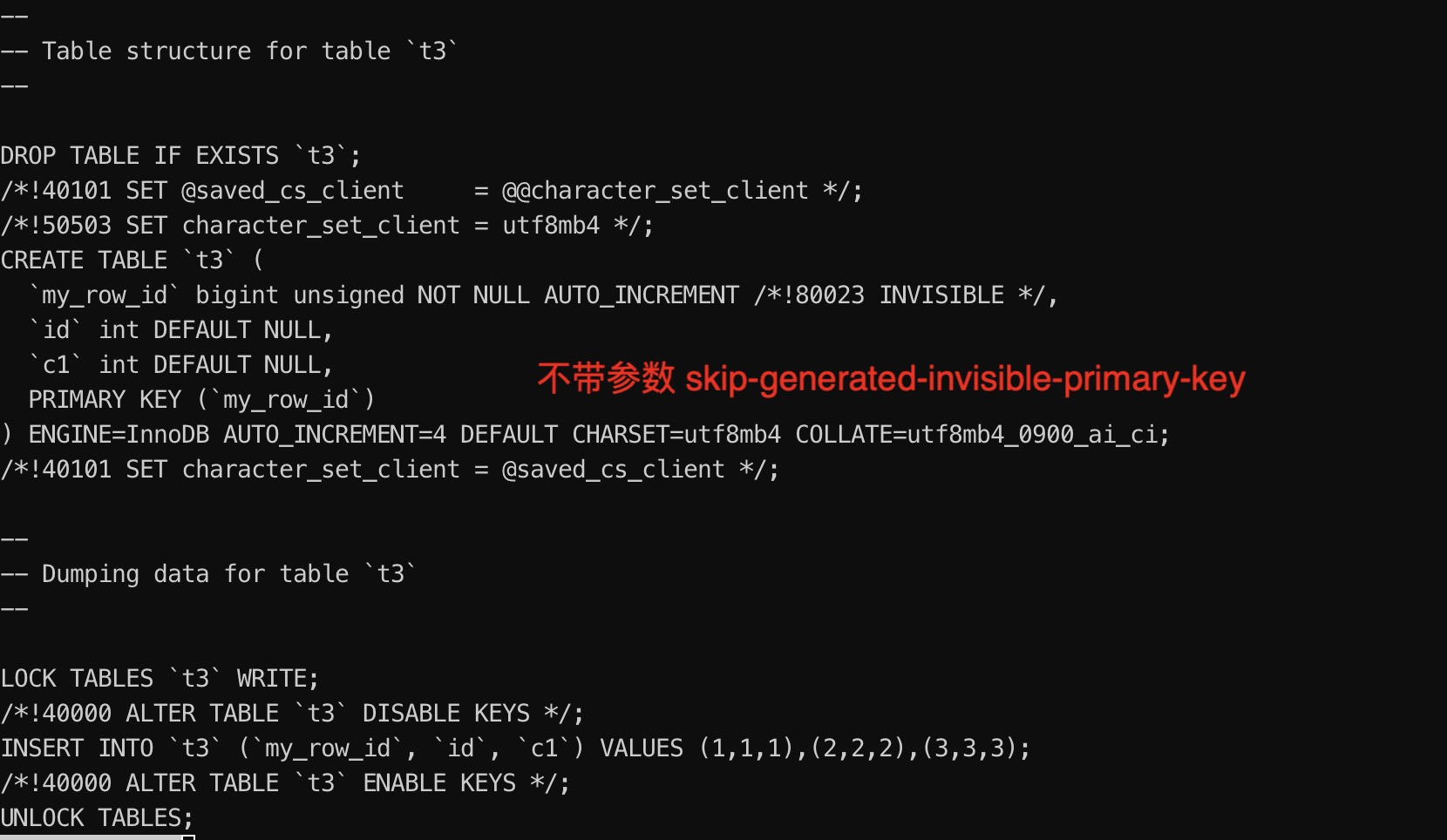
当前位置:网站首页>How to mitigate the attack of corporate account hijacking?
How to mitigate the attack of corporate account hijacking?
2022-08-02 20:57:00 【software testnet】
近日,有报道称,A new malware is pass onLinkedInAccount phishing campaign hijacks high-profileMeta Facebook Businessand ad platform accounts.研究人员表示,这种名为Ducktailof malware use browsers from authenticated user sessionscookieto take over the account,and ultimately hijack anyFacebook Business帐户,steal relevant data.

What is the account was hijacked?
帐户劫持(Account hijacking)is the act of controlling someone else's account,Is usually intended to steal personal information、Impersonate or blackmail a victim.Account hijacking as a common type of attack,执行起来却并不容易,For a successful attack,The attacker must figure out the victim's password in advance.
Corporate account is hijacked can bring huge security threats.例如,在上述“ Facebook Business account hijacked”事件中,In order to penetrate the account,攻击者针对LinkedlnUser initiated a phishing activities,The campaign uses and brands、Product and project planning related keywords to lure victims into downloading executable files containing malware along with related images、Archive files for documents and video files.
据了解,Malware fromFacebookThe specific information stolen includes:安全凭证、Personal Account Identification Information、Business details and ad account information.此外,研究人员表示,Ducktailalso allows threat actors toFacebookFull administrative control of business accounts,This could give them access to a user's credit card or other transaction data for financial gain.
虽然,The new malwareDucktailable to utilize authenticatedFacebooksession from the victimFacebookStealing information from accounts.但一般情况下,Protect corporate account,Identity and access management is still a great solution.
Learn to leverage multi-factor authentication
例如,企业可以在VPN implementation on endpoints RADIUS 认证,Requires a unique credential for access.RADIUS Authentication is much more secure than using shared credentials,But if the user credentials are unfortunately leaked,then additional protection is required.
而在这时,Multi-factor authentication comes in handy.例如,在VPN 和 RDP When the system logs in, the user is required to show the secondary authentication factor, which will further improve the security of the login process..目前,There are several types of authentication factors that already completely prevent bot brute force,and is equally effective against other targeted attacks.
同时,Businesses must also consider various methods of automating access to applications,如用于Web API的TLSMutual Authentication Certificate,and the authentication token and the usedAPI密钥.但关键问题是,To understand how users log in,and take appropriate safeguards for each access method.
访问权限管控
例如,In Enterprise Cloud Account Management,Accounting departments often require access to the payment and billing sections of the cloud vendor console.负责监视IaaSObjects in the environment of the operation engineers may not need to access the details of the billing records.其中,Which members of the accounting department can create new storage spaces、Start a new virtual instance,Or for running on serverlessPaaSfeature changes in,And which ones can't?This is access control,如“最小化权限”,Companies to take some unnecessary access is prohibited.
信任但要验证
as with treatment such asWindowsthe same as internal accounts such as domain accounts,Enterprise security managers should also periodically verify that access levels are appropriate.
Change procedures to be established for termination and work,to ensure that adjustments can be made when individuals give up or change roles;To audit the use of credentials,ensure that its role is played effectively;Also consider whether there is some tools,such as privileged identity management tools that play a role in an enterprise's access policies.其中,Privileged identity management tools help document the use of credentials,The auditing capabilities of tools such as these help document the system、Account access traces.
边栏推荐
- Wechat Gymnasium Appointment Mini Program Graduation Design Finished Works (7) Mid-term Inspection Report
- Interviewer: can you talk about optimistic locking and pessimistic locks
- How can services start smoothly under tens of millions of QPS
- LeetCode 2333. 最小差值平方和(贪心)
- Go 语言快速入门指南:第二篇 变量与常量
- 下载mysql的源码包
- Endanger the safety of common Internet attacks have?
- 今年上半年,我国公路建设总体形势持续向好
- 如何确保智能工厂的安全?
- AtomicInteger详解
猜你喜欢
随机推荐
MySQL索引
redis总结_分布式缓存
Mysql和Redis如何保证数据一致性
深圳地铁16号线二期进入盾构施工阶段,首台盾构机顺利始发
衡量软件产品质量的 14 个指标
golang刷leetcode 经典(1) LRU缓存机制
Code Inspection for DevOps
CUDA+Pycharm-gpu版本+Anaconda安装
织梦提示信息提示框美化
有关代购系统搭建的那点事
NeRF: The Secret of 3D Reconstruction Technology in the Popular Scientific Research Circle
来亲自手搭一个ResNet18网络
Wechat Gymnasium Appointment Mini Program Graduation Design Finished Works (7) Mid-term Inspection Report
究极异常处理逻辑——多层次异常的处理顺序
DevOps之代码检查
AI+医疗:使用神经网络进行医学影像识别分析
成功部署工业物联网的五个关键
POE交换机常见问题解答
My recursive never burst stack
HDF驱动框架的API(3)