当前位置:网站首页>How to manage device authorization
How to manage device authorization
2022-06-29 01:36:00 【CNSINDA_ HK】

In recent years , Computer and Internet applications have been popularized and developed in China , Has penetrated into every corner of society , The government , economic , military , social , Culture and people's life are increasingly dependent on computers and networks , E-government , Paperless office 、MIS、ERP、OA And other systems are also widely used in enterprises and institutions . In the highly competitive electronic and information technology products industry , Products that many companies have worked hard to develop , It was cracked by competitors soon after it was put on the market , The time and cost of product cracking are getting lower and lower , In many industries, there are more imitations than products with their own property rights , Seriously damaged the rights and interests of product developers . At present, the most effective way to protect software and hardware products is to bind encryption chips , It can effectively prevent unauthorized access or copying of on-chip programs , It can also prevent unauthorized use of abnormal means to copy PCB, The of the product PCB Copy completely .
Chapter two Current situation of encryption chip Common types of encryption chips The principle of encryption chip is usually divided into the following : 1) Put data inside the chip , By comparing whether the data are the same shortcoming : Easily simulated 2) The board and the encryption chip place the key at the same time ( It can be the same , Or the same after special data operation ), Encrypt random numbers at the same time ( It will not be reused ), Determine whether it is a legal chip according to the result advantage : Will not be simulated shortcoming : If the board program is broken , The encryption chip will fail 3) Some programs of the board are transplanted into the encryption chip , Call the encryption chip function when necessary advantage : Will not be simulated ; The board program is broken and the encryption chip is not broken , Will not affect program security shortcoming : The high cost , User workload increases , Users need to develop security chip programs , In mass production, it is necessary to build a download program environment . There are still problems Through the encryption chip , Although it can reduce... To some extent PCB The risk of being copied , But the performance is low 、 Slow speed 、 Small storage space is a big problem , Can't protect AI Algorithm and other core modules . It is impossible to put all the business logic codes into the encryption chip to run .
The third chapter CBS Encryption chip enhancement module
1.CBS Overview of encryption chip enhancement module Shenxinda CBS Encryption chip enhancement module uses encryption chip ID、 Keys and algorithms , With the help of business system CPU Computing power of , Through container technology , Amplify the processing capacity of the encryption chip , Let all the logical code of business programs and their algorithms run in a protected secure container , Implement the security of the algorithm, its code and executable module , Not only the anti copy board , It can also prevent decompilation and cracking , It is also resistant to tampering and hacker attacks . CBS Security operation diagram of encryption chip enhancement module inner container CBS The encryption chip enhancement module amplifies the processing capacity of the encryption chip , The core functions are : Encryption container 、 Trusted system 、 Scene white list 、 Data protection and key management of the original encryption chip .
2.CBS Main functions of encryption chip enhancement module CBS-S Encryption chip enhancement module through container technology , Use the key of the encryption chip product to generate a unique password in the system 、 Encrypted container , Let the business system run in the container , The data is stored in a container , The container is isolated from the outside , Internally trusted , Data encryption , Ensure system security , Prevent being copied and reverse analyzed .
1) Encryption container When the system starts, the key of the encryption chip is used , Encryption generation container , And let the business program run in the container , Business data is stored in containers , The container is isolated from the outside , The program files and data files in the container are not accessible from the outside . Cannot touch executable entities , Naturally, there is no reverse analysis , The container key comes from the encryption chip , Can't copy and copy board .
2) Trusted system The container is signed at the kernel level CA Calibration Technology , Sign and authenticate the system application in the container , Implement unsigned processes or processes with inconsistent signatures ( Forgery process ) Unable to run , Eliminate viruses , The operation of the Trojan horse , Make sure OS Layer security .
3) Scene white list The container is set through the white list , Form a program 、 Whitelist scenarios associated with files , All operations outside the scene are prohibited , Even system administrator privileges , The same strict restrictions .
4) File protection Design according to the principle of minimizing permissions , Read and write the data in the container 、 modify 、 Storage is strictly encrypted and authenticated , Only the specified business application is allowed to read / Write the specified file , Ensure file security .
5) Efficient encryption algorithm High efficiency encryption algorithm based on encryption chip is provided in the container , The operation of encryption algorithm is completely with the help of the system master CPU Conduct , Efficient , instant .
3. Use CBS Benefits of encryption chip enhancement module CBS-S The container generation of the encryption chip enhancement module depends on the key generation of the encryption chip , With non replicable characteristics , It has the following advantages :
1) Encryption container uniqueness The container is generated by the encryption chip key , Have uniqueness , Do not copy .
2) All business processes run in an encrypted container The container is an external isolation , Secure and confidential computing environment , Business program all business logic code can run in the container .
3) There is no need to modify the business logic code After the business program development is completed , No code changes required , No need to transplant , No need for additional development , Just put it directly into the container .
4) Speed and efficiency Because the program in the container is with the help of the main CPU The ability to process , So the speed is very efficient .
5) Overall anti reverse engineering Because the business logic and algorithm program are in the container , The container is isolated from the outside , There is no external access to business program entity files and business data , Therefore, it is impossible to reverse analyze .
Chapter four About shenxinda
Shenxinda is a high-tech enterprise focusing on research and development in the field of information security , In information leakage prevention , Active defense, etc , International leading level . The company has a development team composed of the country's top security experts , In data confidentiality , Active defense, etc , A series of research results with independent intellectual property rights have been obtained . Shenxinda products are oriented to R & D enterprises and institutions , Launch from R & D 、 compile 、 debugging 、 To product launch 、 operating , A comprehensive and three-dimensional data security solution covering all stages . We are based on years of research and development experience in the field of information security , For the domestic government 、 telecom 、 Finance 、 manufacture 、 energy 、 Customers in education and other industries provide information security solutions and risk assessment 、 Consulting and other services . At present, the main products of the company are : SDC Sandbox : The system adopts the third generation transparent encryption technology -- Kernel level defense in depth architecture , Advanced technology , Confidentiality in place , In the confidential market of R & D source code , Obvious advantages , It has successively successfully worked for several large enterprises in China (1000 Above terminal ) And state secret related organs (500 Above terminal ) The data security scheme has been implemented . MCK Mainframe reinforcement : It is specially designed for the data security risk of the server 、 Through kernel level hardening of the operating system , Can be effectively lower than the virus invasion , Hackers tamper with and hijack , Make sure the service is safe . CBS Encryption chip enhancement module ( amplifier ): It is an intelligent terminal device for security protection , Provide efficient and enhanced encryption chip function modules , Processing efficiency can be improved 1000 More than times .
The purpose is to prevent extortion virus , Mainframe reinforcement , System reinforcement , Industrial control security server anti-virus , Business system anti-virus , Server intrusion prevention , Production line anti-virus , Industrial computer encryption , Industrial computer reinforcement , Server data security , Industrial control system host safety , Device encryption , Industrial computer anti-virus , Industrial computer encryption , Algorithm encryption , Program encryption anti copy , Super dongle , Device anti cracking , Equipment authorization management , Device antivirus , Industrial computer authorization management , Smart device encryption
The purpose is to prevent extortion virus , Mainframe reinforcement , System reinforcement , Industrial control security server anti-virus , Business system anti-virus , Server intrusion prevention , Production line anti-virus , Industrial computer encryption , Industrial computer reinforcement , Server data security , Industrial control system host safety , Device encryption , Industrial computer anti-virus , Industrial computer encryption , Algorithm encryption , Program encryption anti copy , Super dongle , Device anti cracking , Equipment authorization management , Device antivirus , Industrial computer authorization management , Smart device encryption
The purpose is to prevent extortion virus , Mainframe reinforcement , System reinforcement , Industrial control security server anti-virus , Business system anti-virus , Server intrusion prevention , Production line anti-virus , Industrial computer encryption , Industrial computer reinforcement , Server data security , Industrial control system host safety , Device encryption , Industrial computer anti-virus , Industrial computer encryption , Algorithm encryption , Program encryption anti copy , Super dongle , Device anti cracking , Equipment authorization management , Device antivirus , Industrial computer authorization management , Smart device encryption
The purpose is to prevent extortion virus , Mainframe reinforcement , System reinforcement , Industrial control security server anti-virus , Business system anti-virus , Server intrusion prevention , Production line anti-virus , Industrial computer encryption , Industrial computer reinforcement , Server data security , Industrial control system host safety , Device encryption , Industrial computer anti-virus , Industrial computer encryption , Algorithm encryption , Program encryption anti copy , Super dongle , Device anti cracking , Equipment authorization management , Device antivirus , Industrial computer authorization management , Smart device encryption
The purpose is to prevent extortion virus , Mainframe reinforcement , System reinforcement , Industrial control security server anti-virus , Business system anti-virus , Server intrusion prevention , Production line anti-virus , Industrial computer encryption , Industrial computer reinforcement , Server data security , Industrial control system host safety , Device encryption , Industrial computer anti-virus , Industrial computer encryption , Algorithm encryption , Program encryption anti copy , Super dongle , Device anti cracking , Equipment authorization management , Device antivirus , Industrial computer authorization management , Smart device encryption
The purpose is to prevent extortion virus , Mainframe reinforcement , System reinforcement , Industrial control security server anti-virus , Business system anti-virus , Server intrusion prevention , Production line anti-virus , Industrial computer encryption , Industrial computer reinforcement , Server data security , Industrial control system host safety , Device encryption , Industrial computer anti-virus , Industrial computer encryption , Algorithm encryption , Program encryption anti copy , Super dongle , Device anti cracking , Equipment authorization management , Device antivirus , Industrial computer authorization management , Smart device encryption
The purpose is to prevent extortion virus , Mainframe reinforcement , System reinforcement , Industrial control security server anti-virus , Business system anti-virus , Server intrusion prevention , Production line anti-virus , Industrial computer encryption , Industrial computer reinforcement , Server data security , Industrial control system host safety , Device encryption , Industrial computer anti-virus , Industrial computer encryption , Algorithm encryption , Program encryption anti copy , Super dongle , Device anti cracking , Equipment authorization management , Device antivirus , Industrial computer authorization management , Smart device encryption
The purpose is to prevent extortion virus , Mainframe reinforcement , System reinforcement , Industrial control security server anti-virus , Business system anti-virus , Server intrusion prevention , Production line anti-virus , Industrial computer encryption , Industrial computer reinforcement , Server data security , Industrial control system host safety , Device encryption , Industrial computer anti-virus , Industrial computer encryption , Algorithm encryption , Program encryption anti copy , Super dongle , Device anti cracking , Equipment authorization management , Device antivirus , Industrial computer authorization management , Smart device encryption

边栏推荐
- Analysis of sending principle of OData metadata request for SAP ui5 application
- PAT甲级真题1165
- Callback function of unity after importing resources
- Typescript (6) function
- 7-29 delete substring in string (non KMP)
- QT基於RFID管理系統(可應用於大多數RFID管理系統)
- Linux7 (centos7) setting oracle11 boot auto start
- 2022年启牛商学院证券账户开户安全的嘛?
- How can multidimensional analysis pre summary work?
- How many locks are added to an update statement? Take you to understand the underlying principles
猜你喜欢

Testing until you're 35? The 35 + test will lead to unemployment?

Typescript (6) function
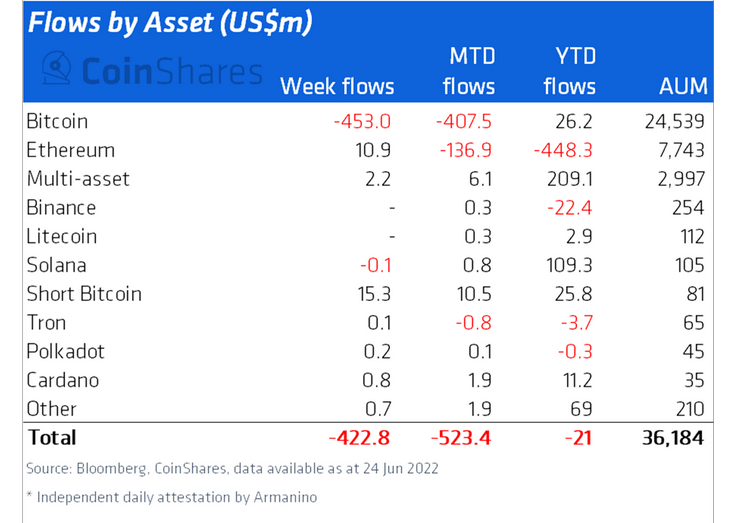
机构加密资产产品上周流出4.23亿美元资金,创历史新高

How can multidimensional analysis pre summary work?

To the interface problems we have encountered

Installing Oracle database in docker

致我们曾经遇到过的接口问题

ASP. Design and implementation of net+sql online alumni list

Finally understand the difference between DOM XSS and reflection XSS

Rasa对话机器人之HelpDesk (五)
随机推荐
Streaming media cluster application and configuration: how to deploy multiple easycvr on one server?
Stm32l4xx serial port log configuration analysis
In MySQL database, the two data written when creating tables with foreign keys are the same. Do I copy them or fail to display them
Kuboardv3 and monitoring kit installation
Typescript (7) generic
多维分析预汇总应该怎样做才管用?
Docker中安裝Oracle數據庫
Statistical learning method (3/22) k-nearest neighbor method
独家分析 | 软件测试关于简历和面试的真实情况
一种全面屏手势适配方案
有了这款工具,自动化识别验证码再也不是问题
Typescript (4) interface
Count the number of different palindrome subsequences in the string
What is the difference between immunohistochemistry and immunohistochemistry?
C语言课程设计------食品仓库管理系统
大厂裁员潮下,测试人员路在何方?
Docker中安装Oracle数据库
免疫组化和免疫组学之间的区别是啥?
利用kubernetes资源锁完成自己的HA应用
Werewolf kill casual game wechat applet template source code / wechat game source code