当前位置:网站首页>Daemon xinted and logging syslogd
Daemon xinted and logging syslogd
2022-07-04 11:01:00 【Brother Xing plays with the clouds】
1 Create daemons
1. Give Way init The process becomes the parent of the new process .
call fork Function to create a child process , Causes the parent process to exit immediately . such , The resulting child process will become an orphan process , And be init Process takeover , meanwhile , The resulting new process will become running in the background .
2. call setsid()
Make the newly created process out of the control terminal , At the same time, create a new process group , And become the first process of the process group .
Process group & conversation & Control terminal
A process group is a collection of one or more processes , Process group ID It is determined by the process number of the leading process .
A session is a collection of one or more process groups , Similar to process groups , Each session has a lead process .
When the user logs into the system from the terminal , The system will create a new session . The processes started on the terminal will be classified into the process group of the session by the system .
The process in the session is connected to a terminal through the leading process in the session .
Because the daemon does not need to control the terminal , therefore , You must create a new session , To get rid of the influence of the parent process ,Linux The system provides setsid Function to create a new session , And make the call setsid The process of the function becomes the leading process of the new session .
setsid() After the call is successful , The process becomes a new conversation leader and a new process leader , And break away from the original login session and process group .
At this time, the process has no control terminal , But it should be prevented from opening the control terminal later , You can prevent the process from reopening the control terminal by making it no longer the session leader :
if(pid=fork())
exit(0);
3. Change current working directory
Use fork The child process generated by the function will inherit the current working directory of the parent process . When the process does not end , Its working directory cannot be uninstalled . In order to prevent this problem from happening , Daemons usually change their working directory to the root directory (/ Catalog ). The function used to change the working directory is chdir.
4. Close the file descriptor , And redirect standard input 、 Output and error output
The newly generated process inherits some open file descriptors from the parent process , If you don't use these file descriptors , You need to turn them off . Daemons run in the background of the system , There should be no output information at the terminal . have access to dup Function takes the standard input 、 Redirect output and error output to /dev/null On the device (/dev/null Is an empty device , Writing data to it will not have any output ).
5. Set the file permission creation mask of the daemon
In many cases , The daemon will create some temporary files . For security reasons , Often do not want these files to be viewed by other users . At this time , have access to umask Function to modify file permissions , Create the value of the mask , To meet the requirements of the daemon .
Simple implementation
void init_daemon(void)
{
int pid;
int i;
if(pid=fork())
exit(0); // End parent process
else if(pid< 0)
exit(1);
// First subprocess , Continue to execute in the background
setsid(); // The first subprocess becomes the new session leader and process leader , And separate from the control terminal
if(pid=fork())
exit(0); // End the first child process
else if(pid< 0)
exit(1); //
// The second subprocess continues to execute , The second child process is no longer the session leader
for(i=0;i< NOFILE;++i) // Close open file descriptor
close(i);
chdir("/tmp"); // Change the working directory to /tmp
umask(0); // Reset file creation mask
return;
}
Super daemons Xinetd
xinetd It can listen to multiple specified ports at the same time , When accepting user requests , It can be different according to the port requested by the user , Start different network service processes to process these user requests .
xinetd and stand-alone Compared with the working mode , Run a single xinetd You can listen to all service ports at the same time , This reduces the system overhead .
But for a large number of visits 、 Concurrent access often occurs ,xinetd Start the corresponding network service process frequently , Instead, it will lead to the decline of system performance .
pstree The command can see the network services started in two different modes . Generally speaking, some services with high load in the system ,Sendmail、Apache The service is started separately ; Other service types can be used xinetd Super The server management .
2 Daemon log management
Because the daemon does not own the control terminal , Therefore, the process operation information cannot be output and displayed . But sometimes we need to manage and maintain the system according to the information provided by the process . So ,Linux The system provides a special mechanism to solve the logging problem of the daemon .syslogd Daemons receive information from other daemons , And record these information in the designated location to solve the problem of logging .syslogd The daemon will judge whether to record the message in the log file according to the message level , It is still displayed on the user terminal .
Linux Log management :
Kernel information -> klogd -> syslogd -> /var/log/dmesg
Other information -> syslogd -> /var/log/messages Wait for the documents
syslog The configuration file -> /etc/syslog.conf
Syslog principle
syslog Responsible for sending 、 Record the information generated by the system kernel and tools , from syslog() call 、syslogd Daemons and configuration files /etc/syslog.conf form . When the system kernel and tools generate information , By calling syslog(), Send the information to syslogd,syslogd According to /etc/syslog.conf Configuration requirements in , Process these information as follows :
1 Record in the system log
2 Output to the system console
3 Forward to the specified user
4 Forward to other hosts through the network syslogd
Almost all network devices can pass syslog agreement , Log information in user datagram protocol (UDP) To the far end The server , The remote log receiving server must pass syslogd monitor UDP port 514, And according to syslog.conf The configuration in the configuration file handles this machine , Receive log information of accessing the system , Write the specified event to a specific file , For background database management and response . It means that any event can be logged into one or more servers , For background database off-line( offline ) Methods analyze the events of remote devices .
Syslog.conf The configuration format is
service name [.=!] Record level Record file or host
Log security
Set hidden properties chattr +a /var/log/messages, Only append must not delete
边栏推荐
- First article
- Huge number (C language)
- Canoe: the fourth simulation project -- bug debugging experience
- Canoe - the third simulation project - bus simulation - 3-1 project implementation
- [untitled]
- Network connection (III) functions and similarities and differences of hubs, switches and routers, routing tables and tables in switches, why do you need address translation and packet filtering?
- The last month before a game goes online
- VI text editor and user rights management, group management and time management
- MBG combat zero basis
- regular expression
猜你喜欢
![[test theory] test process management](/img/d2/65865dffacf38d9a8be720868b75f0.jpg)
[test theory] test process management

2022 AAAI fellow release! Yan Shuicheng, chief scientist of sail, and Feng Yan, Professor of Hong Kong University of science and technology, were selected
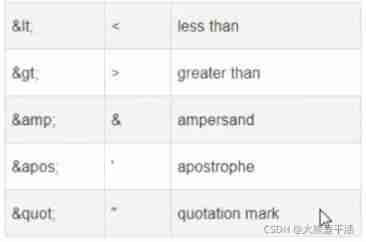
20 minutes to learn what XML is_ XML learning notes_ What is an XML file_ Basic grammatical rules_ How to parse
![[Galaxy Kirin V10] [server] iSCSI deployment](/img/60/13f43dc584c0768965d60811768948.jpg)
[Galaxy Kirin V10] [server] iSCSI deployment
![[Galaxy Kirin V10] [desktop] cannot add printer](/img/a6/28e4aa31e805a018e6db2b32ca1be0.jpg)
[Galaxy Kirin V10] [desktop] cannot add printer
Appscan installation error: unable to install from Net runtime security policy logout appscan solution
![[Galaxy Kirin V10] [server] NFS setup](/img/ed/bd7f1a1e4924a615cb143a680a2ac7.jpg)
[Galaxy Kirin V10] [server] NFS setup
![[Galaxy Kirin V10] [server] soft RAID configuration](/img/d5/789387613fafc18f623d0cff45093b.jpg)
[Galaxy Kirin V10] [server] soft RAID configuration
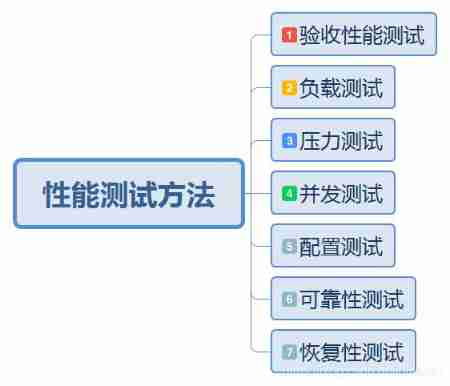
Performance test method
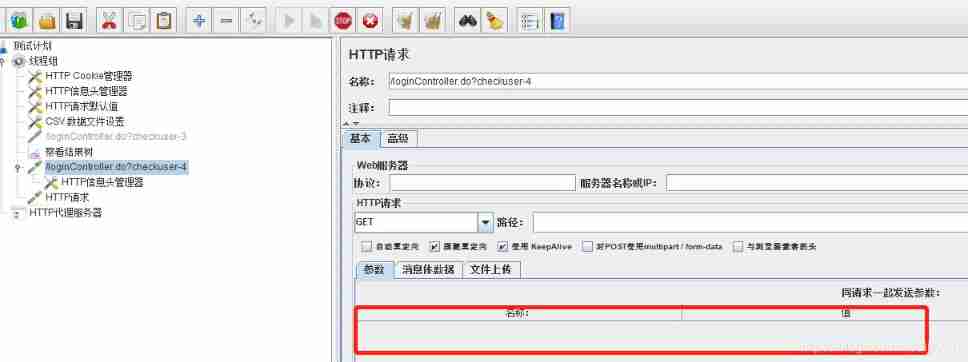
JMeter common configuration components and parameterization
随机推荐
What if the book written is too popular? Author of "deep reinforcement learning" at Peking University: then open the download
20 kinds of hardware engineers must be aware of basic components | the latest update to 8.13
[Galaxy Kirin V10] [server] KVM create Bridge
How to use diff and patch to update the source code
iptables导致Heartbeat脑裂
JMeter common configuration components and parameterization
Fundamentals of software testing
Function introduction of canbedded component
Capl: timer event
/*The rewriter outputs the contents of the IA array. It is required that the type defined by typedef cannot be used in the outer loop*/
本地Mysql忘记密码的修改方法(windows)
2、 Operators and branches
Interview and lecture summary 1
Canoe: the difference between environment variables and system variables
Summary of several job scheduling problems
shell awk
Post man JSON script version conversion
Send a request using paste raw text
[Galaxy Kirin V10] [desktop] login system flash back
Elevator dispatching (pairing project) ②