当前位置:网站首页>Network connection (II) three handshakes, four waves, socket essence, packaging of network packets, TCP header, IP header, ACK confirmation, sliding window, results of network packets, working mode of
Network connection (II) three handshakes, four waves, socket essence, packaging of network packets, TCP header, IP header, ACK confirmation, sliding window, results of network packets, working mode of
2022-07-04 10:30:00 【Big bear loves to work】
How is the network connected _ Learning notes ( The first 2 Chapter )
Just stick to it slowly , The worst result is nothing more than late success
- How is the network connected _ Learning notes ( The first 2 Chapter )
- 2.0 Preface
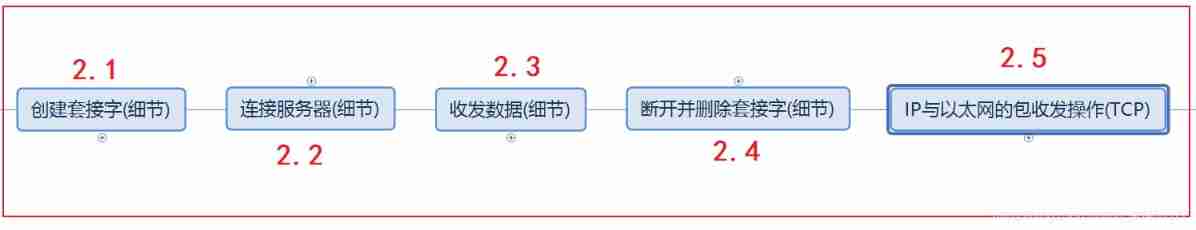
- 2.1 Create socket and its details
- 2.2 Connection server and its details
- 2.3 Send and receive data and its details
- 2.4 Disconnect and delete the socket and its details
- 2.5 IP Packet sending and receiving operation with Ethernet (TCP)
- 2.6 A term is used to explain
- 2.7 The last two maps are a list ( When I have finished the whole book, I will upload and share it for free )
2.0 Preface
- The mind map in this chapter is written before and after a business trip 20 Many days , This article is mainly based on my understanding of the network , I hope you can understand the content clearly , I hope it can help readers , It's my great honor .
- The text part mainly talks about a framework and ideas , The specific details are presented in the mind map .
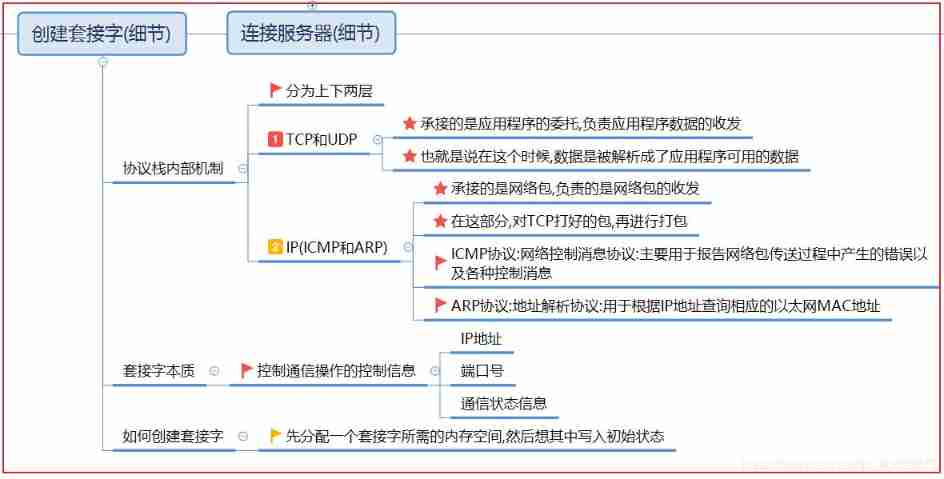
2.1 Create socket and its details
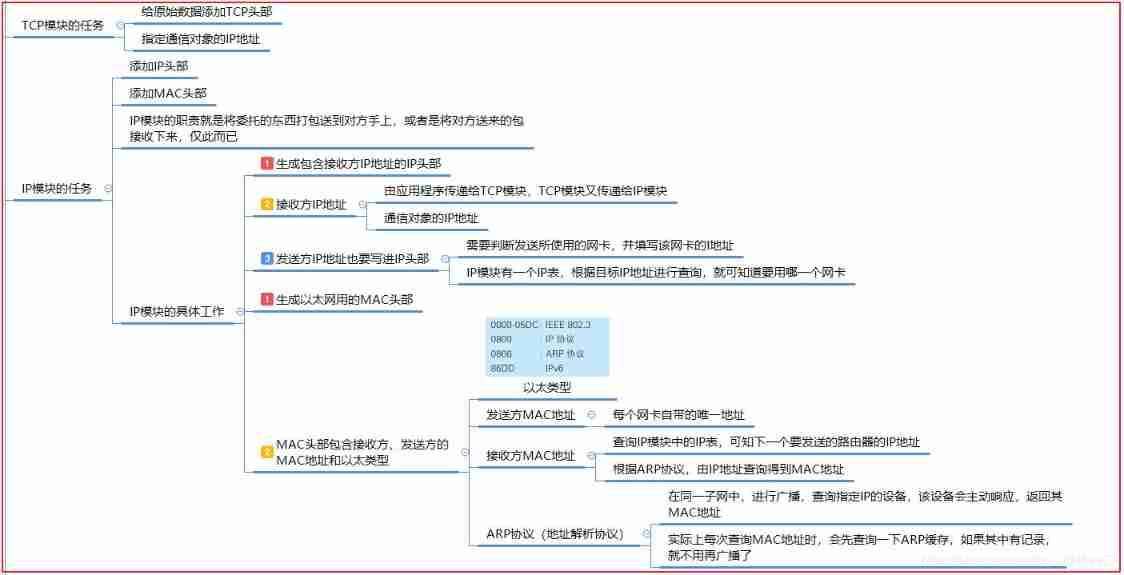
The data to be sent is submitted to the protocol stack from the application , The protocol stack is divided into two layers , Above is TCP/UDP modular , Here is IP modular . For general TCP/IP Protocol communication , Naturally, these data will be handed over to TCP Module to handle , after TCP After processing, give the data to IP modular ( This will be discussed in detail below )
Creating sockets , The code implementation is very simple, as shown below
// Win Create Socket Of API SOCKET WSAAPI socket( int af, int type, int protocol );socket The essence of socket is a pile of control information related to network communication , such as IP Address 、 Port number 、 Current communication status, etc
The essence of creating sockets is to allocate a piece of memory that can be used to store these control information , Then write the initial state information
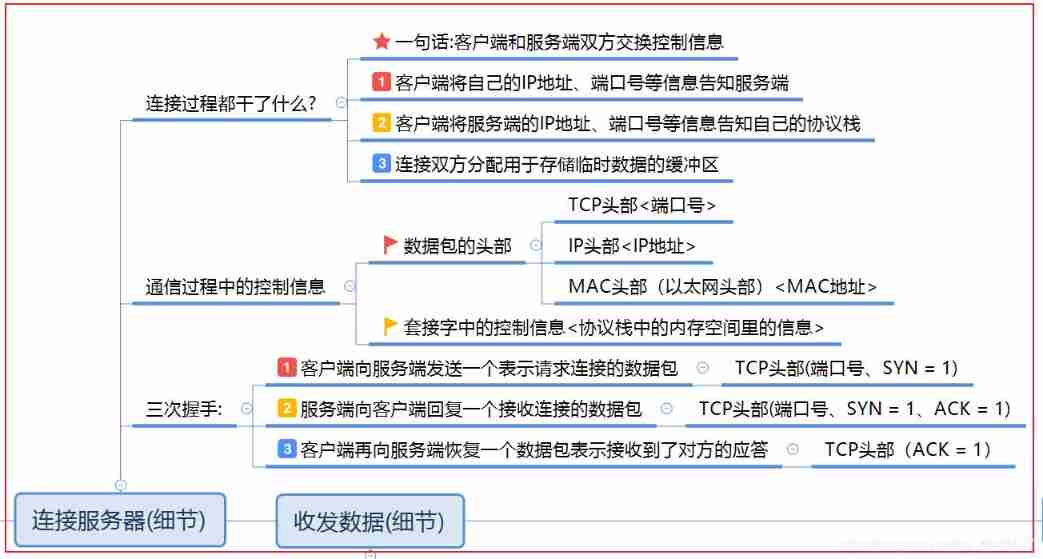
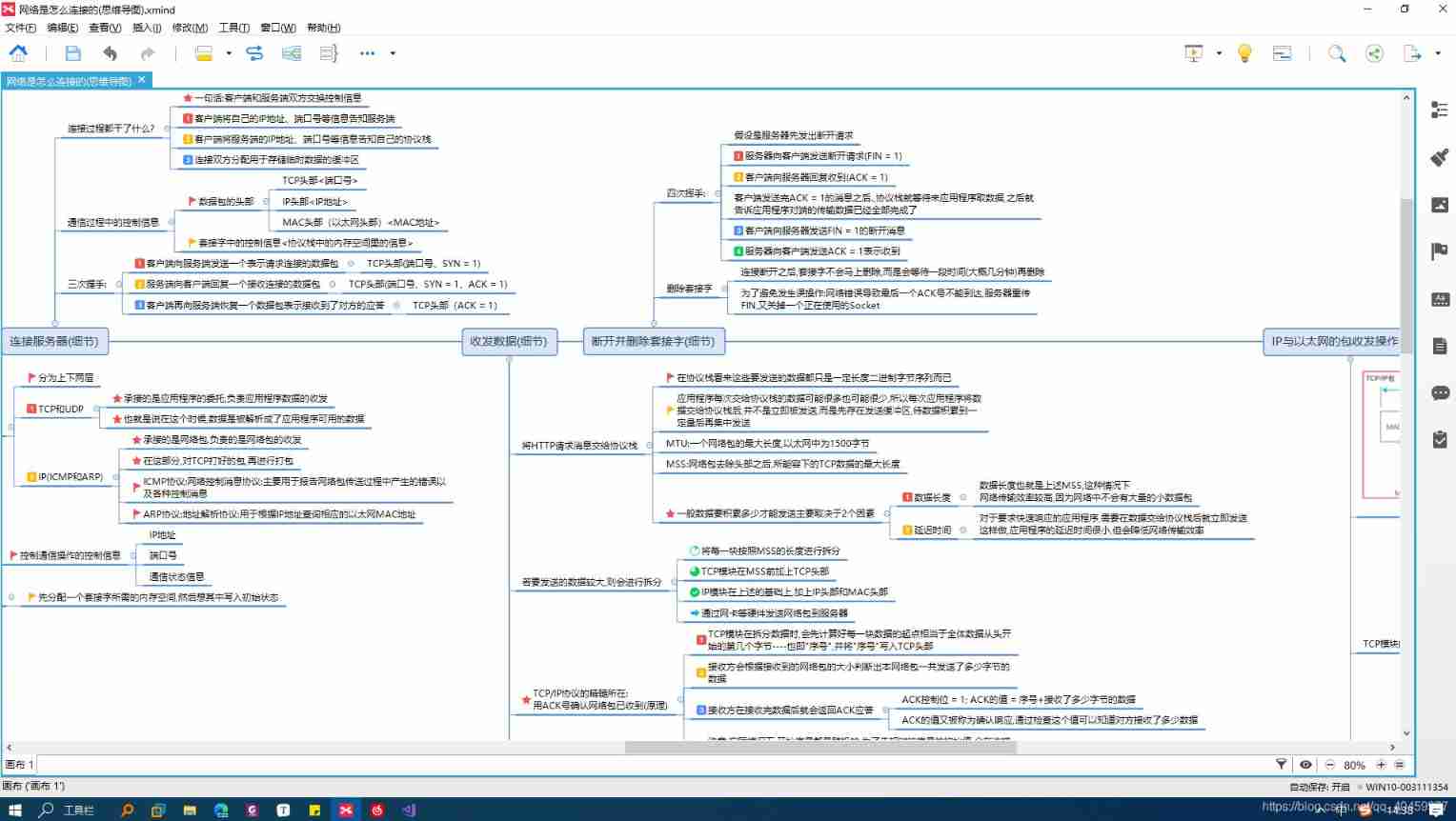
2.2 Connection server and its details
- Connect to server , That is the so-called process of establishing connections , We know TCP\IP Communication is characterized by connection based 、 reliable . This step is the connection step
- Connect the purpose of the connection It mainly exchanges control information between the client and the server , Because this is the basis of communication .
- The client will own IP Address 、 Inform the server of the port number , The server informs its protocol stack of this information ( The first 1 The second handshake )
- The server will return its own IP Address 、 Port number and other information , After receiving this information, the client will inform its own protocol stack of the information of the server or the opposite end ( The first 2 The second handshake )
- The client replies a message to the server, indicating that it has received the data from the server ( The first 3 The second handshake )
- If all goes well , Both parties will allocate buffers for storing temporary data
- thus , Successful connection , Then you can send and receive data happily
2.3 Send and receive data and its details
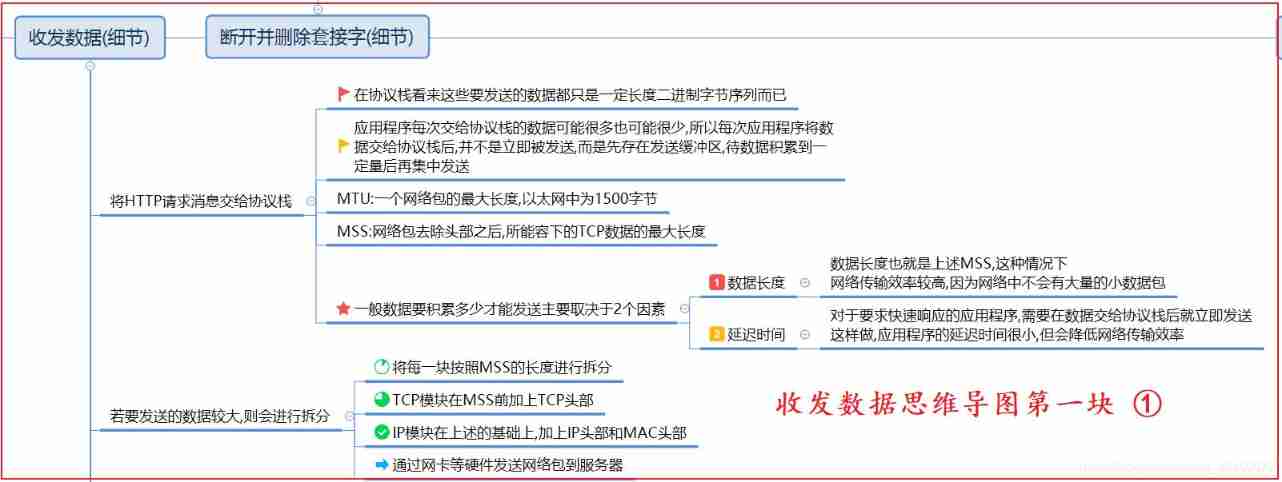
- Or the application software such as browser will give the data to the protocol stack , In the view of the protocol stack , There is no difference between these data Binary byte sequence .
- The protocol stack will be based on Data length and Delay time The requirement of determines the timing of data transmission
- The data length is the maximum amount of data that can be sent by a network packet ----- Network packets can be larger Improve network transmission efficiency , But it will make The delay time increases
- The delay time is the time difference between the data being submitted to the protocol stack and the data being sent by the protocol stack — After the protocol stack receives the data Send it now It will reduce the transmission efficiency of network packets , Also can make The delay time is reduced
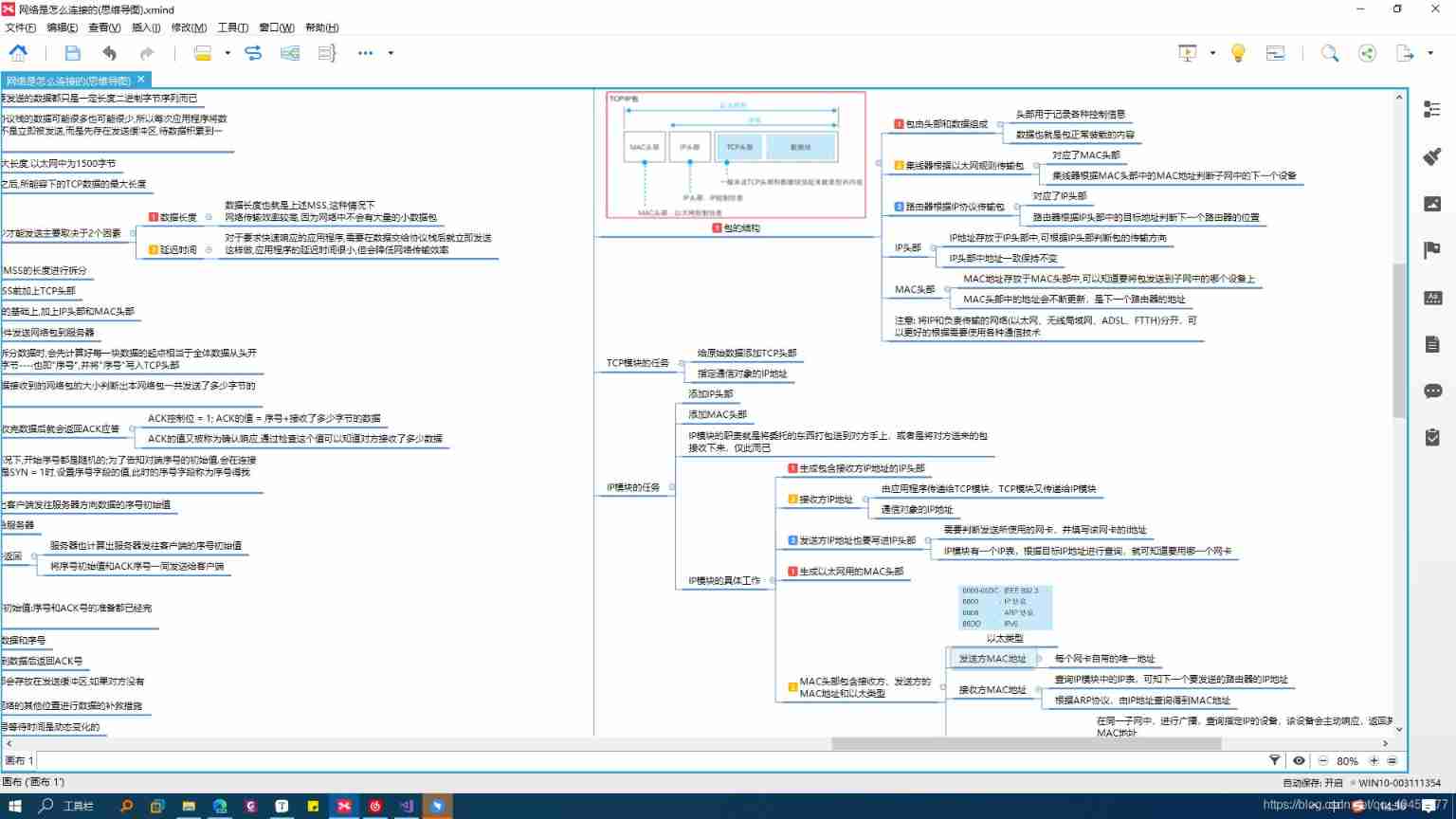
- Get the raw data from the application , If it is too big , More than the MSS( The maximum amount of data a network packet can carry ), Will be subcontracted . Then package the data , The packaging process is as follows :
- TCP Package the raw data ----> add TCP Head
- IP The module repackages the above package ----> add IP Head
- IP The module continues to package the above package ----> add MAC Head
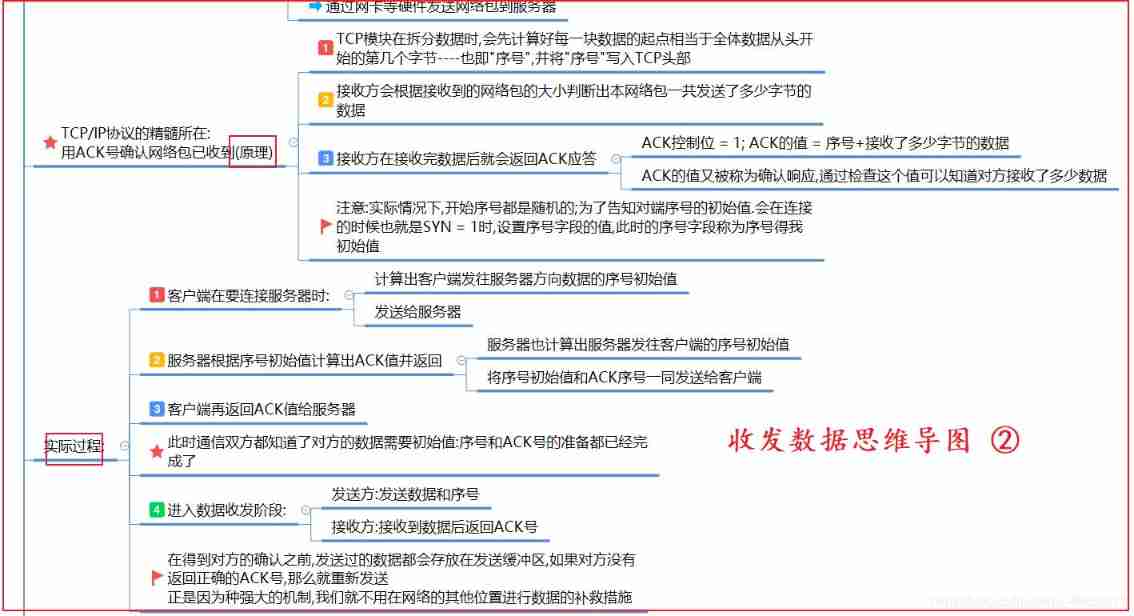
- TCP/IP Protocol transmission is very reliable , What does he rely on to achieve this reliability ?
- ACK No. confirmation is the most important factor , That is to say Confirm response
- If a network packet sends the data , Then there is no need for subcontracting and other operations , After the opposite end receives the data , You need to return a confirmation response
- If subcontracting is required , Then each time you send a network packet, you should focus on Serial number Field , This serial number represents the order of the network packet in the packet before splitting ( Location ), These packets are sent to the opposite end , It will be reorganized according to the serial number , Reconstitute the original data
- Based on the above basic principles , client — The actions of the server when sending and receiving data are roughly as follows
- The client connects to the server , Tell the server the starting serial number of your data , Trying to establish a connection ( This initially occurred during the first handshake )
- After the server receives it , Calculated according to the serial number received ACK value 、 Send the starting serial number of the data on your side to the client ( Occurs in the second handshake )
- When the client receives , Calculate again ACK Number , Back to the server ( The third handshake ----- Connection established successfully )
- From this step, the data sending and receiving stage ,TCP/IP It's full duplex , That is, both ends can send and receive data at the same time
- The sender sends a network packet containing data and an updated sequence number
- When the receiver receives the data , return ACK No. for response confirmation

As mentioned above , After receiving the data, the receiver will ACK No. return , That is to say Confirm response . Only after receiving the confirmation response will the sender think that its data has been correctly received , Otherwise, it will be resend !
So here comes the question , It's like dating someone , How long will it take to be considered that the other party won't come ? Here is waiting ACK How long ?( How long is the timeout ?)
We can analyze it a little :
① If the current network condition is not very good , A little crowding is bound to cause ACK The return time becomes longer , But just give time in your pocket ,ACK( Confirm response ) Will arrive , So the timeout can't be too short .
② If the network is very poor, very poor , Even the network cable is broken , All in all , The data cannot be returned , Then wait a long time at the sender ,ACK Confirm that the response will not be large , So the timeout cannot be infinite .
The actual treatment is Dynamically adjust the timeout
- When ACK When the return is very fast , Just shorten the timeout
- When ACK When the return is slow , Extend the timeout appropriately
== Often asked about sliding window technology
- Sliding window technology is used to improve TCP\IP Mechanism of network communication efficiency
- imagine , If the sender has to wait every time after sending data ACK Send the next packet after returning the confirmation , So did the waiting time soon be greatly wasted ?《 The teacher once said :“ Waste and corruption are great crimes !”》 therefore , Sliding windows came into being .
- Specifically, it is also relatively simple : Just don't wait ACK return , Just send the next packet directly
- However, the receiving party may have limited ability to receive data , If the sender keeps sending tirelessly , It will inevitably lead to data transmission errors , Therefore, the receiver is just before sending and receiving data , You need to tell the opposite end the amount of data you can receive , This data volume is Window size
- In fact, when establishing a connection , Both ends will tell the opposite end the size of their windows . Then in the subsequent data sending and receiving process , The window size will be updated in time , because The window size field is also TCP A field in the header
2.4 Disconnect and delete the socket and its details
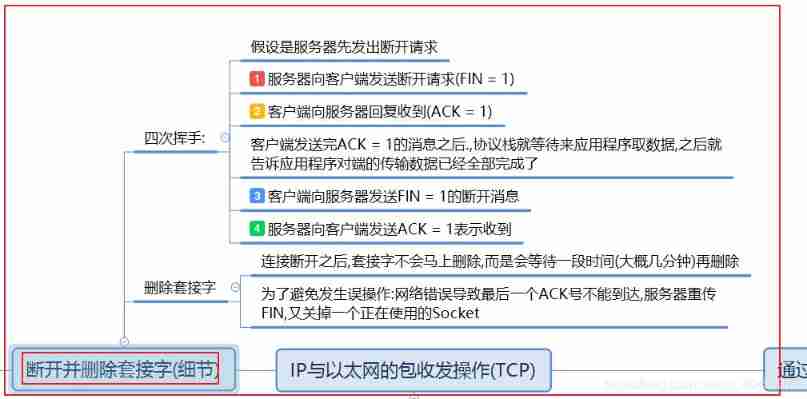
The process of disconnecting is very famous **“ Four waves ”** 了 , In fact, after understanding three handshakes , It's easy to understand four waves
As shown in the mind map above :( Four waves )
① The server sends a disconnect request to the client (FIN = 1) It can also be initiated by the client , This varies with the application
② When the client receives , Reply to the server to confirm the response (ACK = 1)
③ The client sends a disconnect request to the server (FIN = 1)
④ When the server receives , Reply to the client with a confirmation response (ACK = 1)
2.5 IP Packet sending and receiving operation with Ethernet (TCP)
2.5.1 The structure of network package
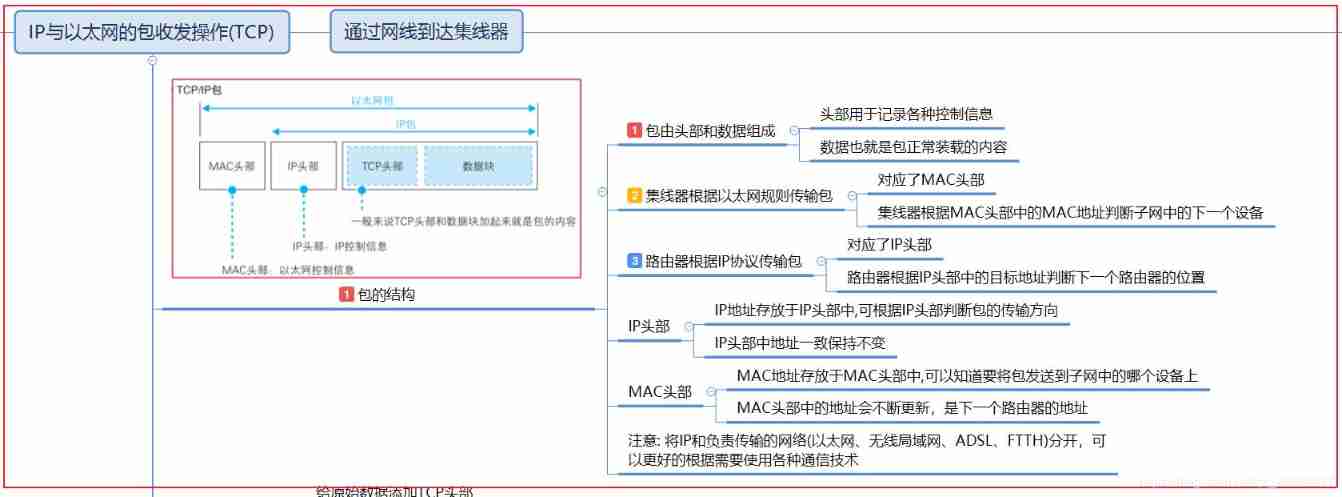
2.5.3 In the protocol stack TCP and IP modular
Structure diagram of protocol stack
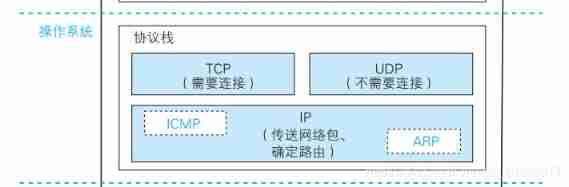
TCP Modules are mainly packaged TCP Head ( Including the control information required for communication 、 Port number and give IP The module specifies the opposite IP Address, etc )
IP Modules are mainly packaged IP Head ( Including their own IP Address 、 To the end IP Address, etc ) pack MAC Head ( Of sender and receiver MAC Address )
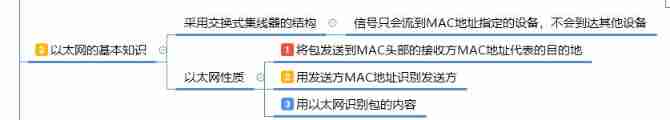
2.5.3 Basic knowledge of Ethernet
- MAC Address is service and Ethernet protocol communication Of , Data will only flow to MAC Address specified device , Will not run to other places
2.5.4 Basic knowledge of network card
- The network card structure is as follows
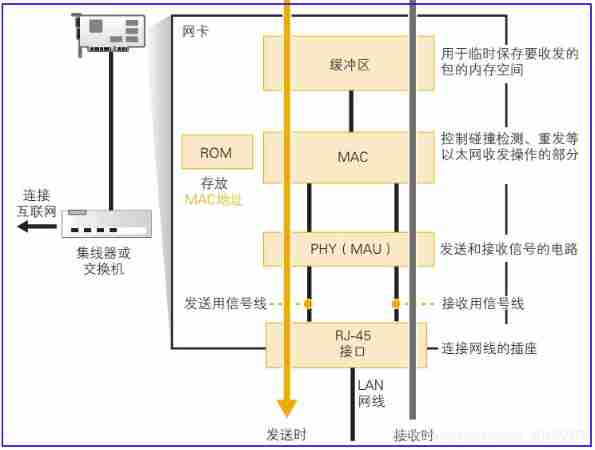
The structure of the network card is shown in the figure above :
Sending data and receiving data are logically opposite , Take sending as an example
- After the network card driver initializes the network card , The network card can work normally
- First MAC The module reads the packed packets to be sent from the buffer of the network card
- In front of the packet ( Add the header , Start frame delimiter ) Back ( Plus frame check sequence ) To form a **“ The final version of the network package ”**
- MAC The module will package ( Digital information ) Signals converted into general format ( My understanding is that you can Give Way PHY The module is the same as the network cable or protocol , Convert to any other format you need )
- MAC The module gives the data in general format to PHY modular
- PHY The module converts the data in general format into on-line ( Optical fiber 、 Telephone line ) Signal format transmitted on
- adopt RJ-45 The interface transmits data

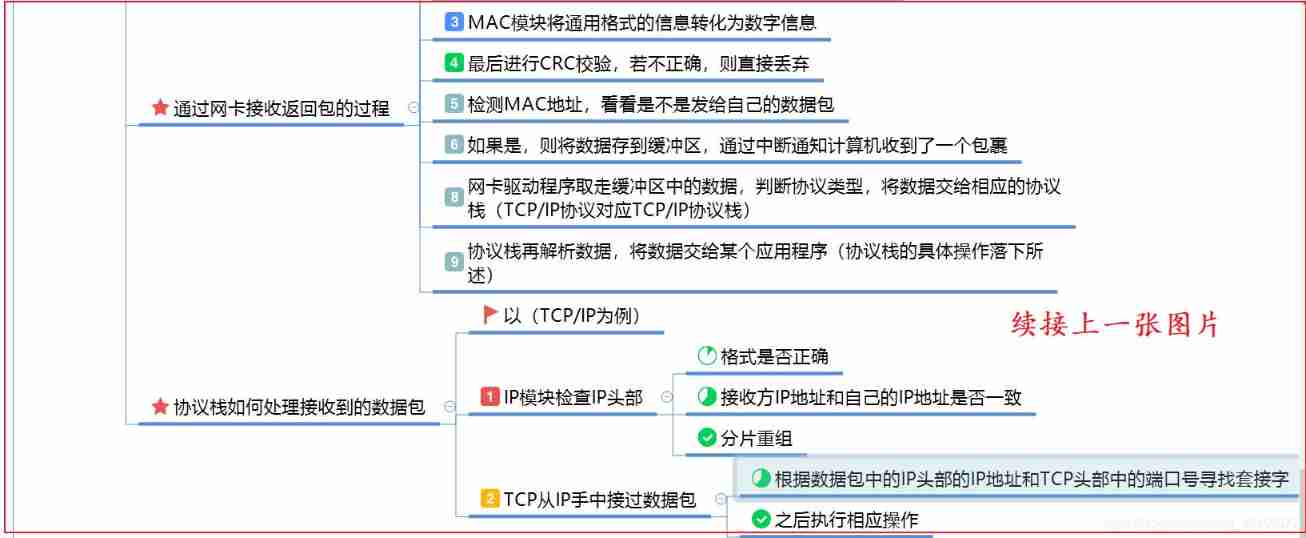
2.5.5 UDP Protocol sending and receiving data

2.6 A term is used to explain
- TCP agreement
- Transmission Control Protocol: Transmission control protocol
- A reliable 、 Connection oriented 、 Based on byte stream Transport layer Communication protocol
- As mentioned above , And IP The protocol is used in conjunction with
- Above TCP The header is the contents of various fields in the Protocol , Corresponding to its working mode
- UDP
- User Datagram Protocol: User datagram protocol
- A connectionless 、 Not very reliable ( Loss of package )、 Fast transmission transport layer communication protocol
- and IP The protocol is used in conjunction with
- IP Deal with the IP Address
- Internet Protocol: Network interconnection protocol
- IP The protocol provides an end-to-end connection , adopt IP Address .
- IP The address is IP An important part of the agreement “ member ”
- IPv4
- IPv6
- ICMP agreement
- Internet Control Message Protocol: internet control message protocol
- The main functions are : Transfer between the host and the router, for example “ Network error ”、“ Routing failure ” Etc
- ARP agreement
- Address Resolution Protocol: Address resolution protocol
- The main functions are : adopt IP Query the physical address of the target ( The specific working mode will be shown in the map above )
- MAC Address
- Media Access Control Address: The media access address is also called MAC Address 、 Ethernet address 、 Physical address
- Every network card has a unique one in the world MAC Address , Used to identify their identity
- It is mainly used to determine a device in a subnet in Ethernet
- MTU
- Maximum Transmission Unit: Maximum transmission unit
- It refers to the maximum length of a network packet ( Contains header data )
- MSS
Maximum Segment Size: Maximum segment length
Specially belong to TCP A noun in the agreement
refer to TCP In bag , Get rid of TCP Behind the head , The maximum amount of data that can be carried ( Data length )
It is mainly used to determine a device in a subnet in Ethernet
- MTU
- Maximum Transmission Unit: Maximum transmission unit
- It refers to the maximum length of a network packet ( Contains header data )
- MSS
- Maximum Segment Size: Maximum segment length
- Specially belong to TCP A noun in the agreement
- refer to TCP In bag , Get rid of TCP Behind the head , The maximum amount of data that can be carried ( Data length )
2.7 The last two maps are a list ( When I have finished the whole book, I will upload and share it for free )
边栏推荐
- C language - stack
- DCL statement of MySQL Foundation
- Delayed message center design
- 【FAQ】华为帐号服务报错 907135701的常见原因总结和解决方法
- Static comprehensive experiment ---hcip1
- Software sharing: the best PDF document conversion tool and PDF Suite Enterprise version sharing | with sharing
- Vanishing numbers
- Basic data types of MySQL
- Huge number (C language)
- [untitled]
猜你喜欢
Safety reinforcement learning based on linear function approximation safe RL with linear function approximation translation 1
The future education examination system cannot answer questions, and there is no response after clicking on the options, and the answers will not be recorded

5g/4g wireless networking scheme for brand chain stores
Some summaries of the third anniversary of joining Ping An in China
Introduction to tree and binary tree
Jianzhi offer 04 (implemented in C language)
Devop basic command
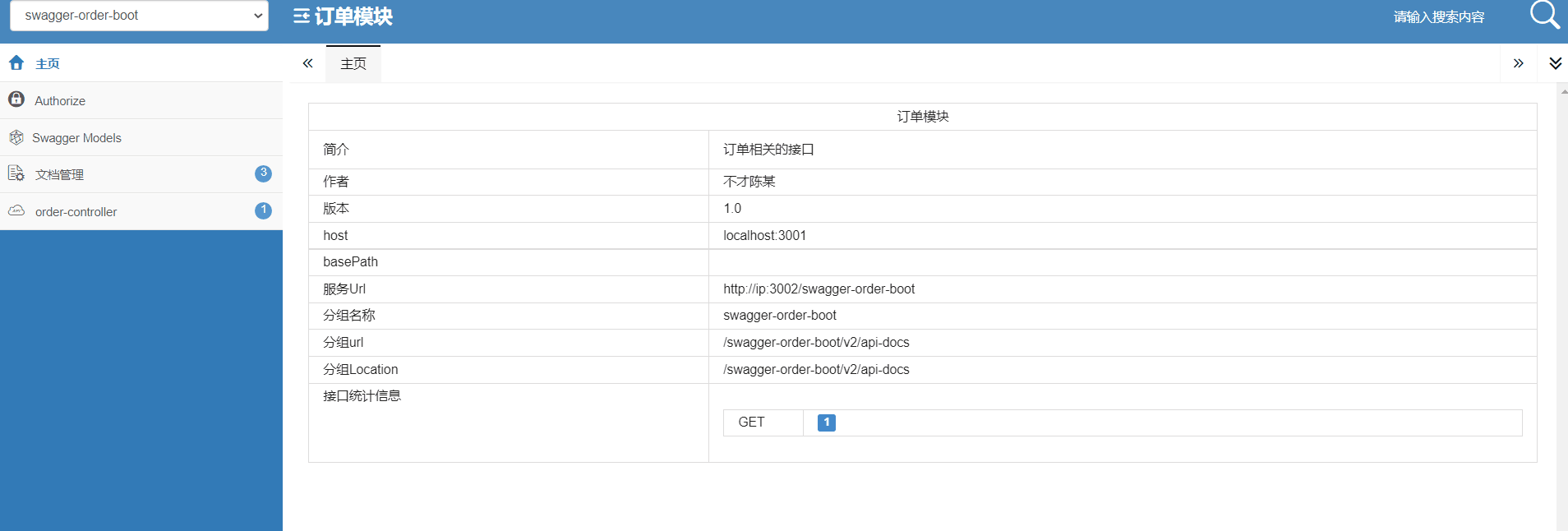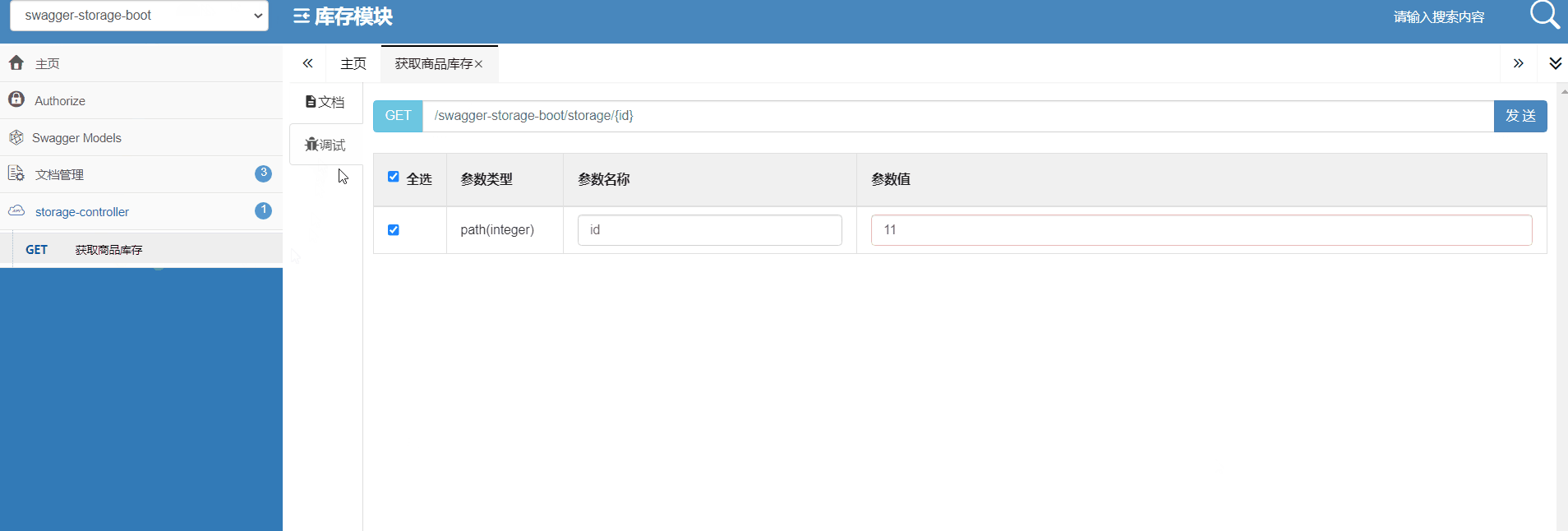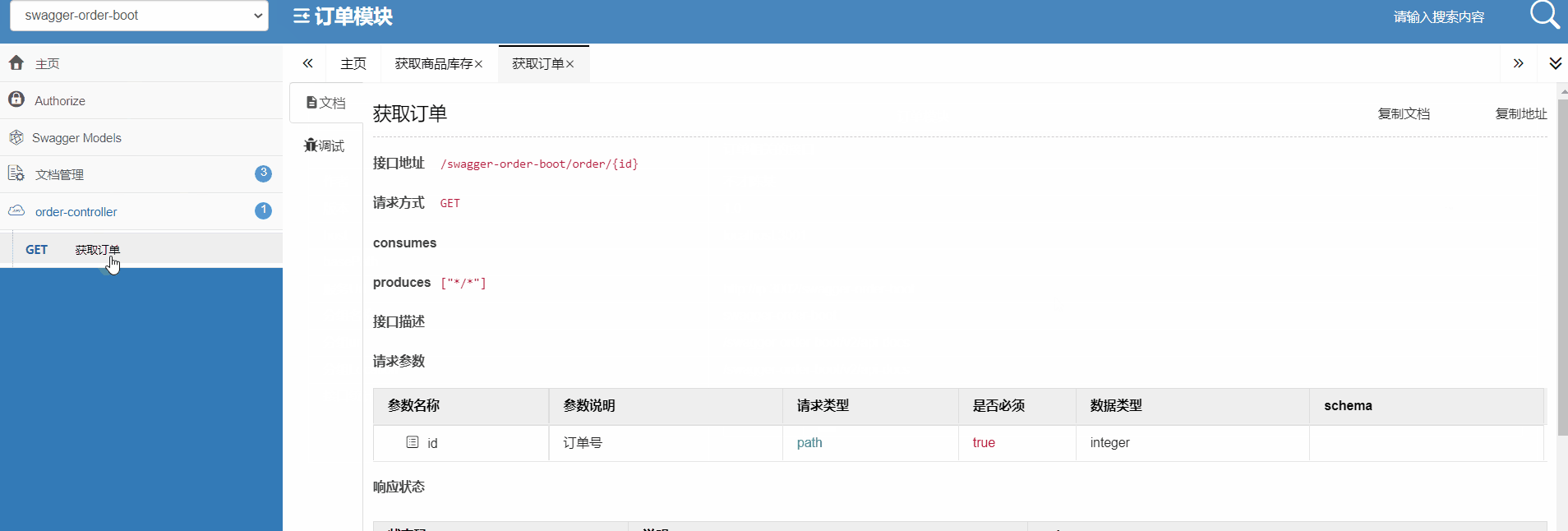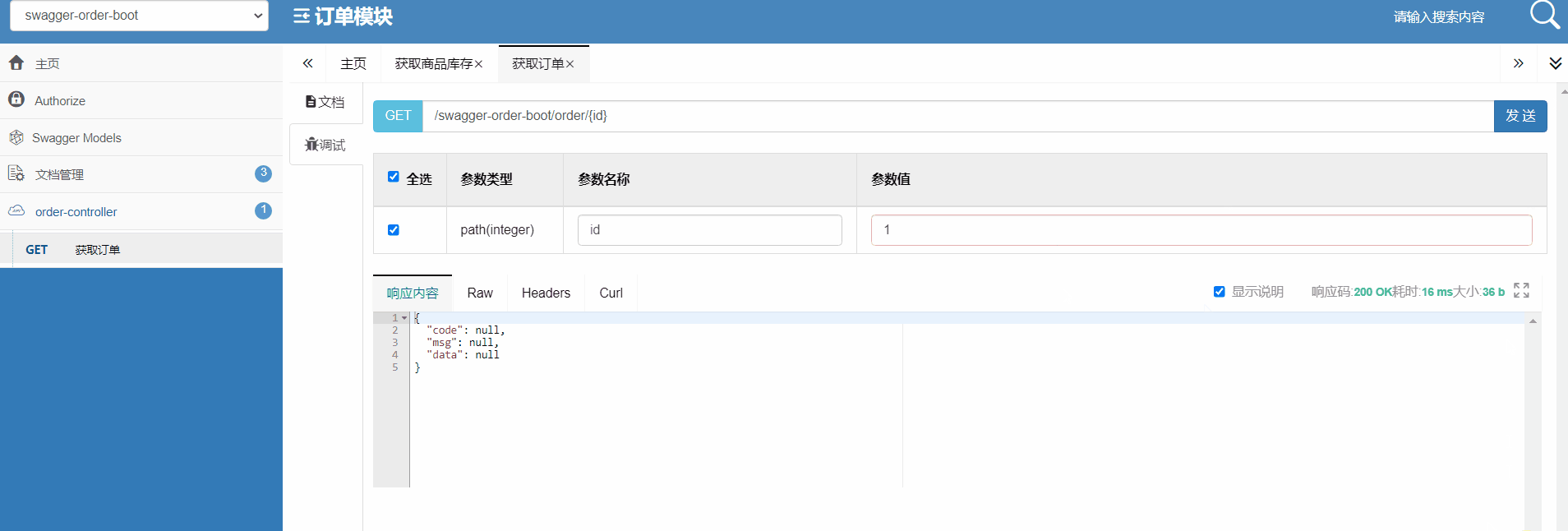
How do microservices aggregate API documents? This wave of show~
【Day1】 deep-learning-basics
The time difference between the past time and the present time of uniapp processing, such as just, a few minutes ago, a few hours ago, a few months ago
随机推荐
Snake (C language)
用数据告诉你高考最难的省份是哪里!
Ruby时间格式转换strftime毫秒匹配格式
Latex learning insertion number - list of filled dots, bars, numbers
Reprint: summation formula of proportional series and its derivation process
Exercise 7-2 finding the maximum value and its subscript (20 points)
Knapsack problem and 0-1 knapsack problem
DCL statement of MySQL Foundation
PHP code audit 3 - system reload vulnerability
Press the button wizard to learn how to fight monsters - identify the map, run the map, enter the gang and identify NPC
Dos:disk operating system, including core startup program and command program
Realsense of d435i, d435, d415, t265_ Matching and installation of viewer environment
Legion is a network penetration tool
Crawl Zhejiang industry and trade news page
If you don't know these four caching modes, dare you say you understand caching?
DML statement of MySQL Foundation
Native div has editing ability
DDL statement of MySQL Foundation
Differences among opencv versions
Sword finger offer 05 (implemented in C language)