当前位置:网站首页>Epidemic data analysis platform work report [3] website deployment
Epidemic data analysis platform work report [3] website deployment
2022-06-12 04:13:00 【m0_ fifty-five million six hundred and seventy-five thousand ei】
As it is an engineering project , Therefore, our data platform must eventually be deployed to the cloud . Finally, the supplier we chose was Alibaba cloud , We'll talk about the special content about this supplier platform later . Here we will only explain the content of universality .
Deployment of the website
Let's first look at a new way :
github Managed server for .
establish github project
Create a new project . Fill in the basic information of the project , Click on Create Repository confirm .
find Github Pages Options , take Source Change it to master branch, Finally, click Save Button 
Finally get a link , Through this link, you can access github pages page .
Code clone To local , Add base code
<!DOCTYPE html>
<html>
<head>
<meta charset="utf-8" />
<meta http-equiv="X-UA-Compatible" content="IE=edge">
<title>Github Page demo</title>
<meta name="viewport" content="width=device-width, initial-scale=1">
<link rel="stylesheet" type="text/css" media="screen" href="main.css" />
<script src="index.js"></script>
</head>
<body>
<div id="main-content">
</div>
</body>
</html>
window.onload = function() {
document.getElementById('main-content').innerHTML = 'Hello, github pages :)'
}
#main-content {
font-size: 36px;
font-weight: bold;
padding: 16px;
}
> git add .
git commit -m "Add simple code"
git push
Waiting for code push After going up , It will take a few minutes to take effect . Open before accessing github pages Options url that will do .
In fact, you can also use your own computer as a server , Then map the port to the public network through a penetration intermediary .

Here is a record of the relevant knowledge about using penetration tools to deploy sites .
What is the intranet
Usually , Intranet It can be simply understood as a network created by a router , Computers connected to this network can access each other .
for instance , Suppose our network architecture is like this :

Connect directly to Xiaoming's router Upper The computer A、 The computer B、 The computer C There is no problem accessing each other , for example :
Xiao Ming is in The computer A The game server is started on , Listening port 20000
Xiaoming uses The computer B Open the game , Connect 192.168.1.2:20000
The computer B Tell the router that it wants to connect 192.168.1.2 Of 20000 port
The router knows that this address corresponds to The computer A, So we set up The computer B <-> The computer A The connection of , In this way, Xiao Ming successfully connected to the game server
Empathy , Connect to Lihua's router There is no problem for several computers on the to access each other .
We can think that several computers under Xiaoming's router are located in the same Intranet in , The computers under Lihua's router are located in Another intranet in .
Xiao Ming and Li Hua communicate with each other
When Xiaoming wants to communicate with Lihua , The problem arises . because Xiaoming's router and Lihua's router There is no direct connection between , Nor is it connected to the same parent route , They don't know how to connect to each other .
If there is a public network IP…
If the operator gives Xiaoming's router or Lihua's router The public network is allocated IP, This problem can be solved easily .
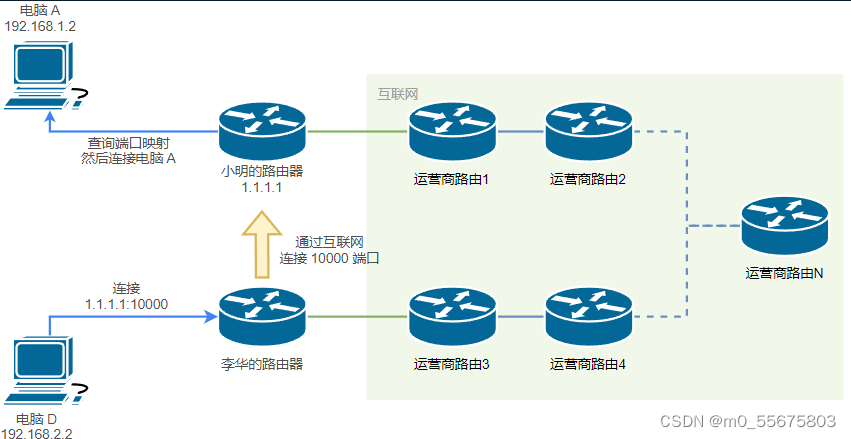
for instance , If Xiao Ming has a public network IP 1.1.1.1, Then Lihua can initiate a campaign against 1.1.1.1 The connection of :
Let's assume that Xiao Ming has configured the router 10000 This port is mapped to The computer A Game server on (20000 port )
Li Hua uses The computer D Open the game , Connect 1.1.1.1:10000
The public network is allocated IP after , Lihua's router You can tell the Internet that it wants to connect 1.1.1.1 Of 10000 port
Because of this public network IP Assigned to Xiao Ming , The router in the Internet will be established Lihua's router <-> Xiaoming's router The connection of
Next , Xiaoming's router It will query the previously configured port mapping and forward the connection to The computer A Of 20000 port
Final , The computer D <-> Xiaoming's router :10000 <-> The computer A:20000 The connection of
If there is no public network IP Well ?
because IPv4 The scarcity of addresses , Three domestic operators ( telecom 、 Move 、 Unicom ) Basically, no public network is allocated to home wide users IP, Not to mention some second tier small operators .
This causes the above connection to fail to be established , because Lihua's router Want to connect to Xiaoming's router You must tell the Internet about the other side's public network IP, But now they are not assigned to the public network IP. At this time , To establish a connection between the two, you need to use intranet penetration or UDP Hole drilling and other techniques .
title HTTP(S) Protocol penetration guide
Default port
HTTP: 80
HTTPS: 443
Confirm the target service
Please confirm that the service to be penetrated can be accessed normally before penetrating , Use the browser to access the service , Refer to the figure below to find the target IP And port :

Select tunnel type
General network providers provide two types of tunnels for penetration HTTP(S) service :
TCP Tunnel
HTTP(S) Tunnel
The difference is :
TCP Tunnel access uses http://www.example.com:12345 such URL form , need With port number , Unwanted Has its own domain name
HTTP(S) Tunnel access uses http://www.example.com such URL form , Unwanted With port number , need Has its own domain name
And there are some limitations :
Use TCP Tunnel time , If the penetration is HTTP agreement , must Use overseas nodes .HTTPS The agreement is not affected .
Use HTTP(S) Tunnel time , Real name authentication must be completed . If domestic nodes are used for penetration , You must use a registered domain name .
Set resolution
HTTP(S) The tunnel must be set with resolution ,TCP The tunnel can be set or directly used as a node IP Or node domain name
First log in to the domain name registrar , Find the modification DNS The place of analysis . Here to Godaddy For example , Because the user interfaces of various registrants are quite different , We can't enumerate . If you can't find it, you can call and ask Registrant Customer service or online search .
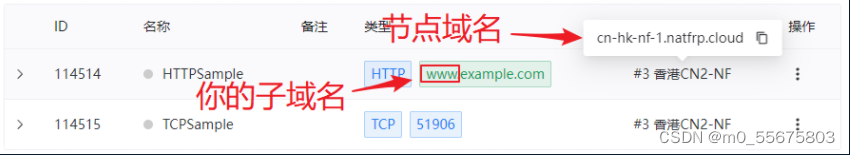
Then go to the tunnel list to find the node domain name , And confirm your subdomain name . The subdomain name here is www, If you use the root domain name directly example.com, Just treat the subdomain name as empty .
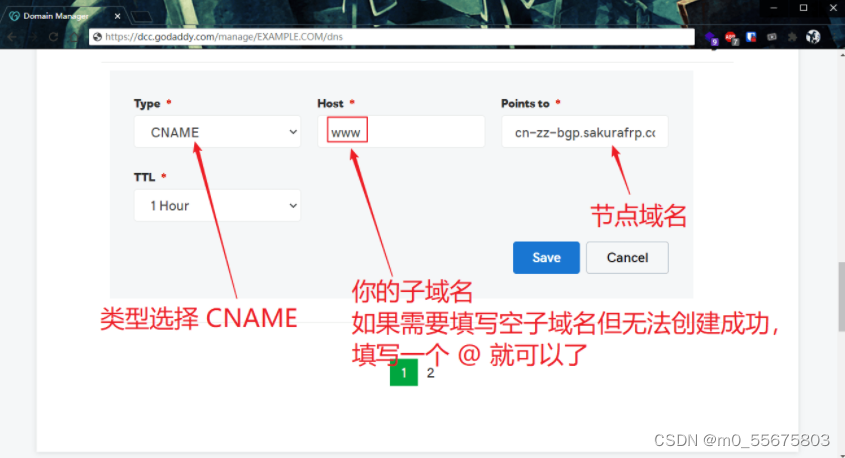
Next, you can set the resolution , Refer to the figure and fill in , The user interface of each registrar is different , But these are basically the things that need to be filled in to set the resolution .
Keep on record :
Website filing is the website's ICP Abbreviation for filing , Relevant national regulations are as follows :《 Internet Information Services 》 It is pointed out that Internet information services are divided into operational and non operational . The State adopts a licensing system for business Internet information services ; For non operating Internet information services, the filing system shall be implemented . Failing to obtain permission or fulfill the filing formalities , Do not engage in Internet information services .
Generally speaking , Filing refers to the filing of domain names , Not the server . Whether a website has been put on record , It depends on whether the space used by the website is domestic or foreign .
If it is a domestic host , The website domain name needs to be filed , To access your website through the domain name .
If it is a foreign host , The website domain name is not required to be filed , You can also access through the domain name .
Be careful : You need to purchase at alicloud 3 Only servers older than months can apply for filing (ECS Servers in ECs that are paid by volume cannot apply for filing ).
边栏推荐
- Paper recommendation: relicv2, can the new self supervised learning surpass supervised learning on RESNET?
- Manually encapsulate a foreacht and map
- 动规(15)-最低通行费
- JSP实现银柜台业务绩效考核系统
- Sed command
- Solution en cas de défaillance du script Unity
- Kinematic gauge (14) - Triangle optimal path problem
- [software tool] [original] tutorial on using VOC dataset class alias batch modification tool
- Zabbix6.0新功能Geomap 地图标记 你会用吗?
- 1. Mx6ull learning notes (II) - uboot migration
猜你喜欢

基于SSH实现健身俱乐部管理系统
MongoDB精华总结

成功解决:WARNING: There was an error checking the latest version of pip.

Eight fallacies of distributed computing

DS18B20数字温度计 (一) 电气特性, 供电和接线方式

Mysql主从搭建与Django实现读写分离

Batch automated e-mail: Vika Vige table x Tencent Qianfan scene connector has made new moves, and business communication and event marketing only need 3 steps

MySQL的check约束数字问题
Enterprise Architect v16

Goodbye to excel and PPT, I found a better visual fool software
随机推荐
DS18B20数字温度计 (一) 电气特性, 供电和接线方式
[data recovery in North Asia] data recovery in which the logical volume of the server is changed and the file system is damaged due to system reinstallation
R语言write函数:使用write函数将数据写入RStudio控制台、write函数将数据写入新的Rstudio窗口(启动新的窗口)
MySQL创建用户并授权
Kotlin协程协程作用域,CoroutineScope MainScope GlobalScope viewModelScope lifecycleScope 分别代表什么
MongoDB精华总结
怎样拥有心灵的平和?获得一颗全新的心灵
R语言plotly可视化:plotly可视化基础二维直方图、自定义设置二维直方图的颜色、二维直方图是二元分布的直方图可视化(Basic 2D Histogram)
Yyds dry inventory MySQL learning - how transactions are isolated
【FPGA混沌】基于FPGA的混沌系统verilog实现
Emperor Wu of Wei knew that he could not correct it, so he stopped offering his words
魏武帝 太祖知不可匡正,遂不复献言
分布式锁介绍
What is the difference between FOB, CIF and CFR?
Webpack--- optimization_ cache
电商中台系统架构
EN in Spacey_ core_ web_ SM installation problems
Is there a row limit for a single MySQL table
动规(15)-最低通行费
疫情数据分析平台工作报告【8.5】额外的爬虫和绘图