmitted normally DNS Query request . Sending a large number of illegal domain name query messages causes DNS The server continues to perform iterative queries , So as to achieve the purpose of less attack traffic and consume a lot of server resources .
Reflex DNS Enlarge the attack
All amplification attacks take advantage of attackers and targets Web Bandwidth consumption differences between resources , Because every robot requires deception IP Address open DNS Parser , The IP The address has been changed to the real source of the target victim IP Address , Then the goal will start from DNS The parser receives the response . To create a lot of traffic , The attacker tried to get as far as possible from DNS The parser constructs the request by generating a response . result , The target received an amplification of the attacker's initial traffic , And their network is blocked by false traffic , Cause a denial of service .
In the face of all kinds of DNS attack , Mohist safety suggests professional advanced defense DNS Anti hijacking service , Ensure the stable operation of the server , Take time to deal with all kinds of DNS attack , Avoidable cause DNS The attack caused online business disruption , Bring great loss to the enterprise .
3、 ... and 、 Scripting language
1. What are the common types of scripting languages ?
asp php aspx jsp javaweb pl py cgi etc.
2. The relationship between different script types and security vulnerabilities ?
Different scripting languages have different rules , The vulnerabilities generated by the program are naturally different ( Code audit ).
3. Relationship between vulnerability mining code audit and script type ?
ditto
Four 、 back door
1. What is the back door ? There are those back doors ?
Backdoor programs generally refer to those program methods that bypass security control and gain access to programs or systems . Category : Webpage 、 Thread insertion 、 Expand 、C/S back door .
2. The practical significance of the back door in security testing ?
For example, the back door is hidden on the web page 、 In the software , Quietly carry out the operation that the attacker wants .
3. What you need to know about the back door ?( How to play , No killing )
No killing , In short, it means bypassing anti-virus software .
5、 ... and 、WEB
1. WEB The composition architecture model ?
Website source code : Divided into script types , Sub application direction
operating system :windows linux
middleware ( Build a platform ):apache iis tomcat nginx etc.
database :access mysql mssql oracle sybase db2 postsql etc.
2. Brief introduction to architecture vulnerability security testing ?
3. Why from WEB Level oriented ?
User contact web At most , Most of it comes from web Start with the page and slowly penetrate into the server . It's not realistic to start directly with the operating system ( In most cases, it is not accessible ).
6、 ... and 、WEB Related security vulnerabilities
- WEB Source class corresponding vulnerabilities
- SQL Inject , Upload files ,XSS, Code execution , Variable coverage , Logical loopholes , Deserialization, etc
- WEB Middleware corresponding vulnerabilities
- Unauthorized access
- WEB Database corresponding vulnerabilities
- Kernel vulnerability
- WEB System layer corresponding vulnerabilities
- Remote code execution , Raise the right
- Other third-party corresponding vulnerabilities
- Third party software vulnerabilities
- APP or PC Application binding class
- owasp top10
7、 ... and 、 The demo case
1. Enumeration and search of multi-level domain names ( principle , The way )
layer Subdomain excavator 、Maltego(kali Bring their own )、 Various websites mining sub domain names : Such as https://www.t1h2ua.cn/tools/
2. DNS Analysis after modification ( Local or service )
Put your own computer DNS Change the service to manual acquisition , And change dns( Such as the first 8.8.8.8, Again 114.114.114.114), , respectively, ping Same website , Look at the analysis ip Is it different .
3. EXE Back door functions and hazards and similar WEB back door
Quasar Backdoor program (.exe) Generate and use :exe Backdoor program generation Quasar_ 91 Security The blog of -CSDN Blog _quasar back door
web back door :beef、WSExploer Grab the bag 、wireshark Grab the bag, etc
4. APP Class combination WEB agreement ,PC Class combination WEB agreement
Burp Suite Catch app My bag , Then change the package and send it ;
Apk Data Extraction ( Android reverse tools ): Download the resources below 、 decompression , And then put a apk Put the file in apps Folder , function exe file , After that, it will generate results file ,apk The data of is right here .
8、 ... and 、 Resources involved
- Free Simulator :【 Free Android Simulator 】 Android simulator computer version _ Which Android simulator is easy to use _ Xiaoyao Android simulator download official website
- WSExplorer Caught tools :wsexplorer1.5 download -wsexplorer Download the network packet capturing tool v1.5 Green Chinese version - Network packet capturing tool - Green resource network
- Quasar Backdoor generation :Releases · quasar/Quasar · GitHub
- Apk Data Extraction :GitHub - TheKingOfDuck/ApkAnalyser: One click to extract sensitive information that may exist in Android Applications .
边栏推荐
- 腾讯T2大牛亲自讲解,跳槽薪资翻倍
- Appx code signing Guide
- Special topic of rotor position estimation of permanent magnet synchronous motor -- fundamental wave model and rotor position angle
- (3) Web security | penetration testing | basic knowledge of network security construction, IIS website construction, EXE backdoor generation tool quasar, basic use of
- Poj1149 pigs [maximum flow]
- 22-07-05 upload of qiniu cloud storage pictures and user avatars
- [Yann Lecun likes the red stone neural network made by minecraft]
- AsyncHandler
- Transformer model (pytorch code explanation)
- Linear distance between two points of cesium
猜你喜欢
Node.js: express + MySQL实现注册登录,身份认证
Redisson bug analysis
2022年6月语音合成(TTS)和语音识别(ASR)论文月报
腾讯字节阿里小米京东大厂Offer拿到手软,老师讲的真棒

Case ① | host security construction: best practice of 3 levels and 11 capabilities
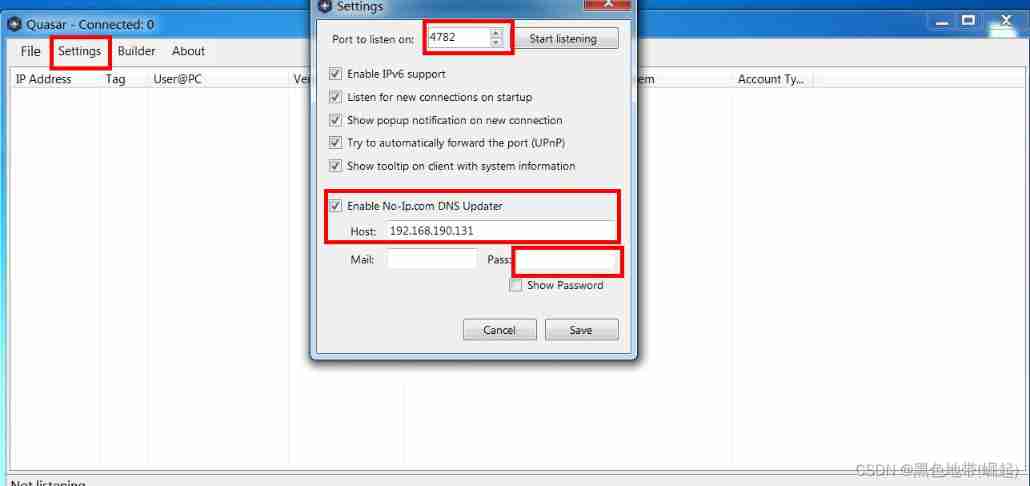
Configuration and simple usage of the EXE backdoor generation tool quasar
Standardized QCI characteristics
Tencent T3 Daniel will teach you hand-in-hand, the internal information of the factory
Vscode debug run fluent message: there is no extension for debugging yaml. Should we find yaml extensions in the market?
5. 无线体内纳米网:十大“可行吗?”问题
随机推荐
mod_wsgi + pymssql通路SQL Server座
A5000 vgpu display mode switching
腾讯T3大牛手把手教你,大厂内部资料
方法关键字Deprecated,ExternalProcName,Final,ForceGenerate
Node. Js: express + MySQL realizes registration, login and identity authentication
Cesium Click to draw a circle (dynamically draw a circle)
新一代垃圾回收器—ZGC
Introduction of Xia Zhigang
数字三角形模型 AcWing 1018. 最低通行费
Example of applying fonts to flutter
Groovy基础语法整理
JS get browser system language
范式的数据库具体解释
OceanBase社区版之OBD方式部署方式单机安装
技术分享 | 抓包分析 TCP 协议
02 基础入门-数据包拓展
JVM_ Common [interview questions]
Method keywords deprecated, externalprocname, final, forcegenerate
Technology sharing | packet capturing analysis TCP protocol
New generation garbage collector ZGC