当前位置:网站首页>ARP and ARP Spoofing
ARP and ARP Spoofing
2022-07-02 08:27:00 【Defeat of Fujiwara Qianhua】
List of articles
Preface
When a network device has data to send to another network device , You have to know the other person's Network layer address (IP Address ).IP The address is provided by the network layer , But only IP The address is not enough ,IP The data packet It must be encapsulated into frames to be sent through the data link layer . The data frame should contain the purpose MAC Address , Therefore, the sender must also obtain the purpose MAC Address .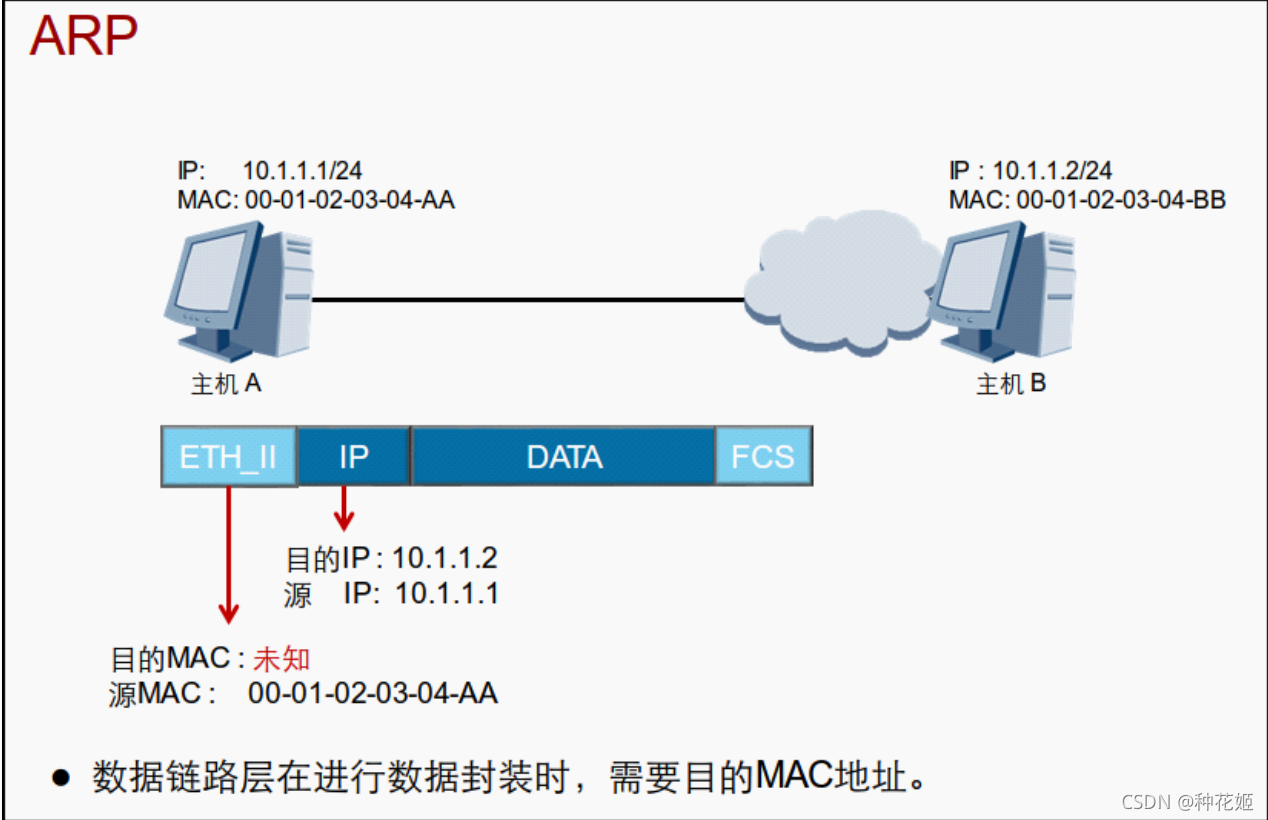
Through purpose IP Get the purpose MAC The process of address is controlled by ARP Protocol to implement .
One 、ARP What is it? ?
Address resolution protocol ,Address Resolution Protocol
host A To send a packet to the host C, Host computer A ping host C 10.0.0.3, Data is encapsulated from the upper layer , Active when reaching the network layer IP And purpose IP( May by DNS obtain ), To the data link layer , To encapsulate the source MAC And purpose MAC, Purpose MAC Unknown . that , You need to send ARP.
Two 、ARP Detailed explanation
1.ARP request
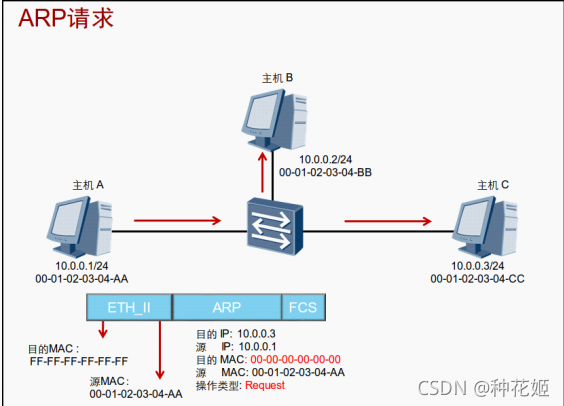
Data is encapsulated into the link layer , Found no MAC Address , Instead, encapsulate a ARP request . But it still needs one to encapsulate into frames MAC Address , Write the destination at the head of the frame MAC:FF-FF-FF-FF-FF-FF, Broadcast address , stay ARP There is a purpose in the data IP Field . Every network device receives this ARP Request package , Can extract ARP data , Match to host IP And packet purpose IP Agreement , Return the... Of the host MAC Address .
2.ARP Respond to

host C Received by the host A It's on the air ARP request , Purpose of discovery IP Consistent with this host , Returns a ARP Response packets .
3.ARP Packet format

ARP Broadcast can only be in the same network segment , Each interface of the router must be in different network segments , therefore ARP The message cannot pass through the router .
In the configuration IP Address time , The network device will send a free ARP, Used to ensure that no IP Address conflict
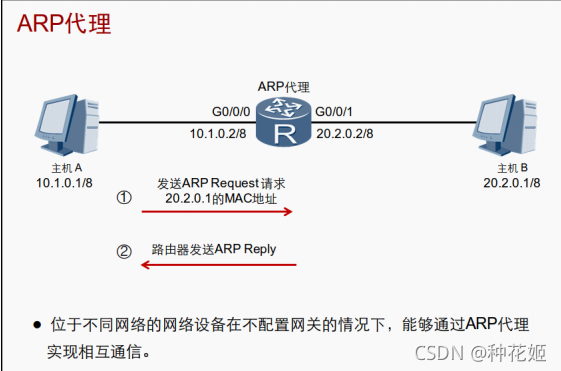
In some special cases , have access to ARP agent , Realize different network segments ARP Request
ARP cheating
ARP cheating : The attacker sent “ Without any reason ARP Respond to ” To disguise other devices , Cause communication failure
边栏推荐
- Chinese garbled code under vscade
- W10 is upgraded to W11 system, but the screen is black, but the mouse and desktop shortcuts can be used. How to solve it
- 使用Matplotlib绘制图表初步
- IP协议与IP地址
- Live broadcast platform development, flexible menu, and freely adjust the horizontal size of the menu bar
- Global and Chinese markets for conventional rubber track 2022-2028: Research Report on technology, participants, trends, market size and share
- DWORD ptr[]
- OpenCV关于x,y坐标容易混淆的心得
- Global and Chinese market of medicine cabinet 2022-2028: Research Report on technology, participants, trends, market size and share
- On the confrontation samples and their generation methods in deep learning
猜你喜欢

Comparable,Comparator,Clonable 接口使用剖析

樂理基礎(簡述)
Matlab mathematical modeling tool

How to build the alliance chain? How much is the development of the alliance chain
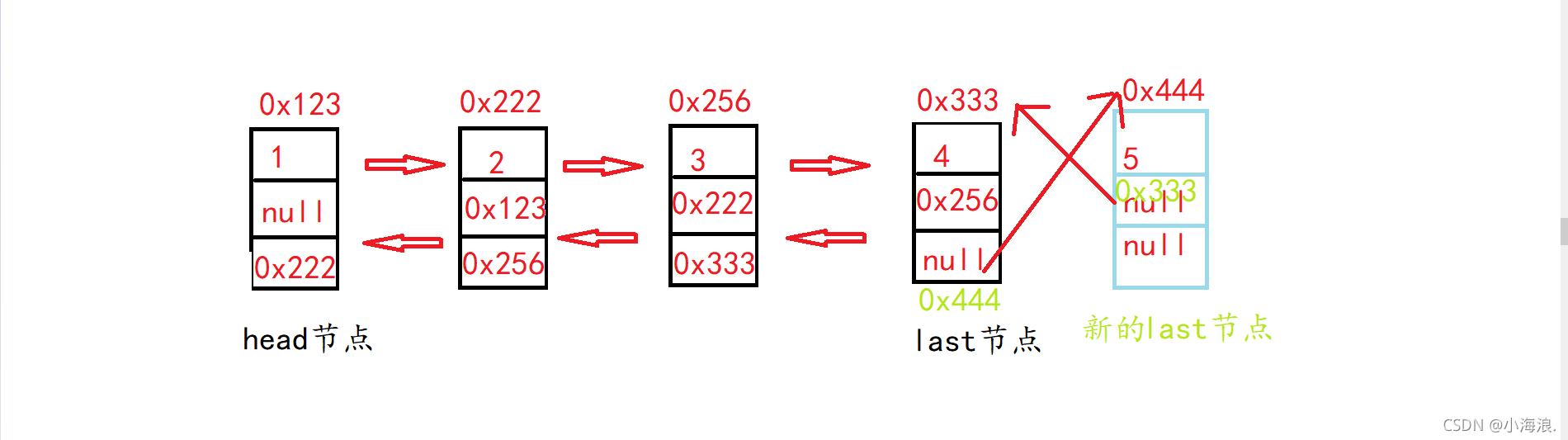
双向链表的实现(双向链表与单向链表的简单区别联系和实现)

ARP及ARP欺骗

HCIA—数据链路层
W10 is upgraded to W11 system, but the screen is black, but the mouse and desktop shortcuts can be used. How to solve it
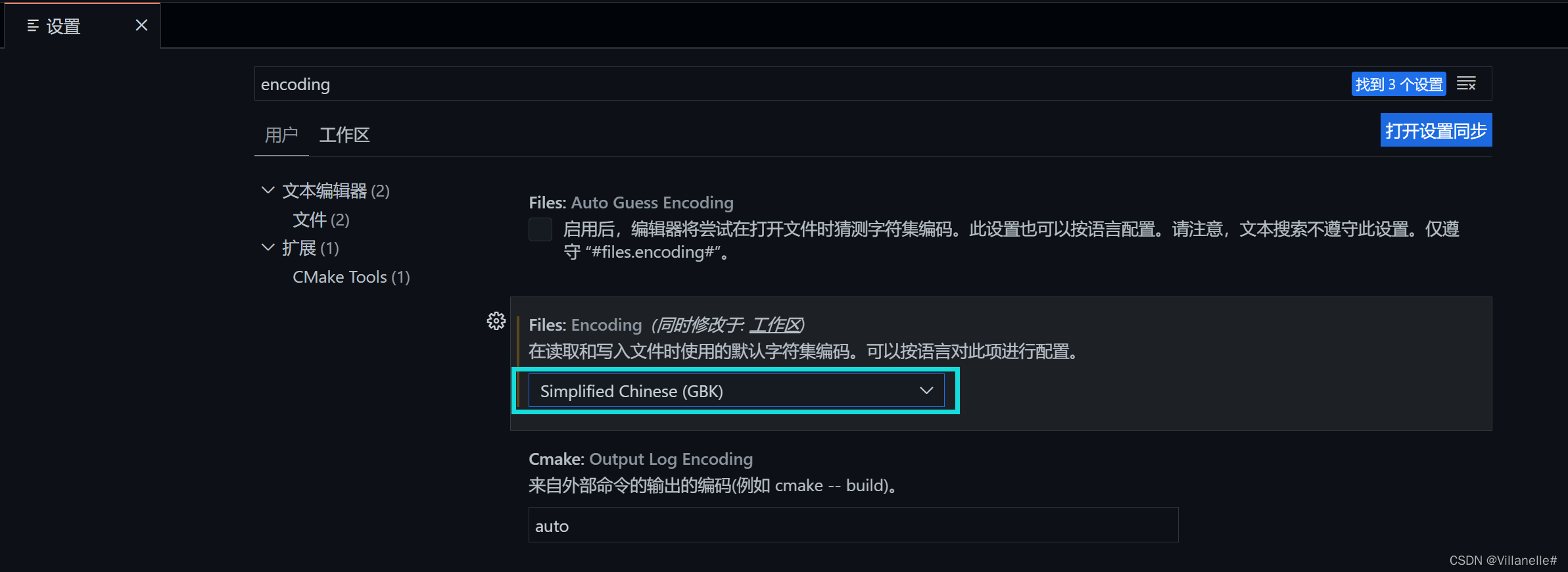
VS Code配置问题

Data reverse attack under federated learning -- gradinversion
随机推荐
The source code of the live app. When the verification method is mailbox verification, the verification code is automatically sent to the entered mailbox
程序猿学英语-Learning C
HCIA—数据链路层
How to apply for a secondary domain name?
程序猿学英语-指令式编程
2022 Heilongjiang's latest eight member (Safety Officer) simulated test question bank and answers
Introduction to anti interception technology of wechat domain name
Learn to write article format
Don't know mock test yet? An article to familiarize you with mock
Global and Chinese market of wire loop, 2022-2028: Research Report on technology, participants, trends, market size and share
Valin cable: BI application promotes enterprise digital transformation
使用wireshark抓取Tcp三次握手
cve_ 2019_ 0708_ bluekeep_ Rce vulnerability recurrence
Jupyter Notebook常用快捷键(在命令模式中按H也可查看)
File upload and download performance test based on the locust framework
Makefile基本原理
Sqlyog remote connection to MySQL database under centos7 system
Opencv common method source link (continuous update)
Opencv3 6.3 reduced pixel sampling with filters
MySQL optimization