当前位置:网站首页>Add anti debugging function to game or code (application level)
Add anti debugging function to game or code (application level)
2022-06-11 21:43:00 【No desire_ Kaikai】
Preface :
thank : Yidao cloud College tiger The teacher guides :
 Commissioning is divided into : Open a debug process and debug an existing process .
Commissioning is divided into : Open a debug process and debug an existing process .
DebugByCreate Called when true CreateProcess() Function to open a debug process , When DebugByCreate Called when false DebugActiveProcess(dwPID) Function to debug an existing program .
One 、 call CreateProcess() Function to open a debug process :
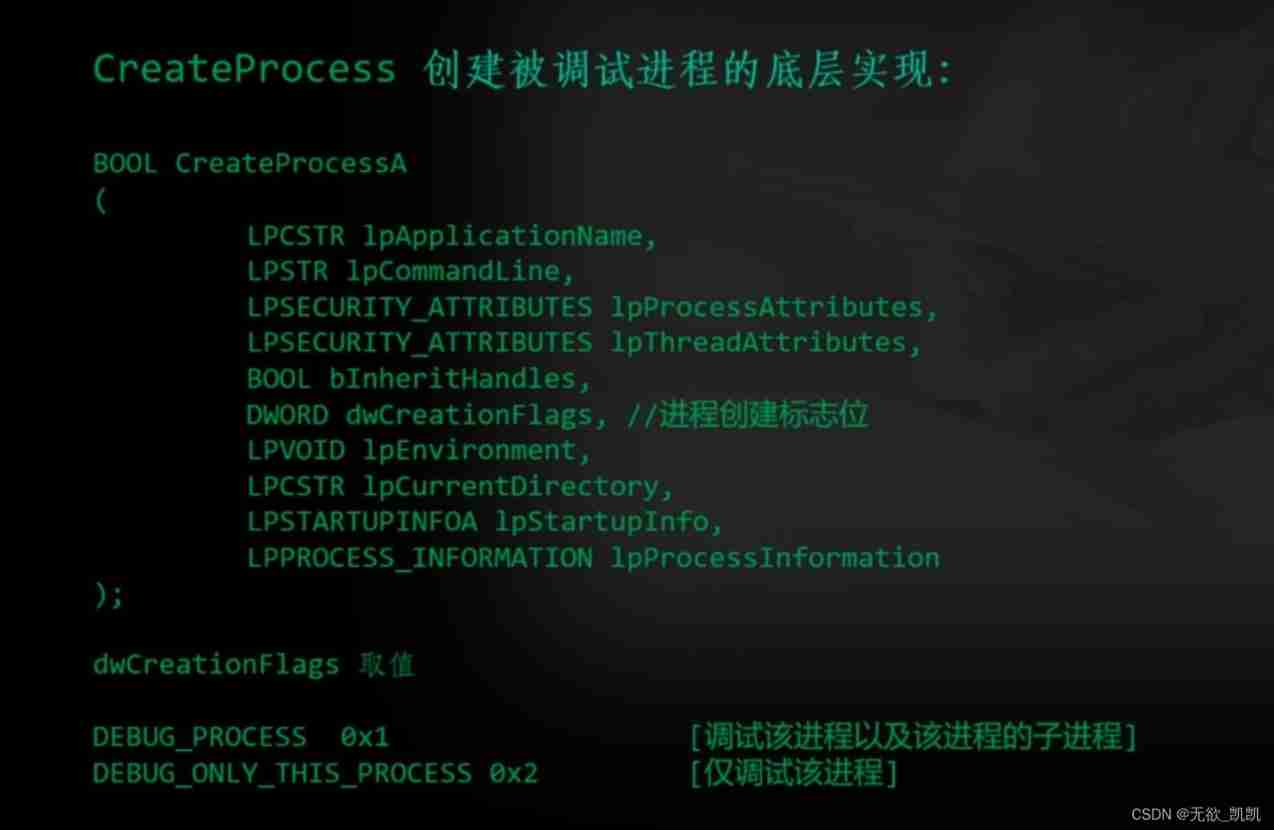 call CreateProcess() The function actually calls at the bottom :
call CreateProcess() The function actually calls at the bottom :

Two 、 call DebugActiveProcess(dwPID) Function to debug an existing program

summary :
A process is debugged , In kernel state EPROCESS Structural DebugProt It must not be for 0, In user mode PEB Structural BeinDebuged It must not be for 0.
NT TP Equal drive anti debugging principle :
Use open mode to debug :
Driver de debugging can be performed in NTCreateProcess() Set callback function at , If it is found that the process of creating debugging is the process to be protected, the function will return failure .
When debugging an existing process
Drive de debugging can take over NtOpenProcess When the function finds that it is the process it wants to protect, it directly returns failure , You can also break every subsequent step to realize the complexity of skipping anti debugging .
Because to establish a debugging relationship, you must put DebugPort And DEBUG_OBJECT Association , Then you can put DebugPort Is set to 0, It can also realize de debugging .
Implement de debugging at the user level
One 、 Setting the main thread as hidden debugging destroys the debugging channel
Use windows Unpublished function implementation this function is located in ntdll Implementation code :
typedef NTSTATUS(NTAPI* zwsetImformationThreadPtr)(DWORD, DWORD, DWORD, DWORD); // The function prototype
auto hNtDll=LoadLibrary("ntdll.dll"); // Load support module
if(hNtDll)
{
zwsetImformationThreadPtr zwsetImformationThread; zwsetImformationThread=(zwsetImformationThreadPtr)GetProcAddress(hNtDll,"zwsetImformationThread")
zwsetImformationThread((DWORD)GetCurrentThread(),0x11,0x0,0x0);// The first parameter is passed into the current thread , Second, the parameters 0X11 This means that the current thread is set to hide debugging
}
Implementation logic :
Debugger debugging program , The next breakpoint is actually written at the breakpoint int3, Then the process will break down and be handled by the debugger , We can use this function to make the current thread in non debug mode . When the debugger drops a breakpoint, it will still write at the breakpoint int3, But because we have set the current thread to no debug mode , So when the program gets here, it will crash , Realize the common function of de debugging .
Implement debugging and detection in the user layer
One 、 adopt BeinDebuged Check if it has been debugged Through the user mode PEB Structural BeinDebuged It must not be for 0. We only test PEB Structural BeinDebuged Is it 0 It can detect whether the current program is debugged . Get by assembly PEB structure : because TEB The structure address is stored in FS In the segment register . typedef struct _TEB { PVOID Reserved1[12]; PPEB ProcessEnvironmentBlock; PVOID Reserved2[399]; BYTE Reserved3[1952]; PVOID TlsSlots[64]; BYTE Reserved4[8]; PVOID Reserved5[26]; PVOID ReservedForOle; PVOID Reserved6[4]; PVOID TlsExpansionSlots; } TEB, *PTEB; TEB Prototypes of structures .
You can see TEB Structure offset 48 This is just PEB Structure pointer ,48 The hexadecimal of is 0X30 So we can write the following assembly to achieve the acquisition PEB structure
PPEB _peb;
_asm { mov eax,fs:[0x30] // obtain PEB Pointer address mov _peb,eax // Pass the address to the variable _peb }
And then determine _peb->BeingDebugged Whether bit 0 Debugging and detection can be realized .
adopt API Function to obtain BeingDebugged Value :
CheckRemoteDebuggerPresent():
IsDebuggerPresent();
Detect through the above two functions , The specific use of the function will not be introduced .
Two 、 Check whether it is debugged through kernel information
typedef NTSTATUS(NTAPI* NtQueryInformationProcessPtr)(HANDLE, DWORD, PVOID,ULONG, PULONG);
Use this function , This function is unpublished by Microsoft You need to import .
auto hNtdll = LoadLibrary(L"ntdll.dll"); NtQueryInformationProcess = (NtQueryInformationProcessPtr)GetProcAddress(hNtdll, "NtQueryInformationProcess");
Then the first parameter of this function needs to be passed in the current thread handle , The second parameter is the three values we need to know :
0x07 : take debugport value . debugport !=0 Is being debugged 0x01E: take debugobject value debugobject !=0 Is being debugged 0x01F: take debugflages value ,debugflages=0 Is being debugged
test method :
、DWORD debug_port = 0;
NtQueryInformationProcess(proce, 0x07, &debug_port, sizeof(debug_port), 0x0);
if (debug_port)return TRUE;
HANDLE debug_object = 0;
NtQueryInformationProcess(proce, 0x01E, &debug_object, sizeof(debug_object), 0x0);
if (debug_object)return TRUE;
BOOL debug_flages = 1;
NtQueryInformationProcess(proce, 0x01F, &debug_flages, sizeof(debug_flages), 0x0);
if (!debug_flages)return TRUE;
return FALSE;
边栏推荐
- Syntax of SQL
- 行而不辍,未来可期|云扩科技入选上海市专精特新企业
- Answer fans' questions | count the number and frequency of letters in the text
- 实验10 Bezier曲线生成-实验提高-交互式生成B样条曲线
- BZOJ3189 : [Coci2011] Slika
- Leetcode-322- change exchange
- Experiment 10 Bezier curve generation - experiment improvement - interactive generation of B-spline curve
- Chain storage structure of linear table
- JVM | local method interface; Native Method Stack
- 8、 BOM - chapter after class exercises and answers
猜你喜欢
![Analysis on the development history and market development status of China's system integration industry in 2020 [figure]](/img/3c/b53c2a3f59ff6784f128cb98a5a7a2.jpg)
Analysis on the development history and market development status of China's system integration industry in 2020 [figure]
LabVIEW控制Arduino实现红外测距(进阶篇—6)

EndnoteX9簡介及基本教程使用說明

Database daily question --- day 9: salesperson

Release of version 5.6 of rainbow, add multiple installation methods, and optimize the topology operation experience

The upcoming launch of the industry's first retail digital innovation white paper unlocks the secret of full link digital success

RPA super automation | nongnongji and cloud expansion accelerate financial intelligent operation

Endnotex9 introduction and basic tutorial instructions

UML系列文章(29)体系结构建模---模式和框架

Release of version 5.6 of rainbow, add multiple installation methods, and optimize the topology operation experience
随机推荐
[v2.1] automatic update system based on motion step API (repair bug, increase completion display, support disconnection reconnection and data compensation)
Servlet get form data
[Part 15] use and basic principle of forkjoinpool [key]
LabVIEW controls Arduino to realize infrared ranging (advanced chapter-6)
Expérience 10 génération de courbes bezier - amélioration expérimentale - génération de courbes B - spline par point de contrôle
Rexroth overflow valve zdb6vp2-42/315v
如何使用 SAP Kyma 控制台手动发送 SAP Commerce Cloud Mock 应用暴露的事件
Leetcode-98- validate binary search tree
[Part 16] copyonwritearraylist source code analysis and application details [key]
LeetCode-76-最小覆盖子串
js对返回的数据的各种数据类型进行非空判断。
为什么需要微服务
2021牛客多校5 Double Strings
Refresh and upgrade | innovation, starting from cloud store
Codeworks round 744 (Div. 3) problem solving Report
Realize the same length of tablayout subscript and text, and change the selected font size
A problem of setting the private library of golang
LaTex实战笔记 3-宏包与控制命令
The same efficiency tool for leading enterprises to promote smart finance. Let's have a quick look?
UML系列文章(29)体系结构建模---模式和框架