当前位置:网站首页>(27) Open operation, close operation, morphological gradient, top hat, black hat
(27) Open operation, close operation, morphological gradient, top hat, black hat
2022-07-01 16:57:00 【Li Sanhe】
First, the main purpose of morphology is to obtain object topology and result information , Through some operations of objects and structural elements , Get the more essential form of the object , The main applications in image processing are :
(1) Use the basic operations of morphology to observe and process the image , So as to improve the image quality
(2) Describe and define various geometric parameters and features of the image, such as area 、 Perimeter 、 connected 、 Particle size 、 Skeleton and directivity

1、 Open operation
The operation is realized by first etching the image and then expanding , The principle expression is as follows :
dst=open(src,element)=dilate(erode(src,element))
It can exclude small lumps ( Suppose the object is brighter than the background ), The result of the open operation deletes the object area that cannot contain structural elements , Smoothed the outline of the object , Broke the narrow connection , Removed the small protrusions , As shown in the figure below : The image on the left is the original image , The figure on the right is the result of the open operation conversion , You can find that the white space at the corner of the letter disappears .
2、 Closed operation
Mathematically, closed operation is the result of expansion and then corrosion , The principle expression is as follows :
dst=close(src,element)=erode(dilate(src,element))
It can exclude small black holes ( Black areas ), It can smooth the outline of the object , But unlike the open operation, the closed operation generally connects narrow gaps to form slender bends , And fill holes smaller than structural elements .
3、 Morphological gradient
The morphological gradient is the difference between the expansion diagram and the corrosion diagram , The operation principle expression is as follows :
dst=morph(src,element)=dilate(src,element)-erode(src,element)
Morphological gradient operation can preserve the edge contour of the object
4、 Top hat
The top hat operation is the difference between the original image and the result of the open operation , The principle expression is as follows :
dst=tophat(src,element)=src-open(src,element)
The result of the open operation is to enlarge the crack or locally reduce the brightness of the area , Therefore, the effect image obtained by subtracting the calculated image from the original image can highlight the area brighter than the area around the outline of the original image , And this operation is related to the size of the selected core . The top hat operation is often used to separate the plates that are lit next to each other , When an image has a large background and small objects are regular , The top hat operation can be used for background extraction .
5、 Black hat
Black hat operation is the difference between the result of closed operation and the original image , The principle expression is as follows :
dst=blackhat(src,element)=close(src,element)-src
The effect image after black hat operation highlights the darker area than the area around the outline of the original image , This operation is also related to the selected core size . So the black hat operation is used to separate the patches darker than the adjacent points , The rendering has a very perfect outline .
边栏推荐
- 想做软件测试的女孩子看这里
- Judge whether a binary tree is a balanced binary tree
- 求求你们,别再刷 Star 了!这跟“爱国”没关系!
- FRP intranet penetration, reverse proxy
- How to use F1 to F12 correctly on laptop keyboard
- SQL question brushing 584 Looking for user references
- China sorbitol Market Forecast and investment strategy report (2022 Edition)
- 重磅披露!上百个重要信息系统被入侵,主机成为重点攻击目标
- 【Try to Hack】vulnhub DC4
- How to restore the system with one click on Lenovo laptop
猜你喜欢
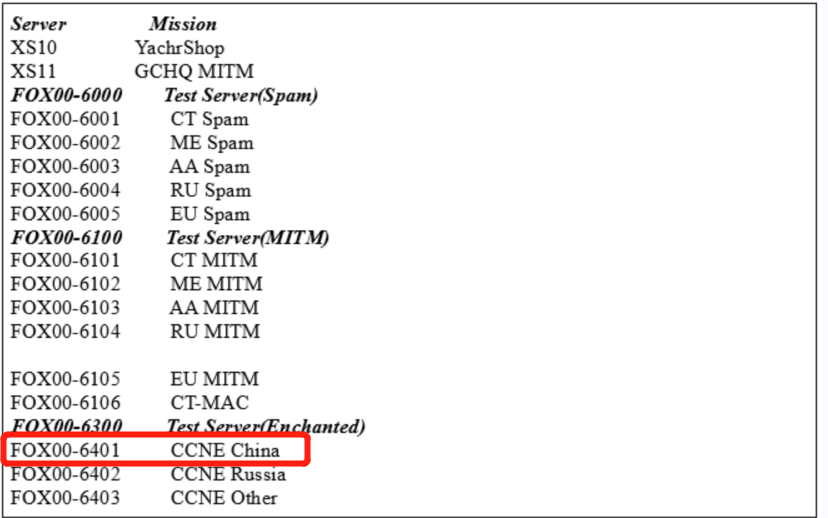
重磅披露!上百个重要信息系统被入侵,主机成为重点攻击目标

Bugku's file contains

GameFramework食用指南
Buuctf gold III
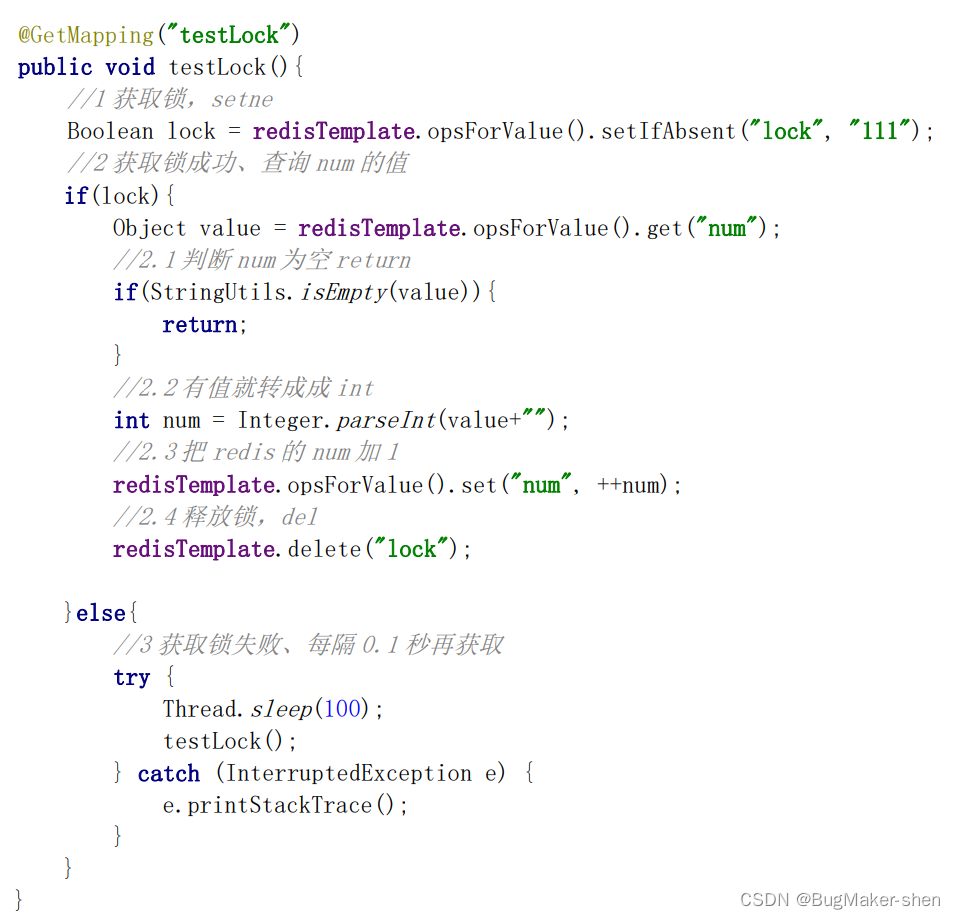
Redis 分布式锁

How to solve the keyboard key failure of notebook computer

Ring iron pronunciation, dynamic and noiseless, strong and brilliant, magic wave hifiair Bluetooth headset evaluation
![[flask introduction series] cookies and session](/img/2e/d50e0a032c4ec48935cb5df206a29b.png)
[flask introduction series] cookies and session

Soft test network engineer full truth simulation question (including answer and analysis)

Défaillance lors du démarrage de la machine virtuelle VMware: le poste de travail VMware n'est pas compatible avec hyper - V...
随机推荐
Redis6.0 new features
巴比特 | 元宇宙每日必读:奈雪币、元宇宙乐园、虚拟股票游戏...奈雪的茶这波“操作拉满”的营销活动你看懂了吗?...
How to restore the system with one click on Lenovo laptop
sql刷题1050. 合作过至少三次的演员和导演
【PyG】文档总结以及项目经验(持续更新
Internet News: "20220222" get together to get licenses; Many products of Jimi have been affirmed by consumers; Starbucks was fined for using expired ingredients in two stores
Graduation season | Huawei experts teach the interview secret: how to get a high paying offer from a large factory?
Pytest learning notes (13) -allure of allure Description () and @allure title()
Research and investment strategy report of hydroxypropyl beta cyclodextrin industry in China (2022 Edition)
[jetsonnano] [tutorial] [introductory series] [III] build tensorflow environment
【C語言補充】判斷明天是哪一天(明天的日期)
想做软件测试的女孩子看这里
Soft test software designer full truth simulation question (including answer analysis)
FRP intranet penetration, reverse proxy
China nylon 11 industry research and future forecast report (2022 Edition)
How to maintain the laptop battery
SQL question brushing 586 Customers with the most orders
重磅披露!上百个重要信息系统被入侵,主机成为重点攻击目标
Cookies and session keeping technology
Introduction to software engineering - Chapter 6 - detailed design