当前位置:网站首页>Firewall working principle and detailed conversation table
Firewall working principle and detailed conversation table
2022-06-24 22:31:00 【Zhuge iron and steel cloud】
How firewall works
How firewall works :
It's essentially looking at the conversation table .
Packets arrive at the firewall , First, check whether there will be any session table matching .
If there is a session table matching , Then match the session table forwarding .
If there is no matching session table , See if you can create a session table .
The premise is that the session table can be created only after the first package .
A. Match the routing table first .B. Then match the security policy .
TCP: SYN --------- First package
SYN+ACK
ACK
ICMP echo-request---- First package
echo-reply
UDP There is no first package concept
State detection mechanism :
When the state prick mechanism is on , The session table can be established only when the first packet passes through the device , Subsequent packets are forwarded directly by matching session table entries .
When the condition monitoring mechanism is closed , Even if the first packet does not pass through the firewall , Subsequent packages can also generate session table entries as long as they pass through the firewall .
Open command :firewall session link-state check ------- On by default
Command to turn off status detection :undo firewall session link-state check tcp/icmp
The first package establishes a session ------- Use state detection .
Status detection is mainly aimed at TCP and ICMP message
What conditions need to turn off status detection :
( scene ) Inconsistent path back and forth (SACG).
Explain the conversation table
Look at the conversation table :
View session profile
[FW1]display firewall session table --------------- View the session table profile
Current Total Sessions : 5
https VPN:public --> public 192.168.0.100:49363-->192.168.0.10:8443
agreement Virtual firewalls work source address : Source port Destination address : Target port
https VPN:public --> public 192.168.0.100:49350-->192.168.0.10:8443
tcp VPN:public --> public 10.1.1.1:49395-->192.168.1.100:17889
ftp-data VPN:public --> public 192.168.1.1:20-->10.1.1.1:49396
ftp VPN:public --> public 10.1.1.1:49393+->192.168.1.1:21
1
2
3
4
5
6
7
8
Filter sessions :
[FW1]display firewall session table servic ftp --------- Filter sessions
Current Total Sessions : 1
ftp VPN:public --> public 10.1.1.1:49393+->192.168.1.1:21
1
2
3
View session table details :
[FW1]display firewall session table verbose -------------------- View session details
ftp/ agreement VPN:public --> public/ Virtual firewalls work ID: a58f362c468281b1855c0cfa4b / The only conversation
Zone: trust--> dmz/ The safety area TTL: 00:20:00/ Aging time Left: 00:19:02/ The rest of the time
Output-interface: GigabitEthernet0/0/2 / Exit interface NextHop: 192.168.1.1/ Next jump MAC: 00-50-56-9e-ea-06/ Next jump MAC
<--packets:0 bytes:0/ Reverse flow -->packets:24 bytes:1180/ Forward flow
10.1.1.1:49393+->192.168.1.1:21/ source address Source port Destination address Target port PolicyName: trust_dmz / Match policy
+-> --------- Representative opens ASPF function
--> meaningless , Normal message
icmp VPN:public --> public ID: a58f362c6bca01d8e15c0d2721
Zone: trust--> dmz TTL: 00:00:20 Left: 00:00:19
Output-interface: GigabitEthernet0/0/2 NextHop: 192.168.1.1 MAC: 00-50-56-9e-ea-06
<--packets:4 bytes:240 -->packets:4 bytes:240
10.1.1.1:1-->192.168.1.1:2048 PolicyName: trust_dmz
10.1.1.1 :1-->192.168.1.1 :2048
Source port Destination port
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
The detailed conversation table contains 13 Item parameters .
agreement , Indicates the protocol of the session
VPN, Use in the virtual firewall
ID, Marks a unique session
ZONE( Area ), Indicate the regional trend of flow .
TTL, Aging time of the session .
Left: Session time remaining
output-interface: Exit interface
nextHop: Next jump
MAC:mac Address ,
MAC The address is full 0 The situation of :
Interface to firewall
Virtual firewall MAC It's the whole thing 0
When ARP When the request fails
Reverse flow statistics
Forward traffic statistics
Quintuples , source address : Source port –> Destination address : Destination port
Be careful :ICMP Port calculation method :
ICMP In the message Identifier Field 16 Base to zero 10 Base number , As a source port
take Type Fields and Code The value of the field does and operation , As the destination port .
for example :Type=8,Code =0; Then the target port =1000 0000 0000 & 0 = 2048
ICMP Reason with port : because ICMP State detection is required , All five tuples are required .ICMP Ports make no sense .
The port number is 0 The situation of :
When the flow is OSPF,ESP,AH Wait for the agreement , Port is 0.
PolicyName: Matching policy name
Aging time (TTL) The problem of :
The default aging time of each protocol session :
Protocol aging time agreement
20s icmp
30s dns
120s 2min qq/tftp/l2tp/udp/rip/ntp/snmp/syslog/h323
240s 4min ftp-data/GRE/AH
600s 10min SIP/HTTPS/ESP
1200s 20min HTTP/FTP/Telnet/SMTP/sqlnet/ssh/tcp/pop3/BGP
14400s 4hours sqlnet-data
summary :
TCP 20min SYN 5s SYN+ACK 5s ACK 20Min frist-fin 900s finrst 5s
UDP 2min
ICMP 20s
Be careful : When the network management firewall traffic , When web Online ,https Ageing 10min, When off web when , Show https Aging time 10s.
namely :HTTPS( Flow rate )----10min(TTL)
HTTPS( No flow )-----10s
What happens to the session table :
Aging time is up
When a virus is detected , The conversation table ages immediately , And join the blacklist
send out FIN, For the first time (frist-fin), Aging time becomes 900s( Default ), Second receipt fin(finrst ), Aging time becomes 10s.
Modification of aging time :
Well known protocol modification aging time [FW1]firewall session aging-time service-set http 2000·---- Note that the unit is S
Modification time of non well-known agreement
First step : Custom protocol
ip service-set abc type object
service 0 protocol 200
firewall session aging-time service-set abc 200
There is a problem with the session time :
Download too large FTP file , There will be an interrupt .
Access database , The operation time is longer than TCP Aging time .
Solution :
Long conversation : Default aging time 168 Hours . Be careful : Only aim at TCP.
The default session time for long sessions can be modified .
[FW1]display firewall long-link aging-time
Long-link aging-time is 168 hours
Modify the default time for long sessions
firewall long-link aging-time 20
1
2
3
4
Configure long reply steps :
To configure ACL Define the agreement
acl number 3000 rule 5 permit tcp source 10.1.1.0 0.0.0.255 destination 192.168.1.0 0.0.0.255 destination-port eq ftp
call ACL
interzone trust dmz long-link 3000 inbound
————————————————
Copyright notice : This paper is about CSDN Blogger 「 Cao Shihong's blog 」 The original article of , follow CC 4.0 BY-SA Copyright agreement , For reprint, please attach the original source link and this statement .
Link to the original text :https://blog.csdn.net/qq_38265137/article/details/88548511
边栏推荐
- Flutter-使用 typedef的注意事项
- NIO、BIO、AIO
- How to automatically remove all . orig files in Mercurial working tree?
- 解决dataframe报错ValueError: Cannot take a larger sample than population when ‘replace=False‘
- Docker 安装 Redis-5.0.12,详细步骤
- Filtered data analysis
- A girl has been making hardware for ten years. 。。
- Find the maximum value in each tree row [extension of one of the hierarchical traversals]
- How to solve the problem that the computer suddenly can't connect to WiFi
- CA Zhouji - the first lesson in 2022 rust
猜你喜欢

Uncover the secret of station B. is it true that programmers wear women's clothes and knock code more efficiently?
Common voting governance in Dao
Description of software version selection of kt6368a Bluetooth dual-mode transparent chip

The profound meaning of unlimited ecological development in Poka -- Multidimensional Interpretation of parallel chain
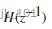
Filtered data analysis

Seven principles of software design

FANUC机器人_KAREL编程入门学习(1)

Ansible basic configuration

Redis-跳表
Flutter-使用 typedef的注意事项
随机推荐
LINQ query collection class introductory cases Wulin expert class
NIO 零拷贝
Flutter 库冲突问题解决
Industrial development status of virtual human
Kubevela v1.2 release: the graphical operation console velaux you want is finally here
Learning notes 23-- basic theory of multi-sensor information fusion (Part I)
CA Zhouji - the first lesson in 2022 rust
Cannot find reference 'imread' in 'appears in pycharm__ init__. py‘
如何提取网页中的日期?
try-with-resources 中的一个坑,注意避让
虚拟人的产业发展现状
OA system -- save the verification code to session
Servlet详解
leetcode:55. 跳跃游戏【经典贪心】
leetcode:515. 在每个树行中找最大值【无脑bfs】
使用Aggregated APIServer扩展你的kubernetes API
socket(2)
ansible基本配置
leetcode:45. 跳跃游戏 II【经典贪心】
磁盘的结构