当前位置:网站首页>Two way process republication + routing policy
Two way process republication + routing policy
2022-07-04 10:20:00 【Attiude】
Two way process republishing + Routing strategy
Related knowledge :
Multipoint two-way republishing : Between two routing protocols or two processes of the same protocol , Use multiple stations ASBR To republish , Realize link backup , Improve network stability and efficiency ;
There may be problems :
In multipoint bidirectional republishing , The first ASBR After the republish is complete , May be republished to B Routing entry for the protocol , Will affect other ABSR, Refresh their routing tables ; Result in routing entries from A The agreement is published to B After the agreement , And back to A agreement :
1、 Routing feedback
2、 Leading to serious poor routing
Solution :
stay cisco In the system eigrp agreement , The default multi-point publishing protocol is the same as other two-way publishing protocols , There will be no routing feedback — cisco In the system rip priority 120 ospf 110 eigrp 90 But the re release goes into eigrp The priority of partial routing is 170;
Because of the different priorities , Make the first ASBR After republishing , It won't affect the other one ASBR The routing table for , Therefore, there is no routing feedback ;
In the Huawei system , Because there is no eigrp, So Huawei is ospf Agreement , The double priority approach is also used ;
ospf The routing priority normally generated is 10, Redistribute incoming 5/7 class LSA, The generated route is 150;
notes : stay ospf Agreement , Loopback works by default based on 32 Bit host routing for delivery ; Therefore, in multi-point two-way republishing ,ASBR It belongs to ospf When the loopback interface of the protocol is republished ,ospf Press 32 Bit transfer , Other protocols will share according to the actual mask of the interface ; If the masks are inconsistent , Will lead to routing problems , Configure loopback interface as 32 Bit host routing , Or modify the loopback interface in ospf The working methods in the agreement can be
Routing strategy :
Noun :
** Control level :** Dynamic routing protocol is the flow of routing protocol information , The direction is the flow direction of the control layer
Data level : The router uses the generated routing table , Forwarded user data traffic ; The direction is opposite to the control level
Routing strategy : When the traffic at the control level enters or leaves the router interface , Grab traffic ; Modify or discard the content , Finally, it affects the generation of routing table , Interfere with the routing of the router ;
【1】 Grab traffic
1)ACL Access control list
ACL It is designed to deal with data level traffic restrictions ; It can also be used to capture the flow at the control level ;
But because of ACL The design is based on data level traffic , Therefore, we do not pay attention to the subnet mask in the packet ; So that when grasping the flow of the control layer , May not match exactly ;
2) The prefix list – It is specially used to capture the flow at the control level , Exact match subnet mask
【2】 Routing strategy — Modify the parameters in the flow control layer
The strategy is a hop by hop behavior , Effects can be superimposed ; Multiple interfaces through which the traffic passes in the whole path are configured with metrics , Finally, add a measure to the total ;
3、 Call... When republishing
[r2]ospf 1
[r2-ospf-1]import-route rip 1 route-policy Huawei
Configuration Guide :
1、 Even if you want to reject a traffic , Permission must also be used when grasping , Then reject in the routing policy ;
2、 Match one by one from top to bottom , If the previous item matches, follow the previous item , Don't view the next , The end implicitly rejects all
3、 In one rule , If there is no flow matching, it is to match all ; If there is no application, only the current big action is performed on the matching traffic ;
Therefore, an empty table with large actions allowed represents that all ;
4、 or And Relationship
Or relationship for each site ( Each serial number ) Between or in relation to ;
Serial number 10 No matching traffic , Then the serial number 20;
Summarize or relate to :
The entry is based on the site number ( Serial number ) Match one by one from top to bottom , If the previous item matches, follow the previous item , Don't view the next — Or relationship
In each serial number , Match all traffic at the same time , Perform all small actions at the same time — And relationships
The experimental requirements :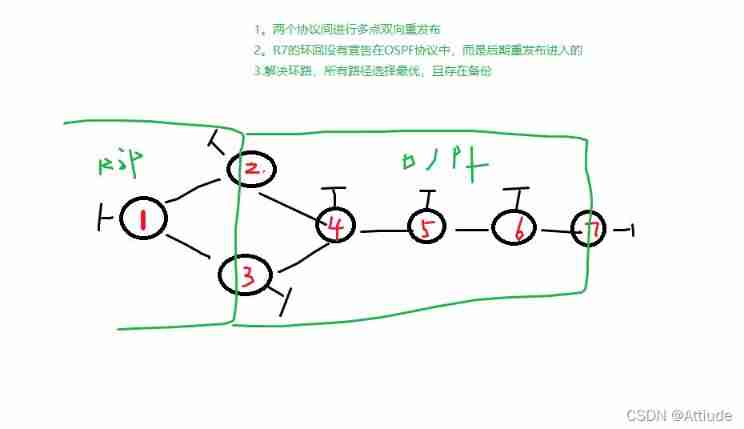
Topology :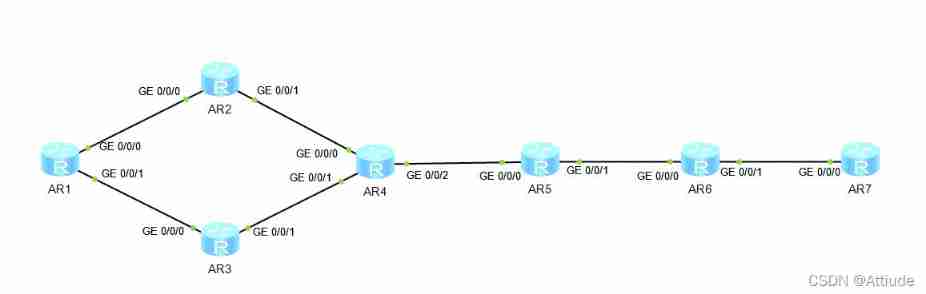
1、 To configure IP Address :
[r1]int g0/0/0
[r1-GigabitEthernet0/0/0]ip add 12.1.1.1 24
[r1-GigabitEthernet0/0/0]int g0/0/1
[r1-GigabitEthernet0/0/1]ip add 13.1.1.1 24
[r1]int l0
[r1-LoopBack0]ip add 1.1.1.1 24
[r2]int g0/0/0
[r2-GigabitEthernet0/0/0]ip add 12.1.1.2 24
[r2-GigabitEthernet0/0/0]int g0/0/1
[r2-GigabitEthernet0/0/1]ip add 24.1.1.1 24
[r2]int l0
[r2-LoopBack0]ip add 2.2.2.2 24
The same goes for other routers , The following only shows the interface information of the router :
R3:
GigabitEthernet0/0/0 13.1.1.2/24
GigabitEthernet0/0/1 34.1.1.1/24
LoopBack0 3.3.3.3/24
R4:
GigabitEthernet0/0/0 24.1.1.2/24
GigabitEthernet0/0/1 34.1.1.2/24
GigabitEthernet0/0/2 45.1.1.1/24
LoopBack0 4.4.4.4/24
R5:
GigabitEthernet0/0/0 45.1.1.2/24
GigabitEthernet0/0/1 56.1.1.1/24
LoopBack0 5.5.5.5/24
R6:
GigabitEthernet0/0/0 56.1.1.2/24
GigabitEthernet0/0/1 67.1.1.1/24
LoopBack0 6.6.6.6/24
R7:
GigabitEthernet0/0/0 67.1.1.2/24
LoopBack0 7.7.7.7/24
2、 According to the requirements of the experiment , stay R1/R2 Loopback /R3 Running on the interface of RIP agreement
[r1]rip 1
[r1-rip-1]v 2
[r1-rip-1]net 1.0.0.0
[r1-rip-1]net 12.0.0.0
[r1-rip-1]net 13.0.0.0
[r2]rip 1
[r2-rip-1]v 2
[r2-rip-1]net 2.0.0.0
[r2-rip-1]net 12.0.0.0
rip 1
version 2
network 13.0.0.0
In addition rip Areas and r7 Outside the loop , function OSPF agreement
[r2]ospf 1 router-id 2.2.2.2
[r2-ospf-1]area 0
[r2-ospf-1-area-0.0.0.0]net 24.1.1.1 0.0.0.0
[r3]ospf 1 router-id 3.3.3.3
[r3-ospf-1]area 0.0.0.0
[r3-ospf-1-area-0.0.0.0]network 3.3.3.3 0.0.0.0
[r3-ospf-1-area-0.0.0.0]network 34.1.1.1 0.0.0.0
R4:
area 0.0.0.0
network 4.4.4.4 0.0.0.0
network 24.1.1.2 0.0.0.0
network 34.1.1.2 0.0.0.0
network 45.1.1.1 0.0.0.0
R5:
area 0.0.0.0
network 5.5.5.5 0.0.0.0
network 45.1.1.2 0.0.0.0
network 56.1.1.1 0.0.0.0
R6:
area 0.0.0.0
network 6.0.0.0 0.0.0.255
network 6.6.6.6 0.0.0.0
network 56.1.1.2 0.0.0.0
network 67.1.1.1 0.0.0.0
R7:
area 0.0.0.0
network 67.1.1.2 0.0.0.0
3、 At every ASBR Yes rip、ospf、r7 Loopback for two-way republication :
R3:
[r3-rip-1]import-route ospf
[r3-ospf-1]import-route rip
R2:
[r2-rip-1]import-route ospf
[r2-ospf-1]import-route rip
R7:
[r7-ospf-1]import-route direct
After republishing , We see the R2 The routing table for :
We found that , Go to R3 There are two routes for loopback , from ospf The learned mask 32 position , from rip What I learned 24 position , Because the masks of routes are different , Are added to the routing table , We only need one , There are two ways :
1、 modify R3 Looped IP
2、 modify R3G0/0/1 Work type of interface
Modify the interface type :
[r3-GigabitEthernet0/0/1]ospf network-type broadcast
It takes effect after restarting the interface , Let's check the routing table :
We found that , Only go to... Is left in the routing table R3 A route of
Next , We use it R1pingR7 The loopback of , Find no way :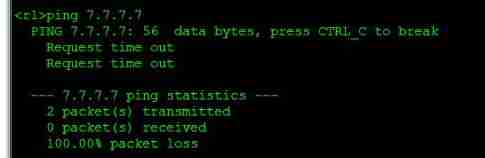
Observe by grabbing bags , Find a lot ICMP package , And check the routing table and find R1—>R2—>
R34—>R3, A loop has occurred .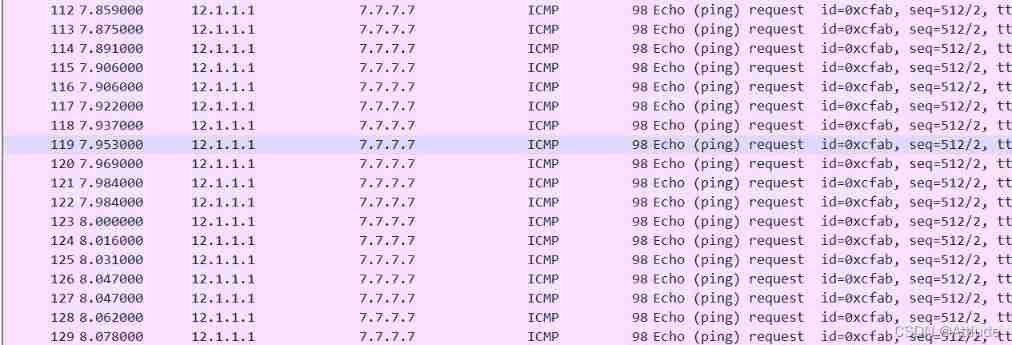
R1:
R2:
R4:
R3:
We found that , The root cause of contact ring is 7.7.7.7 adopt R2 Republish to rip The priority in the area changes to 100, But after R3 After the re release of , The priority becomes 150, therefore R4 Find out from R3 and R5 You can go to R7, also R3 More direct , So I chose R3.
Next , To solve this problem without affecting redundant backups , We can carry out routing strategy , Will be taken from R2 or R3 In the R7 The priority of loopback of is changed to be higher than 150 Big , therefore R4 Will choose R5 To arrive R7 The loopback of .
Next, configure :
[r1]route-policy a permit node 10
[r1-route-policy]apply preference 151
[r1-rip-1]preference route-policy a
Achieve a goal , Try to use R1ping7.7.7.7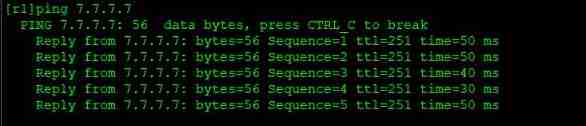
边栏推荐
- Basic principle of servlet and application of common API methods
- leetcode1-3
- 【Day2】 convolutional-neural-networks
- [FAQ] summary of common causes and solutions of Huawei account service error 907135701
- 用数据告诉你高考最难的省份是哪里!
- 按键精灵打怪学习-识别所在地图、跑图、进入帮派识别NPC
- AUTOSAR从入门到精通100讲(106)-域控制器中的SOA
- leetcode729. My schedule 1
- leetcode1229. Schedule the meeting
- What are the advantages of automation?
猜你喜欢
技术管理进阶——如何设计并跟进不同层级同学的绩效
【Day2】 convolutional-neural-networks
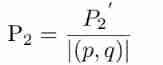
Latex error: missing delimiter (. Inserted) {\xi \left( {p,{p_q}} \right)} \right|}}
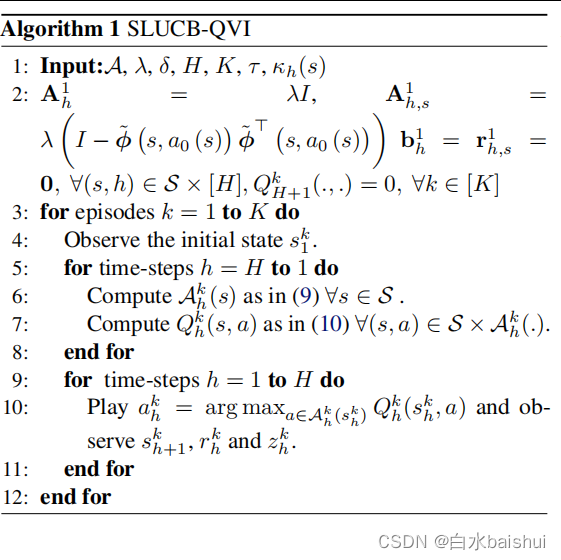
Safety reinforcement learning based on linear function approximation safe RL with linear function approximation translation 1

5g/4g wireless networking scheme for brand chain stores
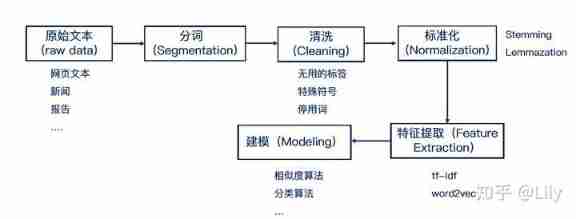
Hands on deep learning (35) -- text preprocessing (NLP)
Rhcsa learning practice
Pcl:: fromrosmsg alarm failed to find match for field 'intensity'

Latex learning insertion number - list of filled dots, bars, numbers

【OpenCV 例程200篇】218. 多行倾斜文字水印
随机推荐
Ruby时间格式转换strftime毫秒匹配格式
【OpenCV 例程200篇】218. 多行倾斜文字水印
Lavel document reading notes -how to use @auth and @guest directives in lavel
Hands on deep learning (44) -- seq2seq principle and Implementation
查看CSDN个人资源下载明细
Legion is a network penetration tool
Regular expression (I)
Fabric of kubernetes CNI plug-in
Dos:disk operating system, including core startup program and command program
How can people not love the amazing design of XXL job
Doris / Clickhouse / Hudi, a phased summary in June
Hands on deep learning (43) -- machine translation and its data construction
2. Data type
Safety reinforcement learning based on linear function approximation safe RL with linear function approximation translation 2
Reprint: summation formula of proportional series and its derivation process
【FAQ】华为帐号服务报错 907135701的常见原因总结和解决方法
SQL replying to comments
Exercise 7-3 store the numbers in the array in reverse order (20 points)
基于线性函数近似的安全强化学习 Safe RL with Linear Function Approximation 翻译 1
Laravel文档阅读笔记-How to use @auth and @guest directives in Laravel