当前位置:网站首页>Soft test network engineer full truth simulation question (including answer and analysis)
Soft test network engineer full truth simulation question (including answer and analysis)
2022-07-01 16:53:00 【ghgj214】
| user B Received by A Message after digital signature M, To verify the authenticity of the message , First of all, you need to CA Get users A The digital certificate of , The digital certificate contains (/) , You can use () Verify the authenticity of the certificate , And then use it (/) verification M Authenticity . A、CA The public key B、B The private key C、A The public key . D、B The public key |
| Put the Internet 117.1 5.32.0/23 Divided into 117.15.32.0/27, How many subnets are obtained ? () How many host addresses can be used in each subnet ? (/) . A、4 B、8 C、16 D、32 |
| RIP The default route update cycle of the protocol is ( ) second . A、30 B、60 C、90 D、100 |
| The so-called quadrature amplitude modulation is to combine two () The analog signal of is synthesized into a carrier signal . A、 Same amplitude and phase difference 90° B、 Same amplitude and phase difference 180° C、 Same frequency and phase difference 90° D、 Same frequency and phase difference 1 80° . |
| The workstation A Of IP The address is 202.117.17.24/28, And workstation B Of IP The address is 202.117.17.100/28, When two workstations are directly connected, communication is not possible , How to modify the address so that the two workstations can communicate with each other ? () A、 Put the workstation A The address of the is changed to 202.117.17.15 B、 Put the workstation B The address of the is changed to 202.117.17.112 C、 Change the subnet mask to 25 D、 Change the subnet mask to 26 |
| answer :A.CA Is the abbreviation of Certification Center , In order to be able to authenticate the identities of both sides of communication on the Internet , You can apply for your own digital certificate in the corresponding Certification Center .CA The digital certificate issued to the user contains the user's public key information 、 Certification information and validity period of the authority . After the user receives the digitally signed message , The authenticity of the certificate must be verified first , That is, use the public key of the certificate to verify , Then use the public key of the other party to verify the authenticity of the message . |
| answer :C. Put the Internet 117.15.32.0/23 Divided into 117.15.32.0/27, Then the subnet mask is expanded 4 position , So the obtained subnet is 16 individual . Because the subnet mask is 27 position , So the host address only accounts for 5 position , The available host addresses in each subnet are 30 individual . |
| answer :A.RIP Update the route periodically , Broadcast the Lunan table to the neighbor router , The broadcasting cycle is 30 second . |
| answer :A. Quadrature amplitude modulation (Quadrature Amplitude Modulation,QAM) Is to put two same amplitude but phase difference 90 The analog signal of is synthesized into a carrier signal , After channel coding, the data combination is mapped to the constellation . |
| answer :C. The workstation A Of IP The address is 202.117.17.24/28: 11001010.01110101. 00010001.00011000 The workstation B Of IP The address is 202.117.17.100/28: 11001010.01110101. 00010001.01100100 The current two addresses do not belong to the same subnet , Change the address mask to 25 It belongs to the same subnet . |
| Host a sends a message to host B TCP Message segment ,SYN Field is “1", The value of the serial number field is 2000, If host B agrees to establish a connection , Then the message segment sent to host a may be (/) , If host B does not agree to establish a connection , be () Field settings "1". A、URG B、RST C、PSH D、FIN |
| Suppose a software company signs a contract with a customer to develop a software system , The function of the system is clearly defined , And customers have strict requirements on delivery time , Then the development of this system is the most suitable ( ) A、 Waterfall model B、 Prototypes . C、V Model D、 Spiral model |
| TCP Use 3 The second handshake protocol establishes the connection , To prevent (/) ; When the requestor sends SYN After the connection request , Wait for the answer (/) To establish the correct connection ; When an incorrect connection occurs , Respond to () . A、SYN,ACK B、FIN,ACK C、PSH,ACK D、RST,ACK |
| In the following description of scripting language , The right is (). A、 Scripting language is a general programming language B、 Scripting language is more suitable for system level program development C、 Script language is mainly implemented by means of interpretation D、 Functions cannot be defined and called in scripting languages |
| Memory units are byte addressable , Address 0000A000H~000OBFFFH share () Storage unit . A、8192K B、1024K C、13K D、8K |
| answer :B. Host a sends a message to host B TCP Message segment ,SYN Field is “1 ”, The value of the serial number field is 2000, If host B agrees to establish a connection , In the message segment sent to host a ,SYN The field should be set to “1”, The answer flag field should be set to “1”, The value of the answer field is the serial number of A +1. If host B does not agree to establish a connection , Or there is an incorrect connection , use RST Field settings “1” Deny . |
| answer :A. Waterfall model is the earliest software development model , It plays an important role in software engineering , It provides the basic framework of software development . The essence of waterfall model is “ One pass ”, That is, each activity is only done once , Finally get the software product , Also called doing “ Linear order model ” perhaps “ Traditional life cycle ”, The process is to receive the work object of the activity as input from the previous activity , Use this input to implement what this activity should accomplish , Give the work results of this activity , Pass as output to the next activity ; Review the implementation of this activity , If their work is confirmed , Then continue to the next activity , Otherwise, return to the previous item , Or even rework the previous activity . Waterfall model is conducive to the organization and management of personnel in the process of large-scale software development , It is conducive to the research and use of software development methods and tools , Thus, the quality and efficiency of large-scale software project development are improved . If the demand analysis is very clear , Waterfall model is recommended . |
| answer :D. Set up three handshakes , Instead of the second handshake, it is to prevent the wrong connection . When the sender sends SYN After the request , You need to wait for the other party to send SYN,ACK Data packets of ; When received , The sender sends ACK Respond , To establish a normal 3 Handshake request . When an incorrect connection occurs , Will RST Packet response to reject the connection . |
| answer :C. Scripting language is also called extended language , Or dynamic language , Is a programming language , Used to control software applications , Scripts are usually in text ( Such as ASCII) preservation , Interpret or compile only when called . A script is usually interpreted rather than compiled . Scripting languages are usually simple 、 studies of the Book of Changes 、 Easy to use features , The purpose is to let the programmer finish the programming work quickly . |
| answer :D. Each address number is a storage unit ( Capacity of 1 Bytes ), Address range 0000A000H〜0000BFFFH share 1FFF+1 An address number ( namely 213),1K=1024, Therefore, the number of storage units in this address range is 8K. |
| IEEE 802.11 stay MAC The layer uses () agreement . A、CSMA/CD B、CSMA/CA C、DQDB D、 Token passing . |
| stay DNS In the resource record of , type A (). A、 Express IP Address to host name mapping B、 Indicates the hostname to IP Address mapping C、 Specify the authorization server D、 Specify a regional mail server |
| stay Windows Operating system ,() File can help domain name resolution . A、cookie B、index C、hosts D、default |
| When receiving mail , Client agent software and POP3 The server through the establishment of () Connect to transmit messages . A、UDP B、TCP C、P2P D、DHCP |
| Mutually exclusive resources in a computer system R The available number of is 8, There are 3 A process P1、P2 and P3 competition R, And every process needs i individual R, The minimum number of deadlocks that can occur in the system i The value is () A、1 B、2 C、3 D、4 |
| answer :B.IEEE 802.11 stay MAC The layer uses CSMA/CA agreement , That is, carrier monitoring multiple access / Conflict avoidance agreement . Therefore, it is not used CSMA/CD It is because the problem of hidden terminals will appear in the case of wireless transmission , Make conflict detection infeasible . |
| answer :B.PTR The record says IP Address to host name mapping ;A The record indicates the host name to IP Address mapping ;NS Record the specified authorization server ;MX Record the mail server in the specified area . |
| answer :C.Hosts Files can define domain name pairs locally IP Parsing . |
| answer :B.POP3 It's the third edition of the post office agreement , Client agent software and POP3 Server setup TCP After connection , Can receive mail , The agreement is based on TCP Of 110 Port no. . |
| answer :D. Use the formula (i-1)*3+1>8, obtain i The minimum is 4. |

边栏推荐
- 为国产数据库添砖加瓦,StoneDB 一体化实时 HTAP 数据库正式开源!
- 毕业季 | 华为专家亲授面试秘诀:如何拿到大厂高薪offer?
- Installation and use of sqoop
- Free lottery | explore the future series of blind box digital copyright works of "abadou" will be launched on the whole network!
- [flask introduction series] cookies and session
- China nylon 11 industry research and future forecast report (2022 Edition)
- [live broadcast appointment] database obcp certification comprehensive upgrade open class
- The difference between the lazy mode of singleton mode and the evil mode
- Research and investment strategy report of hydroxypropyl beta cyclodextrin industry in China (2022 Edition)
- Kali install Nessus
猜你喜欢

数据库系统原理与应用教程(001)—— MySQL 安装与配置:MySQL 软件的安装(windows 环境)
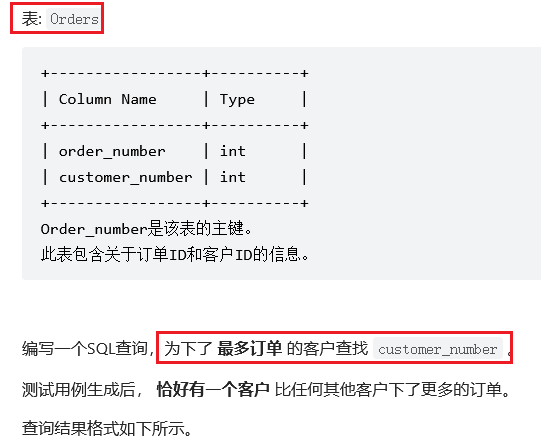
SQL question brushing 586 Customers with the most orders

数据库系统原理与应用教程(002)—— MySQL 安装与配置:MySQL 软件的卸载(windows 环境)
数据库系统原理与应用教程(003)—— MySQL 安装与配置:手工配置 MySQL(windows 环境)

Tutorial on the principle and application of database system (003) -- MySQL installation and configuration: manually configure MySQL (Windows Environment)
The sharp drop in electricity consumption in Guangdong shows that the substitution of high-tech industries for high-energy consumption industries has achieved preliminary results

Flux d'entrées / sorties et opérations de fichiers en langage C

Today, at 14:00, 15 ICLR speakers from Hong Kong University, Beihang, Yale, Tsinghua University, Canada, etc. continue!

VMware virtual machine failed during startup: VMware Workstation is incompatible with hyper-v

Building blocks for domestic databases, stonedb integrated real-time HTAP database is officially open source!
随机推荐
Building blocks for domestic databases, stonedb integrated real-time HTAP database is officially open source!
The difference between the lazy mode of singleton mode and the evil mode
[JetsonNano] [教程] [入门系列] [三] 搭建TensorFlow环境
Research and investment strategy report of neutral protease industry in China (2022 Edition)
【Kotlin】高阶函数介绍
数据库系统原理与应用教程(002)—— MySQL 安装与配置:MySQL 软件的卸载(windows 环境)
SystemVerilog structure (II)
C语言输入/输出流和文件操作
AI college entrance examination volunteer filling: the gods of Dachang fight, and candidates pay to watch
GaussDB(for MySQL) :Partial Result Cache,通过缓存中间结果对算子进行加速
Redis6.0 新功能
Graduation season | Huawei experts teach the interview secret: how to get a high paying offer from a large factory?
Virtual serial port simulator and serial port debugging assistant tutorial "suggestions collection"
拼接字符串,得到字典序最小的结果
Determine whether the linked list is a palindrome linked list
Concatenate strings to get the result with the smallest dictionary order
Comprehensively view the value of enterprise digital transformation
[live broadcast appointment] database obcp certification comprehensive upgrade open class
The sharp drop in electricity consumption in Guangdong shows that the substitution of high-tech industries for high-energy consumption industries has achieved preliminary results
China carbon disulfide industry research and investment strategy report (2022 Edition)