当前位置:网站首页>PHP code audit 3 - system reload vulnerability
PHP code audit 3 - system reload vulnerability
2022-07-04 10:04:00 【W0ngk】
One 、 Preface
1、 Types of system reload vulnerabilities
Automatically delete installation files
Common system installation , Will generate a lock File to determine whether to install , If the system will automatically delete this file , It will lead to system reload vulnerability .No verification of installation results
In this case, it will not be deleted .lock file , It doesn't generate .lock The installation files .Installation detection can bypass
This situation is , During installation , System installation detection is a separate page , After the test 302 Jump to the installation . under these circumstances , We can just get Request the installation page to bypass detection .Variable overwriting causes reloading
have access to GET perhaps POST And submit a variable name $lockFile, And assign a null value to it , overwrite $lockFile, So that file_existe() The result is false, To bypass the detection of installation files .Judge lock After the document , nothing exit
Judge whether it exists lock file , If lock If the file exists, it will jump to a page , But after the jump, there is no exit Testing procedure .There is a parsing vulnerability
After installation, it will install.php Rename it to install.php.bak, But because of Apache The parsing vulnerability of : If you can't recognize the last suffix , It will parse up , Then it becomes php 了 , Then it will be reinstalled in combination with the variable coverage during installation .
2、 List of recent vulnerabilities
- CNVD-2020-58513: ZZCMS 2020 Version system reload vulnerability
- CNVD-2020-33196: Shield spirit 1.0 System reload vulnerability
- CNVD-2020-31454:Heybbs Micro community install.php File reload vulnerability
- CNVD-2020-02229: deliver goods 100 System reload vulnerability
- CNVD-2019-43815:s-cms Enterprise website building system reinstallation vulnerability
- CNVD-2018-05690:hpyun Talent system 4.5 Version reload vulnerability
Two 、ZZCMS 2020 Reload vulnerability analysis and recurrence
1、 Vulnerability analysis
First of all, we see the vulnerable code :install/index.php.
In the code 11 That's ok , There is one $step Variable , The value of the variable , It is passed in by the client .
6:include '../inc/config.php';
7:include 'conn.php';
8:if($_POST) extract($_POST, EXTR_SKIP);// Register the key names in the array directly as variables . It's like putting $_POST[ai] Register directly for $ai.
9:if($_GET) extract($_GET, EXTR_SKIP);
10:$submit = isset($_POST['submit']) ? true : false;
11:$step = isset($_POST['step']) ? $_POST['step'] : 1;
A ternary operator is used here to judge , If no incoming step Parameter words , The default assignment will be 1.
in other words , During the initial visit index.php When , The default assignment will be $step=1.
Next, let's focus on 50 That's ok :
50:switch($step) {
51: case '1':// agreement
52: include 'step_'.$step.'.php';
53: break;
54: case '2':// Environmental Science
55: $pass = true;
56: $PHP_VERSION = PHP_VERSION;
57: if(version_compare($PHP_VERSION, '4.3.0', '<')) {
58: $php_pass = $pass = false;
59: } else {
60: $php_pass = true;
61: }
Here, , Used a switch Sentence to judge $step, When $setp=1 when , Would contain step_1.php file , The function of this file is to detect install.lock File to determine whether our system has been installed . The code is as follows :
if(file_exists("install.lock")){
echo "<div style='padding:30px;'> The installation wizard has run the installation , If reinstallation is required , Please delete /install/install.lock file </div>";
}
And when step by 2 Or others , You will enter the system installation step , therefore , When we capture and modify $step The value of is 2 perhaps 3 after , You will directly enter the system installation steps , Thus bypassing the system installation detection .
2、 Loophole recurrence
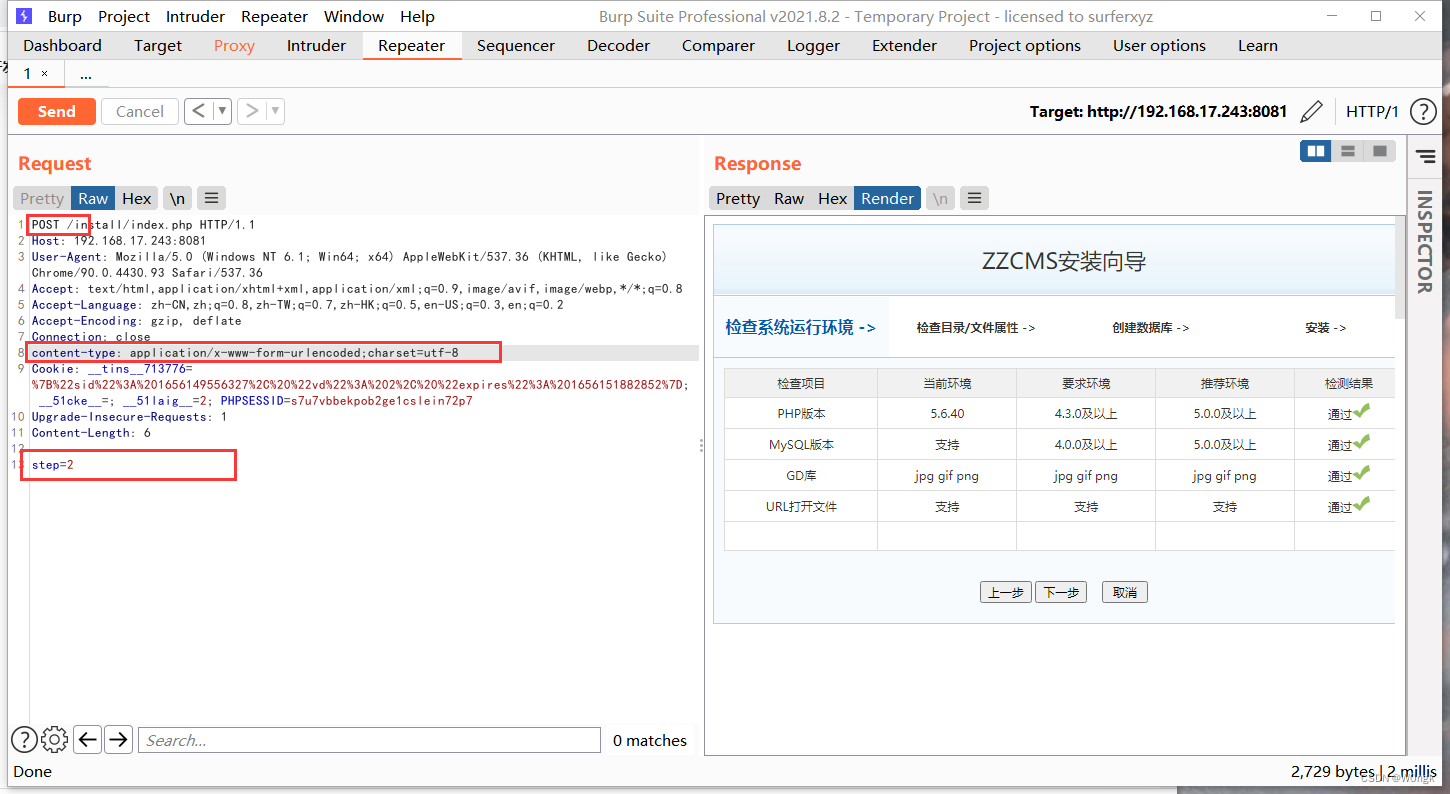
Here's the picture , It's the system we have installed :
We visit /install/index.php, And then use burpsuite Grab the bag , structure step=2, And modify the parameter transfer method to POST Mode submission , Successfully bypassed system installation detection , Enter the system installation steps :
3、 ... and 、 Shield spirit V.10 System reload vulnerability
notes : Dunling system includes official account promotion system 、 The press release system 、 Information sharing system , This time, the official account promotion system of dunling is used for code audit .
1、 Vulnerability analysis
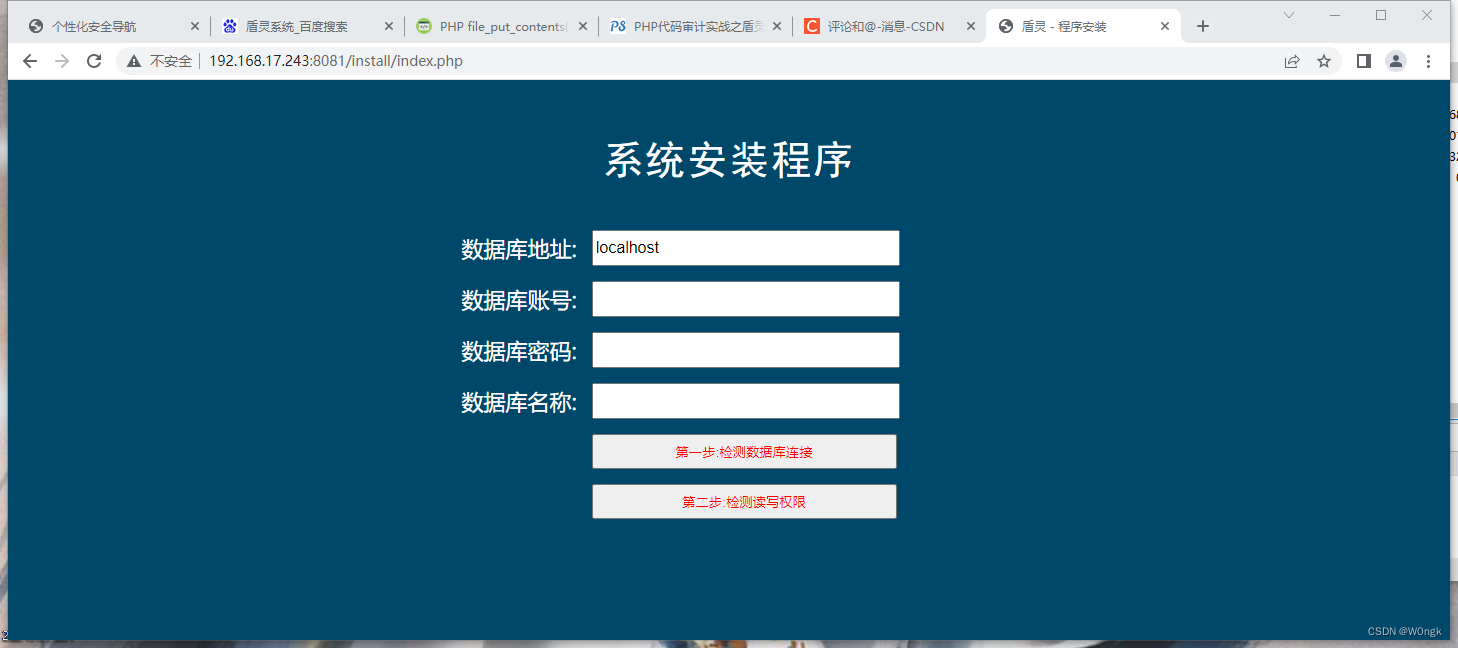
First, let's visit your-IP/install/index.php, The effect is as follows , Two detection steps are provided , One is database connection detection , One is file write permission detection .
Then we focus on /install/index.php file . There are mainly some JS Code , Used jqurey Of ajax Request to send data to the back-end interface . You can see , In the 36 Go to the first place 42 That's ok , Is the use of the ajax Request to send database information to mysql.php.
36: $.post("mysql.php",
37: {
38: mysqlip:mysqlip,
39: mysqlusername:mysqlusername,
40: mysqluserpass:mysqluserpass,
41: mysqldb:mysqldb
42: },
Then we follow the train of thought , I want to see others mysql.php file , The purpose of finding this file is to check whether our database can be connected normally .
<?php
error_reporting(0);
header("Content-type: text/html; charset=utf-8");
$ip = $_POST['mysqlip'];
$username = $_POST['mysqlusername'];
$userpass = $_POST['mysqluserpass'];
$db = $_POST['mysqldb'];
$ok1 = mysql_connect($ip,$username,$userpass)or die(" Database connection error , Please check whether the account or password is correct !");
$ok2 = mysql_select_db($db)or die(" Unable to find database , Please check whether the database name is filled in correctly ");
if($ok1 or $ok2){
echo "ok";
}
?>
Then we follow the train of thought , Let's take a look at the second step of file read-write permission detection , stay /install/index.php In file , The same is used ajax To request the back-end interface , But the requested file is is_writable.php, And in and out file Parameter is config.php.
$("#install_2").click(function(){
$.post("is_writable.php",{
file:'config.php'
}
And found that if_writeable.php The way to judge whether a file has read-write permission is through is_writable() Function to determine config.php Is the document writable .
isset($_POST['file'])?$file = $_POST['file']:$file="config.php";
$is = is_writable($file);
When both test items are tested successfully , The option to install the system immediately will pop up .
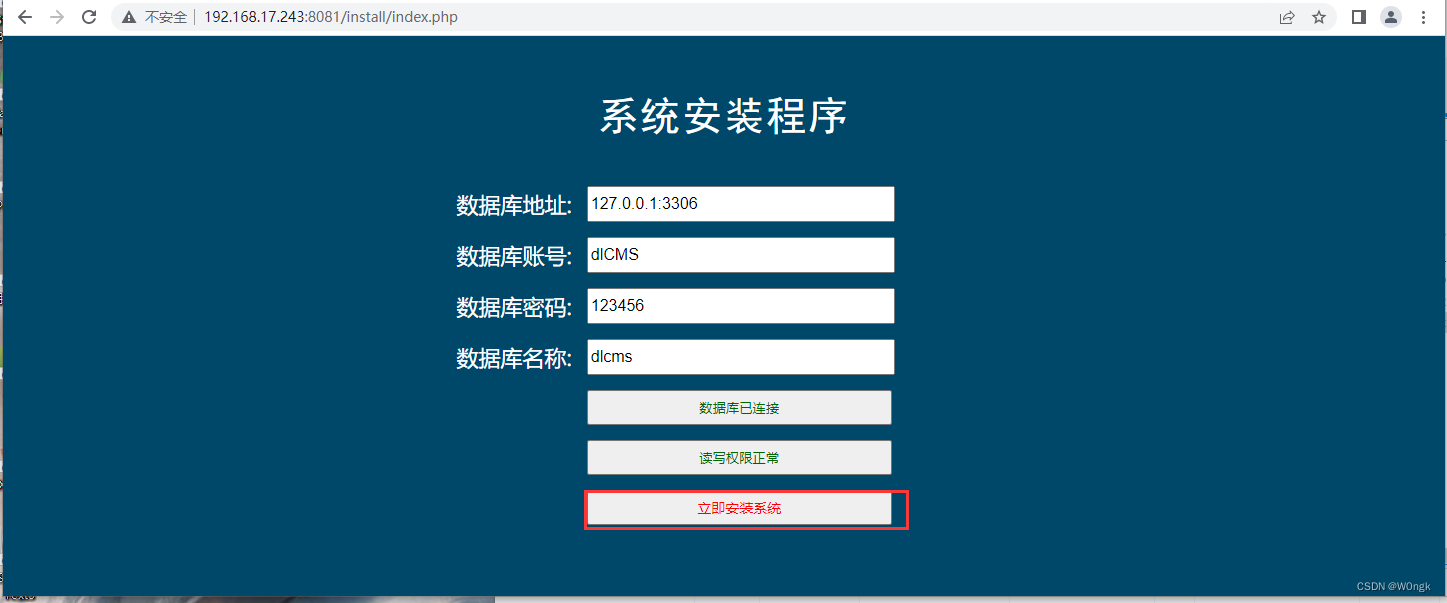
The implementation result of this model selection is through ajax Send parameters related to connecting to the database to the backend “steup.php file ”.
$.post("setup.php",
{
mysqlip:mysqlip,
mysqlusername:mysqlusername,
mysqluserpass:mysqluserpass,
mysqldb:mysqldb
},
stay setup.php in , First, get the parameters of connecting to the database , Then it checks again whether the database can be connected . If the database connection detection result is OK, Will create config.php file . And insert the administrator's account and password , The password here is through MD5 Encrypted , But after the installation is successful , Will prompt admin The password of the account is the first line of the English keyboard , So it is also a password hard coding vulnerability .
In the first 29 That's ok , We see , It will /install In the catalog index.php The file was renamed to index.lock file .
16:if($ok){
17:$mysqlconfig = $ip.'@[email protected]'.$username.'@[email protected]'.$userpass.'@[email protected]'.$db;
18:$config_t = file_get_contents("mysql_config.dll");
19:$config_a = array("@[email protected]","@[email protected]","@[email protected]","@[email protected]");
20:$config_b = array($ip,$username,$userpass,$db);:
21:$mysqlconfig = str_replace($config_a,$config_b,$config_t);
22:$fileok = file_put_contents("../config.php",$mysqlconfig);:
23:if($fileok){
24: echo "installok";
25:$adminsql = "INSERT INTO `dunling_admin` VALUES ('1', 'admin', '90b9aa7e25f80cf4f64e990b78a9fc5ebd6cecad')";
26:$configsql = "INSERT INTO `dunling_config` VALUES ('1', ' Dunling wechat fan alliance system ', 'www.dunling.com', '1.00', '5000.00', '2.00', '10', '0.20', '0.00', '0','25')";
27:mysql_query($configsql,$ok1);
28:mysql_query($adminsql,$ok1);
29:rename("index.php","index.lock");:
30:}else{
31: echo "installno";
32:}
But through the previous analysis , We know , Installing the system is actually setup.php In the document , But the file has not been deleted or renamed , in other words , If we directly construct the database connection parameter request setup.php Words , It will bypass the previous database detection and file permission detection , Reinstall the system directly .
But one notable thing is , When we construct database connection parameters , Relevant parameters are unknown , So we can only rely on social workers or other means to obtain , This is quite difficult to use .
2、 Loophole recurrence
notes : The bar just mentioned , Normally, we don't know the database connection parameters , But here we have obtained the relevant parameters for experiments .
First we see , The installed page looks like this :
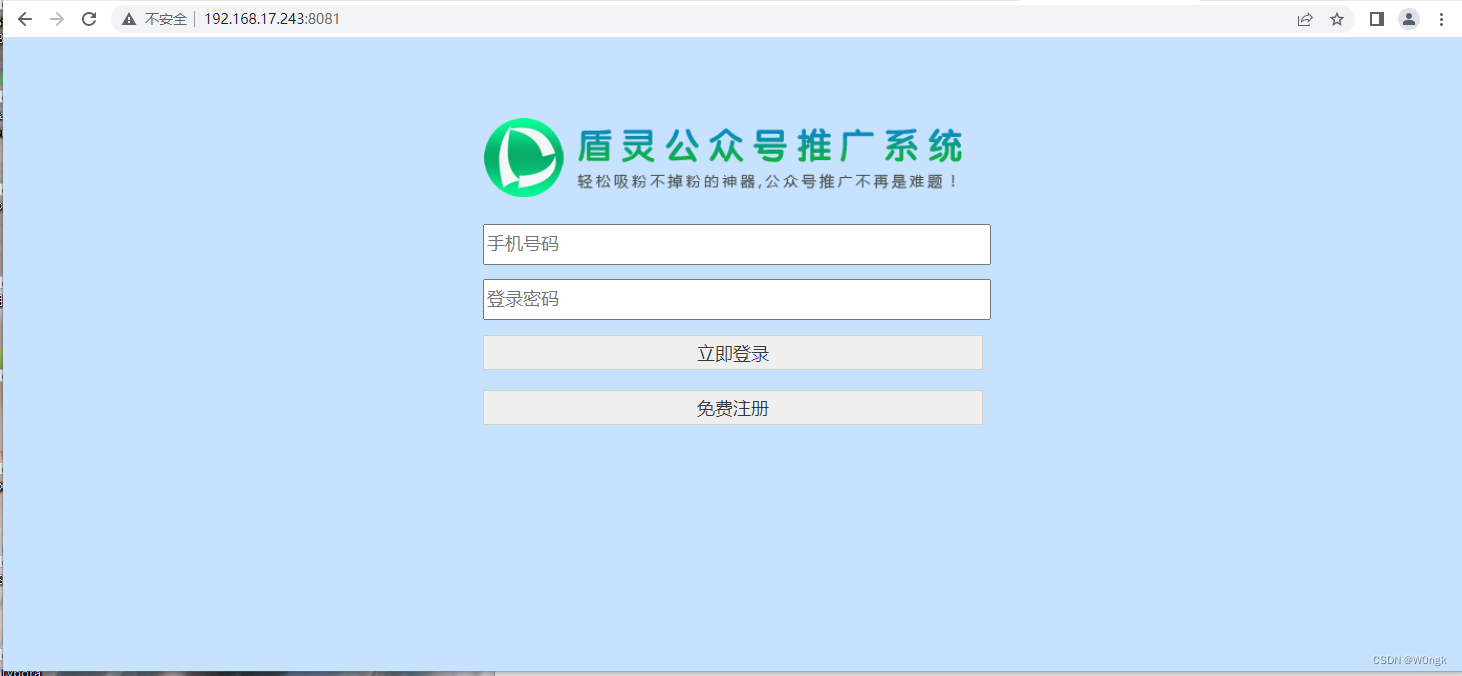
Then we asked /install/setup.php file , And use burpsuite Carry out the bag , Modify the request mode to POST, And set the transmission data as database related parameters , Send a request , You can see the prompt of successful installation .
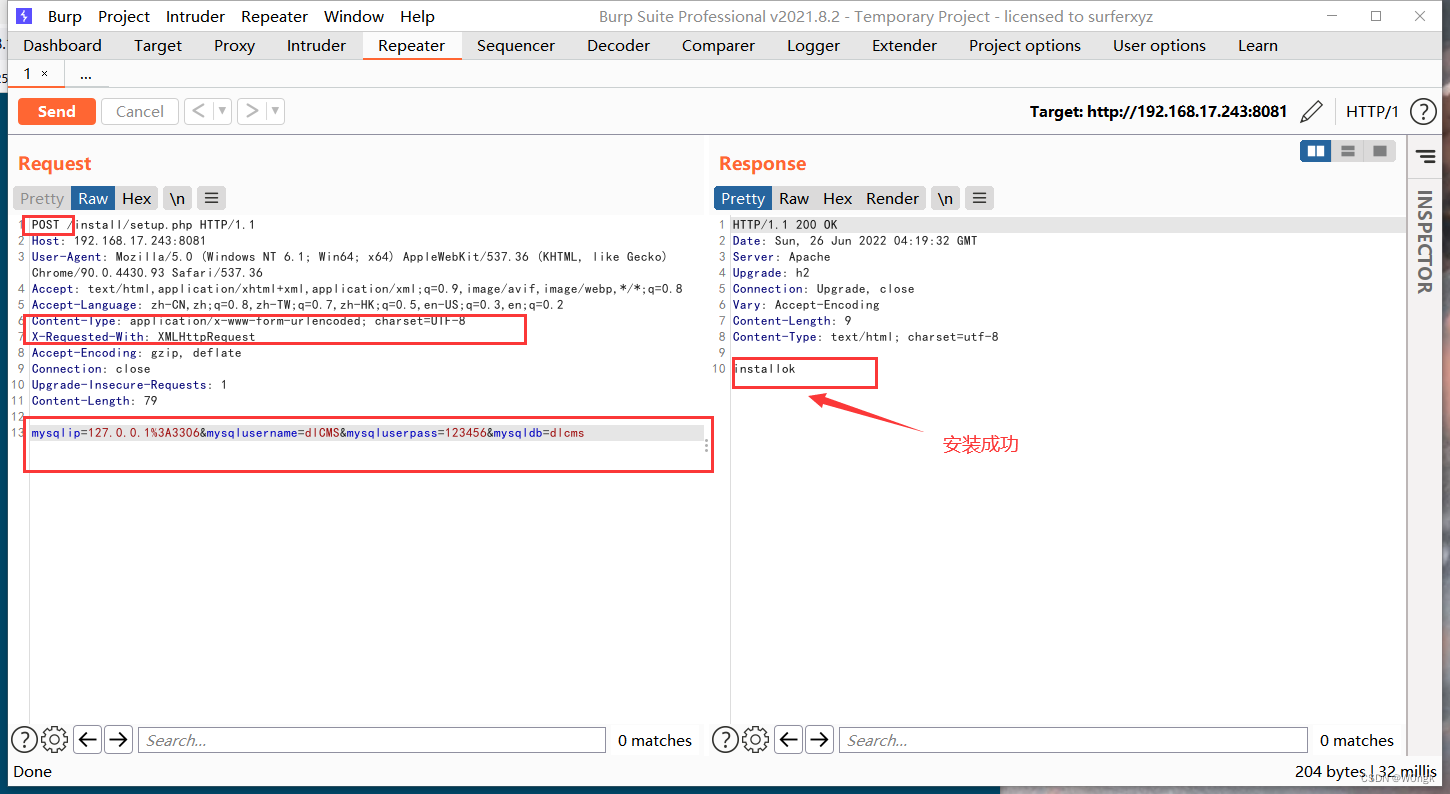
So to conclude , As two relatively recent system reinstallation vulnerabilities that have been discovered at present , It can be seen that their vulnerability logic is due to the situation that installation and detection can be bypassed on different pages . It can be seen that this is indeed a common problem in system installation detection , For new entrants like me who want to exploit such loopholes, you can try this idea more .
边栏推荐
- Get the source code in the mask with the help of shims
- Write a jison parser (7/10) from scratch: the iterative development process of the parser generator 'parser generator'
- Summary of small program performance optimization practice
- Web端自动化测试失败原因汇总
- Go context 基本介绍
- Intelligent gateway helps improve industrial data acquisition and utilization
- Hands on deep learning (44) -- seq2seq principle and Implementation
- 入职中国平安三周年的一些总结
- uniapp 小于1000 按原数字显示 超过1000 数字换算成10w+ 1.3k+ 显示
- uniapp---初步使用websocket(长链接实现)
猜你喜欢
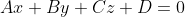
Normal vector point cloud rotation
Web端自动化测试失败原因汇总
Dynamic memory management

PHP代码审计3—系统重装漏洞
Hands on deep learning (36) -- language model and data set

Baidu R & D suffered Waterloo on three sides: I was stunned by the interviewer's set of combination punches on the spot
SSM online examination system source code, database using mysql, online examination system, fully functional, randomly generated question bank, supporting a variety of question types, students, teache
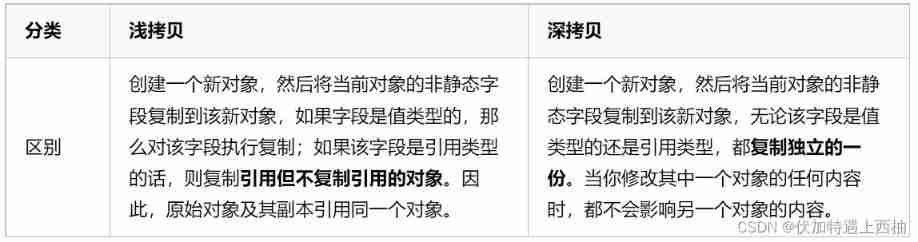
Four common methods of copying object attributes (summarize the highest efficiency)
今日睡眠质量记录78分

5g/4g wireless networking scheme for brand chain stores
随机推荐
Dynamic address book
[200 opencv routines] 218 Multi line italic text watermark
Mmclassification annotation file generation
Sort out the power node, Mr. Wang he's SSM integration steps
Hands on deep learning (36) -- language model and data set
Summary of small program performance optimization practice
Machine learning -- neural network (IV): BP neural network
libmysqlclient.so.20: cannot open shared object file: No such file or directory
Custom type: structure, enumeration, union
使用 C# 提取 PDF 文件中的所有文字(支持 .NET Core)
Hands on deep learning (39) -- gating cycle unit Gru
法向量点云旋转
MySQL transaction mvcc principle
Fabric of kubernetes CNI plug-in
Lauchpad x | MODE
How can people not love the amazing design of XXL job
2021-08-11 function pointer
Svg image quoted from CodeChina
C # use ffmpeg for audio transcoding
Exercise 7-2 finding the maximum value and its subscript (20 points)
