当前位置:网站首页>Web security -- core defense mechanism
Web security -- core defense mechanism
2022-07-02 08:28:00 【Defeat of Fujiwara Qianhua】
Core defense mechanism
Preface
Web Basic security issues for applications ( All user input is not trusted ) A large number of security mechanisms need to be used to attack regions , These mechanisms are composed of the following core factors :
- Access control
- Filter / Limit input
- monitor ( Normal indicators )
- Safety products (WAF)
The vast majority of the attack surface of a typical application is also composed of these mechanisms , That is, attackers exploit vulnerabilities by taking advantage of the defects of these mechanisms . Now let's learn about the security mechanism .
One 、 Access control
majority Web Applications use three layers of interrelated security mechanisms to handle user access :
- Authentication
- session management
- Access control ( Realization )
Authentication
Authentication mechanism is the most basic mechanism for applications to handle user access . Verifying users refers to determining the true identity of users . today , most Web Applications use traditional authentication models , That is, users are required to submit user names and passwords , Then the application verifies it , Confirm its legitimacy
session management
After successfully logging in to the application , Users will access various pages and functions , Send some columns from the browser HTTP request . meanwhile , The server will also receive countless requests from various users . To implement effective access control , The application needs to identify and process various requests submitted by each user .
To meet the above needs , Almost all Web The application establishes a session for each user , And issue a token to the user to identify the session . The session itself is a set of data structures stored on the server , Used to track the interaction status between users and Applications . The token is a unique string , The application maps it to the session ( Such as cookie). When the user receives a token , The browser will follow HTTP Return it to the server in the request , Help the application associate the request with the user .
Access control
Two 、 Processing user input
Basic safety issues : All user input is not trusted . A lot is directed at Web Different attacks on applications are related to submitting incorrect input . Enter confirmation (input validation) Is a necessary means to defend against these attacks .
Input processing method
- Reject known bad input —— The blacklist
- Accept known normal inputs —— White list
- purify —— Input handler 、 code 、 escape
- Secure data processing —— Safe programming method ( The database access process uses correct parameterized queries , Avoid unsafe application function design )
- Syntax check —— authentication
Boundary confirmation
Each individual component or functional unit of the server-side application treats its input as input from a potentially malicious source . Except for the external boundary between the client and the server , The application performs data validation on each of the above trust boundaries .
(1) The application receives the login information of the user . The form handler confirms that each input contains only legal characters , Meet special length restrictions , And does not contain known attack signatures .
(2) The application executes a SQL Query and verify user certificate . To prevent SQL Inject , Before executing the query , The application program escapes all characters contained in the user input that can be used to attack the database .
(3) If the user logs in successfully , The reference program then transmits some data in the user data to SOAP service , Further information about user accounts . To prevent SOAP Injection attack , You need to XML Properly encode metacharacters .
(4) The application displays the user's account information in the user's browser . To prevent cross site scripting attacks , The application executes on any user submitted data implanted in the return page HTML code .
source
《 The classic of hacker attack and Defense Technology Web Actual combat 》
边栏推荐
- Get the width and height of the screen in real time (adaptive)
- C language implements XML generation and parsing library (XML extension)
- Global and Chinese market of tillage finishing machines 2022-2028: Research Report on technology, participants, trends, market size and share
- Wang extracurricular words
- Jumping | Blue Bridge Cup
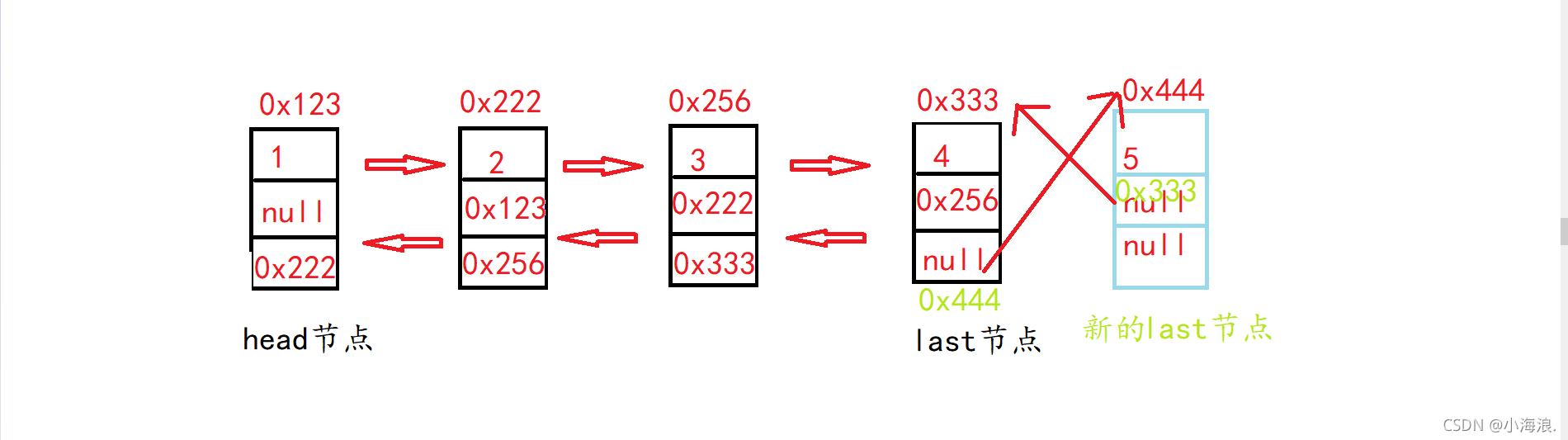
- Realize bidirectional linked list (with puppet node)
- Causes of laptop jam
- OpenCV3 6.2 低通滤波器的使用
- SQL operation database syntax
- ICMP协议
猜你喜欢
随机推荐
16: 00 interview, came out at 16:08, the question is really too
Force deduction method summary: double pointer
Analysis of the use of comparable, comparator and clonable interfaces
The source code of the live app. When the verification method is mailbox verification, the verification code is automatically sent to the entered mailbox
On November 24, we celebrate the "full moon"
什么是SQL注入
Static library and dynamic library
Carsim-問題Failed to start Solver: PATH_ID_OBJ(X) was set to Y; no corresponding value of XXXXX?
Global and Chinese market of wire loop, 2022-2028: Research Report on technology, participants, trends, market size and share
Carsim 学习心得-粗略翻译1
Find and rfind methods in string
Backup, recovery and repair of XFS file system
Carsim-实时仿真的动画同步问题
力扣每日一题刷题总结:栈与队列篇(持续更新)
HCIA—数据链路层
力扣方法总结:双指针
HCIA - application layer
Pointer initialization
樂理基礎(簡述)
Matlab other