当前位置:网站首页>Network connection (III) functions and similarities and differences of hubs, switches and routers, routing tables and tables in switches, why do you need address translation and packet filtering?
Network connection (III) functions and similarities and differences of hubs, switches and routers, routing tables and tables in switches, why do you need address translation and packet filtering?
2022-07-04 10:30:00 【Big bear loves to work】
Just keep holding on , The worst result is nothing more than late success
3.0 Preface
- This chapter mainly talks about after the network package leaves the network card It is transmitted to the hub through the network cable , Then the hub pairs the packets Broadcast , The network packet is then sent to the switch , Switch According to the MAC Address Conduct Forwarding of network packets , Then the data arrives at the router , Router According to the IP Address forwarding , Then forward and deliver in a circular way , And many knowledge points involved in this process
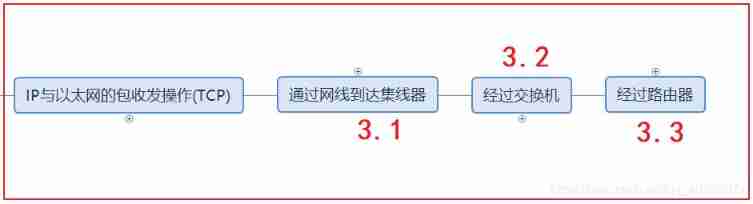
3.1 Reach the hub through the network cable
- The structure diagram of the hub is as follows :
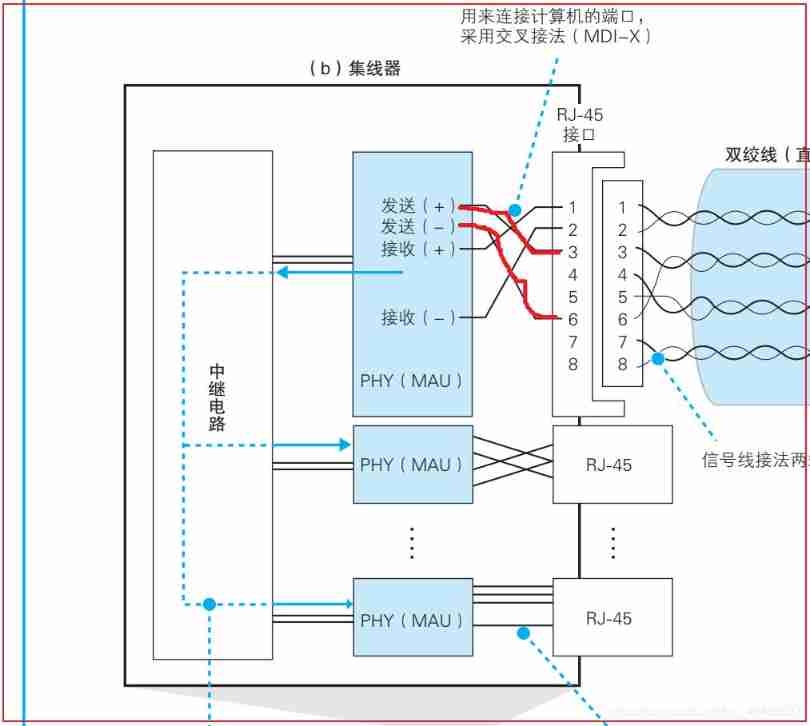
The work of the hub can be put simply :
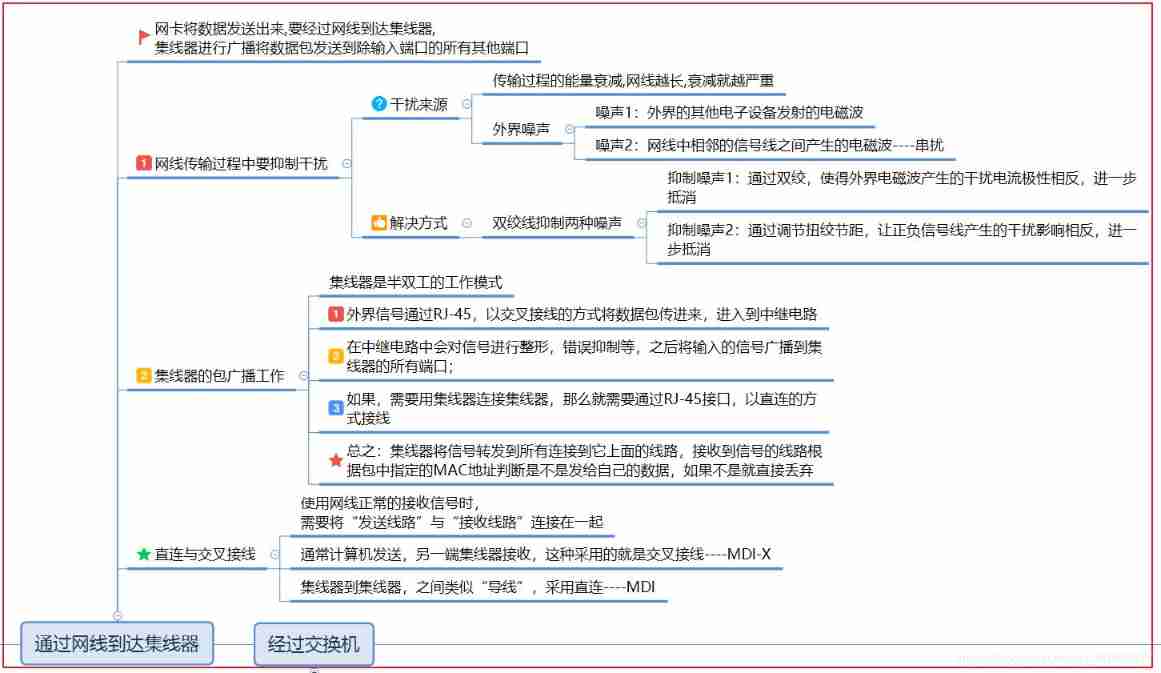
- The network packet signal passes RJ-45 Transfer to hub , In the hub Relay circuit The signal will be processed to a certain extent Shaping and error suppression , After that, the network signal will be radio broadcast All ports of the hub
Network cable passing " Twisted pair " To suppress noise
3.2 Through the switch
- The structure diagram of the switch is as follows :
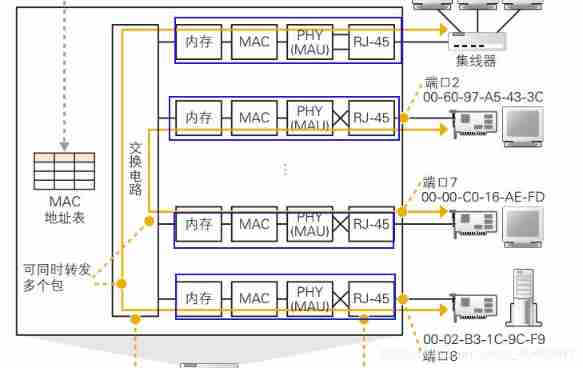
- The work of the switch It can be put simply as :
- Packets arrive at the switch through the port , Switchboard Each port The structure of all similar a sheet No, MAC Address of the network card , It is the same as the network card ( See the last blog ) Send and receive data .
- After the switch receives the data , Query the address table inside the switch , See if it is in the network package MAC The record corresponding to the address , Find the output port
- Through the switching circuit The network packet is transferred to the corresponding output port , Then the output port forwards the data
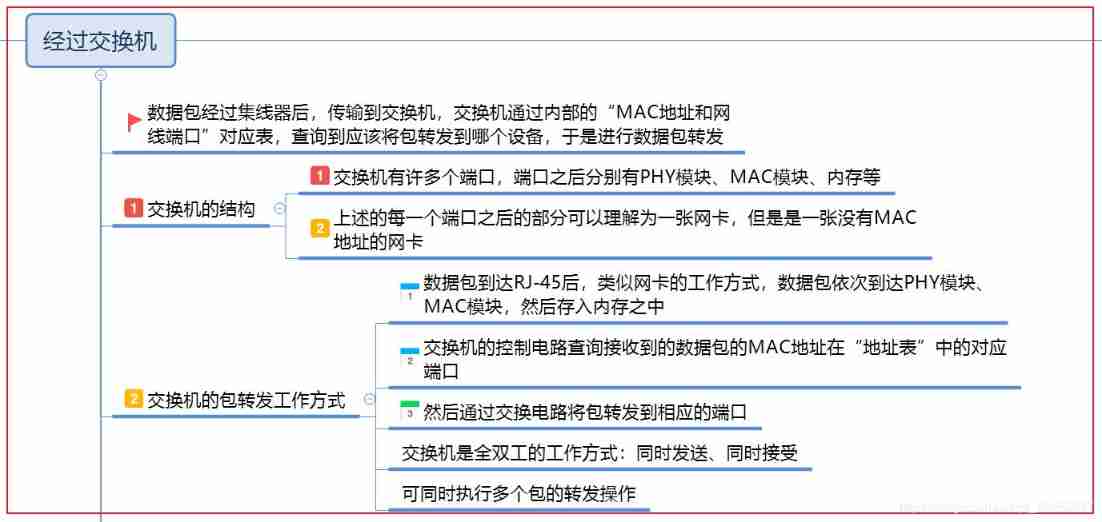
- The address table inside the switch is the address table of the device MAC A record table of the address and which port the device is connected to is shown below :
- Generally, the automatic maintenance of the switch , No manual maintenance required

- Generally, the automatic maintenance of the switch , No manual maintenance required

3.3 Through the router
- The structure diagram of the router is shown below : It is divided into Forwarding module and Port module
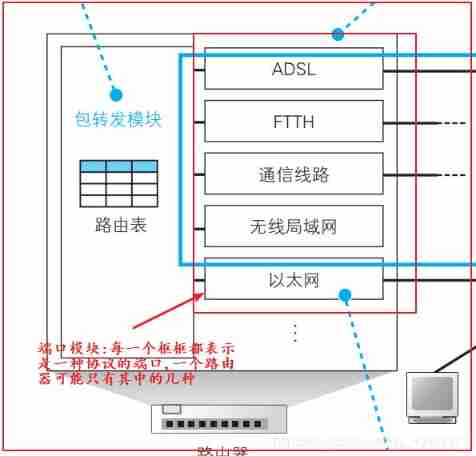
- The working mode of the router is briefly described as :
- Receive the data packet through the port module , Then the forwarding module according to the IP The address is queried in the routing table , Further judge the next Forward destination address
- The forwarding module transfers the packet to the corresponding port ( The result of looking up the table )
- The port sends packets , Before sending the packet, it will first query according to the forwarding target address MAC Address , New use MAC Replace the old address MAC Address
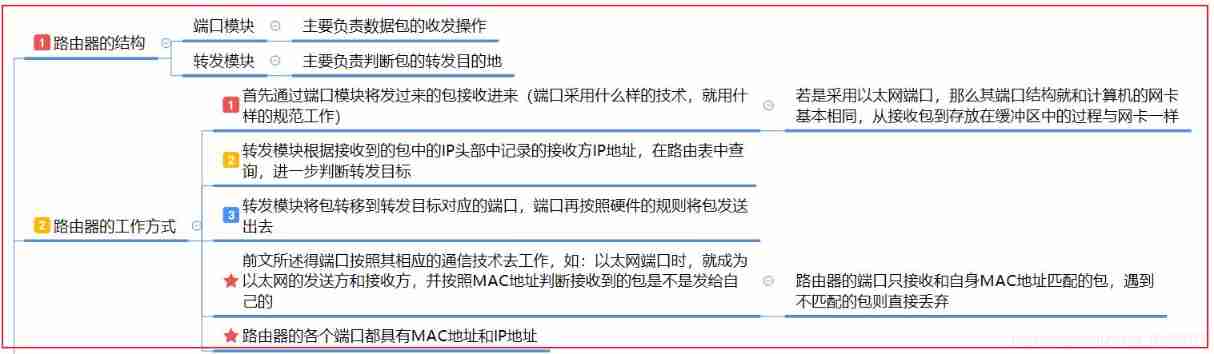
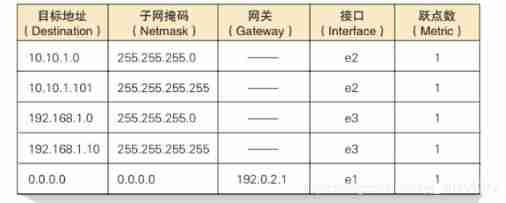
- Structure of routing table
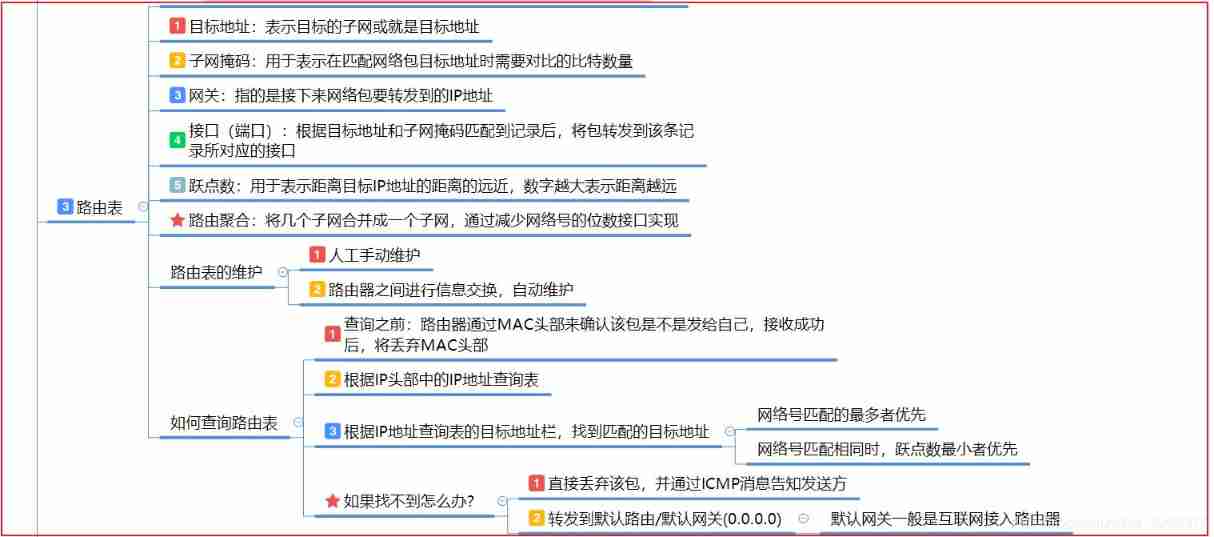
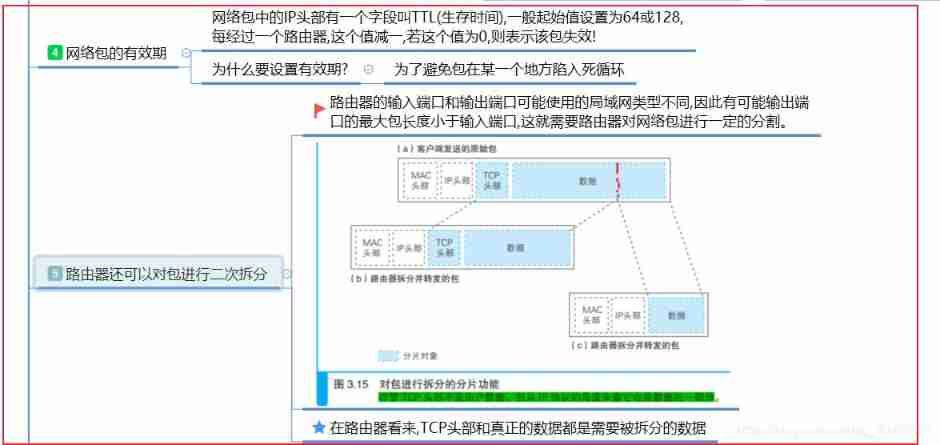
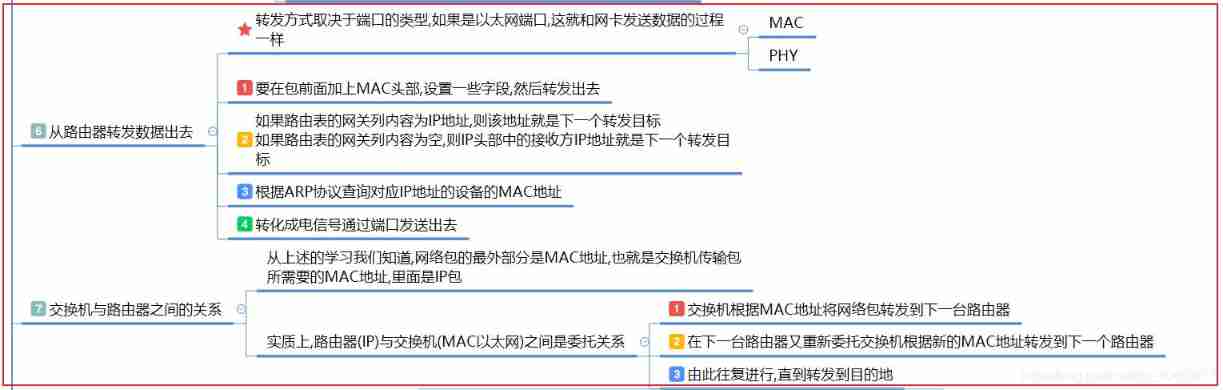
- The relationship between router and switch
- In essence , Router and switch are entrusted , The router entrusts the switch to forward the network packet to the next router
- Routers are based on IP Agreement work , Switches are Ethernet protocols that work
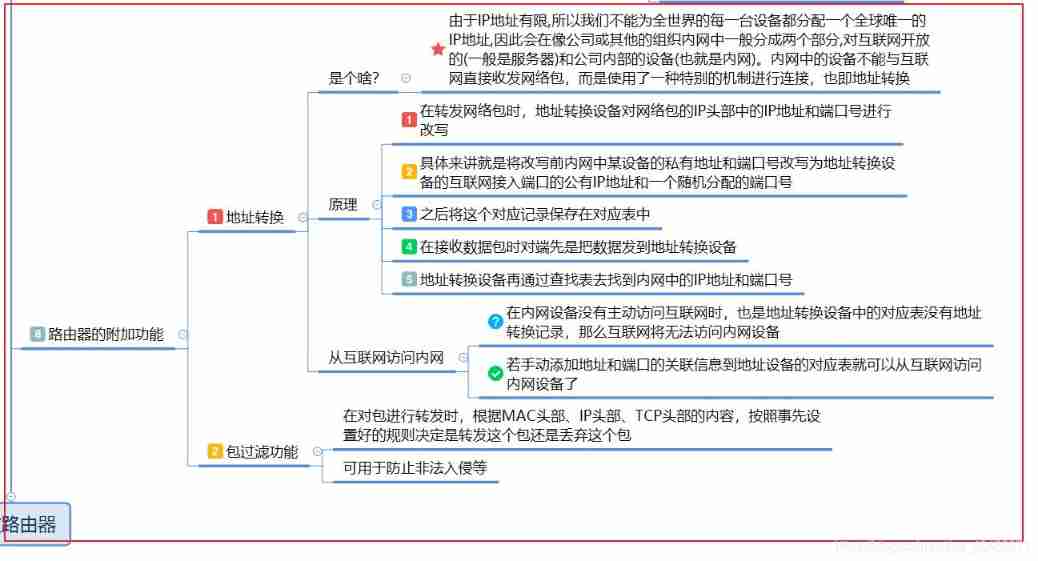
- The router address translation and Packet filtering function
3.4 The similarities and differences between switches and routers
| Item | Router | Switch |
|---|---|---|
| Forwarding basis | According to the... In the head IP Address | According to the... In the head MAC Address |
| Look up the table matching method | Ignore the host number , Only match records with the same network number (IP Address ) | Only match MAC A record with exactly the same address |
| " surface " Maintenance mode of | Packet forwarding and maintenance are independent of each other | The process of packet forwarding is automatically maintained , It is part of packet forwarding |
| When the packet does not know where to forward | Direct discarding / Forward to default route (0.0.0.0) | Broadcast to all ports |
边栏推荐
- Four characteristics and isolation levels of database transactions
- Recursion and divide and conquer strategy
- leetcode729. My schedule 1
- [200 opencv routines] 218 Multi line italic text watermark
- Basic data types of MySQL
- Rhcsa operation
- Debug:==42==ERROR: AddressSanitizer: heap-buffer-overflow on address
- Vanishing numbers
- Ruby时间格式转换strftime毫秒匹配格式
- Container cloud notes
猜你喜欢
Realsense of d435i, d435, d415, t265_ Matching and installation of viewer environment

BGP ---- border gateway routing protocol ----- basic experiment

Two way process republication + routing policy
Four characteristics and isolation levels of database transactions
Reprint: summation formula of proportional series and its derivation process
leetcode1-3
Occasional pit compiled by idea
![[FAQ] summary of common causes and solutions of Huawei account service error 907135701](/img/73/c4ee842475f05e2e67297fcac68779.png)
[FAQ] summary of common causes and solutions of Huawei account service error 907135701
Sword finger offer 05 (implemented in C language)

对于程序员来说,伤害力度最大的话。。。
随机推荐
【Day2】 convolutional-neural-networks
What is an excellent architect in my heart?
/*The rewriter outputs the contents of the IA array. It is required that the type defined by typedef cannot be used in the outer loop*/
Safety reinforcement learning based on linear function approximation safe RL with linear function approximation translation 1
【Day1】 deep-learning-basics
Latex arranges single column table pictures in double column format articles
System. Currenttimemillis() and system Nanotime (), which is faster? Don't use it wrong!
Ruby时间格式转换strftime毫秒匹配格式
Basic data types of MySQL
Press the button wizard to learn how to fight monsters - identify the map, run the map, enter the gang and identify NPC
Static comprehensive experiment ---hcip1
Devop basic command
Idea SSH channel configuration
DCL statement of MySQL Foundation
Es entry series - 6 document relevance and sorting
Sword finger offer 05 (implemented in C language)
Rhcsa - day 13
C language structure to realize simple address book
六月份阶段性大总结之Doris/Clickhouse/Hudi一网打尽
Knapsack problem and 0-1 knapsack problem