当前位置:网站首页>Shanxi group (enterprises) in the second network security skills competition part problem WP (7)
Shanxi group (enterprises) in the second network security skills competition part problem WP (7)
2022-07-30 04:30:00 【[email protected]】
Foreword
I am fortunate to participate in the competition of the enterprise group of the 2nd Shanxi Network Security Skills Competition in 2022. This is the first time I have participated in the ctf competition. I went there for the purpose of accumulating practical experience. The ranking is a bit unexpected.
Tips: The following is the text of this article.
I. Question
Title:
Miscellaneous questions, simple steganographic attachments.
Attachments:
Simple steganographic attachment.png
Second, problem solving steps
1. Problem solving ideas
When you see a PNG image, first use tweakpng to see if crc reports an error.The result indicates that there is a problem with the CRC check.Use the PNG width and height shuttle tool to restore the original size of the picture (or directly change the height through WINHEX), you will find a half-section flag, and prompt the LSB related content.Drag the PNG into the 010 editor, and find that there is a compressed file mark at the end -- "PK", and then separate flag.wav from it. Spectrum analysis does not find any valuable content, and then use the silenteye steganography tool to export the hidden file---flag.pyc.Use the pyc steganography tool --stegosaurus to retrieve the second half of the flag.
2. Problem solving process
(Original image is pure white image)
Resize the image, or use a shuttle tool to restore its size and hide the information.

Get half a FLAG.
In the 010 editor, it is found that there are compressed files hidden in it, and use binwalk to separate them.
# binwalk -e simple steganographic attachment.pngDECIMAL HEXADECIMAL DESCRIPTION--------------------------------------------------------------------------------0 0x0 PNG image, 1195 x 300, 8-bit/color RGB, non-interlaced91 0x5B Zlib compressed data, compressed6553 0x1999 Zip archive data, at least v2.0 to extract, compressed size: 336438, uncompressed size: 353472, name: flag.wav343119 0x53C4F End of Zip archive, footer length: 22Isolate the flag.wav file and use spectrum analysis software to analyze it. No valuable content is found. The music content is a standard piece of music.
Use the silenteye tool to restore the hidden information in flag.wav -->flag.pyc
Use pyc steganography tool to restore steganographic content
F:\software\CTF toolbox\ctf toolbox\other stegos\stegosaurus-1.0>python -m stegosaurus -x F:\sharedir\CTF\_simple steganography attachments.png.extracted\flag.pycStegosaurus requires Python 3.6 or laterThe PY3.9 installed in the virtual machine fails to run.For this reason, the PY3.5 installed on the real machine still prompts the version problem. In desperation, the version detection item is annotated, and it is run again in the PY3.5 environment, and a miracle occurs.
F:\software\CTF toolbox\ctf toolbox\other stegosaurus\stegosaurus-1.0>python -m stegosaurus -x F:\sharedir\CTF\_simple steganographyWritten attachment.png.extracted\flag.pycExtracted payload: 665646cd2139a4ba0b0}Content blocked by stegosaurus.py:
#if sys.version_info < (3, 6):# sys.exit("Stegosaurus requires Python 3.6 or later")The two flags are merged.
flag{8f177eac1dff4665646cd2139a4ba0b0}III. Summary
I haven't solved it during the competition, and I haven't solved a similar problem before. This is the first time I met it.
版权声明
本文为[[email protected] one word]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/211/202207300416449652.html
边栏推荐
- cv2.polylines
- Install MySQL Database on Kylin V10 Operating System
- 2021 Shandong Province Network Construction and Application Test Questions
- 成为一个合格的网安,你知道这些吗?
- Notes on "The Law of Construction"---Chapter 10 Typical Users and Scenarios
- Taobao H5 interface to obtain app data 6.0 format
- (题目练习)条件概率+权值线段树+FWT+后缀数组
- 2022.7.29-----leetcode.593
- 宇宙的尽头是银行?聊聊在银行做软件测试的那些事
- 获取本机IP和Request的IP
猜你喜欢

BGP的简单实验

Pytorch框架学习记录7——卷积层
![[SQL] at a certain correlation with a table of data update another table](/img/66/4dff4383509e5d25890d8a24720de6.png)
[SQL] at a certain correlation with a table of data update another table
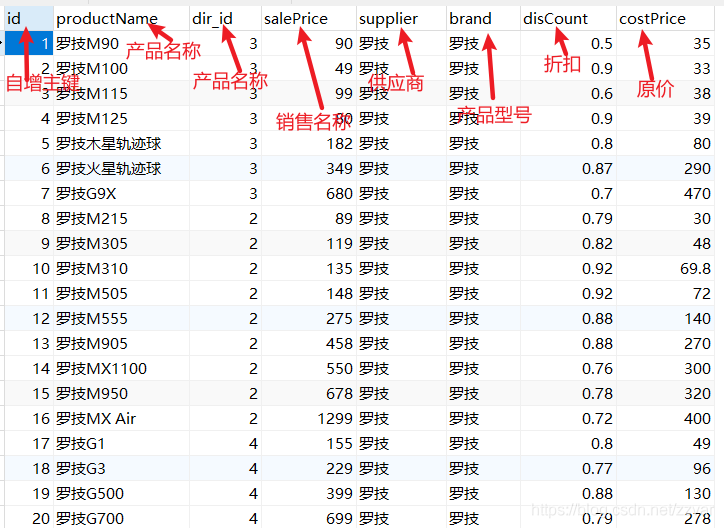
MySQL operation statement Daquan (detailed)

Is the end of the universe a bank?Talk about those things about doing software testing in the bank

handler+message【消息机制】

Pytorch framework learning record 7 - convolutional layer
GCC Rust获批将被纳入主线代码库,或将于GCC 13中与大家见面

PyG搭建R-GCN实现节点分类

Go书籍大全-从初级到高级以及Web开发
随机推荐
MySql 怎么查出符合条件的最新的数据行?
[Driver] udev sets the owner, group and permissions after GPIO is loaded
What is the data directory?Why do you need it?
Introduction to Thymeleaf
SQLSERVER merges subquery data into one field
MySQL data query (subtotal and sorting)
phpoffice edit excel document
Atomic Guarantees of Redis Distributed Locks
MySQL 操作语句大全(详细)
Hongji was once again shortlisted in the Gartner 2022 RPA Magic Quadrant and achieved a significant jump in position
Pytorch框架学习记录1——Dataset类代码实战
Thinkphp 5.0.24 Variable Override Vulnerability Causes RCE Analysis
山西省第二届网络安全技能大赛(企业组)部分赛题WP(九)
Shell script basic editing specifications and variables
[Redis Master Cultivation Road] Jedis - the basic use of Jedis
数据目录是什么?为何需要它?
我的Go+语言初体验——祝福留言小系统,让她也可以感受到你的祝福
PyG搭建R-GCN实现节点分类
Eureka Registry
Is the end of the universe a bank?Talk about those things about doing software testing in the bank