当前位置:网站首页>JMeter common configuration components and parameterization
JMeter common configuration components and parameterization
2022-07-04 10:47:00 【dijiaye1】
Jmeter Common configuration components
Common configuration components :1、HTTP Request defaults ;2、HTTP Cookie Manager ;3、HTTP Cache Manager ;4、HTTP Header Manager
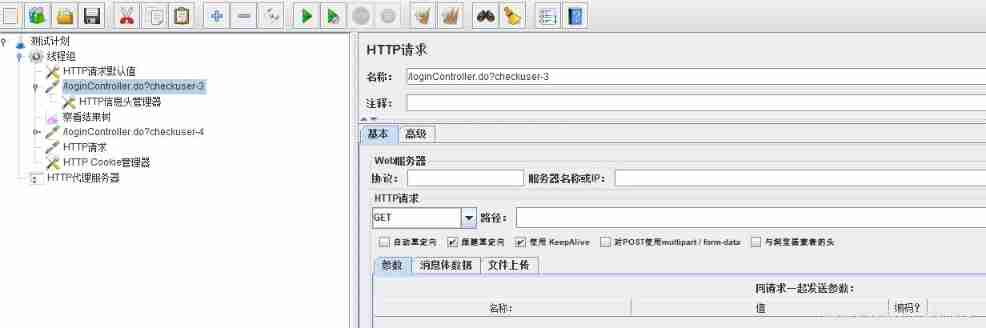
HTTP Request defaults
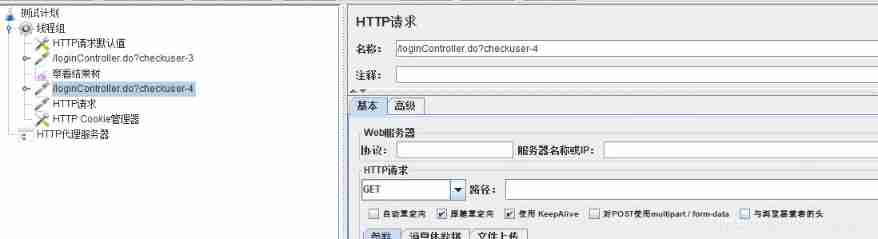
There are many requests to create a test plan and they are all sent to the same server, Just add one in this “HTTP Request defaults ”, And set up “Server Name or IP”
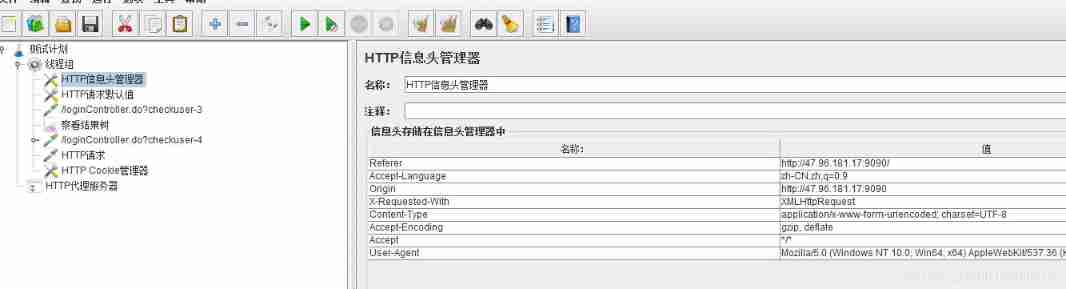
HTTP Header Manager
Set up Jmeter Sent HTTP The information contained in the request header
The message header contains User-Agent、content-type、Referer
Put it at the thread group level as much as possible . Unless for some reason , Testers want different HTTP The request uses a different HTTP Message header
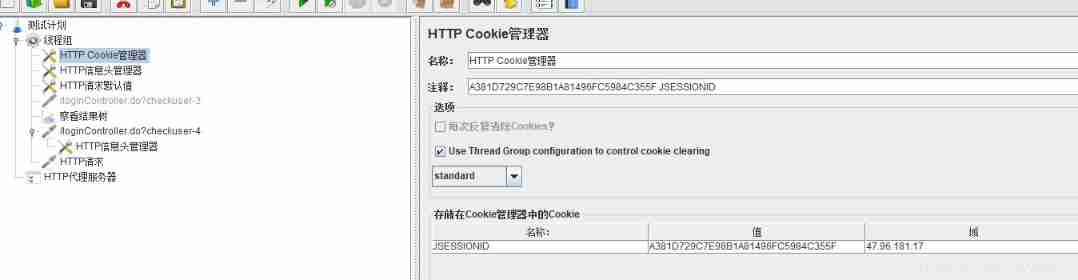
HTTP Cookie Manager
management Test Plan All of the runtime Cookie
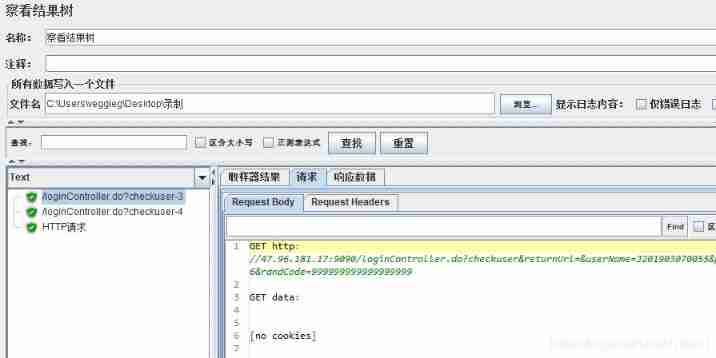
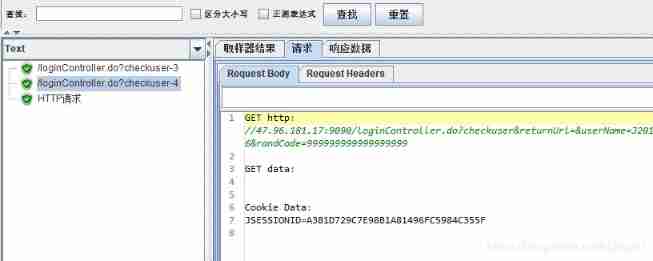
HTTP Cookie The manager can automatically store all messages sent by the server to the client Cookie, And attach the appropriate Cookie
Users can also HTTP Cookie Add some manually in the manager Cookie, These were added by hand Cookie Will be automatically attached to the request when it is sent .
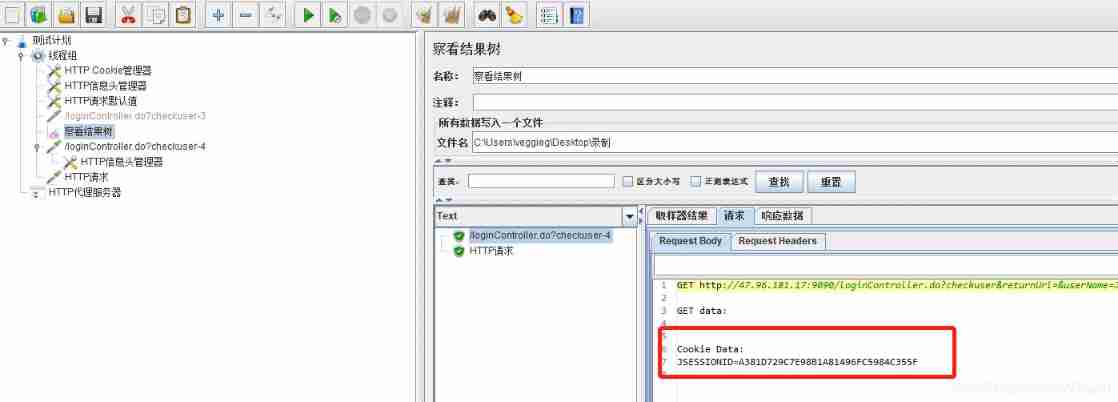
stay Cookie Add the Cookie Information , You only need to log in once to succeed .
HTTP CACHE Manager
It generally refers to the cache of the browser
Can be used to simulate the browser Cache Behavior , Closer to user behavior
If Test Plan One of them Sampler The requested element is the cached element , be Test Plan In the process of operation, it will be directly from Cache Read elements from , In this way, the return value will be empty . The Sampler Assertion is set to check whether the specified content in the response body exists , The assertion will fail .
Jmeter Common parameterization
Parameterization is a common technique for automated test scripts .
Simply speaking , The general usage of parameterization is to use variables to replace some inputs in the script , Specify the value range and rules of variables when the script runs .
such , When the script is running, you can choose different parameters as input according to your needs .
When referencing a variable in a certain place , Can pass ${ Variable name } To get the value of a variable .
If this variable is not defined , Then this formula will be treated as an ordinary string .
${ Variable name }
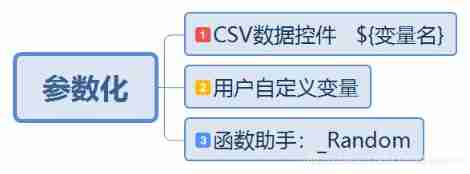
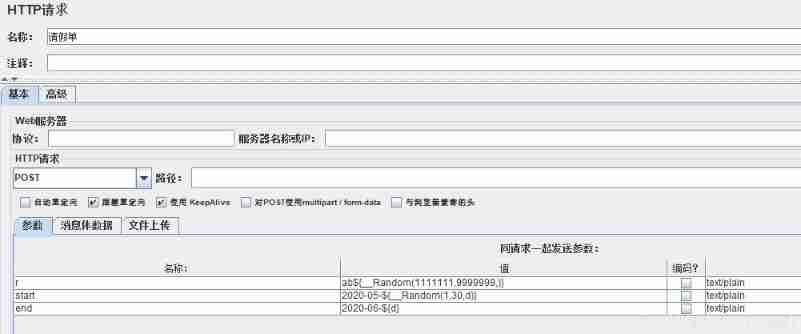
1、CSV Data controls
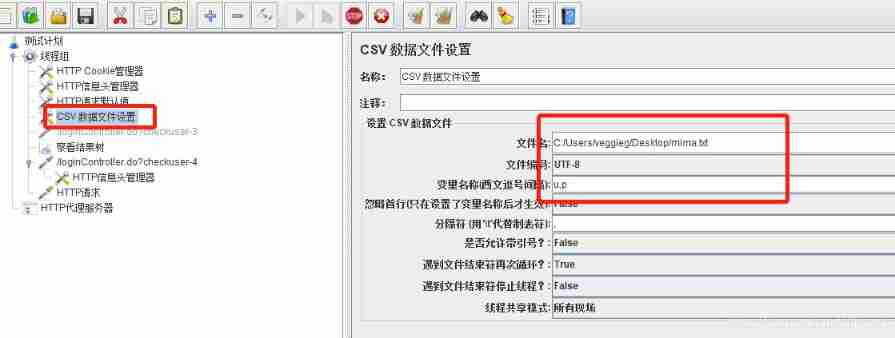 add to CSV Data file settings , Import the document with user name and password ., Set up UTF-8
add to CSV Data file settings , Import the document with user name and password ., Set up UTF-8
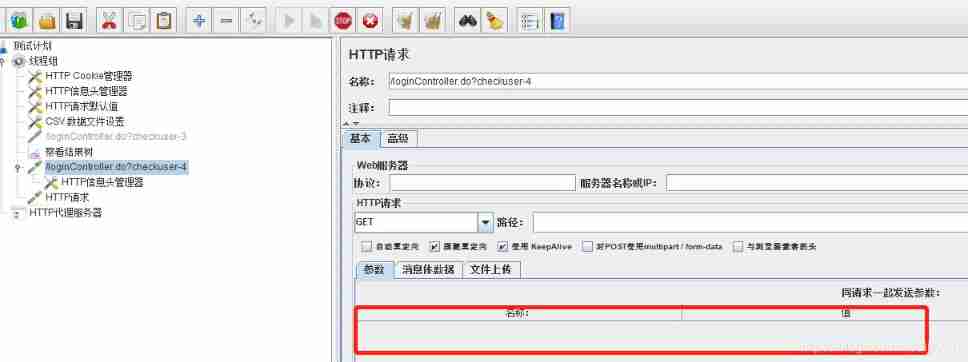
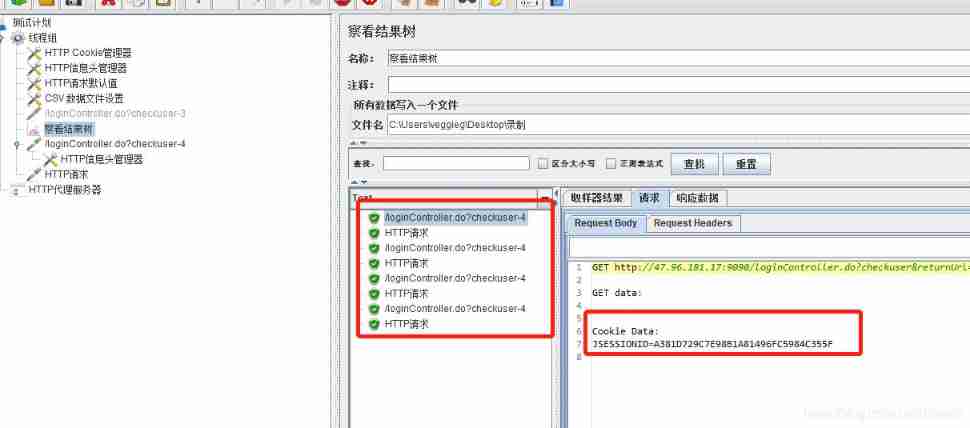
Pictured , You can also ask for success .
The password document contains 5 Group user and password , Loop through thread groups 5 Time , You can traverse the user passwords in the document one by one .
Cancel the parameter in the request
2、 random number
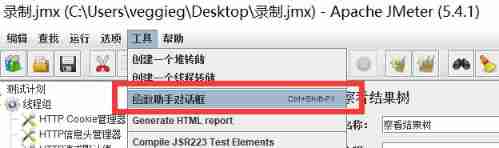
Tools - Function Assistant dialog
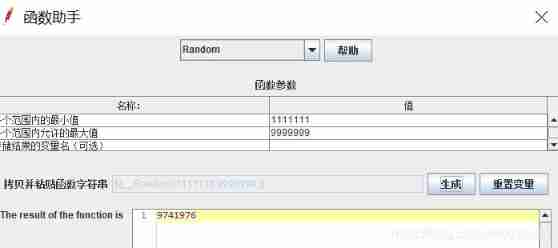
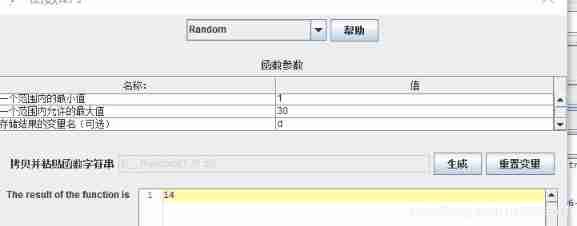
Selection function , Input range , Click on “ Generate ”, That is, the function is copied .
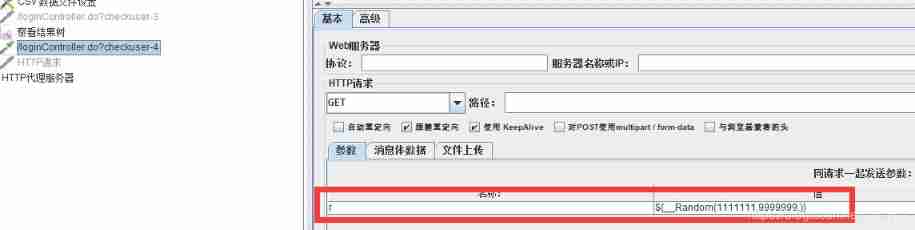
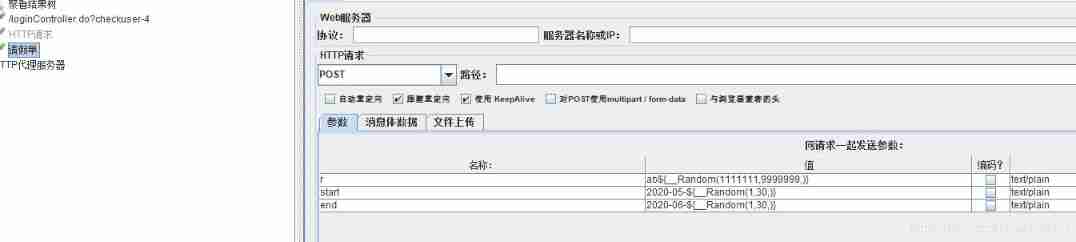
Functions to be copied , Join the request , loop 5 Execution times .
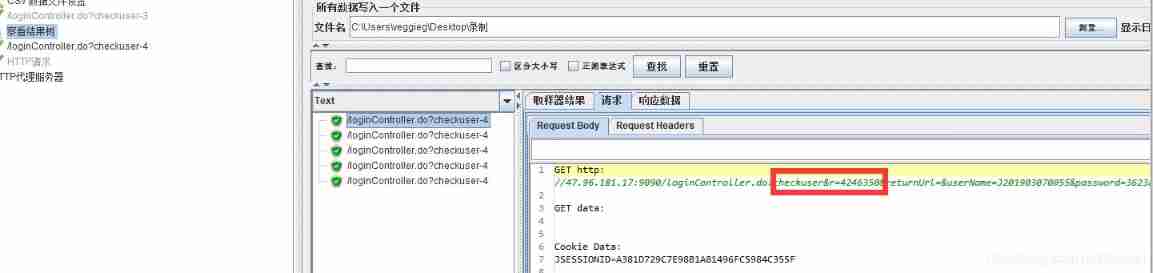
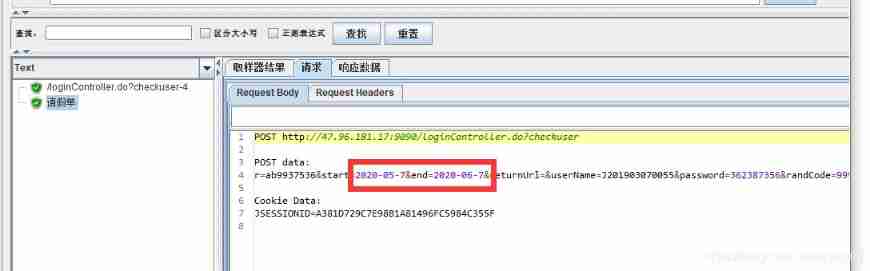
You can see , Circulated 5 Execution times , This value is different every time .
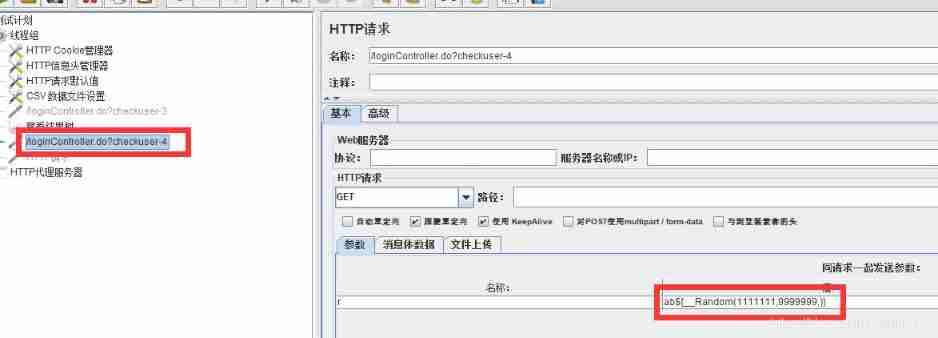
You can also add letters before random numbers ,
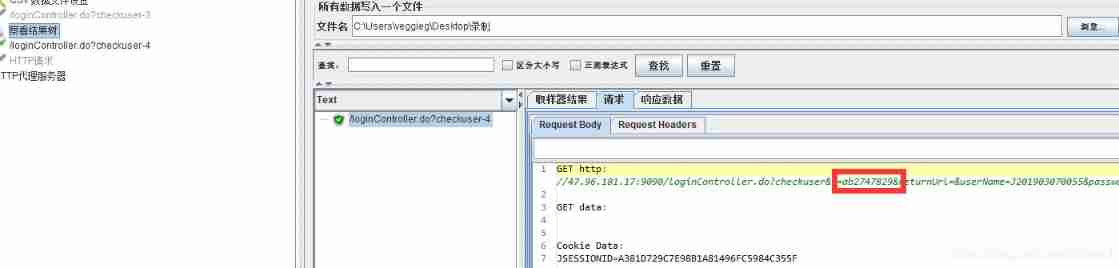
It can also be used. POST Request to view
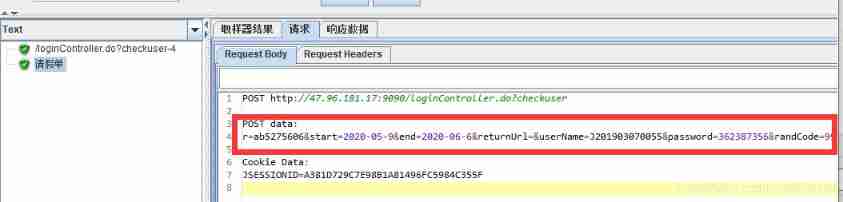
If the random numbers are the same , Is the diagram below
边栏推荐
- How to quickly parse XML documents through C (in fact, other languages also have corresponding interfaces or libraries to call)
- Number of relationship models
- Write a thread pool by hand, and take you to learn the implementation principle of ThreadPoolExecutor thread pool
- Knapsack problem and 0-1 knapsack problem
- If you don't know these four caching modes, dare you say you understand caching?
- System. Currenttimemillis() and system Nanotime (), which is faster? Don't use it wrong!
- [testing theory] thinking about testing profession
- /*Rewrite the program, find the value of the element, and return the iterator 9.13: pointing to the found element. Make sure that the program works correctly when the element you are looking for does
- Article publishing experiment
- Talk about scalability
猜你喜欢

Deepmind proposed a Zuan AI, which specially outputs network attack language
Rhsca day 11 operation
Rhcsa - day 13

Doris / Clickhouse / Hudi, a phased summary in June
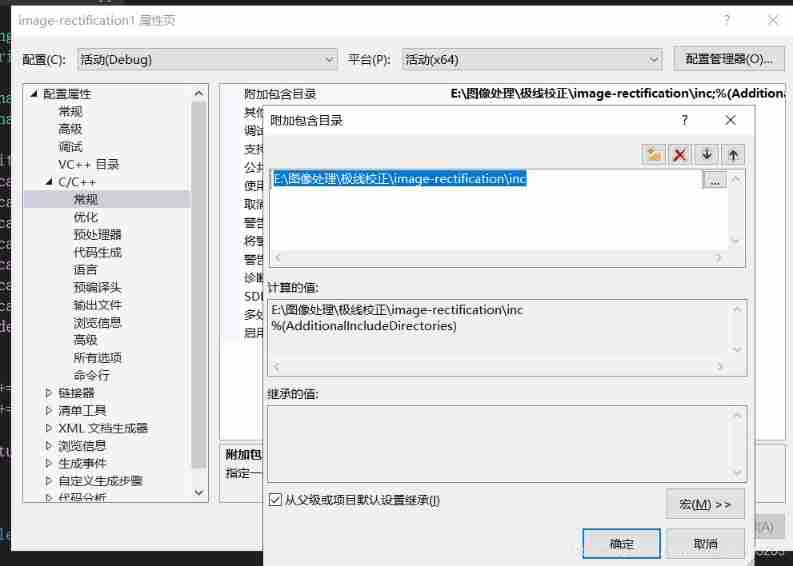
Vs201 solution to failure to open source file HPP (or link library file)

Huge number multiplication (C language)
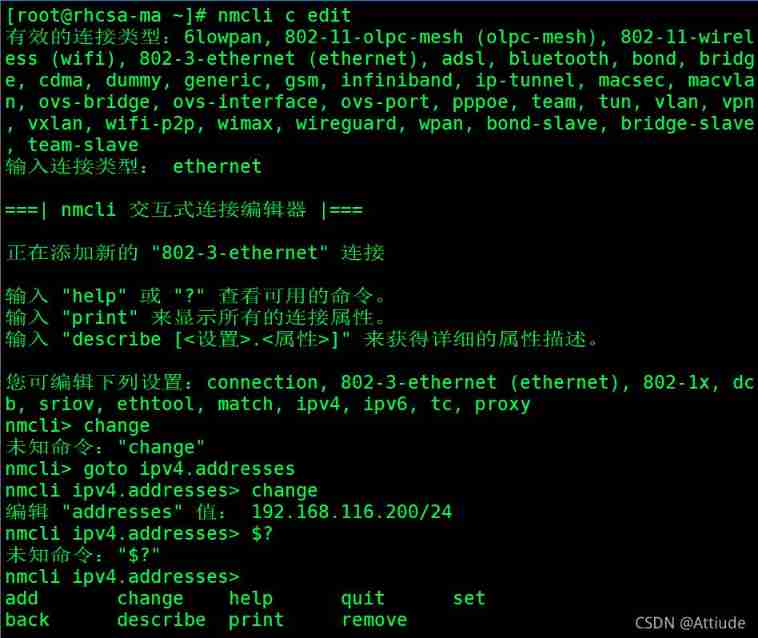
Rhcsa12
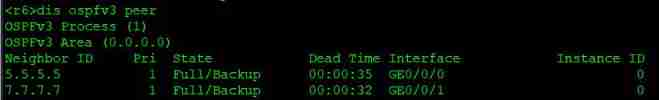
IPv6 comprehensive experiment
leetcode842. Split the array into Fibonacci sequences
Four characteristics and isolation levels of database transactions
随机推荐
2020-03-28
Three schemes of ZK double machine room
/*Write a function to open the file for input, read the contents of the file into the vector container of string class 8.9: type, and store each line as an element of the container object*/
C language structure to realize simple address book
Latex learning insertion number - list of filled dots, bars, numbers
Application and Optimization Practice of redis in vivo push platform
Sword finger offer 31 Stack push in and pop-up sequence
MFC document view framework (relationship between classes)
MPLS: multi protocol label switching
[Galaxy Kirin V10] [desktop] printer
Software sharing: the best PDF document conversion tool and PDF Suite Enterprise version sharing | with sharing
/*Write a loop to output the elements of the list container in reverse order*/
From programmers to large-scale distributed architects, where are you (I)
Es advanced series - 1 JVM memory allocation
Time complexity and space complexity
Article publishing experiment
Vs201 solution to failure to open source file HPP (or link library file)
Network connection (III) functions and similarities and differences of hubs, switches and routers, routing tables and tables in switches, why do you need address translation and packet filtering?
Es entry series - 6 document relevance and sorting
Snake (C language)