当前位置:网站首页>Web Security (4) -- XSS attack
Web Security (4) -- XSS attack
2020-11-07 20:56:00 【Coxhuang】
List of articles
- XSS attack
- #1 What is? XSS attack
- #2 reflective XSS
- #3 Storage type XSS
- #4 DOM Based XSS
- #5 defense XSS Several strategies for
- #5 XSS And CSRF difference
XSS attack
#1 What is? XSS attack
XSS(Cross Site Scripting) The full name of attack is cross site scripting attack , To avoid cascading style sheets CSS(Cascading Style Sheets) confusion , Therefore, the cross-site scripting attack is abbreviated as XSS.
XSS An attack is when a hacker passes through HTML Inject Tampering with the web , Insert malicious script , So when users browse the web , An attack that controls the browser
XSS Attacks are divided into the following categories :
- reflective XSS
- Storage type XSS
- DOM Based XSS
#2 reflective XSS
reflective XSS principle : reflective XSS Generally speaking, an attacker entices the victim to access a malicious code in a specific way URL. This URL The first half is a normal visit to a site ( Such as : Microblogging ) The server address of , and URL There is malicious code in the parameter of , When the user clicks this URL after , You will normally visit the microblog server , If this interface of the server happens to be URL The parameter of is returned to the user , At this point, the malicious code will run on the user's browser , If the content of malicious code is to get the site Cookie, And send it to the attacker's server , Then the attacker can get the user's Cookie.
reflective XSS About the steps :
- The attacker is in normal URL( Microblog interface ) Add malicious attack code to the following parameters ( The content of the code is to get the microblog on the user's browser Cookie)
- When the user opens the URL When , Microblog server will malicious code from URL Remove from , Spliced in html And return to the browser .
- The user's browser performs parsing after receiving the response , The malicious code will also be executed to .
- The attacker steals user data and sends it to the attacker's website through malicious code . The attacker will get, for example cookie Etc , And then use that information to impersonate the behavior of legitimate users , Call the target website interface to perform attacks and other operations .
#3 Storage type XSS
Storage type XSS principle : An attacker injects malicious code into the database of a site ( Such as : Inject malicious code into the comment area of Weibo ), When a user visits a comment , The microblog server will return the malicious code to the user , At this point, the malicious code will be executed on the user's browser , And steal user information
Storage type XSS About the steps :
- The attacker submits the malicious code to the target website database ( You can go through the comment area / Message board Injection ).
- When the user opens the target website , The website server takes the malicious code out of the database , Then splice it to html Back to browser .
- After receiving the response, the user's browser parses and executes , Then the malicious code will be executed .
- So after the malicious code is executed , You can get user data , Like the one above cookie Etc , Then put the cookie Send to the attacker's website , So the attacker gets it cookie Then it will impersonate the user's behavior , Call the target website interface and other illegal operations .
How to prevent :
- The backend needs to filter the submitted data .
- The front end can also do something about it , For example, yes. script label , Replace special characters with HTML Code these, etc .
#4 DOM Based XSS
DOM Based XSS principle : Client's js Can be on the page dom Nodes operate dynamically , For example, insert 、 Modify the content of the page . For example, the client is from URL To extract data and execute it locally 、 If the data entered by the user on the client contains malicious js Script words , But these scripts don't do any filtering , Then our application is likely to get DOM-based XSS The attack of .
DOM Based XSS About the steps :
- The client of a certain site just has a function , obtain URL Parameters in , Also on DOM Nodes operate dynamically
- After receiving the response, the user's browser parses and executes . Front end use js Take out url And execute .
- Execution time , Malicious code steals user data and sends it to the attacker's website , Then the attacker's website gets the data to act as a user's behavior operation . Call the target web interface Perform some of the attacker's actions .
obtain URl Parameters of , The client inserts the parameters into the tag , If the parameter is malicious code , The following will happen :
<script>
...
document.body.innerHTML = "<a href='"+url+"'>"+url+"</a>";
...
</script>
[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-69WgyJkX-1584915853871)(https://raw.githubusercontent.com/Coxhuang/yosoro/master/20200323061021.png)]
#5 defense XSS Several strategies for
- The browser takes the initiative XSS distinguish ,Chrome The browser will automatically recognize XSS Attack code
- The server filters the user's input
How to deal with the server :
- Will be important cookie Marked as http only, In this case Javascript Medium document.cookie Statement cannot get cookie 了
- On data html encode Handle , Filter or remove special Html label
- Filter JavaScript Label of event . for example “οnclick=”, “onfocus” wait
#5 XSS And CSRF difference
- CSRF The attack is when a user has logged in to a site , And in Cookie Before the expiration date , Induce users to click on malicious Links , In this way, you can access some interfaces on the server side of the site as a user ( Such as : bank transfer )
- XSS The attack is through malicious links or injection of malicious code into the server , To get users cookie Etc
Participation of this paper Tencent cloud media sharing plan , You are welcome to join us , share .
版权声明
本文为[Coxhuang]所创,转载请带上原文链接,感谢
边栏推荐
- Practice of Xiaoxiong school development board: real equipment access of smart street lamp sandbox experiment
- 某618大促项目的复盘总结
- C language I blog assignment 03
- 建议患者自杀,OpenAI警告:GPT-3用于医疗目的风险太高
- Dynamic programming -- state compression DP of set represented by binary
- [C + + learning notes] how about the simple use of the C + + standard library STD:: thread?
- DOM节点操作
- Awk implements SQL like join operation
- Ac86u KX Online
- Static + code block + polymorphism + exception
猜你喜欢
What kind of technical ability should a programmer who has worked for 1-3 years? How to improve?

On the coverage technology and best practice of go code

Improvement of maintenance mode of laravel8 update

Using pipe() to improve code readability in pandas
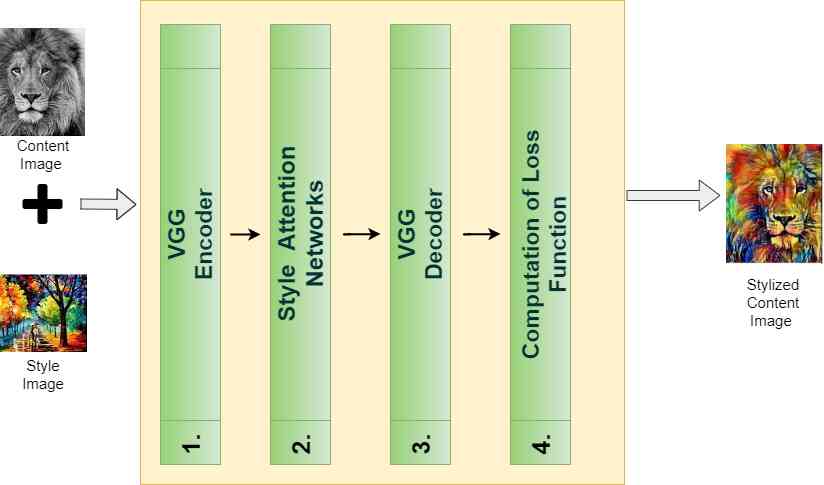
Insight -- the application of sanet in arbitrary style transfer
数据库基本操作

laravel8更新之维护模式改进
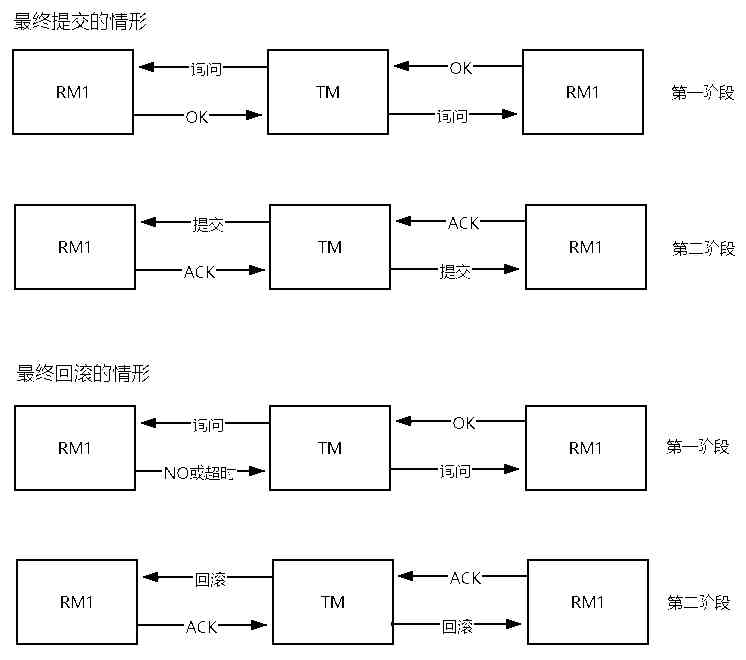
一万四千字分布式事务原理解析,全部掌握你还怕面试被问?
![[original] the influence of arm platform memory and cache on the real-time performance of xenomai](/img/cb/0395507ece572556b2bab373f013a5.jpg)
[original] the influence of arm platform memory and cache on the real-time performance of xenomai

什么都2020了,LINQ查询你还在用表达式树
随机推荐
Design pattern of facade and mediator
awk实现类sql的join操作
你可能不知道的Animation动画技巧与细节
Insight -- the application of sanet in arbitrary style transfer
聊一聊数据库中的锁
Got timeout reading communication packets解决方法
Adobe Lightroom /Lr 2021软件安装包(附安装教程)
WPF 关于绘图个人总结
Share several vs Code plug-ins I use everyday
模型预测准确率高达94%!利用机器学习完美解决2000亿美元库存难题
What kind of technical ability should a programmer who has worked for 1-3 years? How to improve?
Cpp(二) 创建Cpp工程
How did I lose control of the team?
Analysis of kubernetes service types: from concept to practice
Get started, GIT
分享几个我日常使用的VS Code插件
Practice of Xiaoxiong school development board: real equipment access of smart street lamp sandbox experiment
京淘项目day09
A detailed explanation of microservice architecture
Sentry 安装