在进行配置之前,我们大概了解一下ike1(Cisco 中的isakmp)和ike2 的区别.
The negotiation process is different.
IKEv1
IKEv1协商安全联盟主要分为两个阶段.
IKEv1阶段1的目的是建立IKE SA,它支持两种协商模式:主模式和野蛮模式.主模式用6条ISAKMP消息完成协商.野蛮模式用3条ISAKMP消息完成协商.野蛮模式的优点是建立IKE SA的速度较快.但是由于野蛮模式密钥交换与身份认证一起进行无法提供身份保护.
IKEv1阶段2的目的就是建立用来传输数据的IPSec SA,通过快速交换模式(3条ISAKMP消息)完成协商.
IKEv2
IKEv2简化了安全联盟的协商过程.IKEv2正常情况使用2次交换共4条消息就可以完成一个IKE SA和一对IPSec SA,如果要求建立的IPSec SA大于一对时,每一对SA只需额外增加1次交换,也就是2条消息就可以完成.
Different authentication methods.
IKEv2支持EAP身份认证.IKEv2可以借助认证服务器对远程接入的PC、手机等进行身份认证、分配私网IP地址.IKEv1无法提供此功能,必须借助L2TP来分配私网地址.
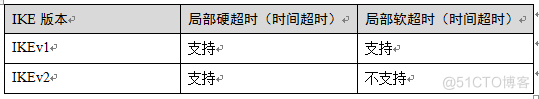
IKE SA的完整性算法支持情况不同.
IKE SA的完整性算法仅IKEv2支持,IKEv1不支持.
DPD中超时重传实现不同.
retry-interval参数仅IKEv1支持.表示发送DPD报文后,如果超过此时间间隔未收到正确的应答报文,DPD记录失败事件1次.当失败事件达到5次时,删除IKE SA和相应的IPSec SA.直到隧道中有流量时,两端重新协商建立IKE SA.
对于IKEv2方式的IPSec SA,超时重传时间间隔从1到64以指数增长的方式增加.在8次尝试后还未收到对端发过来的报文,则认为对端已经下线,删除IKE SA和相应的IPSec SA.
IKE SAManual adjustment function of timeout time支持不同.
IKEv2的IKE SA软超时为硬超时的9/10±一个随机数,所以IKEv2一般不存在两端同时发起重协商的情况,故IKEv2不需要配置软超时时间.
IKE SAManual adjustment function of timeout time
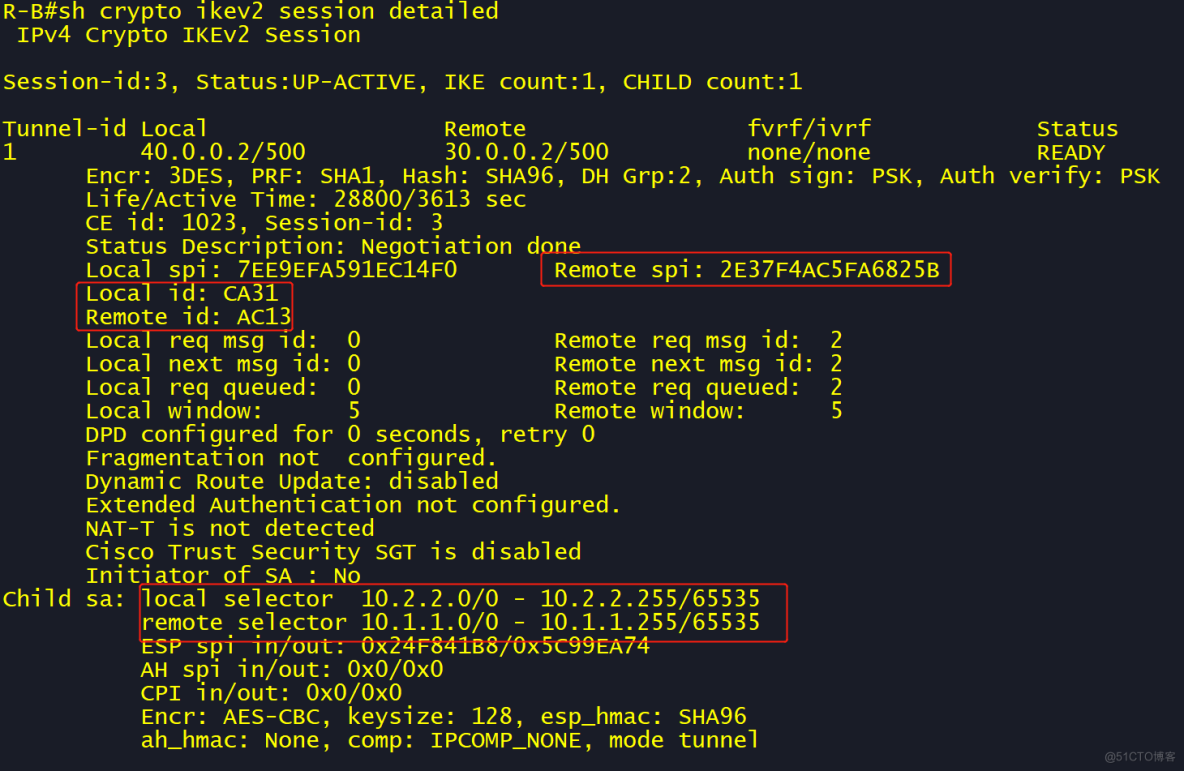
拓扑如下
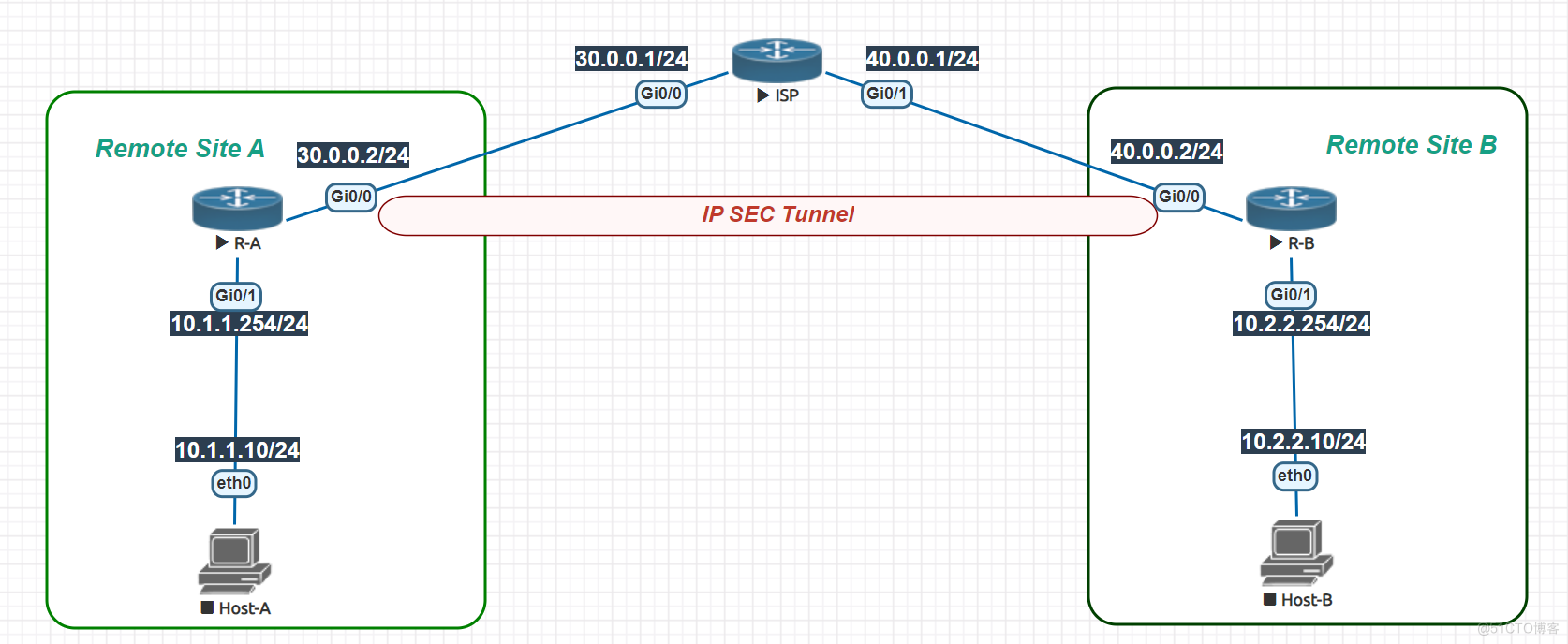
R-A 配置:
hostname R-A
crypto ikev2 proposal A-C-proposal
encryption 3des aes-cbc-128 des
integrity sha1
group 2
crypto ikev2 policy A-C-policy
proposal A-C-proposal
crypto ikev2 keyring A-C-key
peer C
address 40.0.0.2
pre-shared-key local 123456
pre-shared-key remote 123456
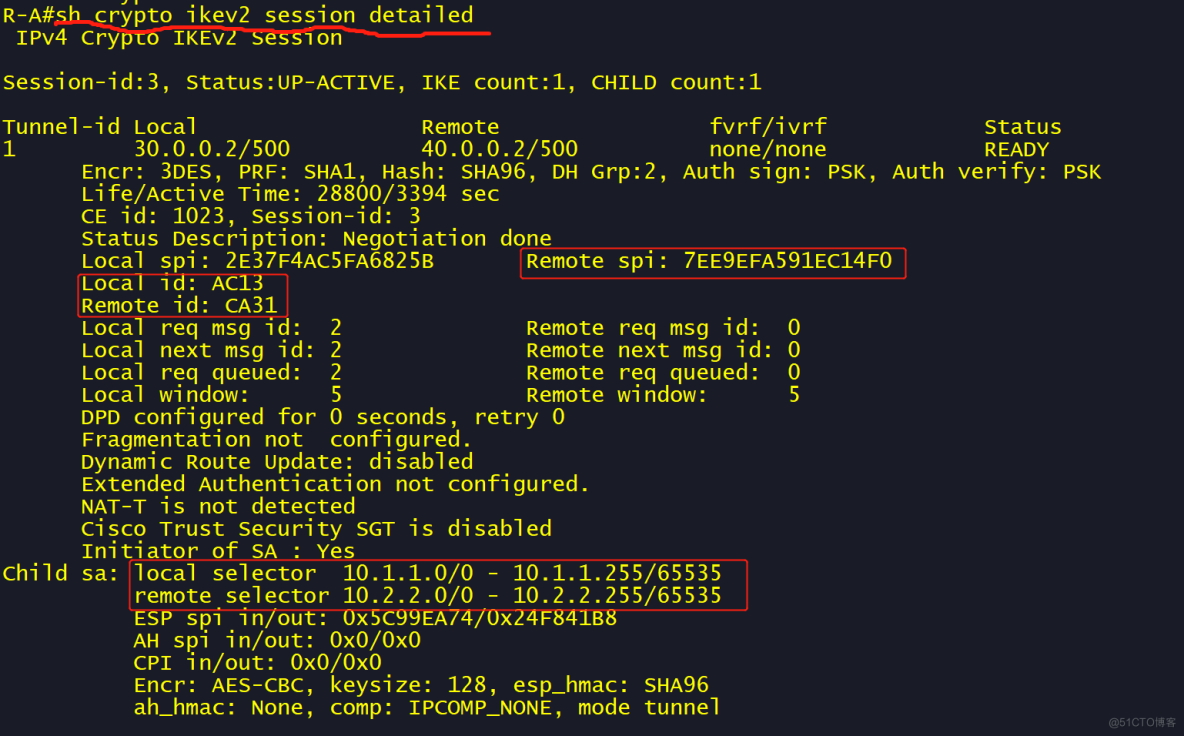
crypto ikev2 profile A-C-profile
match address local interface GigabitEthernet0/0
match identity remote fqdn CA31
identity local fqdn AC13
authentication remote pre-share
authentication local pre-share
keyring local A-C-key
lifetime 28800
crypto ipsec transform-set myset esp-aes esp-sha-hmac
mode tunnel
crypto identity ID
fqdn AC13
crypto map cm-vpn 10 ipsec-isakmp
set peer 40.0.0.2
set security-association lifetime seconds 28800
set transform-set myset
set pfs group2
set ikev2-profile A-C-profile
match address 100
interface GigabitEthernet0/0
ip address 30.0.0.2 255.255.255.0
duplex auto
speed auto
media-type rj45
crypto map cm-vpn
interface GigabitEthernet0/1
ip address 10.1.1.254 255.255.255.0
duplex auto
speed auto
media-type rj45
interface GigabitEthernet0/2
no ip address
shutdown
duplex auto
speed auto
media-type rj45
interface GigabitEthernet0/3
no ip address
shutdown
duplex auto
speed auto
media-type rj45
ip forward-protocol nd
no ip http server
no ip http secure-server
ip route 0.0.0.0 0.0.0.0 30.0.0.1
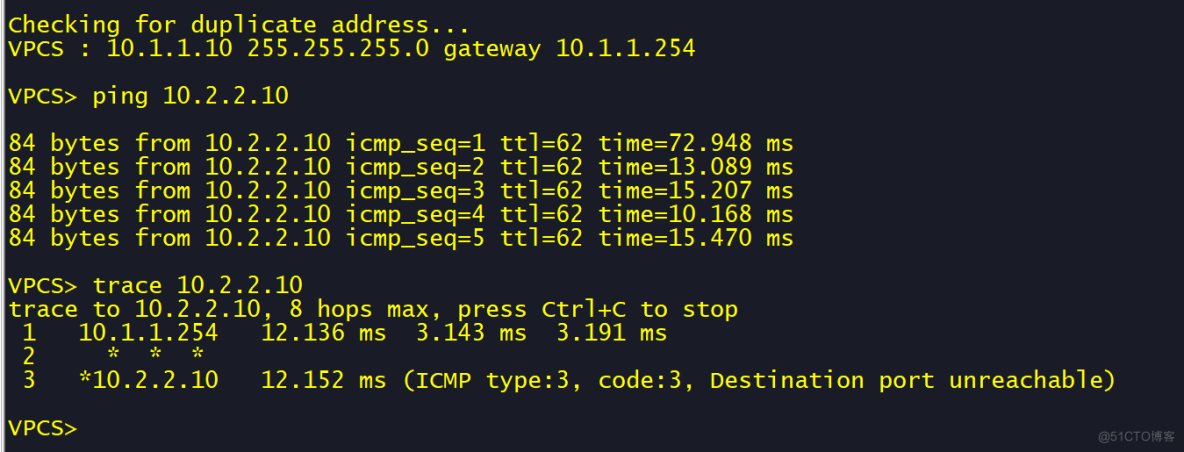
access-list 100 permit ip 10.1.1.0 0.0.0.255 10.2.2.0 0.0.0.255
- 1.
- 2.
- 3.
- 4.
- 5.
- 6.
- 7.
- 8.
- 9.
- 10.
- 11.
- 12.
- 13.
- 14.
- 15.
- 16.
- 17.
- 18.
- 19.
- 20.
- 21.
- 22.
- 23.
- 24.
- 25.
- 26.
- 27.
- 28.
- 29.
- 30.
- 31.
- 32.
- 33.
- 34.
- 35.
- 36.
- 37.
- 38.
- 39.
- 40.
- 41.
- 42.
- 43.
- 44.
- 45.
- 46.
- 47.
- 48.
- 49.
- 50.
- 51.
- 52.
- 53.
- 54.
- 55.
- 56.
- 57.
- 58.
- 59.
- 60.
- 61.
- 62.
- 63.
- 64.
- 65.
- 66.
- 67.
- 68.
- 69.
- 70.
- 71.
- 72.
- 73.
R-B 配置:
hostname R-B
crypto ikev2 proposal C-A-proposal
encryption 3des aes-cbc-128 des
integrity sha1
group 2
crypto ikev2 policy C-A-policy
proposal C-A-proposal
crypto ikev2 keyring C-A-key
peer A
address 30.0.0.2
pre-shared-key local 123456
pre-shared-key remote 123456
crypto ikev2 profile C-A-profile
match address local interface GigabitEthernet0/0
match identity remote fqdn AC13
identity local fqdn CA31
authentication remote pre-share
authentication local pre-share
keyring local C-A-key
lifetime 28800
crypto ipsec transform-set myset esp-aes esp-sha-hmac
mode tunnel
crypto identity ID
fqdn CA31
crypto map cm-vpn 10 ipsec-isakmp
set peer 30.0.0.2
set security-association lifetime seconds 28800
set transform-set myset
set pfs group2
set ikev2-profile C-A-profile
match address 100
interface GigabitEthernet0/0
ip address 40.0.0.2 255.255.255.0
duplex auto
speed auto
media-type rj45
crypto map cm-vpn
interface GigabitEthernet0/1
ip address 10.2.2.254 255.255.255.0
duplex auto
speed auto
media-type rj45
interface GigabitEthernet0/2
no ip address
shutdown
duplex auto
speed auto
media-type rj45
interface GigabitEthernet0/3
no ip address
shutdown
duplex auto
speed auto
media-type rj45
ip route 0.0.0.0 0.0.0.0 40.0.0.1
ip route 10.1.1.0 255.255.255.0 40.0.0.1
access-list 100 permit ip 10.2.2.0 0.0.0.255 10.1.1.0 0.0.0.255
- 1.
- 2.
- 3.
- 4.
- 5.
- 6.
- 7.
- 8.
- 9.
- 10.
- 11.
- 12.
- 13.
- 14.
- 15.
- 16.
- 17.
- 18.
- 19.
- 20.
- 21.
- 22.
- 23.
- 24.
- 25.
- 26.
- 27.
- 28.
- 29.
- 30.
- 31.
- 32.
- 33.
- 34.
- 35.
- 36.
- 37.
- 38.
- 39.
- 40.
- 41.
- 42.
- 43.
- 44.
- 45.
- 46.
- 47.
- 48.
- 49.
- 50.
- 51.
- 52.
- 53.
- 54.
- 55.
- 56.
- 57.
- 58.
- 59.
- 60.
- 61.
- 62.
- 63.
- 64.
- 65.
- 66.
- 67.
- 68.
- 69.
- 70.
- 71.
原网站版权声明
本文为[51CTO]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/215/202208032200506094.html





![[3D检测系列-PV-RCNN] PV-RCNN论文详解、PV-RCNN代码复现、包含官网PV-RCNN预训练权重及报错问题](/img/81/c929864440dc36238b3cb1deb9f112.png)