当前位置:网站首页>Configure SSH certificate login
Configure SSH certificate login
2022-07-04 11:13:00 【juno】
1、 Generate Certificate
cd To home/.ssh Catalog , without ,mkdir .ssh Create a .
ssh-keygen Enter all the way , Generate Certificate .
cat id_rsa > authorized_keys
Modify file permissions to 0600
2、 Copy the private key to the computer host
Copy id_rsa To your computer host .ssh Catalog . The file name does not change .
Modify the authority to 0600
At this time, you can log in directly with a certificate
边栏推荐
- Simple understanding of generics
- Local MySQL forget password modification method (Windows) [easy to understand]
- Function introduction of canbedded component
- QQ get group member operation time
- MBG combat zero basis
- [test theory] test the dimension of professional ability
- Simple understanding of string
- Jemeter plug-in technology
- TS type gymnastics: illustrating a complex advanced type
- unit testing
猜你喜欢
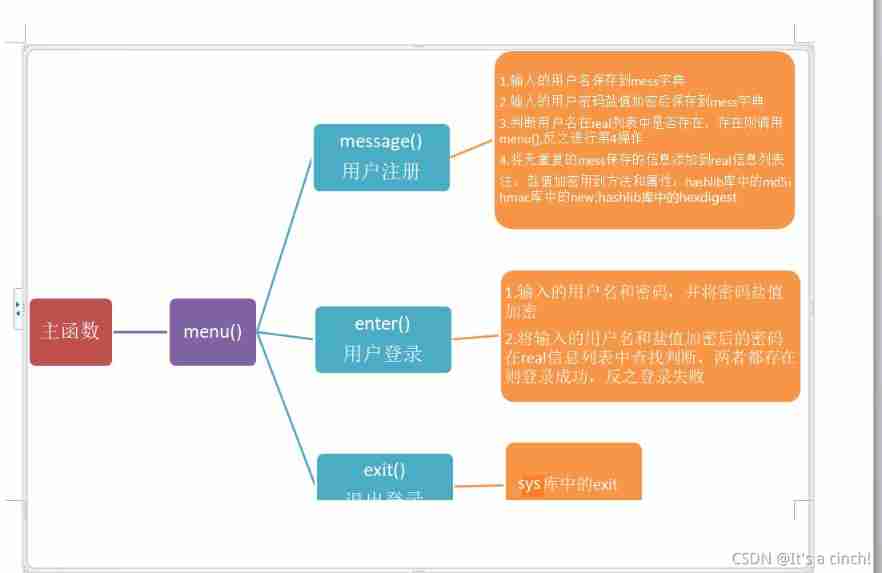
Login operation (for user name and password)
XMIND installation
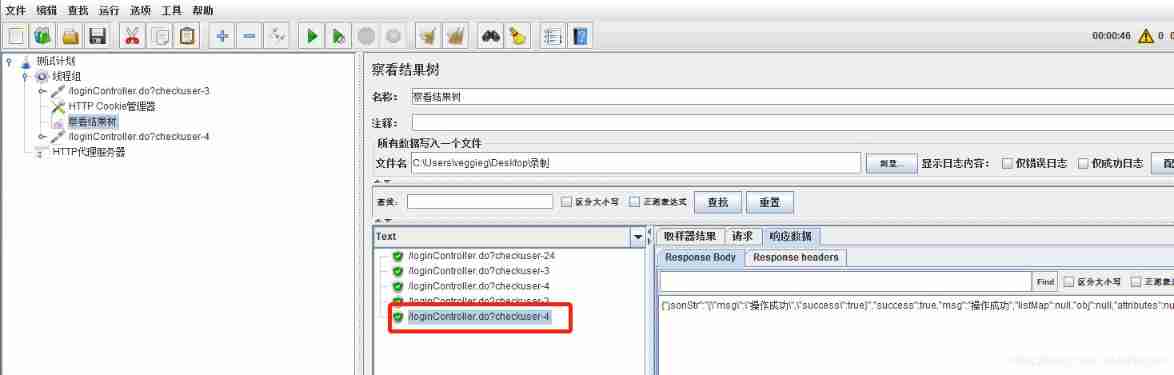
Jemeter script recording
Elevator dispatching (pairing project) ④
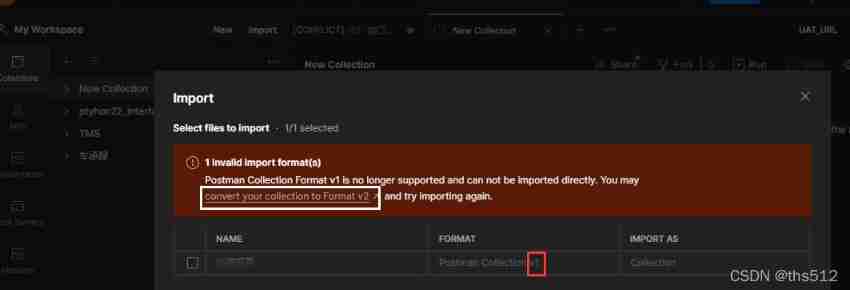
Post man JSON script version conversion
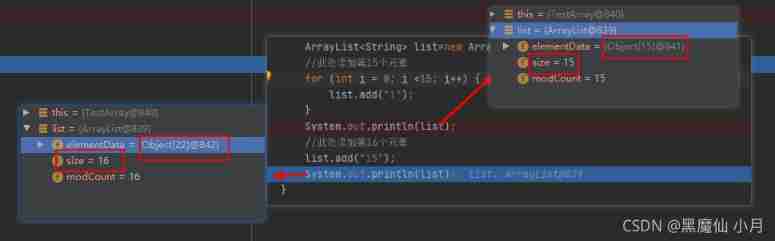
Detailed array expansion analysis --- take you step by step analysis
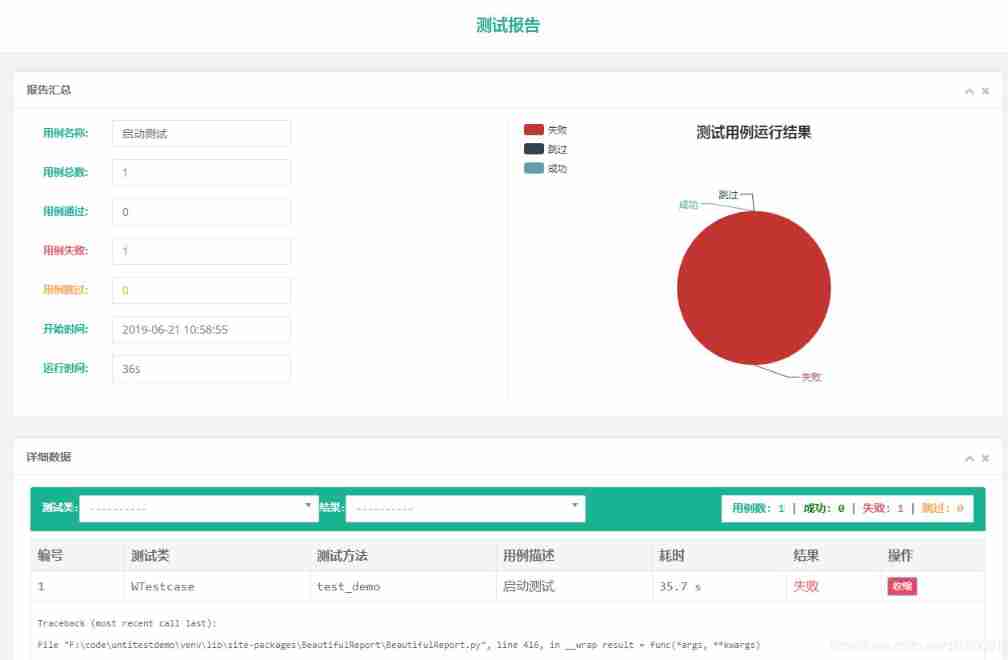
Unittest+airtest+beatiulreport combine the three to make a beautiful test report
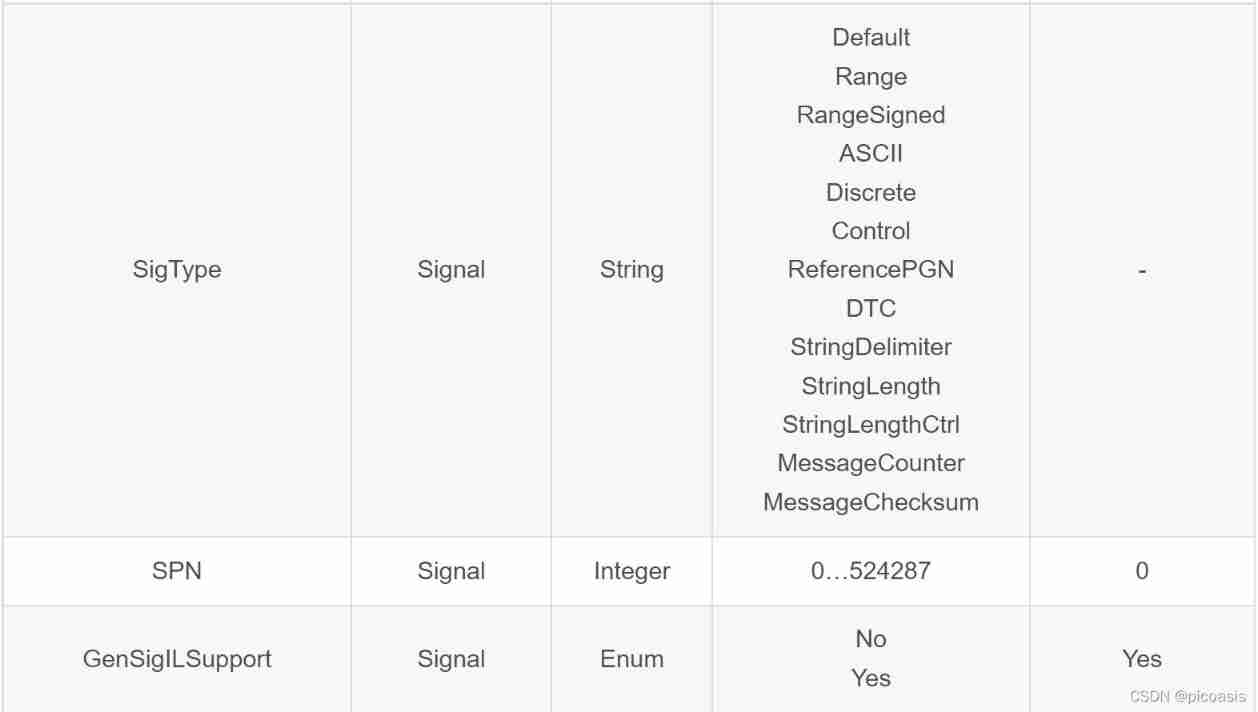
Canoe - description of common database attributes
Foreach (system.out:: println) usage
Elevator dispatching (pairing project) ③
随机推荐
Send a request using paste raw text
Daemon xinted and logging syslogd
Solaris 10 network services
Write a thread pool by hand, and take you to learn the implementation principle of ThreadPoolExecutor thread pool
Canoe test: two ways to create CAPL test module
Login operation (for user name and password)
QQ set group information
For and while loops
守护进程Xinted和日志记录Syslogd
Hidden C2 tunnel -- use of icmpsh of ICMP
array_ The contains() function uses
Understanding of object
[advantages and disadvantages of outsourcing software development in 2022]
Replace() function
Is Sanli futures safe? How to open a futures account? How to reduce the handling charge of futures at present?
三立期货安全么?期货开户怎么开?目前期货手续费怎么降低?
re. Sub() usage
Canoe-the second simulation project-xvehicle-1 bus database design (idea)
Test question bank management system - database design [easy to understand]
试题库管理系统–数据库设计[通俗易懂]