当前位置:网站首页>Introduction to anti interception technology of wechat domain name
Introduction to anti interception technology of wechat domain name
2022-07-02 08:18:00 【Jumingwang】
I believe that wechat intercepts domain names is also something that many webmasters often encounter , Then you know why your domain name is blocked and blocked on wechat ? What is the principle of blocking domain names on wechat ? How can we prevent the domain name from blocking ?
1、 What is the principle of domain names being blocked on wechat ?
Automatic detection of wechat system ; Or the manual detection of wechat staff .
The automatic detection system is to track the illegal keyword jump code inside the domain name after the user visits the domain name .
Manual detection means that users complain and report , How many times in how many time accumulation report quantity , There are staff involved , Start manual testing .
2、 How can we prevent the domain name from blocking ?
Common defensive measures : Test interface + Domain name rotation system
Wechat domain name detection interface , It is recommended to use one , Fast and stable .
Configure your web address , Use multiple sets of domain name one 、 Number two . For example, the domain name shared is number one , This number is called the main domain name . Click open and jump to number two , Check whether number two is blocked before jumping , The number two in this is called the landing domain name .
Usually, the landing of domain name No. 2 requires a little more preparation , The detection interface always automatically queries , Seal it and change it .
Through technology , Screen the report button on the top right corner of wechat , Directly make it impossible for users to report , It directly blocks the reporting function of wechat , Very good results .
The above is the introduction of anti interception technology of wechat domain name .
边栏推荐
猜你喜欢

应对长尾分布的目标检测 -- Balanced Group Softmax

St-link connection error invalid ROM table of STM32 difficult and miscellaneous diseases

【无标题】

使用Matplotlib绘制图表初步
Carla-UE4Editor导入RoadRunner地图文件(保姆级教程)
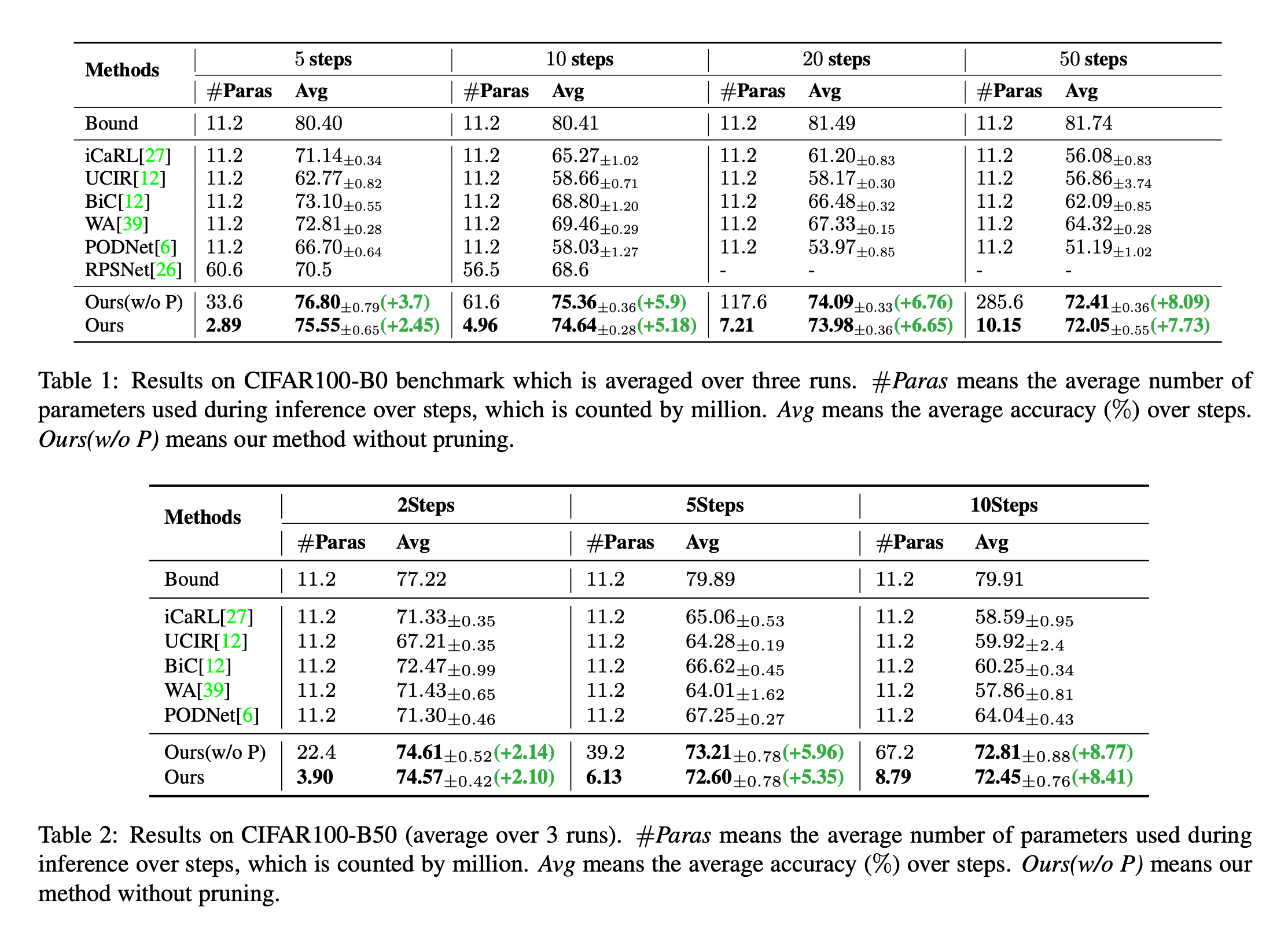
用于类别增量学习的动态可扩展表征 -- DER
Carsim-问题Failed to start Solver: PATH_ID_OBJ(X) was set to Y; no corresponding value of XXXXX?
Simply test the two different data transmission methods of content length and chunked

Use of OpenCV 6.4 median filter
![Open3d learning notes 1 [first glimpse, file reading]](/img/68/68ea87817dbf788591216a32c9375b.png)
Open3d learning notes 1 [first glimpse, file reading]
随机推荐
Global and Chinese markets of tilting feeders 2022-2028: Research Report on technology, participants, trends, market size and share
力扣每日一题刷题总结:栈与队列篇(持续更新)
Open3d learning notes 1 [first glimpse, file reading]
cve_ 2019_ 0708_ bluekeep_ Rce vulnerability recurrence
Summary of one question per day: String article (continuously updated)
Data reverse attack under federated learning -- gradinversion
W10 is upgraded to W11 system, but the screen is black, but the mouse and desktop shortcuts can be used. How to solve it
Chinese garbled code under vscade
力扣每日一题刷题总结:字符串篇(持续更新)
Carla-UE4Editor导入RoadRunner地图文件(保姆级教程)
Open3d learning note 5 [rgbd fusion]
Use of OpenCV 6.4 median filter
Learn to write article format
Matlab-其它
E-R draw clear content
The internal network of the server can be accessed, but the external network cannot be accessed
用C# 语言实现MYSQL 真分页
我的vim配置文件
Erase method in string
Principes fondamentaux de la théorie musicale (brève introduction)