当前位置:网站首页>Seven examples to understand the storage rules of shaped data on each bit
Seven examples to understand the storage rules of shaped data on each bit
2022-07-04 10:25:00 【sqjddb】
In order to understand these seven examples smoothly , The following must be clear :
1. The shaping data is stored in the form of complement ,C The integer of language includes char,short, int,long
2. Improve the overall shape :
In the process of arithmetic operations involving integer numbers , All integer numbers will be converted to integer form ( It's usually int). If int Cannot accommodate all values of the original data type , Then it will be converted into unsigned int To deal with it
3. Rules for integer Promotion :
If it's a signed number , In the front 8*3 Bit complement sign bit
If it's an unsigned number , Then the front face 8*3 Place complement 0
4. use char Type can store integer range 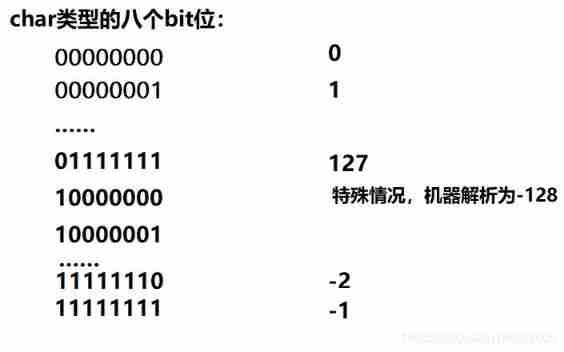 therefore char The range of integers that can be stored by type is -128~127
therefore char The range of integers that can be stored by type is -128~127
Look at these examples after understanding
①
// What output ?
#include <stdio.h>
int main()
{
char a= -1;
signed char b=-1;
unsigned char c=-1;
printf("a=%d,b=%d,c=%d",a,b,c);
return 0;
}
Running results :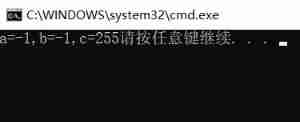
-1 Of
Original code :10000000 00000000 00000000 00000001
Inverse code :11111111 11111111 11111111 11111110
Complement code :11111111 11111111 11111111 11111111
char Type can only be stored low 8 A bit 11111111
The title is printed with plastic , There's an integer boost , According to integer promotion rules
a,b All promoted to 11111111 11111111 11111111 11111111
and c Upgrade to 00000000 00000000 00000000 11111111
These are complements , The corresponding is -1 -1 255
②
#include <stdio.h>
int main()
{
char a = -128;
printf("%u\n",a);
return 0;
}
③
#include <stdio.h>
int main()
{
char a = 128;
printf("%u\n",a);
return 0; }
②③ The running results of are all the figures in the figure below 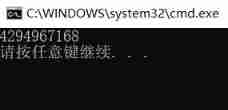
-128 Of
Original code :10000000 00000000 00000000 10000000
Inverse code : 111111111 11111111 11111111 01111111
Complement code :111111111 11111111 11111111 10000000
128 Of
Original code :00000000 00000000 00000000 10000000
Inverse code :011111111 11111111 11111111 01111111
Complement code :011111111 11111111 11111111 10000000
low 8 individual bit Bits are stored in char in 10000000
Print as unsigned integer , Integer raised to 00000000 00000000 00000000 10000000
The data corresponding to this complement is the data in the above figure
④
#include <stdio.h>
int main()
{
int i = -20;
unsigned int j = 10;
printf("%d\n", i + j);
}
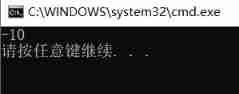
-20 Of
Original code :10000000 00000000 00000000 00010100
Inverse code :11111111 11111111 11111111 11101011
Complement code :11111111 11111111 11111111 11101100
10 Of
Original inverse complement :00000000 00000000 00000000 00001010
Add the two complements to get
11111111 11111111 11111111 11110110
Print in integer
Subtract one from the above complement :
11111111 11111111 11111111 11110101
Take the opposite :
10000000 00000000 00000000 00001010
That is to say -10
⑤
int main()
{
char a[1000];
int i;
for(i=0; i<1000; i++)
{
a[i] = -1-i;
}
printf("%d",strlen(a));
return 0;
}
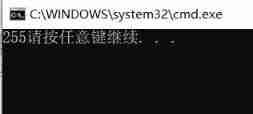
char The range of integers that the type can store is -128~127
The above example is deposited in sequence -1 -2 …… -128 , When you want to store -129 when
-129 Of
Original code :10000000 00000000 00000000 10000001
Inverse code :11111111 11111111 11111111 01111110
Complement code :11111111 11111111 11111111 01111111
Store low 8 individual bit position 01111111, So I want to store -129 When actually deposited 127, After that, it is deposited into 126~0
So the deposit is -1 , -2 …… -128, 127 …… 1 , 0
The length is 128+127=255
⑥
#include <stdio.h>
unsigned char i = 0;
int main()
{
for(i = 0;i<=255;i++)
{
printf("hello world\n");
}
return 0;
}
The result of this example is dead circulation , Because there is no sign char When storing integers The scope is 0~255
When stored 255 When is 11111111
Add one more and change it into 00000000
Fall into a dead cycle
⑦
#include <stdio.h>
int main()
{
unsigned int i;
for (i = 9; i >= 0; i--)
{
printf("%u\n", i);
}
}
The running result of this example is also dead cycle , Because unsigned numbers are always greater than or equal to 0!
边栏推荐
- The future education examination system cannot answer questions, and there is no response after clicking on the options, and the answers will not be recorded
- DDL statement of MySQL Foundation
- Batch distribution of SSH keys and batch execution of ansible
- MySQL develops small mall management system
- From programmers to large-scale distributed architects, where are you (2)
- Intelligent gateway helps improve industrial data acquisition and utilization
- Latex arranges single column table pictures in double column format articles
- Static comprehensive experiment ---hcip1
- 有老师知道 继承RichSourceFunction自定义读mysql怎么做增量吗?
- Whether a person is reliable or not, closed loop is very important
猜你喜欢
From programmers to large-scale distributed architects, where are you (2)
IPv6 comprehensive experiment

Hands on deep learning (40) -- short and long term memory network (LSTM)
Architecture introduction
Occasional pit compiled by idea
Work order management system OTRs
基于线性函数近似的安全强化学习 Safe RL with Linear Function Approximation 翻译 1
入职中国平安三周年的一些总结
Custom type: structure, enumeration, union

Safety reinforcement learning based on linear function approximation safe RL with linear function approximation translation 1
随机推荐
Kotlin: collection use
六月份阶段性大总结之Doris/Clickhouse/Hudi一网打尽
DML statement of MySQL Foundation
AUTOSAR from getting started to mastering 100 lectures (106) - SOA in domain controllers
Laravel文档阅读笔记-How to use @auth and @guest directives in Laravel
Devop basic command
Hands on deep learning (42) -- bi-directional recurrent neural network (BI RNN)
Rhsca day 11 operation
用数据告诉你高考最难的省份是哪里!
RHCE - day one
Hands on deep learning (46) -- attention mechanism
SQL replying to comments
Introduction to extensible system architecture
Reasons and solutions for the 8-hour difference in mongodb data date display
Basic principle of servlet and application of common API methods
Exercise 8-7 string sorting (20 points)
Work order management system OTRs
转载:等比数列的求和公式,及其推导过程
什么是 DevSecOps?2022 年的定义、流程、框架和最佳实践
AUTOSAR从入门到精通100讲(106)-域控制器中的SOA