当前位置:网站首页>Common penetration test range
Common penetration test range
2022-07-03 09:00:00 【qfliweimin】
1.DVWA
As a rookie , Usually, the first shooting range I hear of is DVWA, Deploy and simply install the corresponding version PAM(PHP-Apache-MySQL), After simple configuration, you can use .
1、DVWA Range testable vulnerability : Brute force (Brute Force)、 Command injection (Command Injection)、 Cross-site request forgery (CSRF)、 File contains (File Inclusion)、 Upload files (File Upload)、 Insecure verification code (Insecure CAPTCHA)、SQL Inject (SQL Injection)、SQL Blind note (SQL Injection Blind)、 Reflective cross site scripting attack (XSS Reflected)、 Storage type cross site scripting attack (XSS Stored)
2、 It contains many common Web Loophole , The page is very compact , Integrate vulnerabilities in different business environments , Abstract it and summarize it into an integrated shooting range , It's also easy to use , And each vulnerability page can view the current source code , To some extent, it can improve 、 Proficiency in code auditing .
3、 The range includes four levels, from easy to difficult :Low、Medium、High、Impossible.
The following figure shows the vulnerability pages mentioned above 、 View the source code function 、 Vulnerability level .

summary : Environment installation is simple 、 There are many information available online 、 You can directly view the source code, which is convenient for learning 、 Different grade gradients are more conducive to mastering vulnerabilities , It is common to learn and understand as a novice web The vulnerability is very suitable , Writing programs at ordinary times can also learn from the relevant parts of the code . But only php Language related vulnerabilities , Only common web Loophole .
2、OWASP Broken Web Applications Project
The shooting range can be directly downloaded on the official website vm Open in , Use root owaspbwa Logging in will return to the shooting range address , You can directly access the shooting range .
Range by OWASP Specially for Web A shooting range developed by safety researchers and beginners , It contains a large number of training and experimental environments with known security vulnerabilities and real Web Applications
There are many environments involved , relative DVWA It is more close to actual combat , The shooting range is not only specially designed web Vulnerability application scenarios , It also includes some common open source web Applications , relative dvwa It's not just PHP, There's also Jsp、Asp、Python Dynamic scripting language environment , And the types of vulnerabilities are also very rich , In addition to the usual web Out of the hole , It also includes access control 、 Thread safety 、 Operations hide fields 、 Control parameters 、 Weak conversation cookie、web service 、Open Authentication invalid 、 dangerous HTML Notes, etc. , Perfect for learning and practicing .
Click on ”+“ You can see some information about the corresponding module , Here's the picture .

summary : Simple installation , Rich environment , There are many kinds of coverage vulnerabilities , Close to the real environment , Suitable for practical learning .dvwa Suitable for understanding vulnerabilities and simple vulnerability exploitation ,owaspbwa It is closer to the actual complex business environment . The only regret is that it hasn't been updated since a long time ago , Now I download the old version , There is not much collection of new vulnerabilities .
3、sqli-labs
sqli-labs Contains most sql Injection type , In a breakthrough mode , about sql Inject to exploit the vulnerability . The range vulnerability type is single , But yes. sql Injection class vulnerability exploitation is very comprehensive . Installation complexity and dvwa almost , Simple installation .

4、VulHub
Vulhub It's based on docker and docker-compose A collection of vulnerability environments , Enter the corresponding directory and execute a statement to start a new vulnerability environment , Make it easier to replicate vulnerabilities , Let security researchers focus more on the vulnerability principle itself .
When you build your own environment , because linux Problems with various versions , Failed many times , One click installation basic useless , The manual installation process is also very complicated , But finally reinstall a pure linux after , Installation successful . So follow the steps , It starts a phpxxe Of docker, After the test, I found that there was no problem with the installation .
Except that the installation process took a lot of time , But it's very comfortable to use . Different environments only need to execute a command to successfully build the environment . During the installation process, I know that this is an open source vulnerability environment project , It includes many different environments , yes owaspbwa in the future , There are many kinds of vulnerabilities , A shooting range with rich environment , And the vulnerabilities collected are relatively new , Suitable for a long-term study 、 Live range . Compared with other shooting ranges , Don't care web Server version 、 Download and install , Just install one docker You can run various vulnerability environments smoothly .
边栏推荐
- [RPC] RPC remote procedure call
- 低代码起势,这款信息管理系统开发神器,你值得拥有!
- Monotonic stack -42 Connect rainwater
- Using DLV to analyze the high CPU consumption of golang process
- Markdown learning
- Deep parsing (picture and text) JVM garbage collector (II)
- Methods of checking ports according to processes and checking processes according to ports
- [rust notes] 07 structure
- ES6 promise learning notes
- 状态压缩DP AcWing 291. 蒙德里安的梦想
猜你喜欢
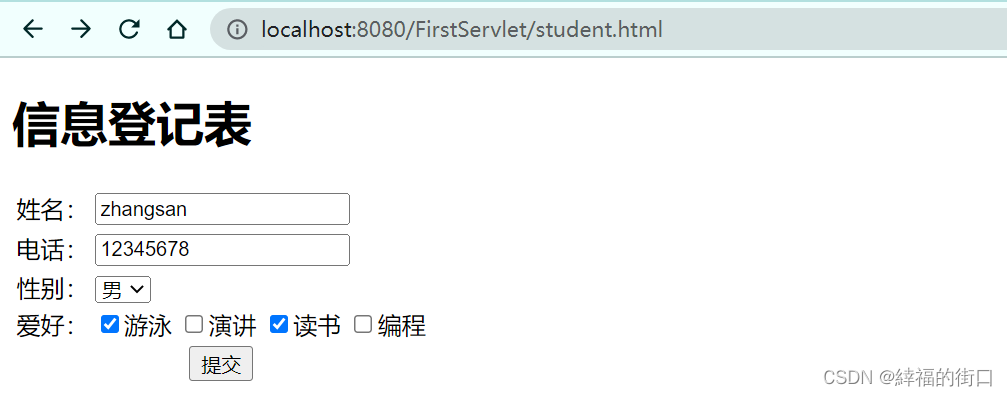
请求参数的发送和接收
LeetCode 535. TinyURL 的加密与解密

LeetCode 438. 找到字符串中所有字母异位词
![[rust notes] 02 ownership](/img/f7/74f8ea3bd697957f9ebfa3e1513fda.png)
[rust notes] 02 ownership

干货!零售业智能化管理会遇到哪些问题?看懂这篇文章就够了

高斯消元 AcWing 883. 高斯消元解线性方程组
Deeply understand the underlying data structure of MySQL index

On the setting of global variable position in C language

Phpstudy 80 port occupied W10 system
Too many open files solution
随机推荐
LeetCode 438. 找到字符串中所有字母异位词
Concurrent programming (V) detailed explanation of atomic and unsafe magic classes
Sending and receiving of request parameters
[rust notes] 13 iterator (Part 1)
Apache startup failed phpstudy Apache startup failed
LeetCode 30. 串联所有单词的子串
22-06-27 西安 redis(01) 安装redis、redis5种常见数据类型的命令
The method for win10 system to enter the control panel is as follows:
LeetCode 515. 在每个树行中找最大值
XPath实现XML文档的查询
Redux - learning notes
Introduction to the usage of getopts in shell
Annotations simplify configuration and loading at startup
LeetCode 57. 插入区间
[concurrent programming] atomic operation CAS
数位统计DP AcWing 338. 计数问题
20220630学习打卡
我們有個共同的名字,XX工
Noip 2002 popularity group selection number
[rust notes] 07 structure